1. [BSidesSF-CTF 2019] Zippy
nc -l -p 4445 > flag.zip
unzip -P supercomplexpassword flag.zip
Archive: flag.zip
inflating: flag.txt
PK.... ...NdbN..,.%...........flag.txtUT ....z\..z\ux.............
..(.y..z.. ..F.......:...#B z..:...YPK....,.%.......PK...... ...NdbN..,.%.........................flag.txtUT.....z\ux.............PK..........N...w.....
发现压缩包和密码
CTF{this_flag_is_your_flag}
2. [鹤城杯 2021]流量分析
打开流量包发现是sql的布尔盲注
/ctf/Less-5/?id=1'%20and%20ascii(substr((select%20flag%20from%20t),1,1))=33--+如果sql语句查询结果正确,那么就会进行下一位的查找,所以只要找到当前
substr()那边,最大的数字就行
使用tshark提取指定的数据
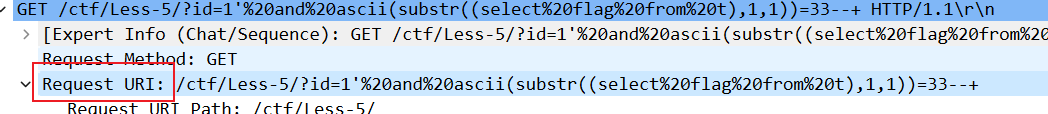
我们想要request uri的值
-r x.pcapng 表示从文件 x.pcapng 中读取网络数据包
-e http.request.uri 指定要提取的字段为 HTTP 请求的 URI
-T fields 表示输出仅包含指定的字段内容
-Y 'http.request.uri' 是过滤表达式,只保留包含 HTTP 请求 URI 的数据包
tshark -r .\timu.pcapng -Y 'http.request.uri' -e http.request.uri -T fields > 1.txt
导出的就是下面这样的数据
/ctf/Less-5/?id=1'%20and%20ascii(substr((select%20flag%20from%20t),1,1))=33--+
/ctf/Less-5/?id=1'%20and%20ascii(substr((select%20flag%20from%20t),1,1))=34--+
/ctf/Less-5/?id=1'%20and%20ascii(substr((select%20flag%20from%20t),1,1))=35--+
/ctf/Less-5/?id=1'%20and%20ascii(substr((select%20flag%20from%20t),1,1))=36--+
......
那我们就写一个py脚本将值提取出来
import re
with open('1.txt','r') as f:
data = f.read()
re1 = r"from%20t\),(\d+),1\)\)=(\d+)--+"
pat = re.compile(re1) # 生成一个正则表达式的对象
a = data.split("\n") # 分割成一个列表
b = {}
for i in a:
try:
rea = pat.search(i)
b[rea[1]] = rea[2]
except:
continue
# print(b)
flag = ""
for i in b:
flag+=chr(int(b[i]))
print(flag)
flag{w1reshARK_ez_1sntit}~~~~<
3. [CISCN 2023 初赛]被加密的生产流量
打开流量包。发现是Modbus协议
tshark.exe -r .\modbus.pcap -Y 'modbus.word_cnt' -e modbus.word_cnt -T fields > modbus.txt
提取modbus.word_cnt的值
发现他是10进制转字符串,然后是base32解码
import libnum
import base64
a = """19789
22871
19800
13127
20037
22871
20312
23122
18241
22852
16701
15677"""
b = a.split("\n")
print(b)
c = ""
for i in b:
c += libnum.n2s(int(i)).decode('utf-8')
print(base64.b32decode(c))
b'c1f_fi1g_1000'
4. [GKCTF 2021]签到
打开流量包,发现是一个webshell执行命令
QER1=cat /f14g|base64
返回包
64306c455357644251306c6e51554e4a5a3046355355737764306c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154576c44546d39525241707154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7162314645616b46445357644251306c6e51554e4a5a32644554545a46524530325157704e5a3046365458524e524531305257704e436e5177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d644442705130354e65556c7154586c4a616b31355357704e65556b4b4e6b467154576442656b31305455524e644556715458644a616b38775a566f324d6d56774e557377643074795556645a64315a485a48593152556c3051576c4e4d5546355a4777316255733254545a7162475a7763573579555552304d464e4d64444254544170304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d537a42425357526159585a764e7a567462485a735130354e564530325255524e436e6f77655531334d464e4e6555467154545a524e327877596a647362584a5252484a7a5131706f516c68614d446c745647637751306c355655524a4d315a74596e4676656d3951567974736357563151303477553078304d464e4d64444254544851775530774b63336858576d786b4d5659354d544e6c4e325179576d684752324a7a576d31615a7a427363446c7064573569567974585a7a427363446c7064573569567974585a7a427363446c706457356956797458537a423354586876564531336230524e6555464454517045546a4252524534775555527356324636546c684e65444258596d593562464a48556b524f5245347759584a6b4d464a6d4f565a6162444658596e644252456c6b556d46746345524c61577832526b6c6b556d46746345524c61577832566b747754544a5a436a303955556c6f545442525245347755516f3d
Hex解密,再base64解码
wIDIgACIgACIgAyIK0wIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMiCNoQD
jMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjoQDjACIgACIgACIggDM6EDM6AjMgAzMtMDMtEjM
t0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0iCNMyIjMyIjMyIjMyI
6AjMgAzMtMDMtEjMwIjO0eZ62ep5K0wKrQWYwVGdv5EItAiM1Aydl5mK6M6jlfpqnrQDt0SLt0SL
t0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLK0AIdZavo75mlvlCNMTM6EDM
z0yMw0SMyAjM6Q7lpb7lmrQDrsCZhBXZ09mTg0CIyUDI3VmbqozoPW+lqeuCN0SLt0SLt0SLt0SL
sxWZld1V913e7d2ZhFGbsZmZg0lp9iunbW+Wg0lp9iunbW+Wg0lp9iunbW+WK0wMxoTMwoDMyACM
DN0QDN0QDlWazNXMx0Wbf9lRGRDNDN0ard0Rf9VZl1WbwADIdRampDKilvFIdRampDKilvVKpM2Y
==QIhM0QDN0Q
发现每一行都被逆序了
import base64
a="""wIDIgACIgACIgAyIK0wIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMiCNoQD
jMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjoQDjACIgACIgACIggDM6EDM6AjMgAzMtMDMtEjM
t0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0iCNMyIjMyIjMyIjMyI
6AjMgAzMtMDMtEjMwIjO0eZ62ep5K0wKrQWYwVGdv5EItAiM1Aydl5mK6M6jlfpqnrQDt0SLt0SL
t0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLK0AIdZavo75mlvlCNMTM6EDM
z0yMw0SMyAjM6Q7lpb7lmrQDrsCZhBXZ09mTg0CIyUDI3VmbqozoPW+lqeuCN0SLt0SLt0SLt0SL
sxWZld1V913e7d2ZhFGbsZmZg0lp9iunbW+Wg0lp9iunbW+Wg0lp9iunbW+WK0wMxoTMwoDMyACM
DN0QDN0QDlWazNXMx0Wbf9lRGRDNDN0ard0Rf9VZl1WbwADIdRampDKilvFIdRampDKilvVKpM2Y
==QIhM0QDN0Q"""
b = a.split("\n")
# print(b)
c = ""
for i in b:
c += i[::-1]
print(base64.b64decode(c).decode('utf-8'))
#######################################
# 2021-03-30 20:01:08 #
#######################################
--------------------------------------------------
窗口:*new 52 - Notepad++
时间:2021-03-30 20:01:13
[回车]
--------------------------------------------------
窗口:*new 52 - Notepad++
时间:2021-03-30 20:01:13
[回车] [回车] [回车] ffllaagg{{}}WWeellcc))[删除] [删除] 00mmee__GGkkCC44FF__mm11ssiiCCCCCCCCCCCC!!
将ffllaagg{{}}WWeellcc00mmee__GGkkCC44FF__mm11ssiiCCCCCCCCCCCC!!解密
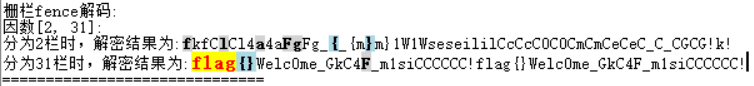
flag{}Welc0me_GkC4F_m1siCCCCCC!flag{}Welc0me_GkC4F_m1siCCCCCC!
5. [闽盾杯 2021]Modbus的秘密
Modbus协议
modbus流量大致有两个点,一个是Register的值,一个是Word Count
2195流找到
flag{HeiDun_2021_JingSai}
6. [LitCTF 2023]easy_shark
题目描述
卧底小帅在潜伏期间截获了一段非常可疑的流量,为了里面的内容不被泄露出去,小帅将flag进行了加密,你能成功发现犯罪团伙的秘密,并拯救小帅吗?flag格式:NSSCTF
在HTTP的最后一个包里
Can you request my question?
(x^2-x**2)+(x-17)(x-77)=0
#gezx{j13p5oznp_1t_z_900y_k3z771h_k001}
x等于17或77,想到仿射密码
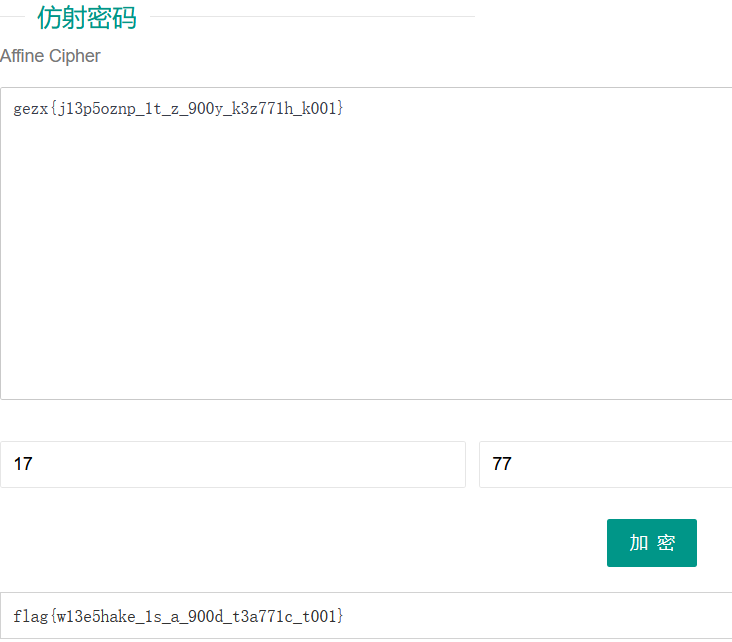
这还不是最终的flag,根据题目描述,在flag后加一个a
flag
flag{w13e5hake_1s_a_900d_t3a771c_t001_a}
7. [CISCN 2022 初赛]ez_usb
考点:USB协议 USB
USB介绍
USB全称是通用串口总线,USB流量是指USB设备接口的流量,攻击者能够通过USB流量获取键盘敲击键、鼠标移动与点击、存储设备的明文传输通信、USB无线网卡网络传输内容等信息
CTF比赛中,USB流量分析主要以键盘鼠标流量为主
区分键盘鼠标流量
主要就是看usbhid.data的值
设置过滤表达式为usbhid.data,观察值
键盘流量数据长度为8字节
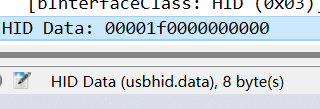
鼠标流量数据长度是4字节
提取USB流量方法
用tshark提取
tshark -r usb.pcap -T fields -e usb.capdata > usbdata.txt
或用UsbKeyboardDataHacker工具进行提取
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# python main.py example.pcap
Running as user "root" and group "root". This could be dangerous.
[-] Unknow Key : 01
[-] Unknow Key : 01
[+] Found : flag{pr355_0nwards_a2fee6e0}
解题
这一题是键盘流量
过滤usbhid.data后发现2.8.1 2.4.1 2.10.1都有分别分类出来
利用usb.addr分别导出来
usb.addr == "2.4.1"
usb.addr == "2.8.1"
usb.addr == "2.10.1"
然后分别导出指定分组,得到三个流量包
然后利用UsbKeyboardDataHacker提取
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# python main.py 2.4.1.pcapng
Running as user "root" and group "root". This could be dangerous.
[+] Found :
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# python main.py 2.8.1.pcapng
Running as user "root" and group "root". This could be dangerous.
[-] Unknow Key : 04
[-] Unknow Key : 04
[-] Unknow Key : 01
[-] Unknow Key : 01
[+] Found : 526172211a0700<CAP>c<CAP>f907300000d00000000000000c4527424943500300000002<CAP>a000000<CAP>02b9f9b0530778b5541d33080020000000666c61672<CAP>e<CAP>747874<CAP>b9b<CAP>a013242f3a<CAP>fc<CAP>000b092c229d6e994167c05<CAP>a7<CAP>8708b271f<CAP>fc<CAP>042ae3d251e65536<CAP>f9a<CAP>da87c77406b67d0<CAP>e6316684766<CAP>a86e844d<CAP>c81aa2<CAP>c72c71348d10c4<CAP>c<DEL>3d7b<CAP>00400700
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# python main.py 2.10.1.pcapng
Running as user "root" and group "root". This could be dangerous.
[+] Found : 35c535765e50074a
2.4.1没有分离出来是因为他的usbhid.data的值有7和6字节的
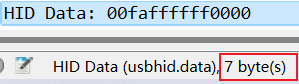
526172211a0700<CAP>c<CAP>f907300000d00000000000000c4527424943500300000002<CAP>a000000<CAP>02b9f9b0530778b5541d33080020000000666c61672<CAP>e<CAP>747874<CAP>b9b<CAP>a013242f3a<CAP>fc<CAP>000b092c229d6e994167c05<CAP>a7<CAP>8708b271f<CAP>fc<CAP>042ae3d251e65536<CAP>f9a<CAP>da87c77406b67d0<CAP>e6316684766<CAP>a86e844d<CAP>c81aa2<CAP>c72c71348d10c4<CAP>c<DEL>3d7b<CAP>00400700
将<CAP>删除,c<DEL删除,然后全部大写
52 61 72 21 1A 07 00 CF 90 73 00 00 0D 00 00 00
00 00 00 00 C4 52 74 24 94 35 00 30 00 00 00 2A
00 00 00 02 B9 F9 B0 53 07 78 B5 54 1D 33 08 00
20 00 00 00 66 6C 61 67 2E 74 78 74 B9 BA 01 32
42 F3 AF C0 00 B0 92 C2 29 D6 E9 94 16 7C 05 A7
87 08 B2 71 FF C0 42 AE 3D 25 1E 65 53 6F 9A DA
87 C7 74 06 B6 7D 0E 63 16 68 47 66 A8 6E 84 4D
C8 1A A2 C7 2C 71 34 8D 10 C4 3D 7B 00 40 07 00
是一个rar的压缩包,密码是35c535765e50074a,得到flag
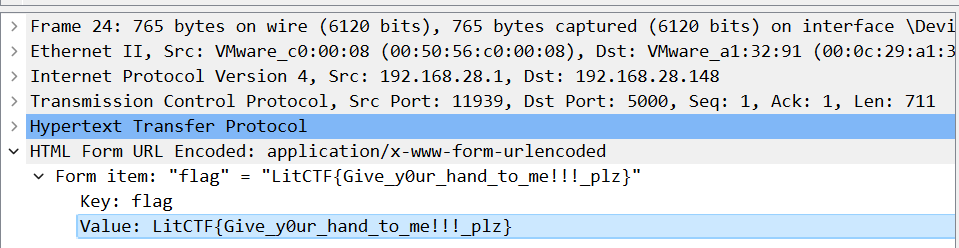
8. [LitCTF 2023]Take me hand (初级)
过滤HTTP
9. [NISACTF 2022]破损的flag
USB的键盘流量
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# python main.py usbdata.pcapng
Running as user "root" and group "root". This could be dangerous.
[+] Found : ujkonjk,tfvbhyhjipokrdcvgrdcvgpokqwsztfvbhujkowazxdqasewsdrpokxdfviklpnjkwsdrrfgyrdcvguhnmkbhjmyhji
得到密文
ujkonjk,tfvbhyhjipokrdcvgrdcvgpokqwsztfvbhujkowazxdqasewsdrpokxdfviklpnjkwsdrrfgyrdcvguhnmkbhjmyhji
这是键盘密码
是一个键盘密码,解法是这样的
键盘上 ujko 四个字符把 i 包围起来
njk 把 m 围起来
tfvbh 中间的是 g
yhji 围得是 u
以此类推得到
i m g u l f f l a g i s w e l c o m e t f j n u
分一下:
im gulf flag is welcome t fjnu
flag有破损,依据题目描述 t 要自行补全为 to,flag为
NSSCTF{welcome_to_fjnu}
10. [HGAME 2022 week1]好康的流量
SMTP是一种提供可靠且有效的电子邮件传输的协议
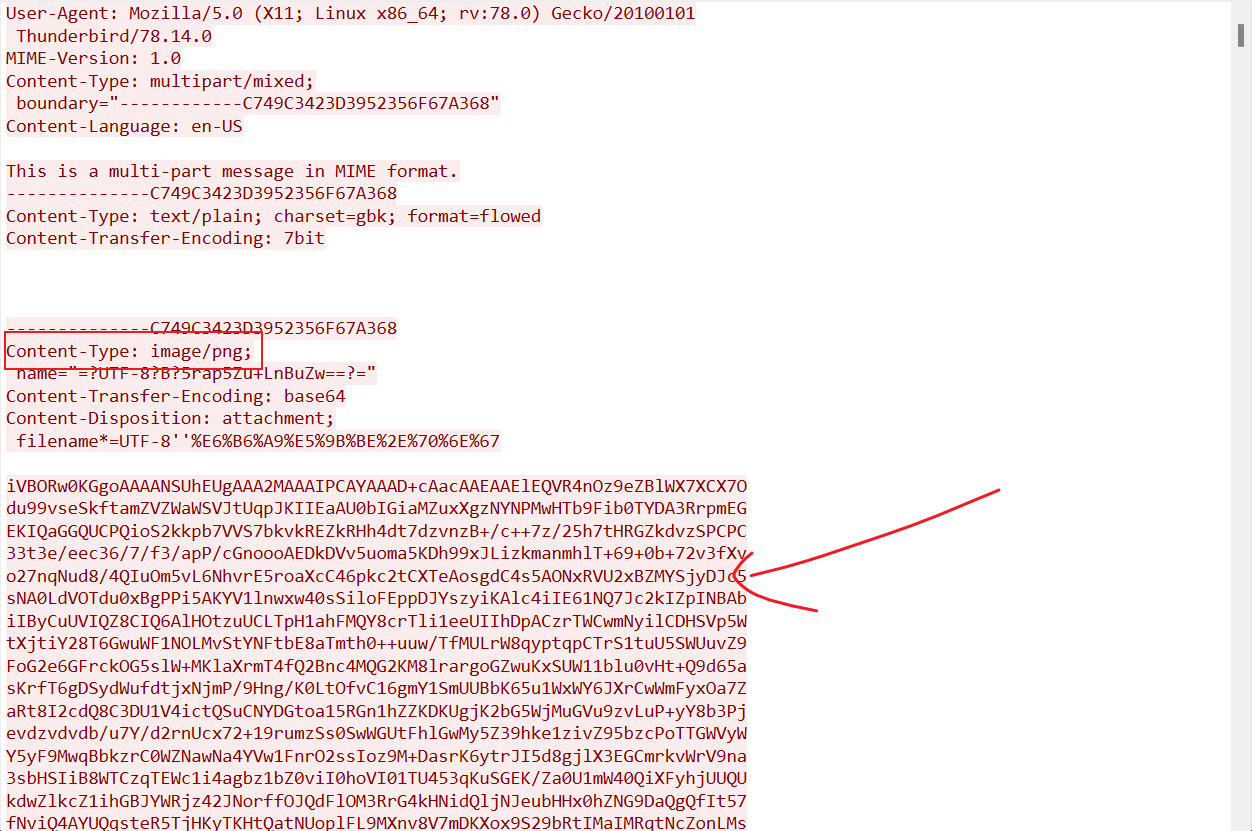
base64转图片后,LSB解密有数据
图片通道里有一张条形码
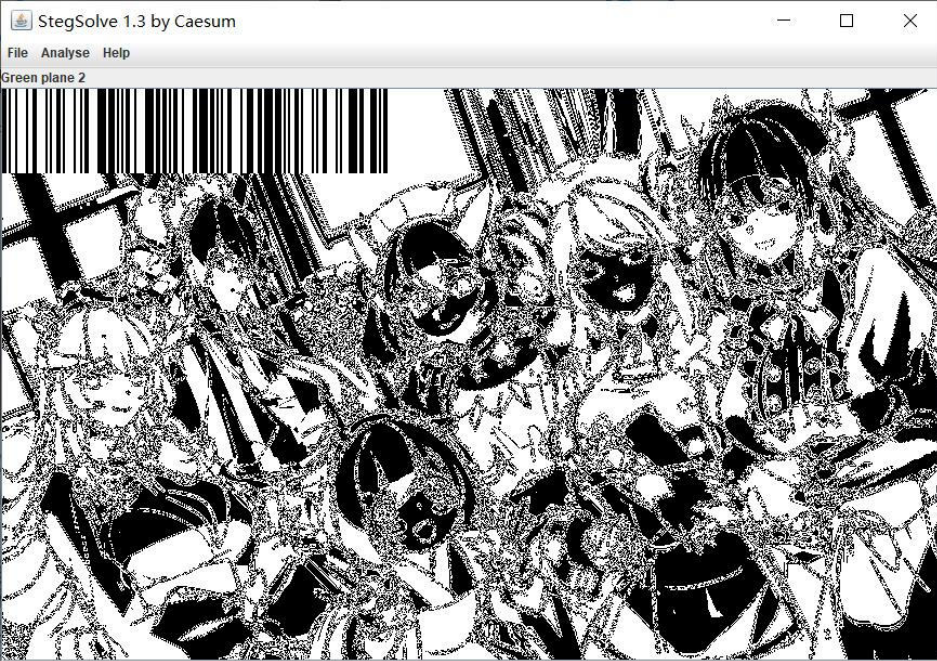
扫
标签:分析,flag,流量,ChR,ret,print,0x65,0x74,NSSCTF From: https://www.cnblogs.com/C0rr3ct/p/18170643