前言
在实际开发过程中,如果后端需要启用https访问,通常项目启动后配置nginx代理再配置https,前端调用时高版本的chrome还会因为证书未信任导致调用失败,通过摸索整理一套开发调试下的https方案,特此分享
后端配置
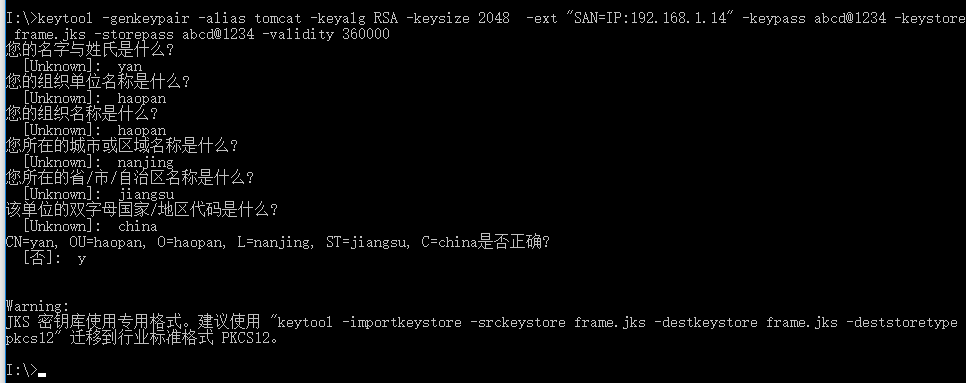
生成HTTPS密钥
keytool -genkeypair -alias tomcat -keyalg RSA -keysize 2048 -ext "SAN=IP:192.168.1.14" -keypass abcd@1234 -keystore frame.jks -storepass abcd@1234 -validity 360000
SAN需要设置你自己电脑的固定ip
配置SSL访问
这里以2.0.0.RELEASE版本为例
server:
ssl:
key-store: classpath:systemfile/frame.jks
key-store-password: abcd@1234
key-store-type: JKS
key-alias: tomcat
如果需要打包部署测试环境,需要添加以下配置将jks密钥排除在外
<resources>
<resource>
<filtering>true</filtering>
<directory>src/main/resources</directory>
<excludes>
<exclude>**/*.jks</exclude>
</excludes>
</resource>
<resource>
<filtering>false</filtering>
<directory>src/main/resources</directory>
<includes>
<include>**/*.jks</include>
</includes>
</resource>
</resources>
创建TomcatConfig配置信任
@Configuration
public class TomcatConfig {
@Bean
public TomcatServletWebServerFactory servletContainer() {
TomcatServletWebServerFactory tomcatServletContainerFactory = new TomcatServletWebServerFactory() {
@Override
protected void postProcessContext(Context context) {
SecurityConstraint constraint = new SecurityConstraint();
constraint.setUserConstraint("CONFIDENTIAL");
SecurityCollection collection = new SecurityCollection();
collection.addPattern("/*");
constraint.addCollection(collection);
context.addConstraint(constraint);
}
};
tomcatServletContainerFactory.addConnectorCustomizers(new FrameTomcatConnectorCustomizer());
return tomcatServletContainerFactory;
}
}
浏览器设置
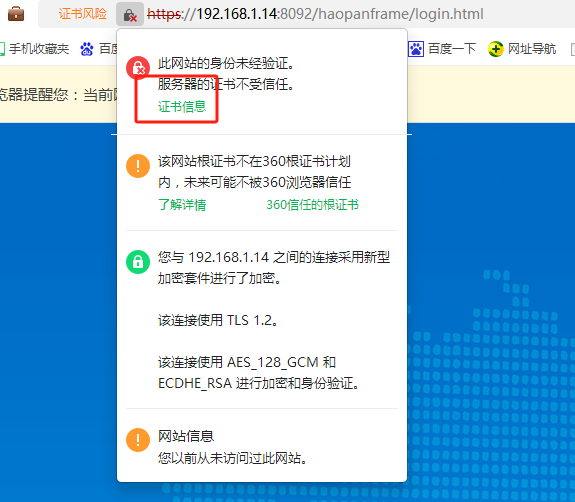
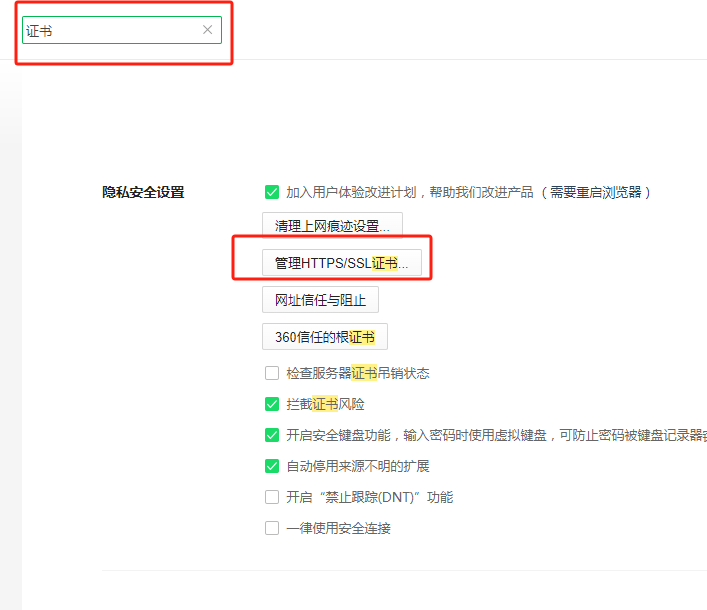
使用360浏览器访问系统后台管理地址,点击地址栏的查看证书并导出
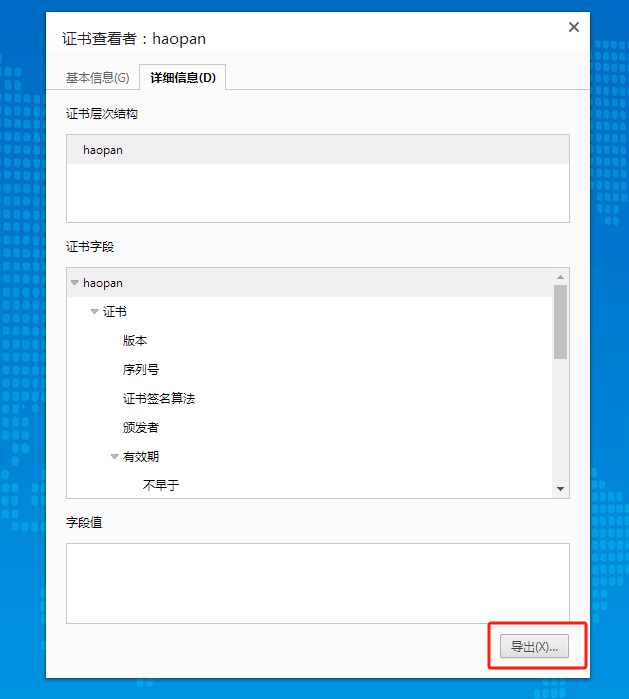
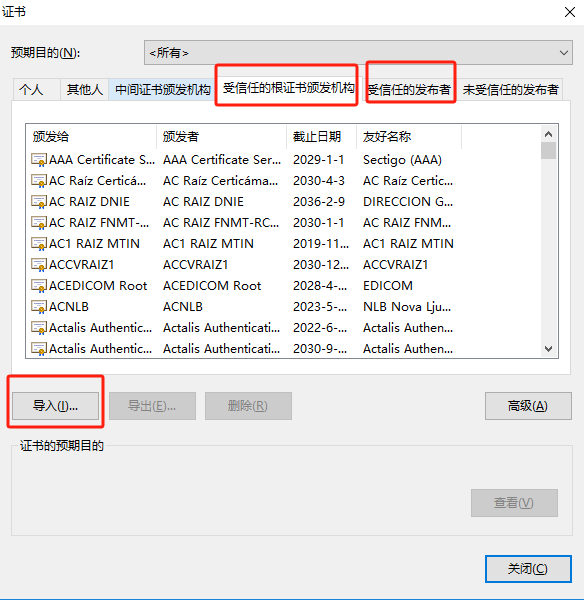
打开360浏览期设置,搜索证书,配置SSL证书,在受信任的根证书派发机构和受信任的发布者两个tab下导入刚才导出的证书
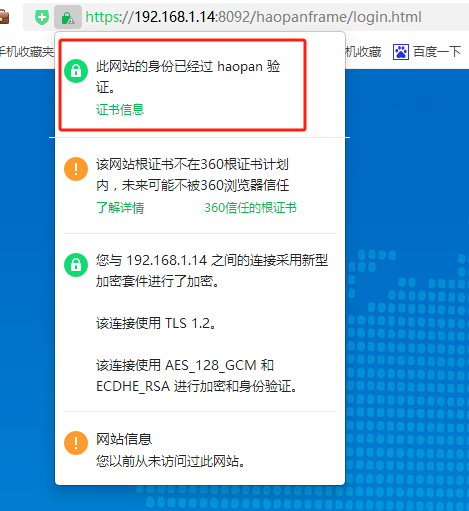
关闭浏览器重新打开,访问系统地址,地址栏锁变绿则代表配置成功
开发调试
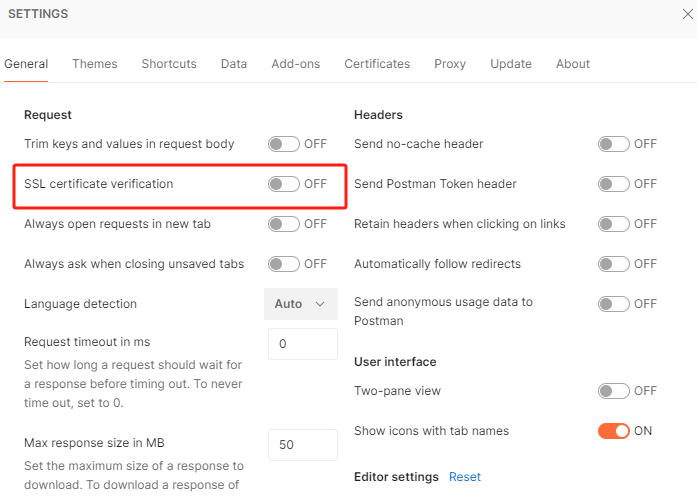
postman在调试https接口时在Setting目录关闭SSL验证