DASCTF
prese
一眼控制了平坦化,可以用d810梭一下
跟进一下main_crypto这个函数
主要是两部分,第一部分是生成一个256大小的数组,通过输入的长度和遍历生成的一个数组
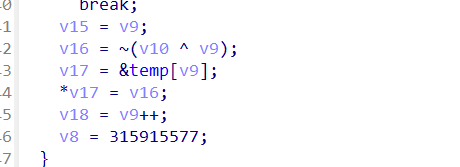
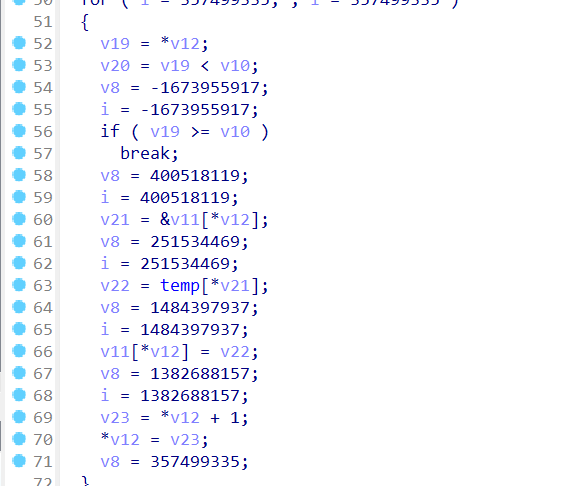
第二部分就是主要的加密过程,那些杂七杂八的值完全可以不用看,其实就是一个找索引的题,然后猜一下输入的长度
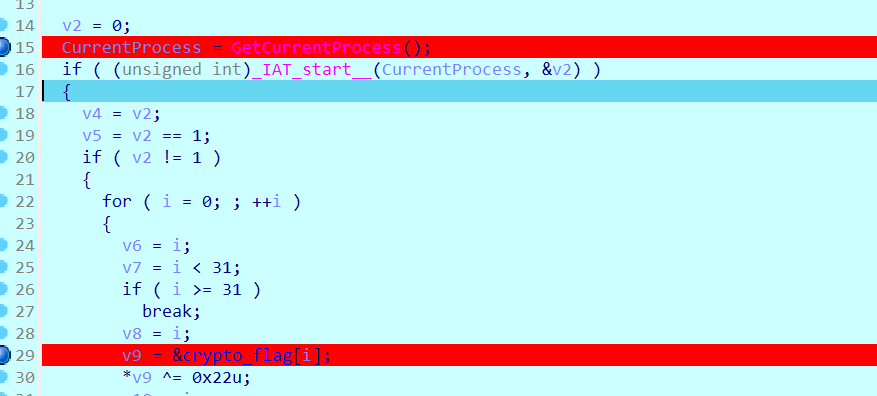
当时做的时候很奇怪的答案,后面又仔细看了看,发现crypoto_flag被劫持了,然后异或了一个0x22
enc = [0x86, 0x83, 0x91, 0x81, 0x96, 0x84, 0xB9, 0xA5, 0xAD, 0xAD,
0xA6, 0x9D, 0xB6, 0xAA, 0xA7, 0x9D, 0xB0, 0xA7, 0x9D, 0xAB,
0xB1, 0x9D, 0xA7, 0xA3, 0xB1, 0xBB, 0xAA, 0xAA, 0xAA, 0xAA,
0xBF]
sb=[]
for i in range(256):
sb.append((~(len(enc)^i))%256)
for i in range(len(enc)):
a=sb.index(enc[i])
print(chr(a^0x22),end='')
ezVM
输入key的第一个函数
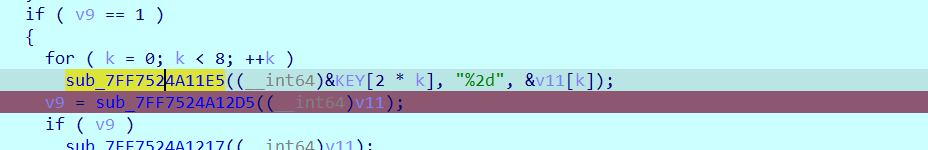
对输入的key做了处理,根据输入前后可以猜测是两位两位为一组,然后第一位做十位,第二位做个位。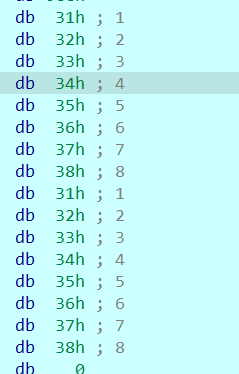
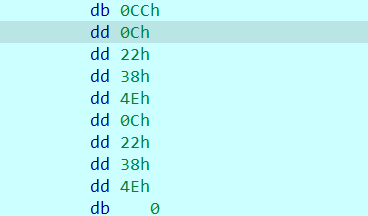
然后处理的结果作为参数传到第二个函数里面,识别了三个参数其实只有一个参数所以可以手动改一下
类型转换,其实这下v10就是key了,v9的数组是给死了的,所以执行的过程是一样的,可以动态调试慢慢试
最后可以模拟打印堆栈
from z3 import *
v9=[0]*93
v9[0] = 162
v9[1] = 0
v9[2] = 132
v9[3] = 163
v9[4] = 8
v9[5] = 0
v9[6] = 163
v9[7] = 8
v9[8] = 1
v9[9] = 176
v9[10] = 8
v9[11] = 316
v9[12] = 178
v9[13] = 163
v9[14] = 9
v9[15] = 1
v9[16] = 163
v9[17] = 9
v9[18] = 2
v9[19] = 163
v9[20] = 9
v9[21] = 3
v9[22] = 176
v9[23] = 9
v9[24] = 158
v9[25] = 178
v9[26] = 166
v9[27] = 4
v9[28] = 22
v9[29] = 163
v9[30] = 0
v9[31] = 4
v9[32] = 176
v9[33] = 0
v9[34] = 889
v9[35] = 178
v9[36] = 164
v9[37] = 5
v9[38] = 11
v9[39] = 161
v9[40] = 8
v9[41] = 5
v9[42] = 163
v9[43] = 8
v9[44] = 6
v9[45] = 176
v9[46] = 8
v9[47] = 38
v9[48] = 178
v9[49] = 163
v9[50] = 7
v9[51] = 6
v9[52] = 176
v9[53] = 7
v9[54] = 96
v9[55] = 178
v9[56] = 161
v9[57] = 9
v9[58] = 1
v9[59] = 163
v9[60] = 9
v9[61] = 2
v9[62] = 165
v9[63] = 9
v9[64] = 5
v9[65] = 176
v9[66] = 9
v9[67] = 111
v9[68] = 178
v9[69] = 166
v9[70] = 5
v9[71] = 7
v9[72] = 161
v9[73] = 8
v9[74] = 0
v9[75] = 165
v9[76] = 8
v9[77] = 6
v9[78] = 163
v9[79] = 8
v9[80] = 5
v9[81] = 176
v9[82] = 8
v9[83] = 859
v9[84] = 178
v9[85] = 163
v9[86] = 3
v9[87] = 4
v9[88] = 176
v9[89] = 3
v9[90] = 706
v9[91] = 178
v9[92] = 192
key=[0]*11
v7=0
while v9[v7] != 192:
if ( v9[v7] == 160 ):
# v10[v9[v7 + 1]] = v9[v7 + 2]
print("v10[",v9[v7 + 1],"] = ",v9[v7 + 2])
v7 += 3
if ( v9[v7] == 161 ):
# v10[v9[v7 + 1]] = v10[v9[v7 + 2]]
print("v10[",v9[v7 + 1],"] = v10[",v9[v7 + 2],"]")
v7 += 3
if ( v9[v7] == 162 ):
# v10[v9[v7 + 1]] += v9[v7 + 2]
print("v10[",v9[v7 + 1],"] += ",v9[v7 + 2])
v7 += 3
if ( v9[v7] == 163 ):
# v10[v9[v7 + 1]] += v10[v9[v7 + 2]]
print("v10[",v9[v7 + 1],"] += v10[",v9[v7 + 2],"]")
v7 += 3
if ( v9[v7] == 164 ):
# v10[v9[v7 + 1]] -= v9[v7 + 2]
print("v10[",v9[v7 + 1],"] -= ",v9[v7 + 2])
v7 += 3
if ( v9[v7] == 165 ):
# v10[v9[v7 + 1]] -= v10[v9[v7 + 2]]
print("v10[",v9[v7 + 1],"] -= v10[",v9[v7 + 2],"]")
v7 += 3
if ( v9[v7] == 166 ):
# v10[v9[v7 + 1]] *= v9[v7 + 2]
print("v10[",v9[v7 + 1],"] *= ",v9[v7 + 2])
v7 += 3
if ( v9[v7] == 167 ):
# v10[v9[v7 + 1]] *= v10[v9[v7 + 2]]
print("v10[",v9[v7 + 1],"] *= v10[",v9[v7 + 2],"]")
v7 += 3
if ( v9[v7] == 176 ):
# v12 = v10[v9[v7 + 1]] == v9[v7 + 2]
print("v12 = v10[",v9[v7 + 1],"] == ",v9[v7 + 2])
v7 += 3
if ( v9[v7] == 177 ):
# v12 = v10[v9[v7 + 1]] == v10[v9[v7 + 2]]
print("v12 = v10[",v9[v7 + 1],"] == v10[",v9[v7 + 2],"]")
v7 += 3
if ( v9[v7] == 178 ):
v7+=1
v10[ 0 ] += 132
v10[ 8 ] += v10[ 0 ]
v10[ 8 ] += v10[ 1 ]
v12 = v10[ 8 ] == 316
v10[ 9 ] += v10[ 1 ]
v10[ 9 ] += v10[ 2 ]
v10[ 9 ] += v10[ 3 ]
v12 = v10[ 9 ] == 158
v10[ 4 ] *= 22
v10[ 0 ] += v10[ 4 ]
v12 = v10[ 0 ] == 889
v10[ 5 ] -= 11
v10[ 8 ] = v10[ 5 ]
v10[ 8 ] += v10[ 6 ]
v12 = v10[ 8 ] == 38
v10[ 7 ] += v10[ 6 ]
v12 = v10[ 7 ] == 96
v10[ 9 ] = v10[ 1 ]
v10[ 9 ] += v10[ 2 ]
v10[ 9 ] -= v10[ 5 ]
v12 = v10[ 9 ] == 111
v10[ 5 ] *= 7
v10[ 8 ] = v10[ 0 ]
v10[ 8 ] -= v10[ 6 ]
v10[ 8 ] += v10[ 5 ]
v12 = v10[ 8 ] == 859
v10[ 3 ] += v10[ 4 ]
v12 = v10[ 3 ] == 706
z3约束求解
s=Solver()
v10=[0]*10
for i in range (len(v10)):
v10[i] = BitVec('v10[' + str(i) + ']', 8)
for i in range (len(v10)):
s.add(v10[i] <=99)
s.add(v10[i] >=0)
v10[0] += 132
v10[8] += v10[ 0 ]
v10[8] += v10[ 1 ]
s.add(v10[ 8 ] == 316)
v10[9] += v10[ 1]
v10[9] += v10[ 2]
v10[9 ] += v10[ 3 ]
s.add(v10[ 9 ] == 158)
v10[4 ] *= 22
v10[0 ] += v10[ 4 ]
s.add(v10[ 0 ] == 889)
v10[ 5 ] -= 11
v10[ 8 ] = v10[ 5 ]
v10[ 8 ] += v10[ 6 ]
s.add(v10[ 8 ] == 38)
v10[ 7 ] += v10[ 6 ]
s.add(v10[ 7 ] == 96)
v10[ 9 ] = v10[ 1 ]
v10[ 9 ] += v10[ 2 ]
v10[ 9 ] -= v10[ 5 ]
s.add(v10[ 9 ] == 111)
v10[ 5 ] *= 7
v10[ 8 ] = v10[ 0 ]
v10[ 8 ] -= v10[ 6 ]
v10[ 8 ] += v10[ 5 ]
s.add(v10[ 8 ] == 859)
v10[ 3 ] += v10[ 4 ]
s.add(v10[ 3 ] == 706)
if s.check() == sat:
m=s.model()
print(m)
后面函数动态加载dll里面的函数跟进一下就是一个简单的异或
enc=[0x0D, 0x08, 0x1A, 0x0A, 0x1D, 0x0F, 0x32, 0x78, 0x2A, 0x7B, 0x2A, 0x7B, 0x7C, 0x7D, 0x71, 0x64,
0x7A, 0x2C, 0x7B, 0x7D, 0x64, 0x28, 0x7D, 0x71, 0x2C, 0x64, 0x78, 0x78, 0x7D, 0x7A, 0x64, 0x28,
0x7A, 0x7D, 0x70, 0x7F, 0x28, 0x7A, 0x2B, 0x7E, 0x7D, 0x79, 0x79, 0x34]
for i in range(len(enc)):
enc[i]^=0x49
print(chr(enc[i]),end="")