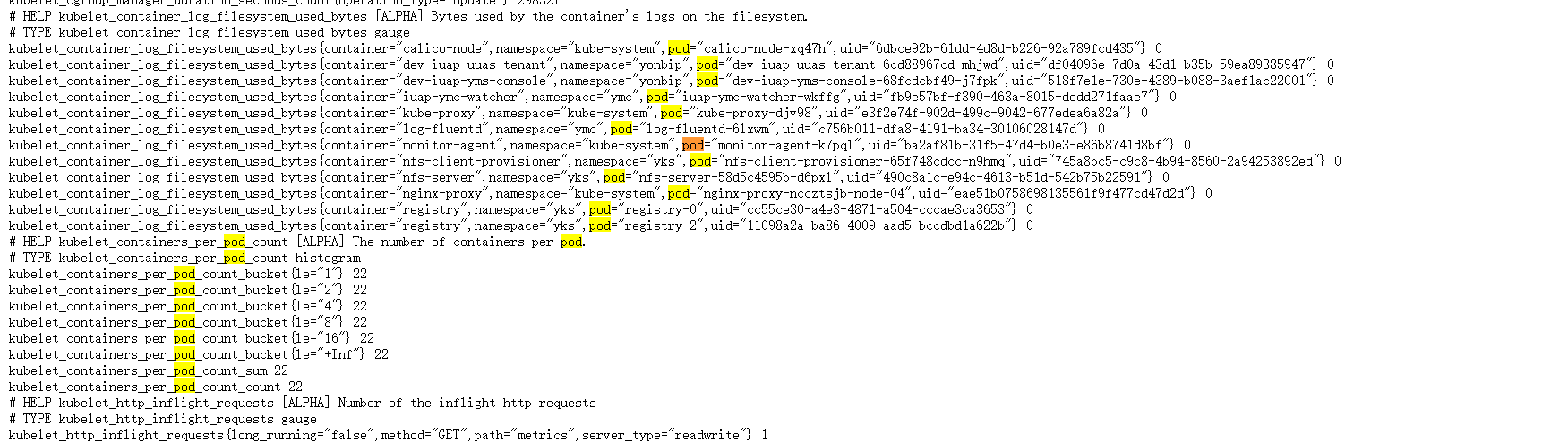
1、背景说明
kubelet本身的10250端口,就提供了节点上的监控数据。
metrics server可以进行访问。
但是,如果想要通过浏览器,或者curl命令进行访问,发现,是需要进行认证
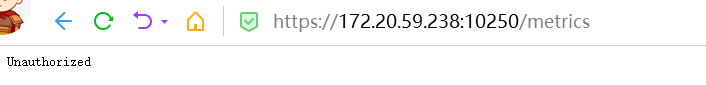
[root@nccztsjb-node-02 ~]# curl -k https://172.20.59.238:10250/metrics
Unauthorized[root@nccztsjb-node-02 ~]#
[root@nccztsjb-node-02 ~]#
那要如何进行访问呢?
2、通过token的方式进行访问
在k8s中,可以通过证书,也可以通过token的方式进行认证和访问。
那么,这个token,从哪里来呢?
就涉及到一个概念,在k8s里面的概念,就是权限的问题,比如clusterrole和serviceaccount的概念。
serviceaccount是k8s里的用户的概念,只要seviceaccount有访问node资源的权限,就可以获取对应的资源的信息了。
通过下面的命令,创建clusterrole,serviceaccount和clusterrolebinding
--- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: node-metrics rules: - apiGroups: - "" resources: - nodes/metrics - nodes/stats - nodes/proxy verbs: - get --- apiVersion: v1 kind: ServiceAccount metadata: name: node-metrics namespace: default --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: node-metrics roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: node-metrics subjects: - kind: ServiceAccount name: node-metrics namespace: default
- 创建集群角色clusterrole node-metrics,有访问nodes资源的权限
- 创建serviceaccount node-metrics,也就是用户
- 创建clusterrolebinding,也就是将用户和角色进行绑定
[root@nccztsjb-node-02 ~]# vi node-metrics-privileges.yaml [root@nccztsjb-node-02 ~]# kubectl apply -f node-metrics-privileges.yaml clusterrole.rbac.authorization.k8s.io/node-metrics unchanged serviceaccount/node-metrics unchanged clusterrolebinding.rbac.authorization.k8s.io/node-metrics unchanged [root@nccztsjb-node-02 ~]#
查看serviceaccount信息
[root@nccztsjb-node-02 ~]# kubectl get serviceaccount node-metrics -o yaml
apiVersion: v1
kind: ServiceAccount
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"v1","kind":"ServiceAccount","metadata":{"annotations":{},"name":"node-metrics","namespace":"default"}}
creationTimestamp: "2023-11-16T08:30:53Z"
name: node-metrics
namespace: default
resourceVersion: "15119522"
selfLink: /api/v1/namespaces/default/serviceaccounts/node-metrics
uid: bfb769eb-733b-45cb-9b7d-a0f82822a435
secrets:
- name: node-metrics-token-zln7v
[root@nccztsjb-node-02 ~]#
其中,secrets里面是用户的认证信息
secrets: - name: node-metrics-token-zln7v
查看secret的详细内容
[root@nccztsjb-node-02 ~]# kubectl get secret node-metrics-token-zln7v -o yaml
apiVersion: v1
data:
ca.crt: LS0tLS1CRUdJcccTiBDRVsdfsdfJUSUZJsdfsdfsQ0FURS0tLS0tCk1JSUMvakNDQWVhZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJek1Ea3dPREE0TURjME5Gb1hEVE16TURrd05UQTRNRGMwTkZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTVpvCkRRVDZrc0MwbUN5L21YYXkzK0xrVzJBNFpINEVWenRkYnpJamtNenlreDVnWkhmN25ZK0Rqdk1wS294a2NrTzAKN05qSTBmc3BIOEZnMU0rUlN5V3JTc1p6KzlWbE1WdnBQS2F4YmtDaDVhSUpibThDL2pmaU1tT1N6akovb05NUgpENVFTWmNCZFFuNEM1YlFGb1pRdUJ2QzRnNExTYlFVSDR3eURUcUFnZ2RsZHZRamZuTUNWUzdvcVpBSnpTeDVqCnI0SEhvSUFSdXhWUVJjWENaUVR2SVZuM1dpY0NoRFo3am1aVm85MTlidW4yNXQwUWZMcWFReWxHYjRhSERMMloKSXJOUDlEK2xPcERTckozMzZ0ZFhwTWF0TTNxSDlHMXJmRkpMRHF1OFNVVGV6ZnVVcjBXU0x3Wi9BdDM1Vm1ieApQUEZOcWxkZUFnQ0hEUURwTWlFQ0F3RUFBYU5aTUZjd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZNWjlIWlZaVUp6aDFFcFdidlFvRzRmeFVtditNQlVHQTFVZEVRUU8KTUF5Q0NtdDFZbVZ5Ym1WMFpYTXdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBQnJ5MVBhU3JXVUhBOHAzM05TegorQ3BiVHVTVGttcTJNS1FrbitNd1NRWEZLSHVIT0FlcEVzY2RHKzdPVUhiQ1J1UWEyOEtJbUlGR2Rxa0lUYllBCnNmKzg3Q0psV21ZOVRBRUI2Y2kwcS9yWklqMk8xVlFuaTJjbVA3RzRjSldaU0pzVGtqM2JsVTRkZEhCeERReWIKcDYxVmNTRU9lckYvTlMvdGFoSkt6em56VG1rc3dZWU5wS0VwUXZGVkl2QjA2S1ZVQWpDck9UYkxsTzdIbU1UNwoyUkxGaFR4cjZMbXR1d1FFb0EzVEtCL3d5bWp5ZjRWQlM4Wi9Ndit4eGFucDViTjJFNHhCd3RoY21tZzBGZXVvCjNjbTRnQ2Z4anQvM09SNSt5eTJNNlBobTRpaUtlOE5pQTk2S3RtV0xvL2VLL2k4bm96VGhJZVBOOVprdFY3aFMKWnh3PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
namespace: ZGVmYXVsdA==
token: ZXlKaGJHY2lPaUpTVXpJMU5pSXNJsdfsdffsfbXRwWkNJNklqTjFRWFJ5WVhVeFdFSlJZa0pZU205M2FHeE5kVTE2Vm1KM04yeFBlVGhwYWxCMWNVdGxjMEZLVjJzaWZRLmV5SnBjM01pT2lKcmRXSmxjbTVsZEdWekwzTmxjblpwWTJWaFkyTnZkVzUwSWl3aWEzVmlaWEp1WlhSbGN5NXBieTl6WlhKMmFXTmxZV05qYjNWdWRDOXVZVzFsYzNCaFkyVWlPaUprWldaaGRXeDBJaXdpYTNWaVpYSnVaWFJsY3k1cGJ5OXpaWEoyYVdObFlXTmpiM1Z1ZEM5elpXTnlaWFF1Ym1GdFpTSTZJbTV2WkdVdGJXVjBjbWxqY3kxMGIydGxiaTE2Ykc0M2RpSXNJbXQxWW1WeWJtVjBaWE11YVc4dmMyVnlkbWxqWldGalkyOTFiblF2YzJWeWRtbGpaUzFoWTJOdmRXNTBMbTVoYldVaU9pSnViMlJsTFcxbGRISnBZM01pTENKcmRXSmxjbTVsZEdWekxtbHZMM05sY25acFkyVmhZMk52ZFc1MEwzTmxjblpwWTJVdFlXTmpiM1Z1ZEM1MWFXUWlPaUppWm1JM05qbGxZaTAzTXpOaUxUUTFZMkl0T1dJM1pDMWhNR1k0TWpneU1tRTBNelVpTENKemRXSWlPaUp6ZVhOMFpXMDZjMlZ5ZG1salpXRmpZMjkxYm5RNlpHVm1ZWFZzZERwdWIyUmxMVzFsZEhKcFkzTWlmUS5id1pBaXRwLTY0ek5sRTBVb1dXUGVLdWpjcllZdE5IeVB0X2FiWDU5VVU3XzNLcDctVi1IWGJCdTZYVFNWQVdVUlZwc2FWRy1zcUVZd2pmZW9VeVZLdktITXJ0elJWS0xuUnMyTWl2Um9fdzBHWE5MR1Naa2NtdU1VajdMYTdNb2ZiM3o2OFpLXzllRURSRHpWcUEzQUladnNZcTh1V0c5Q3BROFhKNG8wTzVEdUF3aFFuN0d5MFVDUGVJODB2bmVrVzFaaDdWT000UjUzc1l3aFgzSzRCM20wc0Q2MW1sTE83NmJKbVE1aWlacUFMb1RlTXFhYWdoR3B5bmJma3ZBajVxRVg4MHRwTl9WYWpJS0hKa0sybWFCYk44OW9uRFVDR2p5SGJrS3B3dWVYdkhZU2psU21PeHhicTJERjJuUDNhOXRTOUlCd2tOdmswRTZFeWQ4bkE=
kind: Secret
metadata:
annotations:
kubernetes.io/service-account.name: node-metrics
kubernetes.io/service-account.uid: bfb769eb-733b-45cb-9b7d-a0f82822a435
creationTimestamp: "2023-11-16T08:30:53Z"
name: node-metrics-token-zln7v
namespace: default
resourceVersion: "15119521"
selfLink: /api/v1/namespaces/default/secrets/node-metrics-token-zln7v
uid: 61d45eb4-9293-4a3a-93cd-66e12a90bf05
type: kubernetes.io/service-account-token
[root@nccztsjb-node-02 ~]#
可以看到token的信息
token: ZXlKaGJHY2lPaUpTVXpJMU5psdfsdfsfdsfSXNJbXRwWkNJNklqTjFRWFJ5WVhVeFdFSlJZa0pZU205M2FHeE5kVTE2Vm1KM04yeFBlVGhwYWxCMWNVdGxjMEZLVjJzaWZRLmV5SnBjM01pT2lKcmRXSmxjbTVsZEdWekwzTmxjblpwWTJWaFkyTnZkVzUwSWl3aWEzVmlaWEp1WlhSbGN5NXBieTl6WlhKMmFXTmxZV05qYjNWdWRDOXVZVzFsYzNCaFkyVWlPaUprWldaaGRXeDBJaXdpYTNWaVpYSnVaWFJsY3k1cGJ5OXpaWEoyYVdObFlXTmpiM1Z1ZEM5elpXTnlaWFF1Ym1GdFpTSTZJbTV2WkdVdGJXVjBjbWxqY3kxMGIydGxiaTE2Ykc0M2RpSXNJbXQxWW1WeWJtVjBaWE11YVc4dmMyVnlkbWxqWldGalkyOTFiblF2YzJWeWRtbGpaUzFoWTJOdmRXNTBMbTVoYldVaU9pSnViMlJsTFcxbGRISnBZM01pTENKcmRXSmxjbTVsZEdWekxtbHZMM05sY25acFkyVmhZMk52ZFc1MEwzTmxjblpwWTJVdFlXTmpiM1Z1ZEM1MWFXUWlPaUppWm1JM05qbGxZaTAzTXpOaUxUUTFZMkl0T1dJM1pDMWhNR1k0TWpneU1tRTBNelVpTENKemRXSWlPaUp6ZVhOMFpXMDZjMlZ5ZG1salpXRmpZMjkxYm5RNlpHVm1ZWFZzZERwdWIyUmxMVzFsZEhKcFkzTWlmUS5id1pBaXRwLTY0ek5sRTBVb1dXUGVLdWpjcllZdE5IeVB0X2FiWDU5VVU3XzNLcDctVi1IWGJCdTZYVFNWQVdVUlZwc2FWRy1zcUVZd2pmZW9VeVZLdktITXJ0elJWS0xuUnMyTWl2Um9fdzBHWE5MR1Naa2NtdU1VajdMYTdNb2ZiM3o2OFpLXzllRURSRHpWcUEzQUladnNZcTh1V0c5Q3BROFhKNG8wTzVEdUF3aFFuN0d5MFVDUGVJODB2bmVrVzFaaDdWT000UjUzc1l3aFgzSzRCM20wc0Q2MW1sTE83NmJKbVE1aWlacUFMb1RlTXFhYWdoR3B5bmJma3ZBajVxRVg4MHRwTl9WYWpJS0hKa0sybWFCYk44OW9uRFVDR2p5SGJrS3B3dWVYdkhZU2psU21PeHhicTJERjJuUDNhOXRTOUlCd2tOdmswRTZFeWQ4bkE=
注意:这里的token是经过bas4加密的
需要进行base64的解密
[root@nccztsjb-node-02 ~]# echo "ZXlKaGJHY2ldfsdfsfsfggPaUpTVXpJMU5pSXNJbXRwWkNJNklqTjFRWFJ5WVhVeFdFSlJZa0pZU205M2FHeE5kVTE2Vm1KM04yeFBlVGhwYWxCMWNVdGxjMEZLVjJzaWZRLmV5SnBjM01pT2lKcmRXSmxjbTVsZEdWekwzTmxjblpwWTJWaFkyTnZkVzUwSWl3aWEzVmlaWEp1WlhSbGN5NXBieTl6WlhKMmFXTmxZV05qYjNWdWRDOXVZVzFsYzNCaFkyVWlPaUprWldaaGRXeDBJaXdpYTNWaVpYSnVaWFJsY3k1cGJ5OXpaWEoyYVdObFlXTmpiM1Z1ZEM5elpXTnlaWFF1Ym1GdFpTSTZJbTV2WkdVdGJXVjBjbWxqY3kxMGIydGxiaTE2Ykc0M2RpSXNJbXQxWW1WeWJtVjBaWE11YVc4dmMyVnlkbWxqWldGalkyOTFiblF2YzJWeWRtbGpaUzFoWTJOdmRXNTBMbTVoYldVaU9pSnViMlJsTFcxbGRISnBZM01pTENKcmRXSmxjbTVsZEdWekxtbHZMM05sY25acFkyVmhZMk52ZFc1MEwzTmxjblpwWTJVdFlXTmpiM1Z1ZEM1MWFXUWlPaUppWm1JM05qbGxZaTAzTXpOaUxUUTFZMkl0T1dJM1pDMWhNR1k0TWpneU1tRTBNelVpTENKemRXSWlPaUp6ZVhOMFpXMDZjMlZ5ZG1salpXRmpZMjkxYm5RNlpHVm1ZWFZzZERwdWIyUmxMVzFsZEhKcFkzTWlmUS5id1pBaXRwLTY0ek5sRTBVb1dXUGVLdWpjcllZdE5IeVB0X2FiWDU5VVU3XzNLcDctVi1IWGJCdTZYVFNWQVdVUlZwc2FWRy1zcUVZd2pmZW9VeVZLdktITXJ0elJWS0xuUnMyTWl2Um9fdzBHWE5MR1Naa2NtdU1VajdMYTdNb2ZiM3o2OFpLXzllRURSRHpWcUEzQUladnNZcTh1V0c5Q3BROFhKNG8wTzVEdUF3aFFuN0d5MFVDUGVJODB2bmVrVzFaaDdWT000UjUzc1l3aFgzSzRCM20wc0Q2MW1sTE83NmJKbVE1aWlacUFMb1RlTXFhYWdoR3B5bmJma3ZBajVxRVg4MHRwTl9WYWpJS0hKa0sybWFCYk44OW9uRFVDR2p5SGJrS3B3dWVYdkhZU2psU21PeHhicTJERjJuUDNhOXRTOUlCd2tOdmswRTZFeWQ4bkE=" | base64 -d eyJhbGciOiJSUzI1NiIsImtpZCdsfdI6IjN1QXRyYXUxWEJRYkJYSm93aGxNdU16VmJ3N2xPeThpalB1cUtlc0FKV2sifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6Im5vZGUtbWV0cmljcy10b2tlbi16bG43diIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJub2RlLW1ldHJpY3MiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJiZmI3NjllYi03MzNiLTQ1Y2ItOWI3ZC1hMGY4MjgyMmE0MzUiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpub2RlLW1ldHJpY3MifQ.bwZAitp-64zNlE0UoWWPeKujcrYYtNHyPt_abX59UU7_3Kp7-V-HXbBu6XTSVAWURVpsaVG-sqEYwjfeoUyVKvKHMrtzRVKLnRs2MivRo_w0GXNLGSZkcmuMUj7La7Mofb3z68ZK_9eEDRDzVqA3AIZvsYq8uWG9CpQ8XJ4o0O5DuAwhQn7Gy0UCPeI80vnekW1Zh7VOM4R53sYwhX3K4B3m0sD61mlLO76bJmQ5iiZqALoTeMqaaghGpynbfkvAj5qEX80tpN_VajIKHJkK2maBbN89onDUCGjyHbkKpwueXvHYSjlSmOxxbq2DF2nP3a9tS9IBwkNvk0E6Eyd8nA[root@nccztsjb-node-02 ~]#
然后用解密之后的token访问节点的,也就是kubelet的metrics
token=eyJhbGciOiJSUzI1NiIsIsdfsgmtpZCI6IjNssQXRyYXUxWEJRYkJYSm93aGxNdU16VmJ3N2xPeThpalB1cUtlc0FKV2sifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6Im5vZGUtbWV0cmljcy10b2tlbi16bG43diIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJub2RlLW1ldHJpY3MiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJiZmI3NjllYi03MzNiLTQ1Y2ItOWI3ZC1hMGY4MjgyMmE0MzUiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpub2RlLW1ldHJpY3MifQ.bwZAitp-64zNlE0UoWWPeKujcrYYtNHyPt_abX59UU7_3Kp7-V-HXbBu6XTSVAWURVpsaVG-sqEYwjfeoUyVKvKHMrtzRVKLnRs2MivRo_w0GXNLGSZkcmuMUj7La7Mofb3z68ZK_9eEDRDzVqA3AIZvsYq8uWG9CpQ8XJ4o0O5DuAwhQn7Gy0UCPeI80vnekW1Zh7VOM4R53sYwhX3K4B3m0sD61mlLO76bJmQ5iiZqALoTeMqaaghGpynbfkvAj5qEX80tpN_VajIKHJkK2maBbN89onDUCGjyHbkKpwueXvHYSjlSmOxxbq2DF2nP3a9tS9IBwkNvk0E6Eyd8nA curl -s -k -H "Authorization: Bearer $token" https://172.20.59.238:10250/metrics > node-metrics.log
结果,输出到文件中。
查看结果:
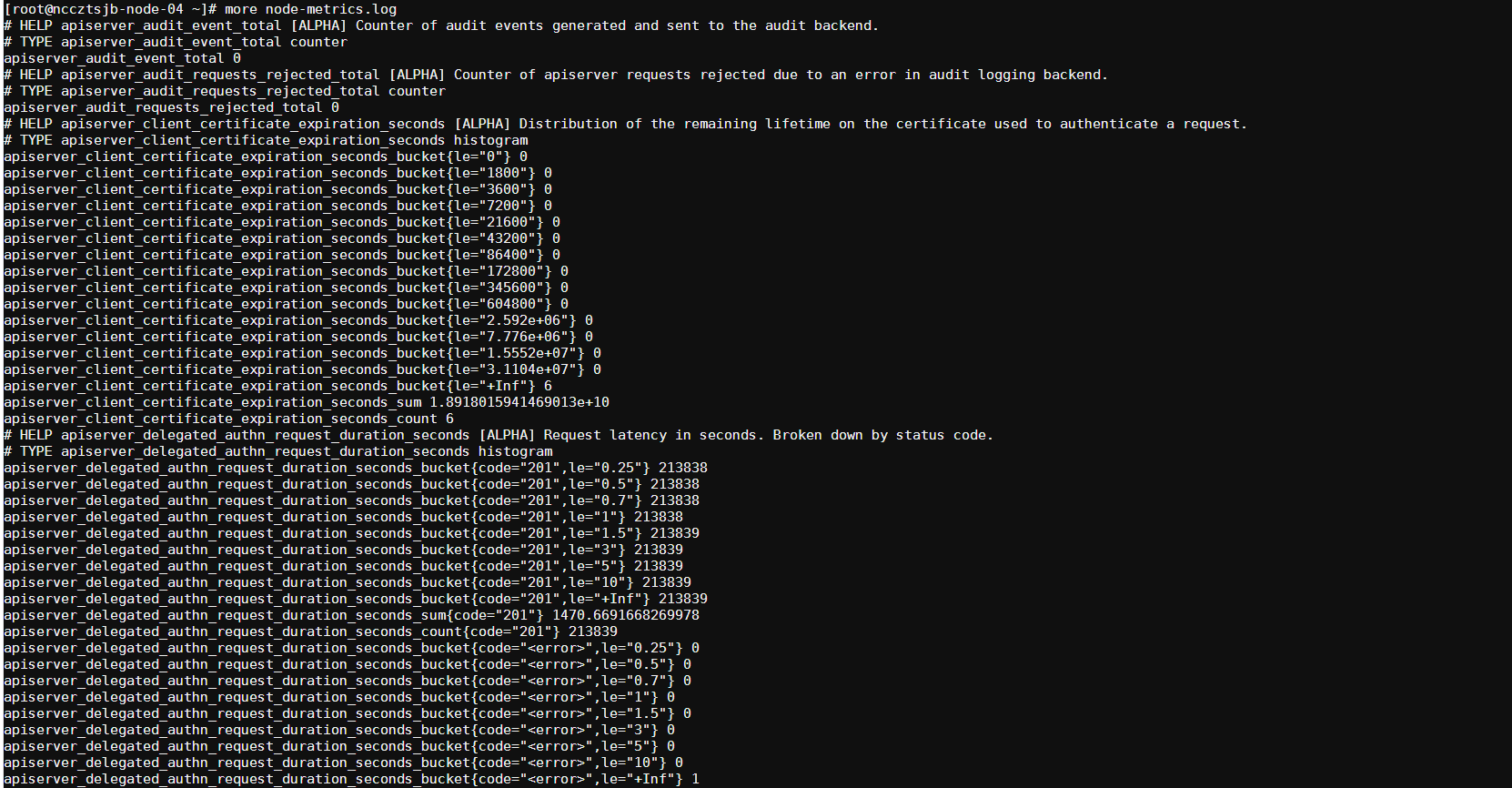
就可以看到的metrics的指标数据了。
或者,在浏览器中,修改header,增加token,也可以进行访问
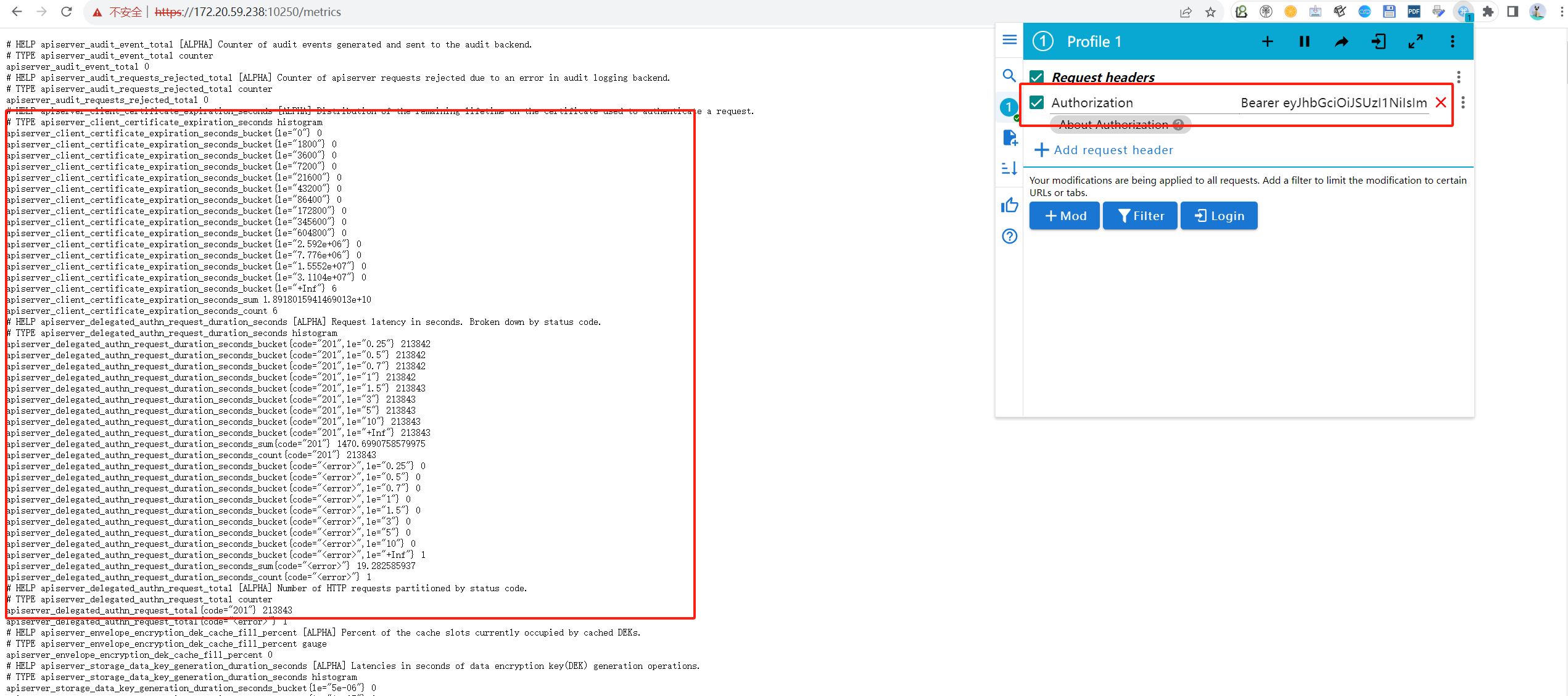
可以看到,对应的pod的信息