如果要ingress的域名增加TLS的证书,该怎么办?
那如何将证书和密钥保存到k8s的secret中呢?
如果使用自签名的证书,使用下面的命令创建密钥和证书
[root@nccztsjb-node-23 secrets]# openssl req -x509 \ > -newkey \ > rsa:4096 \ > -nodes \ > -keyout server.key \ > -out server.crt \ > -sha256 \ > -days 3650 \ > -subj "/C=CN/ST=Beijing/L=Beijing/O=Alididi/OU=Ops/CN=www.example.com" Generating a 4096 bit RSA private key ......................................................................................................................................++ ........................................................++ writing new private key to 'server.key' ----- [root@nccztsjb-node-23 secrets]# [root@nccztsjb-node-23 secrets]# [root@nccztsjb-node-23 secrets]# ls server.crt server.key [root@nccztsjb-node-23 secrets]# ls -ltr total 8 -rw-r--r-- 1 root root 3272 Jun 26 14:44 server.key -rw-r--r-- 1 root root 2025 Jun 26 14:44 server.crt
创建好了密钥key和证书之后,通过如下的命令,保存到secret中
kubectl create secret tls myweb-secret --key server.key --cert server.crt
创建好了,之后,可以查看其信息:
[root@nccztsjb-node-23 secrets]# kubectl create secret tls myweb-secret --key server.key --cert server.crt secret/myweb-secret created [root@nccztsjb-node-23 secrets]# kubectl get secret NAME TYPE DATA AGE default-token-ghs97 kubernetes.io/service-account-token 3 118d myweb-secret kubernetes.io/tls 2 5s [root@nccztsjb-node-23 secrets]# kubectl get secret myweb-secret NAME TYPE DATA AGE myweb-secret kubernetes.io/tls 2 14s [root@nccztsjb-node-23 secrets]# kubectl get secret myweb-secret -o yaml apiVersion: v1 data: tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUZxVENDQTVHZ0F3SUJBZ0lKQU5UV0sweEZucG9hTUEwR0NTcUdTSWIzRFFFQkN3VUFNR3N4Q3pBSkJnTlYKQkFZVEFrTk9NUkF3RGdZRFZRUUlEQWRDWldscWFXNW5NUkF3RGdZRFZRUUhEQWRDWldscWFXNW5NUkF3RGdZRApWUVFLREFkQmJHbGthV1JwTVF3d0NnWURWUVFMREFOUGNITXhHREFXQmdOVkJBTU1EM2QzZHk1bGVHRnRjR3hsCkxtTnZiVEFlRncweU16QTJNall3TmpRME1UaGFGdzB6TXpBMk1qTXdOalEwTVRoYU1Hc3hDekFKQmdOVkJBWVQKQWtOT01SQXdEZ1lEVlFRSURBZENaV2xxYVc1bk1SQXdEZ1lEVlFRSERBZENaV2xxYVc1bk1SQXdEZ1lEVlFRSwpEQWRCYkdsa2FXUnBNUXd3Q2dZRFZRUUxEQU5QY0hNeEdEQVdCZ05WQkFNTUQzZDNkeTVsZUdGdGNHeGxMbU52CmJUQ0NBaUl3RFFZSktvWklodmNOQVFFQkJRQURnZ0lQQURDQ0Fnb0NnZ0lCQU44bkhVanU1bFpHOEJRdVVhVU0KOFVpd2F2cE53dXpvaHY4U2ZoaGV3ODZLdWM4NEJ3Zk1SMTFRS1pUbFRCa004MUs2YWxwQjI2dzlXNGZBQWF3VgpOSDJHR2VxU3JNSjRkMHF4SW8yVHJLbVB1dVpWSW45QS9vb2NIMVdKMFlzTitGMWoyZGxqMnFBVXM3QjJtVXJXCktEVU1GcWdNcHVLOFlPUTZUcngxSCtHUEJoUGlKWFl1ZjFDMUtVYXlKR05PSmpQc2FCc1VtS0Y1WWtSa0NlNGQKeDlUNWt1SDF6aXEyQUFiQUlDelZFMld2UnBwYnRXVmR3MGZkVlFDNFE1cjRsRlcyTk5DK0sreDNZeForVVBOWAo3UEtUblk0MSs0ZS9MaCt3VDJxdE1kQ3hrbHdmKzJ4MDJpYTU5WHNmS3BuSzBJN3hyUjZIUTFML0pKOGJCeVdnCmpnaC9ZRmxDQUpaUEVSYjFOUFRZMFJDSGZZcTJYdmxsdnl6U2MzNnZTWWdUcmNZWldQdGJPNU9EYlJxZlZ6ZkIKRTNuQjhSOHFUc3RvMFVhUlJIRFQyN1pQWEN4c3Q2WXdYSnBYenNkczE5ZGI4UHBmVnRvNTZRRG9YbHFjV3JRVwpoYURVYXlXY29nTVRnYTBDZ0c3UzgwZDJLWWF0U3Q5OWZWbFF0QjNxQm9UMU5adW1XY3doaFZBQ0VXMFBuQmw3Clh6S2IyS3ViMUZ6YmZuZ0NxckFRbmFsL2EzTHNRZjdPWUtSZlRWVUtLMXBlY2dDZzRiVElma28vOWk5Y2lMbS8Ka1M1WTNwV1lGOHlBQ0hza0JRQWdraGRia1hVVWNGeWF0L0dNZFYraEx1Y2dqVEdIelkzc3krakF1NHljaGFUeApPS2thajhnM3hsS3hmMlU2UlJtT09Lc1BBZ01CQUFHalVEQk9NQjBHQTFVZERnUVdCQlN6YXVHL1RpajNHMFNjCnRBekMrQXVVazRxWnZEQWZCZ05WSFNNRUdEQVdnQlN6YXVHL1RpajNHMFNjdEF6QytBdVVrNHFadkRBTUJnTlYKSFJNRUJUQURBUUgvTUEwR0NTcUdTSWIzRFFFQkN3VUFBNElDQVFBNWJNOWNyN2QyZzlBY2RieklRTWczSDRObgpZd0poZHlJZjFYQ2RiYmFra0pzZGlFY2N3dkN0c0l3ZThIVkhJOEdWUC9IN0pvUm5ZMjdhVGFsb21zM3RqSGhvClpHdFUvTmdpN3dGTXFwTEJ0RkZKdGt1aHJVWGk2d201THRuQXRrZ0VlNHI5ZlRRZzJtRFZWMGZiNVVpY1o5ZisKT2RmOHpHL0I0OEVNK0k4dU43b2crYU5Oa3FWa2s3d05pZE5NK1VQV0xyLzZRMTBHN29nYmpRTElqT3YzbUxCRwpQWnZDQU1FMnhOK2hhUEtKMkJDdzFRakEvTGtXcjdhYmhhQ0tyV1VGK1NVLzJqa1lxdkZqa2dHZkZmQ3JiZTc1Ck1uZHl4UTZGREJUcW83ck9wNUxoSWhBc1I4L1o4Ym5XYlIwWVRHcUhwNGtoa1IrMVp2Vnh6RUE4aTQ1dG5ENW0KY0R6Nmh2dXNLVWQ3VittSWk1YUg5cExoMHdtVDA0dzUwUkJhU1cybTFJQXMyM2tMMTlaL0REbCtXVGJLUTBwTAp3SmJIa01hdmRRckxMUmJoTUVkUm9jYUhMVUdnVG01Rkl6Qmg5cEk3VjRqa05BSGJrYldEbTdlWk1IdSs5a3IxCmlkYzI4NHdYWkxHamlIaGhJN0kyK0dZdjI4ZG8zTWMyckFkTWlBTHNZNFB2UHVYNW1WcTNxUlBiem41VzNYUkQKLzlkcmhjQUVTMlhwaWU4WUwyRTA0a3VrV2I0ankyMHNKZjl6SkkxWjk1NlM5aE1TU1FnZ1E3UmJac3ppRmhLMwpCbG9IaDJDb3kyM1hvYUNBRVJkaHR1aTREdEEvc1huR3pYdEZ3OWRGR3JPYmsvTjJ3MnVKRFJKaUowN241di90CnpzL3kyMm54NFZaT0lrVWY2Zz09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K tls.key: LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCk1JSUpRZ0lCQURBTkJna3Foa2lHOXcwQkFRRUZBQVNDQ1N3d2dna29BZ0VBQW9JQ0FRRGZKeDFJN3VaV1J2QVUKTGxHbERQRklzR3I2VGNMczZJYi9FbjRZWHNQT2lyblBPQWNIekVkZFVDbVU1VXdaRFBOU3VtcGFRZHVzUFZ1SAp3QUdzRlRSOWhobnFrcXpDZUhkS3NTS05rNnlwajdybVZTSi9RUDZLSEI5VmlkR0xEZmhkWTluWlk5cWdGTE93CmRwbEsxaWcxREJhb0RLYml2R0RrT2s2OGRSL2hqd1lUNGlWMkxuOVF0U2xHc2lSalRpWXo3R2diRkppaGVXSkUKWkFudUhjZlUrWkxoOWM0cXRnQUd3Q0FzMVJObHIwYWFXN1ZsWGNOSDNWVUF1RU9hK0pSVnRqVFF2aXZzZDJNVwpmbER6Vit6eWs1Mk9OZnVIdnk0ZnNFOXFyVEhRc1pKY0gvdHNkTm9tdWZWN0h5cVp5dENPOGEwZWgwTlMveVNmCkd3Y2xvSTRJZjJCWlFnQ1dUeEVXOVRUMDJORVFoMzJLdGw3NVpiOHMwbk4rcjBtSUU2M0dHVmo3V3p1VGcyMGEKbjFjM3dSTjV3ZkVmS2s3TGFORkdrVVJ3MDl1MlQxd3NiTGVtTUZ5YVY4N0hiTmZYVy9ENlgxYmFPZWtBNkY1YQpuRnEwRm9XZzFHc2xuS0lERTRHdEFvQnUwdk5IZGltR3JVcmZmWDFaVUxRZDZnYUU5VFdicGxuTUlZVlFBaEZ0CkQ1d1plMTh5bTlpcm05UmMyMzU0QXFxd0VKMnBmMnR5N0VIK3ptQ2tYMDFWQ2l0YVhuSUFvT0cweUg1S1AvWXYKWElpNXY1RXVXTjZWbUJmTWdBaDdKQVVBSUpJWFc1RjFGSEJjbXJmeGpIVmZvUzduSUkweGg4Mk43TXZvd0x1TQpuSVdrOFRpcEdvL0lOOFpTc1g5bE9rVVpqamlyRHdJREFRQUJBb0lDQUNGTkFQM0ZTUEpQRzd5blBOL1lrcGs2CldueUg1akxjY0dqWUphRVZZenNMVUxjdnNUemtxekd0cU1iamdQdXNCeE90WmZtYUltSU50ZjhJRkRmTjRrdHAKRzZ6NXZuWTI2L1psZ0xhSDl4aEdycWw0d3ZFaWpkbW1ZTGF2SG1vVjU1NW9MRFpZeEdObk0zbDkrVnBGb3pKbgpYMm9zbVNyMDJiQzFVdEtrMStFZEt0Y0V4SHBpYmZWcFU0T05TZ2pYdkxPNjc3NDYwSndvTlJYbnArTzA1Z0ZPClRURVRNWFVHTy9MRjhRYy90T2xUd3NGK05nK3VjbG5qR2JCRnp6RHRMNVdxM3k3WGNrNlRjbUlFNzZlZzAyZFAKeUE5VTF2aG0rMGNYVklLaTNmQTZ6NUNYNVRsR0p0Zm9vRTJEVlNRbU5BRmc1MmpLM3EwZ0RpTUFNWXpYN05ubwpiOHViUXNEbHNsdWx3ck5OTDJtUjZ6TzRBZDBrRzRMMS9Hemt1Q2hVWndjVnAvcFZrUHpscGNHenZ4TE8rMElECmRoNEY0ZHZVWVdsSWJ4aUU1SVhzMjZZbEFyYTRJK2krb1JRWFJGQVpkYy84UUxXdkJFWHp5V1dlaHdVUityYmcKd0N5bFc2TTVZZ3BSR09UeG9VUUgxdmlUcVN3Mk5COU1oei9sczQ2VEJxdndGVWpUV1BPcTFjUjREQXJiaHQvOApmNVRwRXpUdmJ4aHRaU3MvMFZzUDdxTGl4LzVFcEtaSnEyZjVrYWh1UEt3dENkTTh0Y1BFV0F0azI3RE94SWxQCjRHdUxKcE01UHFrbmluUkdjTUZibnRKSE4vL05aWnpCditsWXAxV281d0pCWWE1UlNVWVJaeFVLQ2RWaDhvb2EKV1pHZmo0dDVGTnVvYnpMODJSamhBb0lCQVFEeTYzdjZLSWVxNS8wTkh2bHBCdzhCb0Q5Mmlrc0p4cDFoVGhpTwphV2M3ejkrNitpNVI5TllNdE1YRnFKQ0JYNkVJZUhiTUQyMTUrVWpyNERZSlJqY0Y3c3ZzV2dxWUdSMFlFaUNtCmlVS3pDbGQzdlQrREZZMmFiTUpjRzFzczhxOStxaDVnb0k1bGdidGFkVTJ5bVFBRzN3VDc0K1dLQThBZDB4bDIKMXFRZG9ZM2RGOCttWGczZlhuY2dVOVFlSXJRcC83ZUEwTHpyZm5xSG1hSldsYmFBNHorWnh0azB1VitFRUFUcQoxSm81OFd2SGpsQ3AvZnRCL3l1QUFGaXdqUHNudVRiQWRpY1c3dGFzeTBWSUVsVEtJSll6RUtYclRQZHRoMGdCCkgxdU5iaVFMN1VJVkJYUVgvcmJvVnF0cnlFMXRTZ2pBSDZVR0Qwc1JJajZZaGlGOUFvSUJBUURyS3licGNjSDgKakw1a2hFL1VwdlorZzlXVlZRUjZodnMvVXNQTzNYdTJFSHd1Y005bmJDalNEb1Q1ZmVZNS9wUXRYK2luOWowMAo5bXA5UjdteE4reGFDSzJtajFsWTlEU2ZmaTFQUDUvcjNIRTRuMC8yaWdjazZzQ1FWREdmV0VsTXhqb1VobW41CkpNNjFRYnN2RHRsY3lOOXdPeHZrTGZhVHhJYml0ZVE2emZ0a0ZRdHY1MDl3UHkxR2ZLYS83U1EwNjk0MGp3bUQKb1kwZS9ZL1k1eG9EMDlQTHB2MTdiQ08xbTBzdEF5VVVXVnZ6UFdWcDkxZ0x5bXNUVVExV0V5dWtlOTduNk9NVgo2cEZhSU5DMGp3MVJDeWRpNytwNkZqY3QvV2NVays4L0J1TmlCQnpicVBJN3RoSGhCcTNUakxzL2NuVCtYN2I0CnpodEhVaGQ2SlNSN0FvSUJBUURsT3pxZThpZzBLdjhzcHBJTmZrKzI1UlYrTXpwa1d6eWdXaVhxSGFVQldFUjAKR1Nva3hMcEkrejIyTEQ5UkZvRExrWUhwUnBXMGlIMDd1VFRFdzdHZ3M1dFR5aFE5TzFXdEpVNFNXV3pMcjNLaQoxNzliWDdka2hrVlN6YTNZV0pzckdEWGFVU2lPdVVHbk54Sysrb3AvOFd5dWxueEJKUkRpRkJidmdkVVU4U01DCkJEbzdjSDMrenhIek82ZnJXQ3hUaGJBUXF1bmNBRnA0STQ2QnpuMk9XdVBscFRQTEFUTVZXRmlMa1Z5SVdUMnYKN3FoSUFoaGNTd010b3lZT1ZMdWMzTGJDSDd6N2N4NjVxSWdVWHRnTWRYdkhiR3BtQlJkb0VFVHVhanptMVl6RwpoSG5iaEczdFJyd3J1NzIvMUNEY2hRU0U2RmU5eENpK1htWmJZQmV4QW9JQkFFS3VscmNFK2FONTZSYXBhZFY3CmpsTnJZR21hbE0yRmJzS1MzbERPL3FBdVpuZm9wdmJGZFlHeWVrUWdUZUxON0FnOXRNUERqN0Z2MmR3eU5WWXAKN0V2UFFDWUZhYWxPZllsb0JzTDg0SVRKbWhVYkgxcGg0d3Exd2VwcTVUTXdub0ExaVF4KzNKZTN0eUV3UlRwZgp0SVNadExtbkdRNkhkZTZLZ0ZEU2tLZVg5cHQzV0NuZjVlZUhFbmgxS2ZjcjcrTk5xbEV1NmR5NE4wSzlWVWVFCnFCekR1TDk3VjA3aTUvRTcyb0lsN1NLcS8rYWwxeGJIK3VCRkFqMlU4dm9nTDNUUlp2Qk5XZTdCOTNzZDZPLzUKekNYWnlzNUVCekdkRVFKcVl3c3pzMWdreE43ckdaK3pkUlEzV1RSOFoxZWdCUXhGa1NUNzBPOFZ5aWhiLzZvegowL2NDZ2dFQUxhUS9iOCtobmw4QXV4WGh6eWpJeXgyWm1ONjZXQW1TYWFKMHJWUk9EMVhGZFVOL2NEcTg0V2g2CnNZUzhqZHZLeUFMQkdQazdyMzYxYU10OEdyVlRpVWZIcDhQK0svVTd4U05tQ2dmTGRkTGw1TWZVYTVyRUlSV0kKUmpJNUNNbTJoZmowV3IrTnpjVk9yU0lWc1hDejhDMUlXL0JBUjNQRlBFbnAyM3ZLZzArZTlWZGFBWWZWRk9veQpwOW0weXZJRzBLMTJrRkRqZytaS2p6eTRxYkZCQkUrQUFBSVB0Q0dqNjFZVDR0L2dmT243U2QrTGZhbXM5Z1FaCm1vZFRTQ2pJTThQZlBYSHRpZmRXYTlmazd6cHI2NHNGSHE5M0tvNFFta01tYVFubGMyQUpEUzlaTWp3ajRPN1QKcWcydDI5SFVUWlNaQ2dQeWJJS3E5WVo1NU1Fb0Z3PT0KLS0tLS1FTkQgUFJJVkFURSBLRVktLS0tLQo= kind: Secret metadata: creationTimestamp: "2023-06-26T06:44:50Z" name: myweb-secret namespace: default resourceVersion: "15234021" uid: ebabbbb5-0801-480f-96fb-9e057ecda0fb type: kubernetes.io/tls [root@nccztsjb-node-23 secrets]#
看到的数据是tls.crt和tls.key
后续,就可以将这个secret挂载到ingress里面了来使用了。
下面是,如何在ingress中,应用这个证书?
在tls段,引用刚刚创建好的secret对象
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-tls
namespace: default
spec:
tls:
- hosts:
- mywebsite.com
secretName: myweb-secret
ingressClassName: nginx
rules:
- host: mywebsite.com
http:
paths:
- backend:
service:
name: nginx-deployment
port:
number: 80
path: /
pathType: Prefix
[root@nccztsjb-node-23 yamls]# kubectl get ingress ingress-tls
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress-tls nginx mywebsite.com 172.20.58.65 80, 443 58s
[root@nccztsjb-node-23 yamls]#
这里是自动增减了443端口的
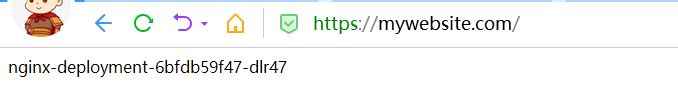
通过域名进行访问,主要是https的访问
[root@nccztsjb-node-23 yamls]# curl -H "Host:mywebsite.com" -k https://172.20.58.65 nginx-deployment-6bfdb59f47-4qgr4 [root@nccztsjb-node-23 yamls]# curl -H "Host:mywebsite.com" -k https://172.20.58.65 nginx-deployment-6bfdb59f47-6kjn5 [root@nccztsjb-node-23 yamls]# curl -H "Host:mywebsite.com" -k https://172.20.58.65 nginx-deployment-6bfdb59f47-4qgr4 [root@nccztsjb-node-23 yamls]#
这样就可以进行对ingress的https的域名访问了。
浏览器也可以进行访问(需要配置hosts)