创建私钥
openssl genrsa -out etcd.key 2048
创建CSR,包含sujectAltName(IP)
openssl req \ -new \ -key etcd.key \ -out etcd.csr \ -subj "/C=CN/ST=Beijing/L=Beijing/O=DC/OU=System/CN=etcd" \ -reqexts SAN \ -config <(printf "[req]\ndistinguished_name=req\n[SAN]\nsubjectAltName=IP:127.0.0.1,IP:10.92.21.102,IP:10.92.21.103,IP:10.92.21.109")
查看CSR
openssl req -in etcd.csr -text -noout
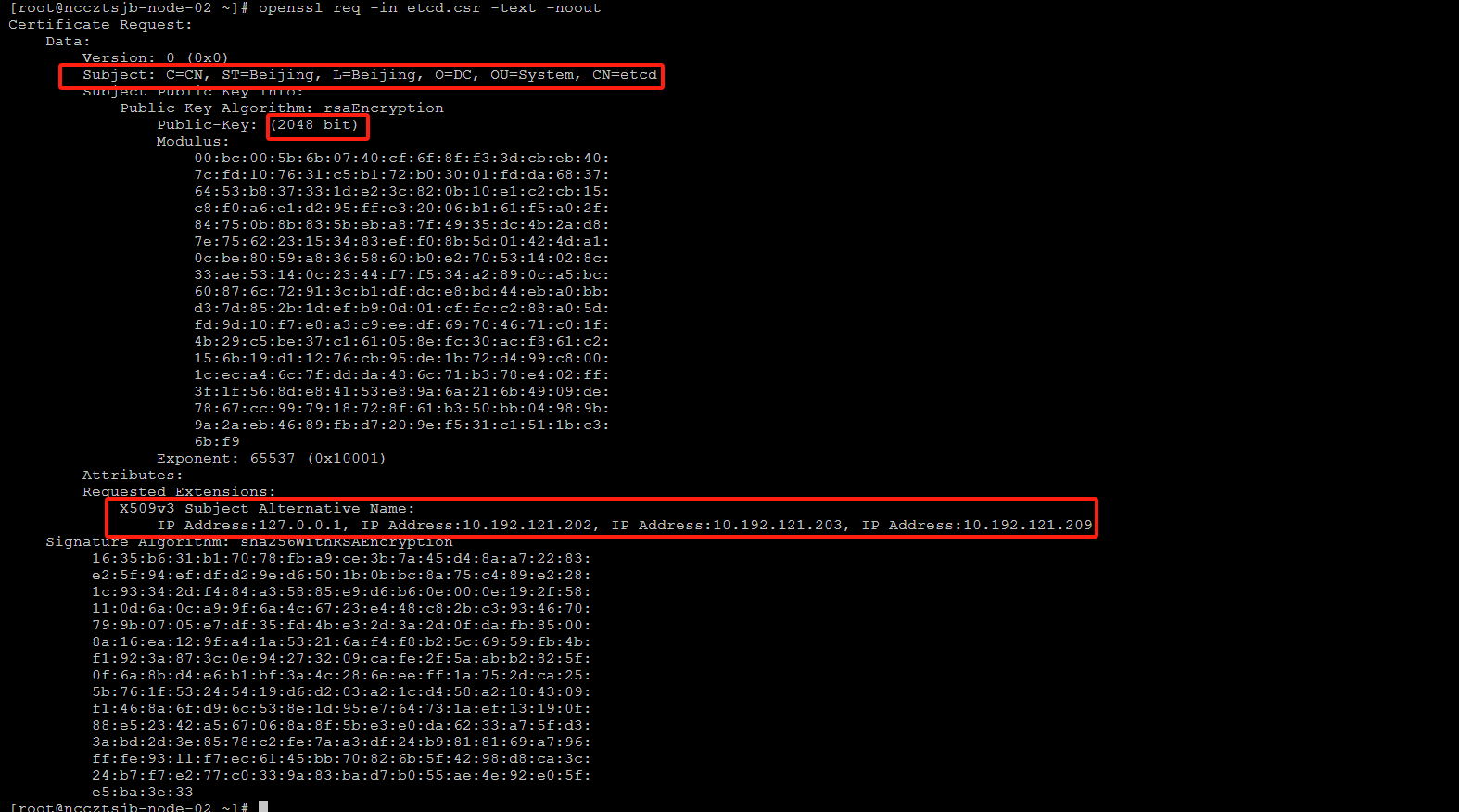
使用CA对CSR签名,生成证书
openssl x509 -req \ -CA /etc/ssl/etcd/ssl/ca.pem \ -CAkey /etc/ssl/etcd/ssl/ca-key.pem \ -CAcreateserial \ -in etcd.csr \ -out etcd.pem \ -extfile <(printf "subjectAltName = IP:127.0.0.1,IP:10.192.121.202,IP:10.192.121.203,IP:10.192.121.209") \ -days 7300
- -days 表示证书的过期时间,单位是天,这里是20年。
查看证书
openssl x509 -in etcd.pem -text -noout
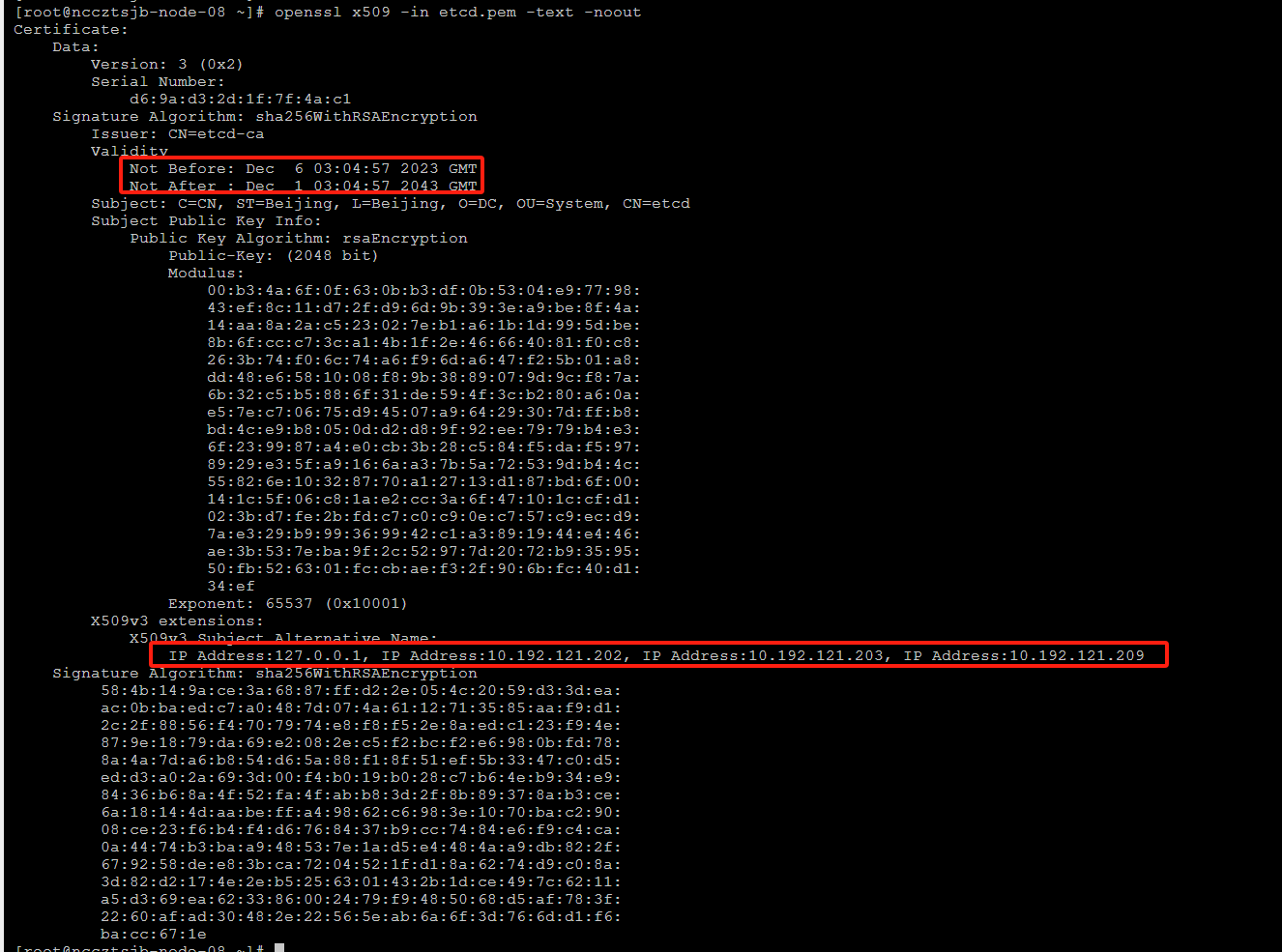
这样,在证书里面,就包含了subjectAltName,这里面是用的IP地址,也可以用多个域名,使用DNS的方式
标签:crs,证书,IP,ca,openssl,ssl,etcd,pem From: https://www.cnblogs.com/chuanzhang053/p/17879094.html