目录
一、概述
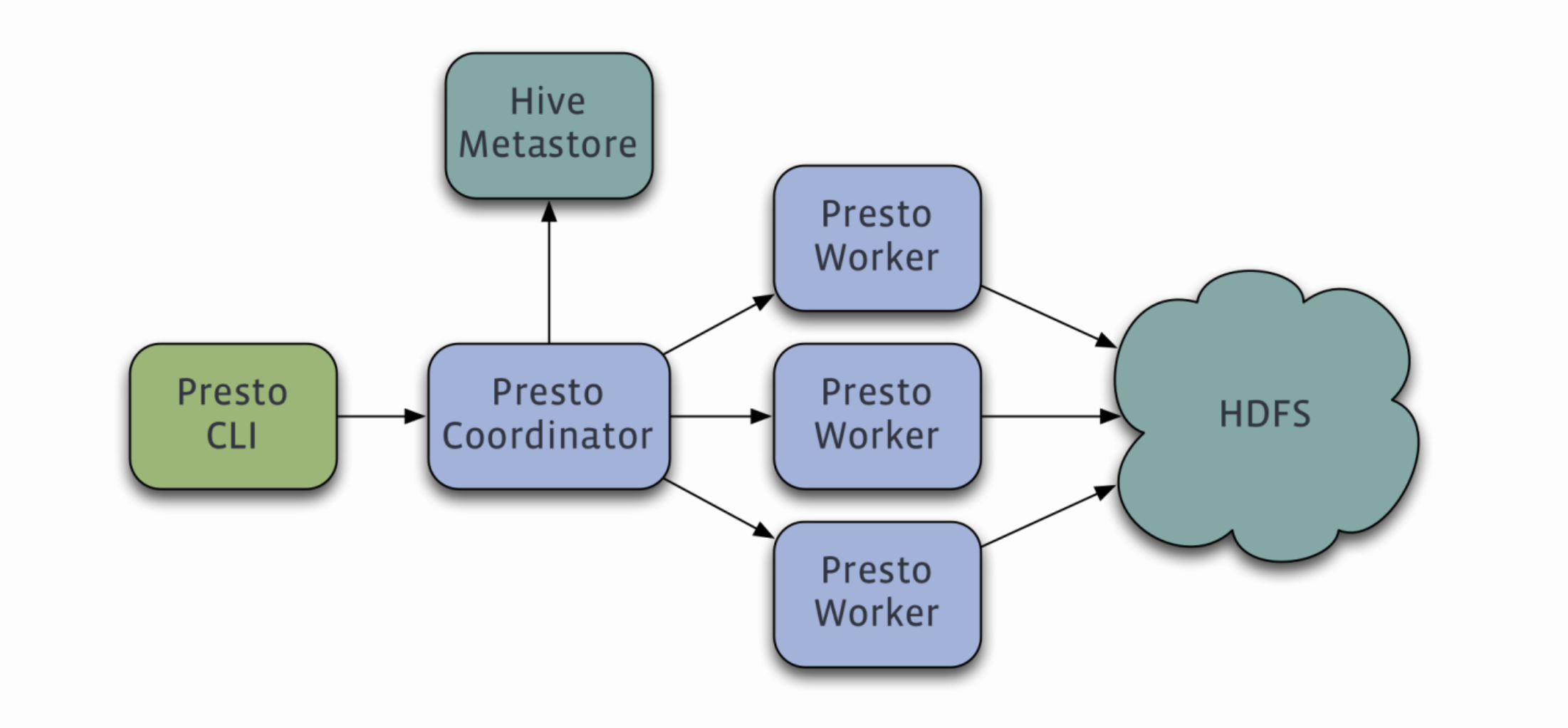
Trino(以前称为Presto SQL或PrestoDB)支持TLS(传输层安全性)认证以确保在数据传输过程中的安全性。TLS认证是一种用于加密和保护数据传输的协议,它在客户端和服务器之间建立安全的通信通道,以防止中间人攻击和数据泄露。
以下是使用TLS认证的一些背景信息:
-
数据安全性:在数据分析和查询过程中,敏感数据的传输可能涉及到机密信息,如个人身份信息、财务数据等。TLS认证提供了一种加密通信的方式,确保数据在传输过程中不被未经授权的人或系统访问。
-
防止中间人攻击:TLS认证可以防止中间人攻击,其中攻击者试图在客户端和服务器之间的通信中插入恶意代码或窃取数据。通过建立安全通信通道并验证服务器的身份,TLS可以保护免受此类攻击的影响。
-
合规性要求:许多法规和合规性要求要求对敏感数据的传输进行加密。使用TLS认证有助于满足这些要求,并降低数据泄露的风险。
-
身份验证:TLS认证还允许客户端验证服务器的身份。服务器使用SSL证书来证明其身份,客户端可以验证此证书以确保连接到正确的服务器。这有助于防止恶意伪装服务器的攻击。
-
数据完整性:TLS还提供了数据完整性检查,以确保在传输过程中数据未被篡改或损坏。
要在Trino中启用TLS认证,你需要生成和配置SSL证书,然后在Trino的配置文件中指定证书的路径和其他相关设置。一旦配置完成,Trino服务器和客户端将能够建立安全的TLS连接,确保数据传输的机密性和完整性。这对于保护敏感数据以及满足安全性和合规性要求非常重要。
官方文档:https://trino.io/docs/current/security/tls.html
二、安装 Trino
如果想快速部署,可以参考我之前的文章:
- 大数据Hadoop之——基于内存型SQL查询引擎Presto(Presto-Trino环境部署)
- 【大数据】通过 docker-compose 快速部署 Presto(Trino)保姆级教程
- 【云原生】Presto/Trino on k8s 环境部署
Trino官方文档:https://trino.io/docs/current/
这里为了快速部署就选择docke-compose部署了。
git clone https://gitee.com/hadoop-bigdata/docker-compose-presto.git
cd docker-compose-presto
# 部署
docker-compose up -d
# 为了不影响之前的分支,这里创建一个新分支
git checkout -b https-passwd
三、配置 HTTPS
1)生成证书
如果已有证书,这一步就可以省略。
mkdir tls && cd tls
# 生成 CA 证书私钥
openssl genrsa -out trino.key 4096
# 生成 CA 证书
openssl req -x509 -new -nodes -sha512 -days 3650 \
-subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=mytrino.com" \
-key trino.key \
-out trino.cert
# 合并
cat trino.key trino.cert > trino.pem
2)配置 Trino
在Trino的配置文件中,指定密钥库和密码,以便Trino服务器能够使用生成的证书和密钥。配置文件中的示例设置如下:
http-server.https.enabled=true
http-server.https.port=8443
http-server.https.keystore.path=/opt/apache/trino/etc/tls/trino.pem
#节点之间不需要使用https通信,在内网部署无需,外网需打开,默认就是false
internal-communication.https.required=false
3)修改 Trino docker-compose yaml 文件
version: '3'
services:
trino-coordinator:
image: registry.cn-hangzhou.aliyuncs.com/bigdata_cloudnative/trino-jmx-exporter:416
user: "hadoop:hadoop"
container_name: trino-coordinator
hostname: trino-coordinator
restart: always
privileged: true
env_file:
- .env
volumes:
- ./etc/coordinator/config.properties:${TRINO_HOME}/etc/config.properties
- ./etc/coordinator/jvm.config:${TRINO_HOME}/etc/jvm.config
- ./etc/coordinator/log.properties:${TRINO_HOME}/etc/log.properties
- ./etc/coordinator/node.properties:${TRINO_HOME}/etc/node.properties
- ./etc/catalog/:${TRINO_HOME}/etc/catalog/
- ./jmx-exporter/jmx_config.yaml:${TRINO_HOME}/etc/jmx_config.yaml
- ./tls:${TRINO_HOME}/etc/tls
ports:
- "30080:${TRINO_SERVER_PORT}"
- "30443:${TRINO_SERVER_HTTPS_PORT}"
- "30980:${JMX_RMIREGISTRY_PORT}"
- "30981:${JMX_RMISERVER_PORT}"
- "3900"
command: ["sh","-c","/opt/apache/bootstrap.sh trino-coordinator"]
networks:
- hadoop-network
healthcheck:
test: ["CMD-SHELL", "curl --fail http://localhost:${TRINO_SERVER_PORT}/v1/info || exit 1"]
interval: 10s
timeout: 20s
retries: 3
trino-worker:
image: registry.cn-hangzhou.aliyuncs.com/bigdata_cloudnative/trino:416
user: "hadoop:hadoop"
restart: always
privileged: true
deploy:
replicas: 1
env_file:
- .env
volumes:
- ./etc/worker/config.properties:${TRINO_HOME}/etc/config.properties
- ./etc/worker/jvm.config:${TRINO_HOME}/etc/jvm.config
- ./etc/worker/log.properties:${TRINO_HOME}/etc/log.properties
- ./etc/worker/node.properties:${TRINO_HOME}/etc/node.properties
- ./etc/catalog/:${TRINO_HOME}/etc/catalog/
- ./jmx-exporter/jmx_config.yaml:${TRINO_HOME}/etc/jmx_config.yaml
- ./tls:${TRINO_HOME}/etc/tls
ports:
- "${TRINO_SERVER_PORT}"
command: ["sh","-c","/opt/apache/bootstrap.sh trino-worker"]
networks:
- hadoop-network
healthcheck:
test: ["CMD-SHELL", "curl --fail http://localhost:${TRINO_SERVER_PORT}/v1/info || exit 1"]
interval: 10s
timeout: 10s
retries: 3
# 连接外部网络
networks:
hadoop-network:
external: true
4)开始部署 Trino
# 如果没创建就先创建
docker network create hadoop-network
# 开始部署
docker-compose -f docker-compose.yaml up -d
5)测试验证
web:https://[ip或域名]:对外端口
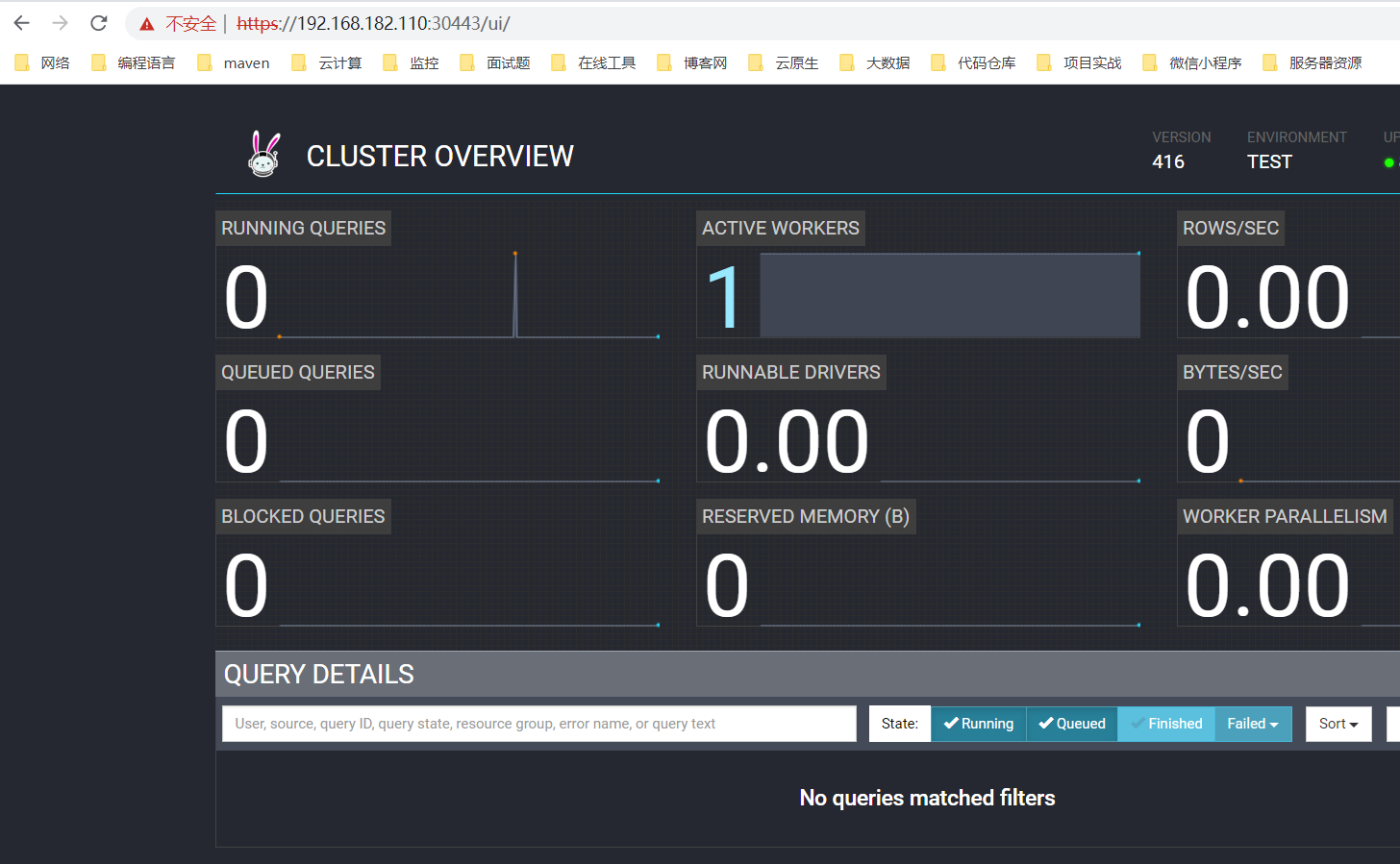
【温馨提示】原先的http也是可以访问的。
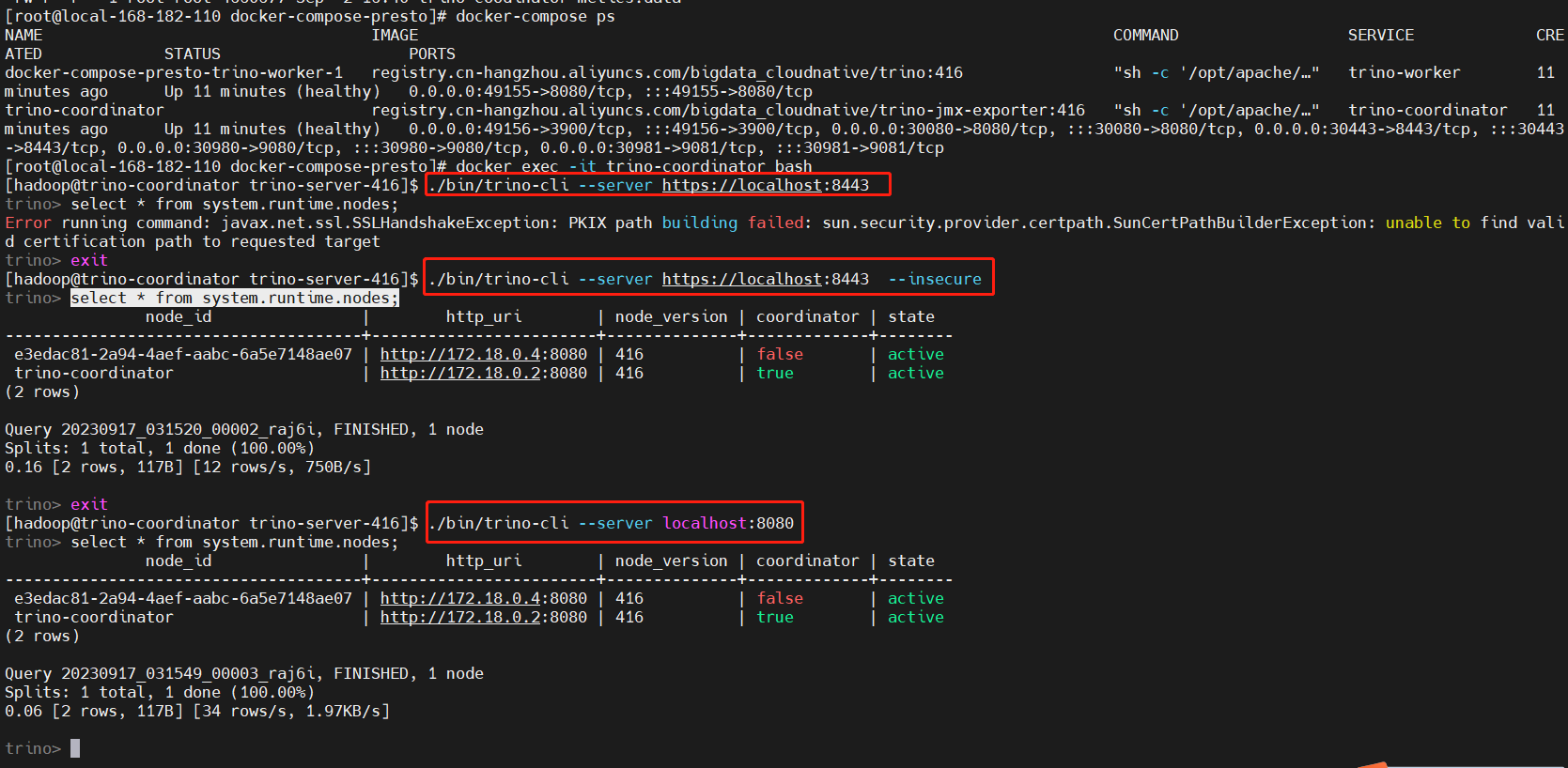
docker exec -it trino-coordinator bash
# 执行下面的命令可能不行,那是因为自己生成的证书是不可信的,得加一个参数 --insecure,去跳过证书验证。
./bin/trino-cli --server https://localhost:8443
select * from system.runtime.nodes;
./bin/trino-cli --server https://localhost:8443 --insecure
select * from system.runtime.nodes;
# http 也是可以访问的
./bin/trino-cli --server localhost:8080
select * from system.runtime.nodes;
四、密码认证
【温馨提示】要使用trino的权限控制,从官方文档上看,需要开启https,因此一定需要证书的。
1)开启密码认证
# etc/config.properties增加如下配置,开启密码认证
http-server.authentication.type=PASSWORD
# trino最新版本要求当启用trino的认证机制后,比如你开了kerberos,就必须要求trino节点内部通信提供一个shared-secret,这个secret你可以自定义。worker和coordinator的shared-secret保持一致即可。
#节点通信秘钥凭证
internal-communication.shared-secret=trino-secret
2)创建密码认证配置文件
创建配置etc/password-authenticator.properties,此处可以配置使用LDAP或密码文件认证,这里测试采用密码文件认证。配置内容如下:
password-authenticator.properties,里面需要用到password.db,这个文件就是在登录trino的时候使用到的用户名密码,需要bcrypt加密,可以去网络上找在线加密
password-authenticator.name=file
file.password-file=/opt/apache/trino/etc/password.db
password.db,用户密码文件,一行就是一个用户名密码,用户密码用:隔开,比如我定义了一个admin/123456的用户。在使用bcrypt加密的时候,生成的密码可能是$2a$开头的,而根据trino文档内定义的password规范是需要$2y$开头的,这里需要注意。
这里提供一个在线bcrypt加密地址:http://www.ab126.com/goju/10822.html
etc/password.db 内容如下:
admin:$2y$10$9O.FnPn27br2ebxzns3QkOj22OTQAaTvIBPjZd1dAjS5MOXaOJFxK
3)修改 Trino docker-compose yaml 文件
version: '3'
services:
trino-coordinator:
image: registry.cn-hangzhou.aliyuncs.com/bigdata_cloudnative/trino-jmx-exporter:416
user: "hadoop:hadoop"
container_name: trino-coordinator
hostname: trino-coordinator
restart: always
privileged: true
env_file:
- .env
volumes:
- ./etc/coordinator/config.properties:${TRINO_HOME}/etc/config.properties
- ./etc/coordinator/jvm.config:${TRINO_HOME}/etc/jvm.config
- ./etc/coordinator/log.properties:${TRINO_HOME}/etc/log.properties
- ./etc/coordinator/node.properties:${TRINO_HOME}/etc/node.properties
- ./etc/catalog/:${TRINO_HOME}/etc/catalog/
- ./jmx-exporter/jmx_config.yaml:${TRINO_HOME}/etc/jmx_config.yaml
- ./tls:${TRINO_HOME}/etc/tls
- ./etc/password.db:${TRINO_HOME}/etc/password.db
- ./etc/password-authenticator.properties:${TRINO_HOME}/etc/password-authenticator.properties
ports:
- "30080:${TRINO_SERVER_PORT}"
- "30443:${TRINO_SERVER_HTTPS_PORT}"
- "30980:${JMX_RMIREGISTRY_PORT}"
- "30981:${JMX_RMISERVER_PORT}"
- "3900"
command: ["sh","-c","/opt/apache/bootstrap.sh trino-coordinator"]
networks:
- hadoop-network
healthcheck:
test: ["CMD-SHELL", "curl --fail http://localhost:${TRINO_SERVER_PORT}/v1/info || exit 1"]
interval: 10s
timeout: 20s
retries: 3
trino-worker:
image: registry.cn-hangzhou.aliyuncs.com/bigdata_cloudnative/trino:416
user: "hadoop:hadoop"
restart: always
privileged: true
deploy:
replicas: 1
env_file:
- .env
volumes:
- ./etc/worker/config.properties:${TRINO_HOME}/etc/config.properties
- ./etc/worker/jvm.config:${TRINO_HOME}/etc/jvm.config
- ./etc/worker/log.properties:${TRINO_HOME}/etc/log.properties
- ./etc/worker/node.properties:${TRINO_HOME}/etc/node.properties
- ./etc/catalog/:${TRINO_HOME}/etc/catalog/
- ./jmx-exporter/jmx_config.yaml:${TRINO_HOME}/etc/jmx_config.yaml
- ./tls:${TRINO_HOME}/etc/tls
- ./etc/password.db:${TRINO_HOME}/etc/password.db
- ./etc/password-authenticator.properties:${TRINO_HOME}/etc/password-authenticator.properties
ports:
- "${TRINO_SERVER_PORT}"
command: ["sh","-c","/opt/apache/bootstrap.sh trino-worker"]
networks:
- hadoop-network
healthcheck:
test: ["CMD-SHELL", "curl --fail http://localhost:${TRINO_SERVER_PORT}/v1/info || exit 1"]
interval: 10s
timeout: 10s
retries: 3
# 连接外部网络
networks:
hadoop-network:
external: true
4)开始部署 Trino
# 如果没创建就先创建
docker network create hadoop-network
# 开始部署
docker-compose -f docker-compose.yaml up -d
5)测试验证
web:https://[ip或域名]:对外端口

docker exec -it trino-coordinator bash
# 执行下面的命令可能不行,那是因为自己生成的证书是不可信的,得加一个参数 --insecure,去跳过证书验证。
./bin/trino-cli --server https://localhost:8443 --user=admin --password --insecure
# 输入密码:123456
select * from system.runtime.nodes;
exit
# 非交互登录设置一个TRINO_PASSWORD 环境变量
export TRINO_PASSWORD="123456"
./bin/trino-cli --server https://localhost:8443 --user=admin --password --insecure
select * from system.runtime.nodes;

五、权限控制(优雅下线)
优雅下线官方文档:https://trino.io/docs/current/admin/graceful-shutdown.html
权限控制官方文档:https://trino.io/docs/current/security/built-in-system-access-control.html
如果需要优雅下线操作,必须设置访问权限,默认default是没有权限优雅下线worker节点的。这里只是拿优雅下线的操作的简单说一下权限权限控制,后面会详细介绍。系统提供了四种访问权限:
| 权限名称 | 描述 |
|---|---|
| default | 除了用户模拟和触发 Graceful shutdown之外,所有操作都是允许的。如果未配置,则这是默认访问控制。 |
| allow-all | 所有操作均被允许。 |
| read-only | 允许读取数据或元数据的操作,但不允许写入数据或元数据的操作。 |
| file | 授权规则在配置文件中指定。请参阅 基于文件的访问控制。 |
1)配置 etc/access-control.properties
access-control.name=allow-all
2)修改 Trino docker-compose yaml 文件
挂载文件,完整 docker-compose.yaml 文件
version: '3'
services:
trino-coordinator:
image: registry.cn-hangzhou.aliyuncs.com/bigdata_cloudnative/trino-jmx-exporter:416
user: "hadoop:hadoop"
container_name: trino-coordinator
hostname: trino-coordinator
restart: always
privileged: true
env_file:
- .env
volumes:
- ./etc/coordinator/config.properties:${TRINO_HOME}/etc/config.properties
- ./etc/coordinator/jvm.config:${TRINO_HOME}/etc/jvm.config
- ./etc/coordinator/log.properties:${TRINO_HOME}/etc/log.properties
- ./etc/coordinator/node.properties:${TRINO_HOME}/etc/node.properties
- ./etc/catalog/:${TRINO_HOME}/etc/catalog/
- ./jmx-exporter/jmx_config.yaml:${TRINO_HOME}/etc/jmx_config.yaml
- ./tls:${TRINO_HOME}/etc/tls
- ./etc/password.db:${TRINO_HOME}/etc/password.db
- ./etc/password-authenticator.properties:${TRINO_HOME}/etc/password-authenticator.properties
- ./etc/access-control.properties:${TRINO_HOME}/etc/access-control.properties
ports:
- "30080:${TRINO_SERVER_PORT}"
- "30443:${TRINO_SERVER_HTTPS_PORT}"
- "30980:${JMX_RMIREGISTRY_PORT}"
- "30981:${JMX_RMISERVER_PORT}"
- "3900"
command: ["sh","-c","/opt/apache/bootstrap.sh trino-coordinator"]
networks:
- hadoop-network
healthcheck:
test: ["CMD-SHELL", "curl --fail http://localhost:${TRINO_SERVER_PORT}/v1/info || exit 1"]
interval: 10s
timeout: 20s
retries: 3
trino-worker:
image: registry.cn-hangzhou.aliyuncs.com/bigdata_cloudnative/trino:416
user: "hadoop:hadoop"
restart: always
privileged: true
deploy:
replicas: 1
env_file:
- .env
volumes:
- ./etc/worker/config.properties:${TRINO_HOME}/etc/config.properties
- ./etc/worker/jvm.config:${TRINO_HOME}/etc/jvm.config
- ./etc/worker/log.properties:${TRINO_HOME}/etc/log.properties
- ./etc/worker/node.properties:${TRINO_HOME}/etc/node.properties
- ./etc/catalog/:${TRINO_HOME}/etc/catalog/
- ./jmx-exporter/jmx_config.yaml:${TRINO_HOME}/etc/jmx_config.yaml
- ./tls:${TRINO_HOME}/etc/tls
- ./etc/password.db:${TRINO_HOME}/etc/password.db
- ./etc/password-authenticator.properties:${TRINO_HOME}/etc/password-authenticator.properties
- ./etc/access-control.properties:${TRINO_HOME}/etc/access-control.properties
ports:
- "${TRINO_SERVER_PORT}"
command: ["sh","-c","/opt/apache/bootstrap.sh trino-worker"]
networks:
- hadoop-network
healthcheck:
test: ["CMD-SHELL", "curl --fail http://localhost:${TRINO_SERVER_PORT}/v1/info || exit 1"]
interval: 10s
timeout: 10s
retries: 3
# 连接外部网络
networks:
hadoop-network:
external: true
3)开始部署 Trino
# 如果没创建就先创建
docker network create hadoop-network
# 开始部署
docker-compose -f docker-compose.yaml up -d
4)测试验证
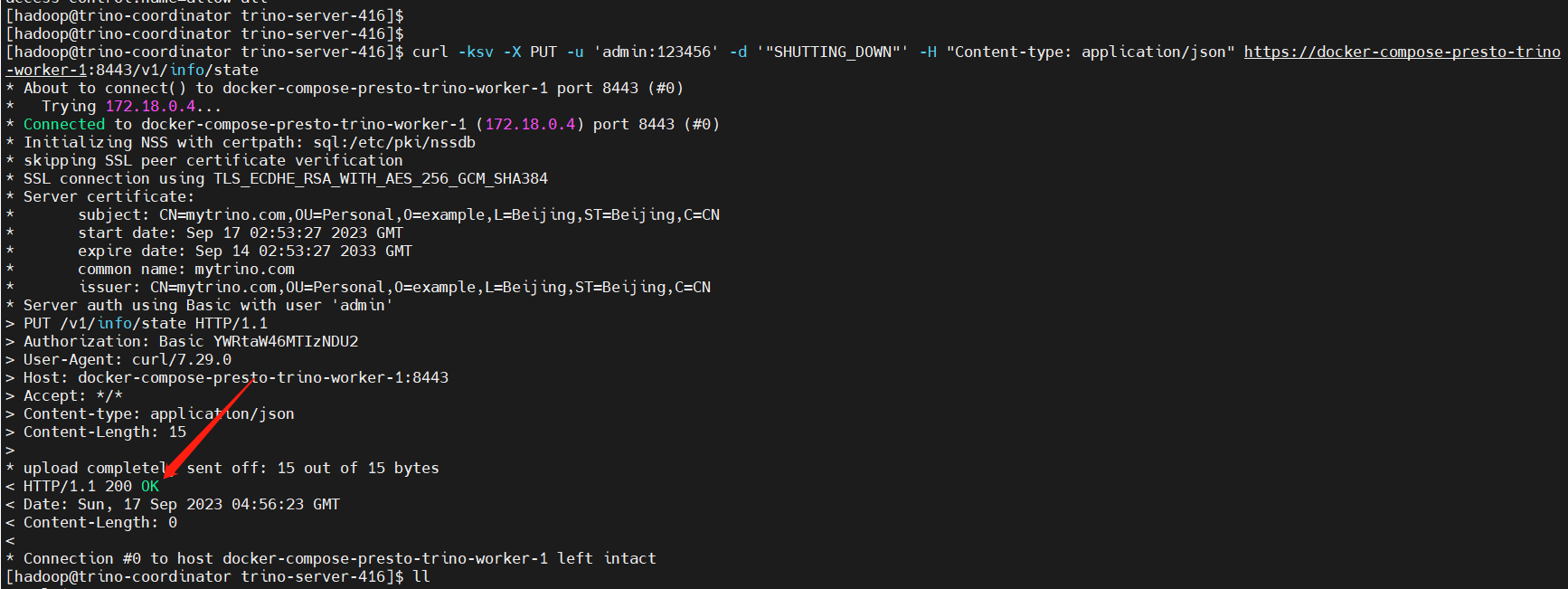
docker exec -it trino-coordinator bash
# 优雅下线 worker 节点
curl -ksv -X PUT -u 'admin:123456' -d '"SHUTTING_DOWN"' -H "Content-type: application/json" https://docker-compose-presto-trino-worker-1:8443/v1/info/state
Trino HTTPS 与密码认证介绍与实战操作就先到这里了,有任何疑问也可关注我公众号:大数据与云原生技术分享,进行技术交流,如本篇文章对您有所帮助,麻烦帮忙一键三连(点赞、转发、收藏)~
