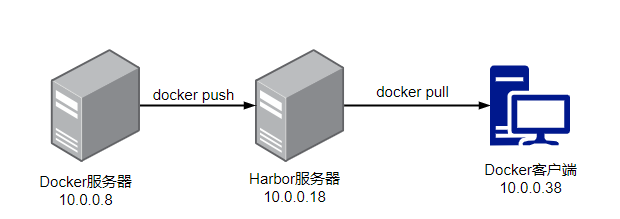
1.1 搭建harbor服务器
[root@rocky8 ~]$ cat /data/scripts/install_harbor.sh
#!/bin/bash
DOCKER_VERSION="20.10.10"
UBUNTU_DOCKER_VERSION="5:${DOCKER_VERSION}~3-0~${ID}-${UBUNTU_CODENAME}"
DOCKER_COMPOSE_VERSION="2.16.0"
DOCKER_COMPOSE_FILE=docker-compose-Linux-x86_64
HARBOR_VERSION="2.5.6"
HARBOR_BASE="/usr/local/"
HARBOR_NAME=harbor.yanlinux.org
HARBOR_IP=`hostname -I|awk '{print $1}'`
HARBOR_ADMIN_PASSWORD=123456
COLOR_SUCCESS="echo -e \\033[1;32m"
COLOR_FAILURE="echo -e \\033[1;31m"
END="\033[m"
. /etc/os-release
color () {
RES_COL=60
MOVE_TO_COL="echo -en \\033[${RES_COL}G"
SETCOLOR_SUCCESS="echo -en \\033[1;32m"
SETCOLOR_FAILURE="echo -en \\033[1;31m"
SETCOLOR_WARNING="echo -en \\033[1;33m"
SETCOLOR_NORMAL="echo -en \E[0m"
echo -n "$1" && $MOVE_TO_COL
echo -n "["
if [ $2 = "success" -o $2 = "0" ] ;then
${SETCOLOR_SUCCESS}
echo -n $" OK "
elif [ $2 = "failure" -o $2 = "1" ] ;then
${SETCOLOR_FAILURE}
echo -n $"FAILED"
else
${SETCOLOR_WARNING}
echo -n $"WARNING"
fi
${SETCOLOR_NORMAL}
echo -n "]"
echo
}
install_docker() {
if [ $ID = "centos" -o $ID = "rocky" ];then
if [ $VERSION_ID = "7" ];then
cat > /etc/yum.repos.d/docker.repo <<EOF
[docker]
name=docker
gpgcheck=0
#baseurl=https://mirrors.aliyun.com/docker-ce/linux/centos/7/x86_64/stable/
baseurl=https://mirrors.tuna.tsinghua.edu.cn/docker-ce/linux/centos/7/x86_64/stable/
EOF
else
cat > /etc/yum.repos.d/docker.repo <<EOF
[docker]
name=docker
gpgcheck=0
#baseurl=https://mirrors.aliyun.com/docker-ce/linux/centos/8/x86_64/stable/
baseurl=https://mirrors.tuna.tsinghua.edu.cn/docker-ce/linux/centos/8/x86_64/stable/
EOF
fi
yum clean all
yum makecache
${COLOR_FAILURE} "Docker有以下版本"${END}
yum list docker-ce --showduplicates
${COLOR_FAILURE}"5秒后即将安装: docker-"${DOCKER_VERSION}" 版本....."${END}
sleep 5
yum -y install docker-ce-${DOCKER_VERSION} docker-ce-cli-${DOCKER_VERSION} || { color "Base,Extras的yum源失败,请检查yum源配置" 1;exit; }
else
dpkg -s docker-ce &> /dev/null && $COLOR"Docker已安装,退出" 1 && exit
apt update || { color "更新包索引失败" 1 ; exit 1; }
apt -y install apt-transport-https ca-certificates curl software-properties-common || \
{ color "安装相关包失败" 1 ; exit 2; }
curl -fsSL https://mirrors.tuna.tsinghua.edu.cn/docker-ce/linux/ubuntu/gpg | sudo apt-key add -
add-apt-repository "deb [arch=amd64] https://mirrors.aliyun.com/docker-ce/linux/ubuntu $(lsb_release -cs) stable"
apt update
${COLOR_FAILURE} "Docker有以下版本"${END}
apt-cache madison docker-ce
${COLOR_FAILURE}"5秒后即将安装: docker-"${UBUNTU_DOCKER_VERSION}" 版本....."${END}
${COLOR_FAILURE}"如果想安装其它Docker版本,请按ctrl+c键退出,修改版本再执行"${END}
sleep 5
apt -y install docker-ce=${UBUNTU_DOCKER_VERSION} docker-ce-cli=${UBUNTU_DOCKER_VERSION}
fi
if [ $? -eq 0 ];then
color "安装软件包成功" 0
else
color "安装软件包失败,请检查网络配置" 1
exit
fi
mkdir -p /etc/docker
tee /etc/docker/daemon.json <<EOF
{
"registry-mirrors": ["https://5lwrg1ye.mirror.aliyuncs.com"],
"insecure-registries":["harbor.yanlinux.org"]
}
EOF
systemctl daemon-reload
systemctl enable docker
systemctl restart docker
docker version && color "Docker 安装成功" 0 || color "Docker 安装失败" 1
echo 'alias rmi="docker images -qa|xargs docker rmi -f"' >> ~/.bashrc
echo 'alias rmc="docker ps -qa|xargs docker rm -f"' >> ~/.bashrc
echo 'alias dps="docker ps -a"' >> ~/.bashrc
echo 'alias dim="docker images"' >> ~/.bashrc
}
install_docker_compose() {
${COLOR_SUCCESS}"开始安装 Docker compose....."${END}
sleep 5
if [ ! -e ${DOCKER_COMPOSE_FILE} ];then
curl -L https://get.daocloud.io/docker/compose/releases/download/v${DOCKER_COMPOSE_VERSION}/docker-compose-$(uname -s)-$(uname -m) -o /usr/bin/docker-compose
else
mv ${DOCKER_COMPOSE_FILE} /usr/bin/docker-compose
fi
chmod +x /usr/bin/docker-compose
if docker-compose --version ;then
${COLOR_SUCCESS}"Docker Compose 安装完成"${END}
else
${COLOR_FAILURE}"Docker compose 安装失败"${END}
exit
fi
}
install_harbor() {
${COLOR_SUCCESS}"开始安装 Harbor....."${END}
sleep 5
#下载文件
if [ ! -e harbor-offline-installer-v${HARBOR_VERSION}.tgz ];then
wget https://github.com/goharbor/harbor/releases/download/v${HARBOR_VERSION}/harbor-offline-installer-v${HARBOR_VERSION}.tgz || ${COLOR_FAILURE} "下载失败!" ${END}
fi
#[ -d ${HARBOR_BASE} ] || mkdir ${HARBOR_BASE}
tar xvf harbor-offline-installer-v${HARBOR_VERSION}.tgz -C ${HARBOR_BASE}
cd ${HARBOR_BASE}/harbor
#编辑配置文件
cp harbor.yml.tmpl harbor.yml
sed -ri "/^hostname/s/reg.mydomain.com/${HARBOR_NAME}/" harbor.yml
sed -ri "/^https/s/(https:)/#\1/" harbor.yml
sed -ri "s/(port: 443)/#\1/" harbor.yml
sed -ri "/certificate:/s/(.*)/#\1/" harbor.yml
sed -ri "/private_key:/s/(.*)/#\1/" harbor.yml
sed -ri "s/Harbor12345/${HARBOR_ADMIN_PASSWORD}/" harbor.yml
sed -i 's#^data_volume: /data#data_volume: /data/harbor#' harbor.yml
${HARBOR_BASE}/harbor/install.sh && ${COLOR_SUCCESS}"Harbor 安装完成"${END} || ${COLOR_FAILURE}"Harbor 安装失败"${END}
cat > /lib/systemd/system/harbor.service << EOF
[Unit]
Description=Harbor
After=docker.service systemd-networkd.service systemd-resolved.service
Requires=docker.service
Documentation=http://github.com/vmware/harbor
[Service]
Type=simple
Restart=on-failure
RestartSec=5
ExecStart=/usr/bin/docker-compose -f ${HARBOR_BASE}/harbor/docker-compose.yml up
ExecStop=/usr/bin/docker-compose -f ${HARBOR_BASE}/harbor/docker-compose.yml down
[Install]
WantedBy=multi-user.target
EOF
systemctl daemon-reload
systemctl enable --now harbor &> /dev/null || ${COLOR}"Harbor已配置为开机自动启动"${END}
if [ $? -eq 0 ];then
echo
color "Harbor安装完成!" 0
echo "-------------------------------------------------------------------"
echo -e "请访问链接: \E[32;1mhttp://${HARBOR_IP}/\E[0m"
echo -e "用户和密码: \E[32;1madmin/${HARBOR_ADMIN_PASSWORD}\E[0m"
else
color "Harbor安装失败!" 1
exit
fi
}
docker info &> /dev/null && ${COLOR_FAILURE}"Docker已安装"${END} || install_docker
docker-compose --version &> /dev/null && ${COLOR_FAILURE}"Docker Compose已安装"${END} || install_docker_compose
install_harbor
[root@rocky8 ~]$ sh /data/scripts/install_harbor.sh
1.2 在Harbor服务器(10.0.0.18)上配置https
1.2.1 生成Harbor服务器证书
#生成ca的私钥
openssl genrsa -out ca.key 4096
#生成ca的自签名证书
openssl req -x509 -new -nodes -sha512 -days 3650 \
-subj "/C=CN/ST=Jiangsu/L=Nanjing/O=example/OU=Personal/CN=yanlinux.org" \
-key ca.key \
-out ca.crt
#生成harbor主机的私钥
openssl genrsa -out harbor1.yanlinux.org.key 4096
#生成harbor主机的证书申请
openssl req -new -sha512 \
-subj "/C=CN/ST=Jiangsu/L=Nanjing/O=example/OU=Personal/CN=harbor1.yanlinux.org" \
-key harbor1.yanlinux.org.key \
-out harbor1.yanlinux.org.csr
#创建x509 v3扩展文件(新版新增的要求)
cat > v3.txt <<EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1=yanlinux.org
DNS.2=yanlinux
DNS.3=harbor1.yanlinux.org #域名
EOF
#给harbor主机颁发证书
openssl x509 -req -sha512 -days 3650 \
-extfile v3.txt \
-CA ca.crt -CAkey ca.key -CAcreateserial \
-in harbor1.yanlinux.org.csr \
-out harbor1.yanlinux.org.crt
#最终文件
ca.crt ca.srl harbor1.yanlinux.org.csr v3.txt
ca.key harbor1.yanlinux.org.crt harbor1.yanlinux.org.key
1.2.2 配置Harbor服务器使用证书
mkdir /data/harbor/certs/
#拷贝证书文件
cp harbor1.yanlinux.org.crt harbor1.yanlinux.org.key /data/harbor/certs/
#修改配置,加上https认证
vim /usr/local/harbor/harbor.yml
......
# https related config
https:
# https port for harbor, default is 443
port: 443
# The path of cert and key files for nginx
certificate: /data/harbor/certs/harbor1.yanlinux.org.crt
private_key: /data/harbor/certs/harbor1.yanlinux.org.key
......
#使配置生效
cd /usr/local/harbor
./prepare; docker-compose down -v; docker-compose up -d
打开网址就会跳转到https

1.3 在Docker服务器端(10.0.0.8)下载CA的证书并上传镜像
直接登录和上传下载镜像会报错
[root@rocky8 ~]$ vi /etc/hosts
10.0.0.18 harbor1.yanlinux.org
#没有证书验证,直接登录失败
[root@rocky8 ~]$ docker login harbor1.yanlinux.org
Username: admin
Password:
Error response from daemon: Get "https://harbor1.yanlinux.org/v2/": x509: certificate signed by unknown authority
#拉取失败
[root@rocky8 ~]$ docker pull harbor1.yanlinux.org/test/nginx:1.22.1-20230222
Error response from daemon: Get "https://harbor1.yanlinux.org/v2/": x509: certificate signed by unknown authority
在docker服务器端使用证书文件
#在harbor服务器端,转换harbor的crt证书文件为cert后缀,docker识别crt文件为CA证书,cert为客户端证书
[root@rocky8 certs]$ openssl x509 -inform PEM -in harbor1.yanlinux.org.crt -out harbor1.yanlinux.org.cert
[root@rocky8 certs]$ ll harbor1.yanlinux.org.c*rt
-rw-r--r-- 1 root root 2134 Feb 28 22:24 harbor1.yanlinux.org.cert
-rw-r--r-- 1 root root 2134 Feb 28 21:46 harbor1.yanlinux.org.crt
#两个文件一样,直接cp -a harbor1.yanlinux.org.crt harbor1.yanlinux.org.cert就行
[root@rocky8 certs]$ md5sum harbor1.yanlinux.org.cert harbor1.yanlinux.org.crt
23ef17b3e9fa2069fe5a190dd8b428de harbor1.yanlinux.org.cert
23ef17b3e9fa2069fe5a190dd8b428de harbor1.yanlinux.org.crt
#在docker服务端下载证书
[root@rocky8 ~]$ mkdir /etc/docker/certs.d/harbor1.yanlinux.org/ -p
[root@rocky8 ~]$ cd /etc/docker/certs.d/harbor1.yanlinux.org/
[root@rocky8 ~]$ scp 10.0.0.18:/root/certs/{harbor1.yanlinux.org.cert,harbor1.yanlinux.org.key,ca.crt} /etc/docker/certs.d/harbor1.yanlinux.org/
#在harbor服务器上拷贝证书到/etc/docker下,实现harbor服务器的上传与下载镜像
[root@rocky8 harbor1.yanlinux.org]$ scp -r /etc/docker/certs.d/ 10.0.0.18:/etc/docker/
[root@rocky8 ~]$ systemctl restart docker
#登录账户
[root@rocky8 ~]$ docker login harbor1.yanlinux.org
#打标签
[root@rocky8 ~]$ docker tag alpine-base:3.17.2 harbor1.yanlinux.org/test/alpine-base:3.17.2
[root@rocky8 ~]$ docker tag nginx-alpine:1.22.1 harbor1.yanlinux.org/test/nginx-alpine:1.22.1
[root@rocky8 ~]$ docker tag alpine-jdk:8u202 harbor1.yanlinux.org/test/alpine-jdk:8u202
[root@rocky8 ~]$ docker tag tomcat-base:v8.5.85 harbor1.yanlinux.org/test/tomcat-base:v8.5.85
[root@rocky8 ~]$ docker tag haproxy-alpine:2.1.2 harbor1.yanlinux.org/test/haproxy-alpine:2.1.2
#上传镜像
[root@rocky8 ~]$ docker push harbor1.yanlinux.org/test/alpine-base:3.17.2
The push refers to repository [harbor1.yanlinux.org/test/alpine-base]
87c8bbf9e2e8: Pushed
0ba47f277eb9: Pushed
7cd52847ad77: Pushed
3.17.2: digest: sha256:d2aaa9d3e26da43e5b83d02b92aab403f33e9d4c9a3e9171a14ef314692e4a7a size: 947
[root@rocky8 ~]$ docker push harbor1.yanlinux.org/test/nginx-alpine:1.22.1
The push refers to repository [harbor1.yanlinux.org/test/nginx-alpine]
fa80f3c76ef6: Pushed
01c65a043850: Pushed
adbe8696b1b4: Pushed
1e356a844716: Pushed
ebb41e59056a: Pushed
0ba47f277eb9: Mounted from test/alpine-base
7cd52847ad77: Mounted from test/alpine-base
1.22.1: digest: sha256:104304b5133de8acd1978485c2d980748dab7314d267d29b4278f22573010058 size: 1784
[root@rocky8 ~]$ docker push harbor1.yanlinux.org/test/alpine-jdk:8u202
The push refers to repository [harbor1.yanlinux.org/test/alpine-jdk]
d88c104af48e: Pushed
4236564ab151: Pushed
31af46d91eef: Pushed
87c8bbf9e2e8: Mounted from test/alpine-base
0ba47f277eb9: Mounted from test/nginx-alpine
7cd52847ad77: Mounted from test/nginx-alpine
8u202: digest: sha256:6a93df44d46e757dda66a6c2f8ea28c11d3954d3c714392b608c40f45b2e2413 size: 1574
[root@rocky8 ~]$ docker push harbor1.yanlinux.org/test/tomcat-base:v8.5.85
The push refers to repository [harbor1.yanlinux.org/test/tomcat-base]
6d1a20593ad3: Pushed
8d7f5b279153: Pushed
0abb32fe3733: Pushed
d88c104af48e: Mounted from test/alpine-jdk
4236564ab151: Mounted from test/alpine-jdk
31af46d91eef: Mounted from test/alpine-jdk
87c8bbf9e2e8: Mounted from test/alpine-jdk
0ba47f277eb9: Mounted from test/alpine-jdk
7cd52847ad77: Mounted from test/alpine-jdk
v8.5.85: digest: sha256:a19bb6ff4a407cbd9881a27b8ca412b6bd45d5fd0b8bff35e6a6d759813fb273 size: 2200
[root@rocky8 ~]$ docker push harbor1.yanlinux.org/test/haproxy-alpine:2.1.2
The push refers to repository [harbor1.yanlinux.org/test/haproxy-alpine]
406ce5ba5219: Pushed
3ecff3848c3e: Pushed
89180f31278f: Pushed
87c8bbf9e2e8: Mounted from test/tomcat-base
0ba47f277eb9: Mounted from test/tomcat-base
7cd52847ad77: Mounted from test/tomcat-base
2.1.2: digest: sha256:bbf660062436f982e820d2daacb8fcd1d83ecc06115e178bfe094b8c4f513066 size: 1576
查看仓库上传的镜像

1.4 在客户端下载镜像(10.0.0.38 安装docker)
直接登录和上传下载镜像会报错
[root@rocky8 ~]$ vi /etc/hosts
10.0.0.18 harbor1.yanlinux.org
#没有证书验证,直接登录失败
[root@rocky8 ~]$ docker login harbor1.yanlinux.org
Username: admin
Password:
Error response from daemon: Get "https://harbor1.yanlinux.org/v2/": x509: certificate signed by unknown authority
#拉取失败
[root@rocky8 ~]$ docker pull harbor1.yanlinux.org/test/nginx:1.22.1-20230222
Error response from daemon: Get "https://harbor1.yanlinux.org/v2/": x509: certificate signed by unknown authority
配置Docker客户端使用证书文件
#在docker客户端下载证书
[root@rocky8 ~]$ mkdir /etc/docker/certs.d/harbor1.yanlinux.org/ -p
[root@rocky8 ~]$ cd /etc/docker/certs.d/harbor1.yanlinux.org/
[root@rocky8 harbor1.yanlinux.org]$ scp 10.0.0.18:/root/certs/{harbor1.yanlinux.org.cert,harbor1.yanlinux.org.key,ca.crt} /etc/docker/certs.d/harbor1.yanlinux.org/
[root@rocky8 ~]$ systemctl restart docker
拉取镜像
[root@rocky8 ~]$ docker pull harbor1.yanlinux.org/test/haproxy-alpine:2.1.2
[root@rocky8 ~]$ docker pull harbor1.yanlinux.org/test/tomcat-base:v8.5.85
[root@rocky8 ~]$ docker pull harbor1.yanlinux.org/test/alpine-jdk:8u202
[root@rocky8 ~]$ docker pull harbor1.yanlinux.org/test/nginx-alpine:1.22.1
[root@rocky8 ~]$ docker pull harbor1.yanlinux.org/test/alpine-base:3.17.2
[root@rocky8 ~]$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
harbor1.yanlinux.org/test/haproxy-alpine 2.1.2 9eeb5cb28dbe About an hour ago 226MB
harbor1.yanlinux.org/test/tomcat-base v8.5.85 f5a9ab5c83ab 2 hours ago 615MB
harbor1.yanlinux.org/test/alpine-jdk 8u202 a38ecf1969fd 3 hours ago 600MB
harbor1.yanlinux.org/test/alpine-base 3.17.2 b3e65dab1347 3 hours ago 197MB
harbor1.yanlinux.org/test/nginx-alpine 1.22.1 7f619fd93a01 5 hours ago 213MB
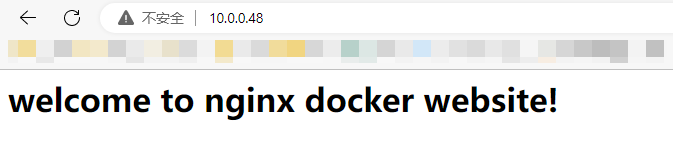
1.5 运行nginx服务
[root@rocky8 ~]$ docker run -d --name web01 -p 80:80 harbor1.yanlinux.org/test/nginx-alpine:1.22.1
122ce510bc25d74325525aae4ed9d4a10296cb525fb893aa3c6635ebda7cd936
查看网页信息