还是先复习前面内容,再学习新知识。
..............
.............
............
T10.dp泄露
一.题目:
from Crypto.Util.number import *
flag = b'NSSCTF{******}' + b'1'*100
p = getPrime(512)
q = getPrime(512)
n = p*q
e = 65537
d = inverse(e, (p-1)*(q-1))
dp = d % (p-1)
m = bytes_to_long(flag)
c = pow(m, e, n)
print(f'n = {n}')
print(f'c = {c}')
print(f'dp = {dp}')
'''
n = 79201858340517902370077926747686673001645933420450220163567700296597652438275339093680329918615445030212417351430952656177171126427547284822789947152085534939195866096891005587613262293569611913019639653984932469691636338705418303482885987114085769045348074530172292982433373154900841135911548332400167290083
c = 70109332985937768446301118795636999352761371683181615470371772202170324747707233792154935611826981798791499937601162039878070094663516868746240133223110650205575807753345252087103328657073552992431511929172241702073381723302143955977662087561904058172777520360991685289300855900793806183473523998422682944404
dp = 3098334089252415941833934532457314870210700261428241562420857845879512952043729097866485406309479489101668423603305497982177150304625615059119312238777275
'''
关键步骤:给了dp,也了给e,失去了dq
dp = d % (p-1)
二.解题思路以及wp:
1.思路:化简dp解p,
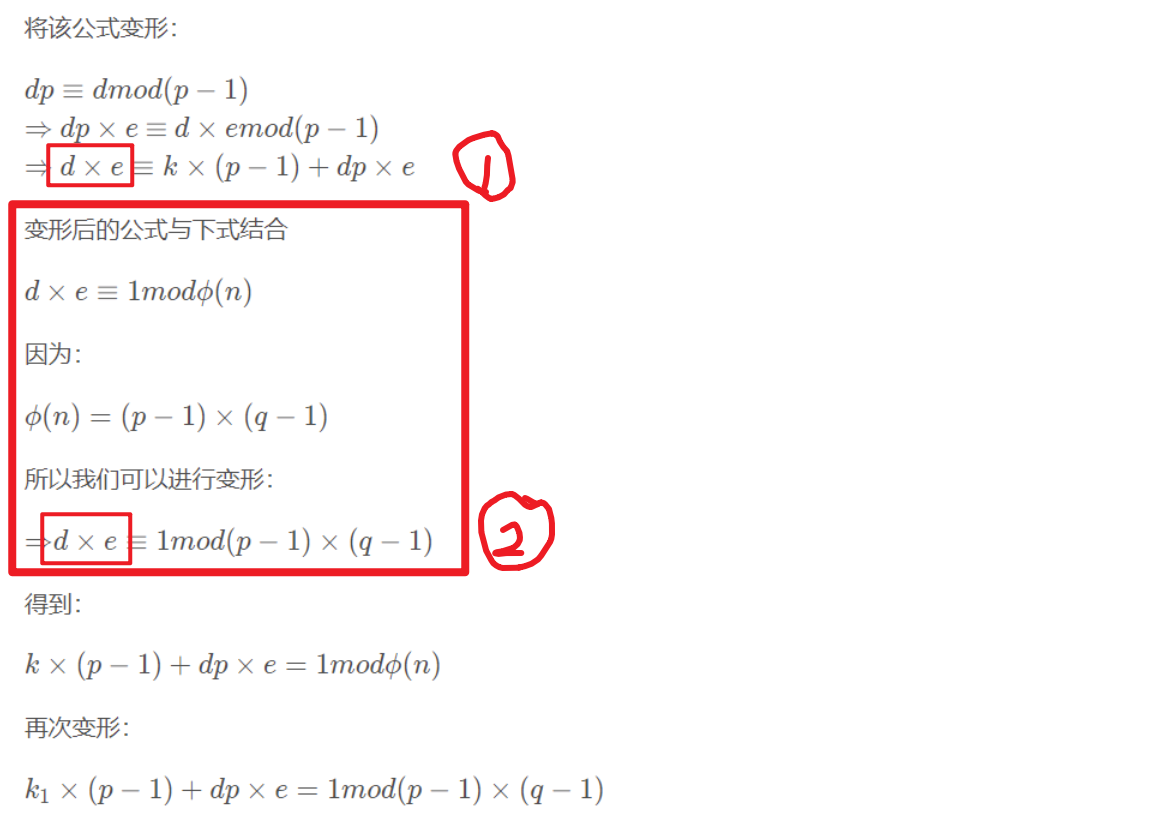
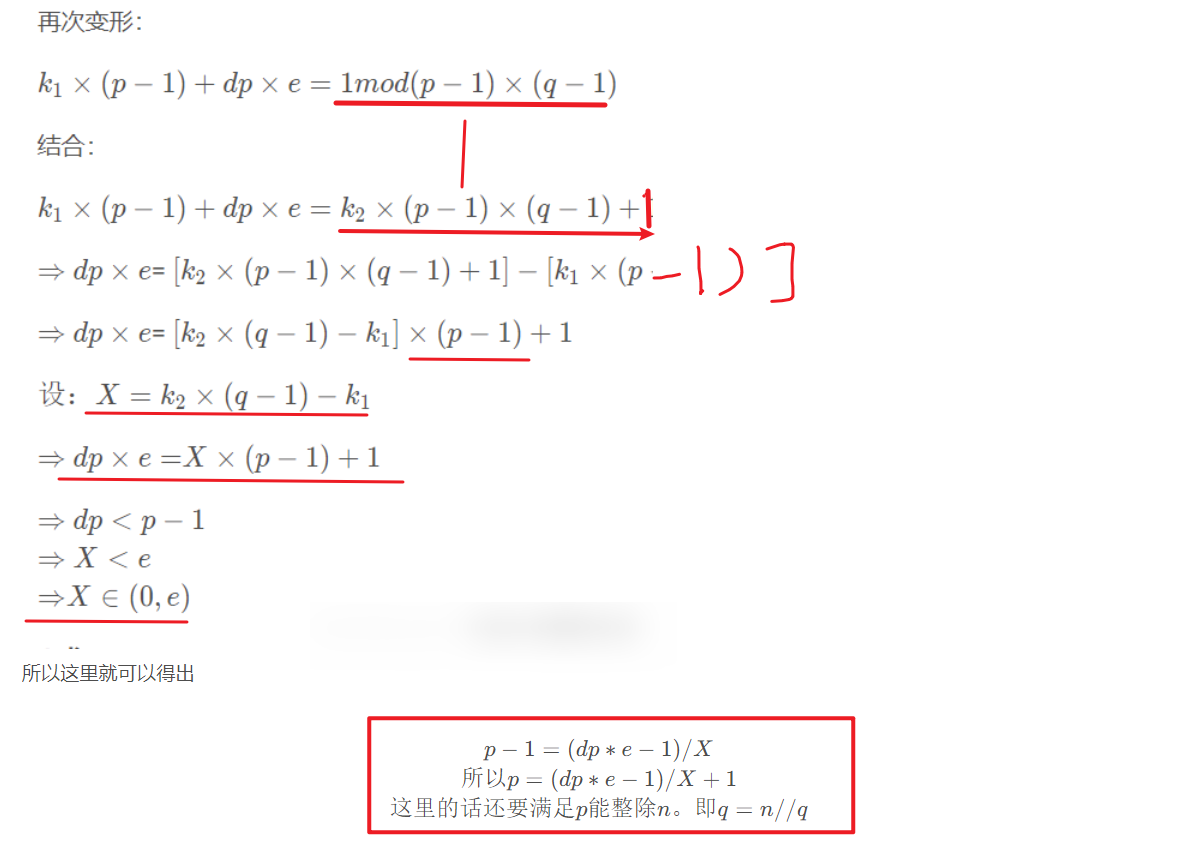
2.条件: e小且X属于(0,e)
from Crypto.Util.number import *
from gmpy2 import *
n = 79201858340517902370077926747686673001645933420450220163567700296597652438275339093680329918615445030212417351430952656177171126427547284822789947152085534939195866096891005587613262293569611913019639653984932469691636338705418303482885987114085769045348074530172292982433373154900841135911548332400167290083
c = 70109332985937768446301118795636999352761371683181615470371772202170324747707233792154935611826981798791499937601162039878070094663516868746240133223110650205575807753345252087103328657073552992431511929172241702073381723302143955977662087561904058172777520360991685289300855900793806183473523998422682944404
dp = 3098334089252415941833934532457314870210700261428241562420857845879512952043729097866485406309479489101668423603305497982177150304625615059119312238777275
e = 65537
for k in range(1, e):
if (e * dp - 1) % k == 0:
p = (e * dp - 1) // k + 1
if n % p == 0:
q = n // p
d = invert(e, (p - 1) * (q - 1))
m = powmod(c, d, n)
break
print(long_to_bytes(m))
T11.e很大的dp泄露攻击
一.题目:
from Crypto.Util.number import *
flag = b'NSSCTF{******}' + b'1'*80
p = getPrime(512)
q = getPrime(512)
n = p*q
e = getPrime(128)
d = inverse(e, (p-1)*(q-1))
dp = d % (p-1)
m = bytes_to_long(flag)
c = pow(m, e, n)
print(f'n = {n}')
print(f'e = {e}')
print(f'c = {c}')
print(f'dp = {dp}')
'''
n = 108280026722298796068968170303156759745471686664814404724171434502249429011870583595808692893118419248225924869164875379709992190884930717654004006466664403479467573176438601715156464950045121937338569942817256182277141174728470067308962244296992229214749863655518517510026063088263849891990324547823192559069
e = 305691242207901867366357529364270390903
c = 26537258289122728220745496185201994733321402056894636636642710319261241111675937946139938310952968353253866895253865273981912174303818938005932883052177988834834575591342856235464380238486868448329727891268391728758132913642966389278296932186703733187105516710825918064228397602264185334108934765627411913661
dp = 2656631506624565349527023729530989647164022271235521672257622068579788839123502046687139927161669209201953909023994372208117081512139181611949631467292513
'''
关键步骤: 有dp,但是e很大,比起T10来说
e = getPrime(128)
d = inverse(e, (p-1)*(q-1))
dp = d % (p-1)
二.解题思路以及代码:
1.思路:


得到公式
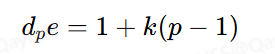
代到下面公式
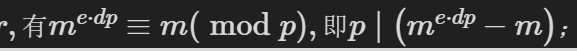
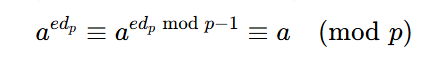
得到

2.解题代码
from Crypto.Util.number import *
from gmpy2 import *
n = 108280026722298796068968170303156759745471686664814404724171434502249429011870583595808692893118419248225924869164875379709992190884930717654004006466664403479467573176438601715156464950045121937338569942817256182277141174728470067308962244296992229214749863655518517510026063088263849891990324547823192559069
e = 305691242207901867366357529364270390903
c = 26537258289122728220745496185201994733321402056894636636642710319261241111675937946139938310952968353253866895253865273981912174303818938005932883052177988834834575591342856235464380238486868448329727891268391728758132913642966389278296932186703733187105516710825918064228397602264185334108934765627411913661
dp = 2656631506624565349527023729530989647164022271235521672257622068579788839123502046687139927161669209201953909023994372208117081512139181611949631467292513
m = 10007
p = gcd(powmod(m, e*dp, n) - m, n)
q = n // p
d = invert(e, (p - 1) * (q - 1))
m = powmod(c, d, n)
print(long_to_bytes(m))
#NSSCTF{p_leak_but_with_huge_e}
利用风佬工具一把梭
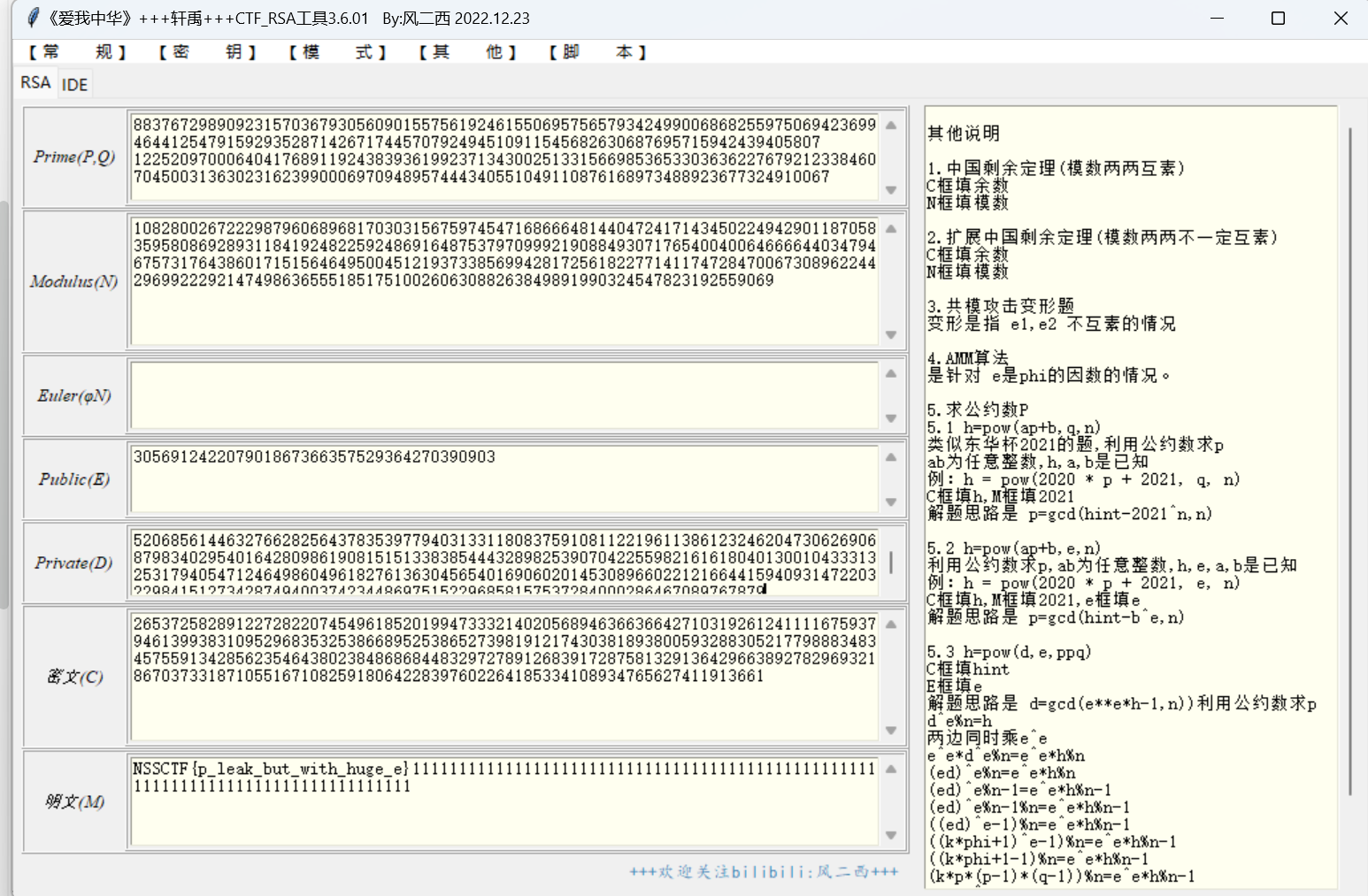
第一步:填入n,c,e,dp填在d那行,选择仅dp攻击
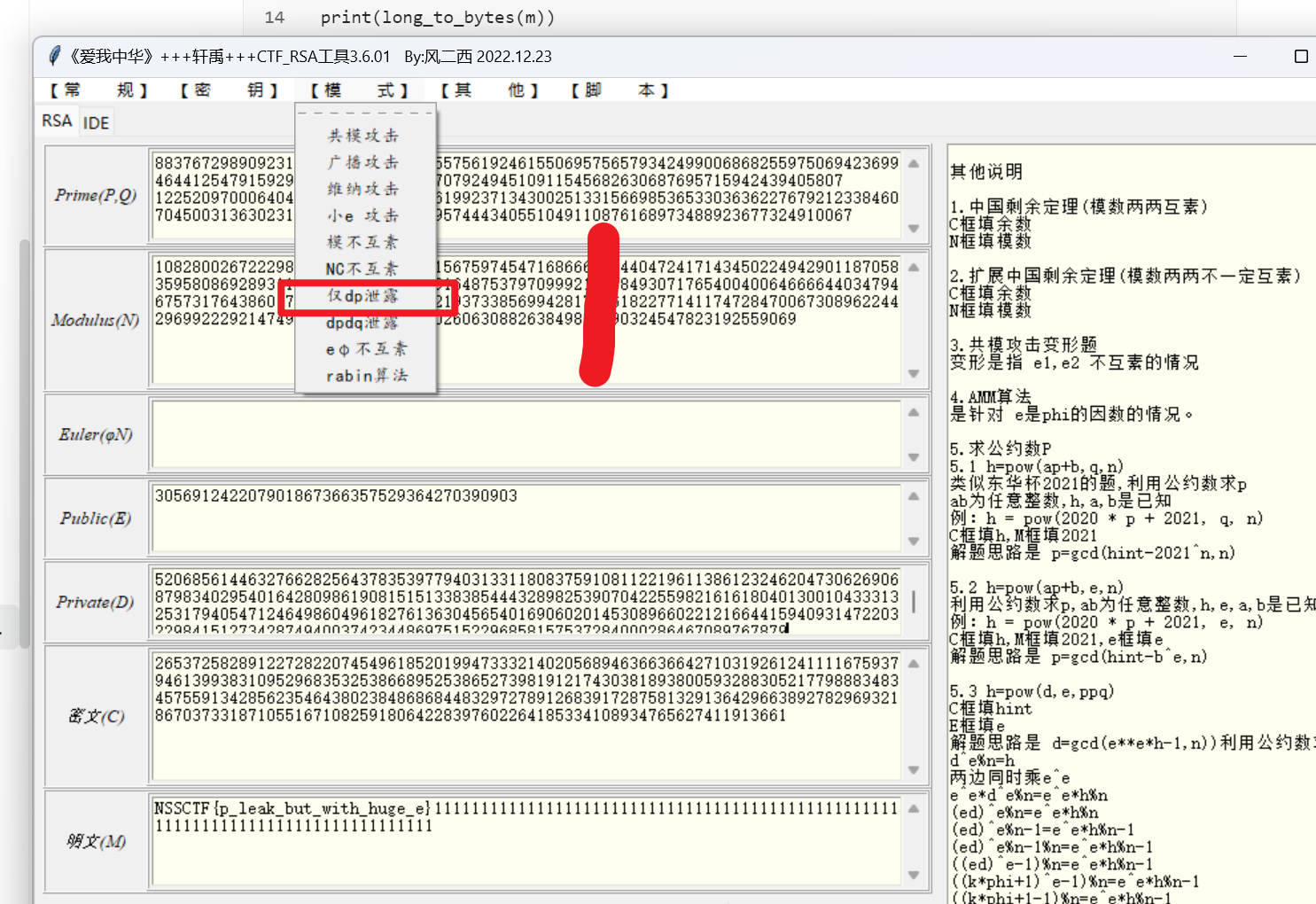
第二步,现在以及有了p,q,直接计算d,再计算明文,明文转字符得到flag
结语:
看一些详细算法耽误了时间,有一些新算法没有理解,换以前可以就停下来了,但是现在,需要去想要怎样解决,觉得实在是有点难,就先学其他的,后面再来深究。
标签:进阶,bytes,RSA,---,flag,getPrime,print,import,dp From: https://www.cnblogs.com/yanxiao777/p/18391956