一.RC4加密简介
RC4(Rivest Cipher 4)是一种流加密算法,由罗纳德·李维斯特(Ron Rivest)在1987年开发。RC4算法的核心思想是利用伪随机数生成器(PRNG)和密钥共同生成一个密钥流,该密钥流与明文进行异或运算得到密文。
在RC4算法中,密钥流由两部分组成:密钥调度算法(KSA)和伪随机数生成算法(PRGA)。KSA的主要作用是将输入的密钥进行排列,生成一个密钥数组。PRGA则根据密钥数组生成伪随机数序列,这个序列与明文进行异或运算,得到密文。
来源于大佬:
B站/可厉害的土豆
RC4加密算法原理简单理解 - 沉默的赌徒 - 博客园 (cnblogs.com)


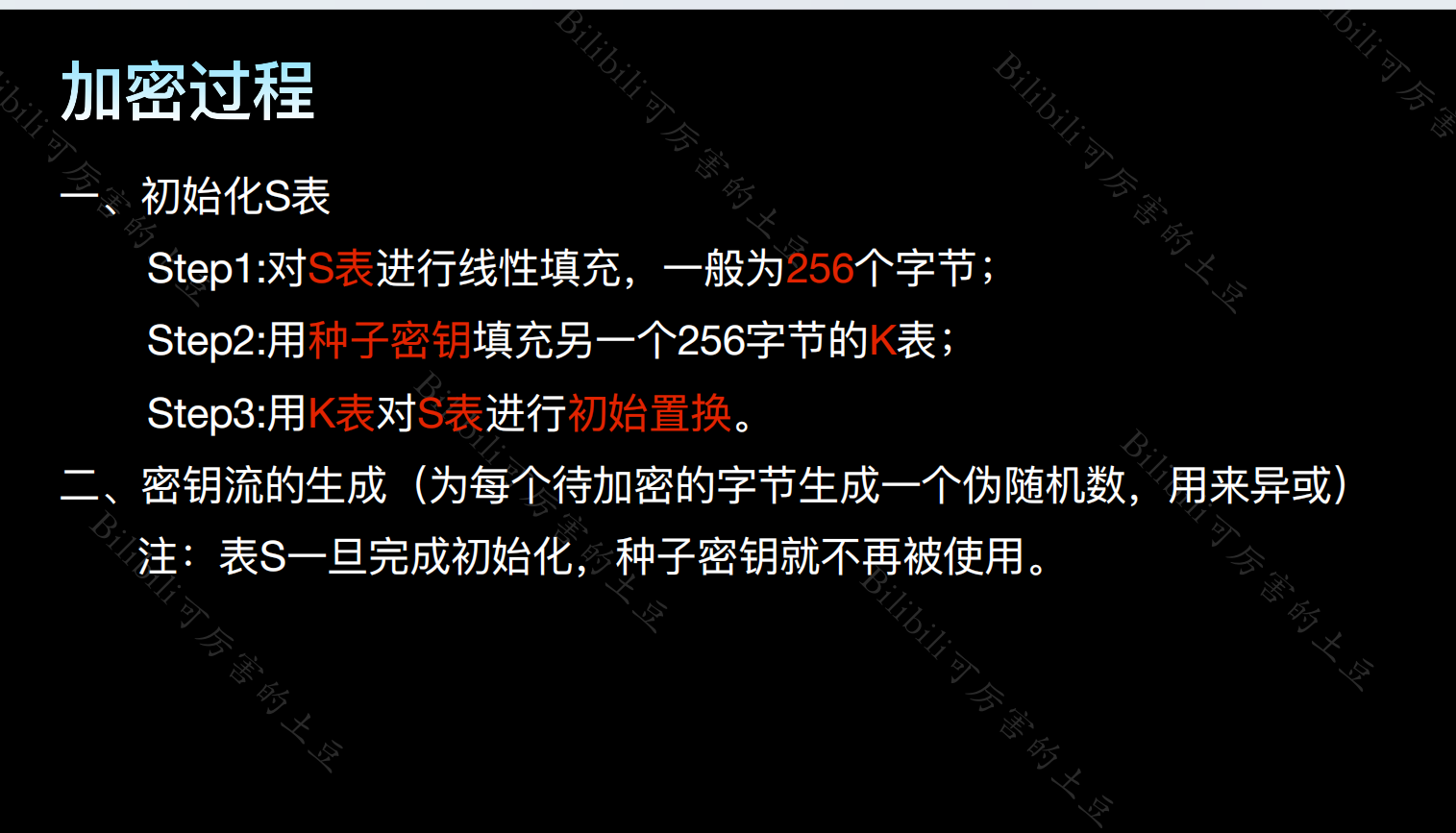
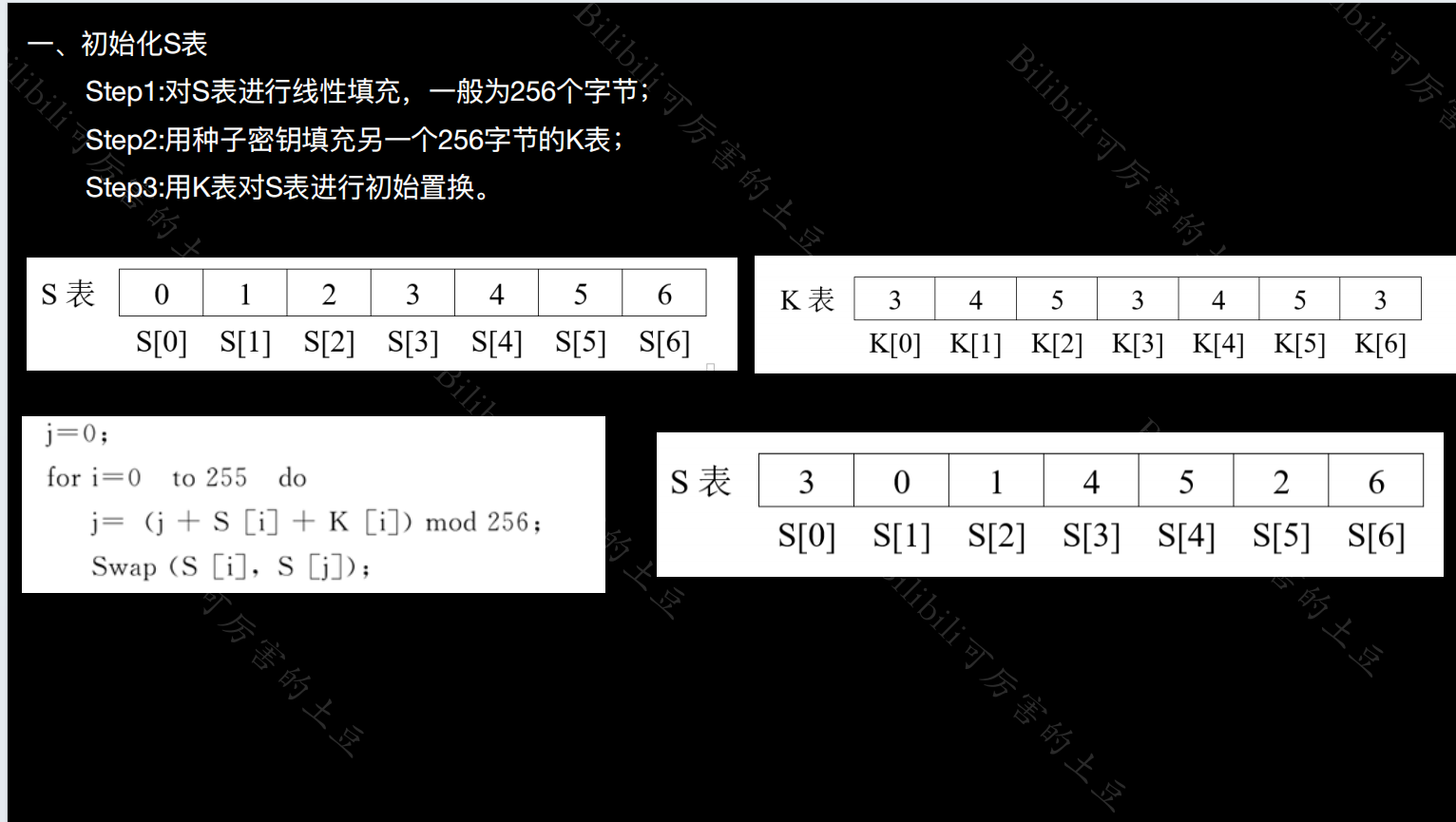
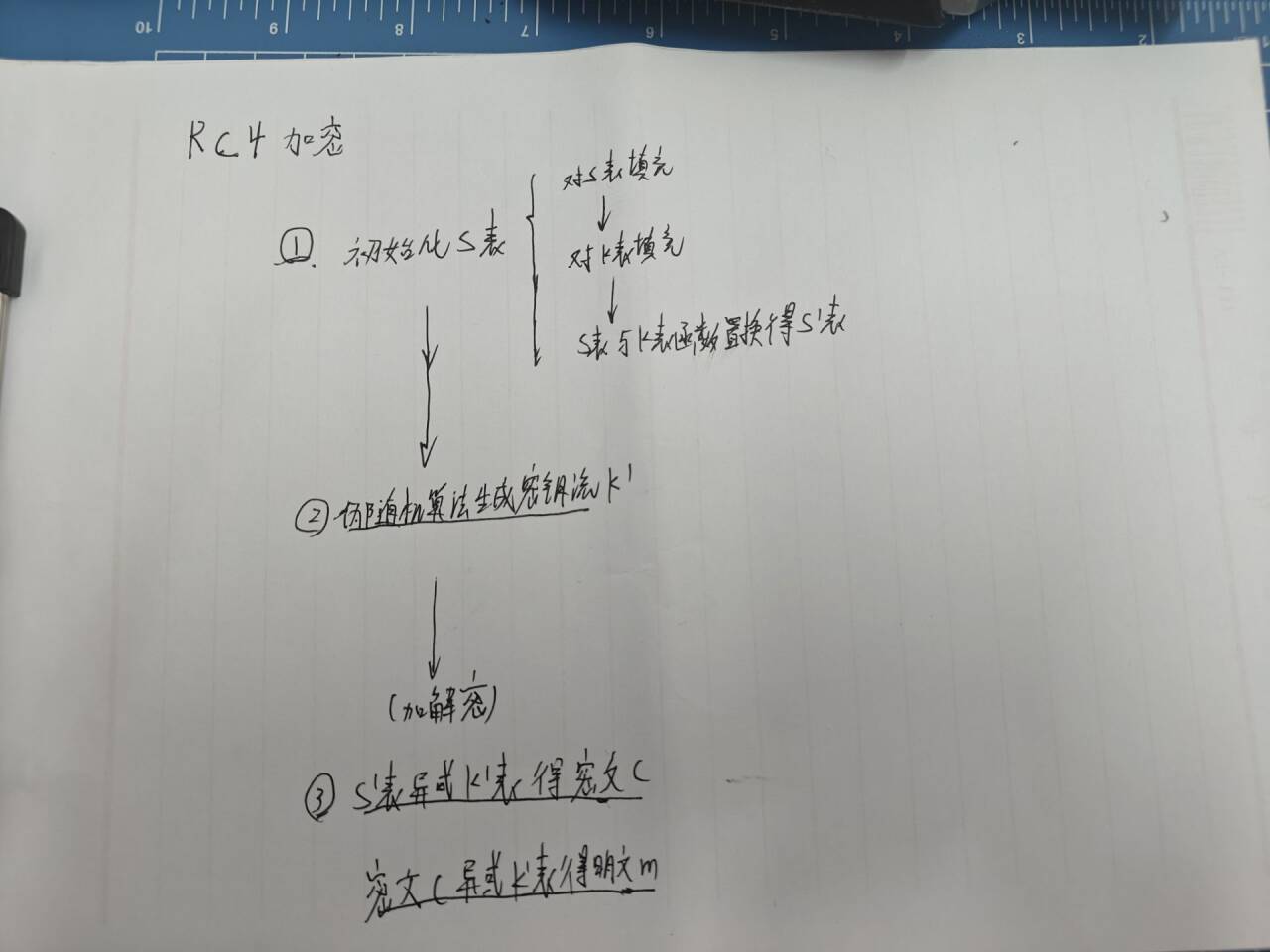
(1)初始化S表
for i from 0 to 255
S[i] := i #填充S表
endfor
j := 0
for i from 0 to 255 #填充K表冰置换得到S'表
j := (j + S[i] + key[i mod keylength]) mod 256
swap values of S[i] and S[j]
endfor
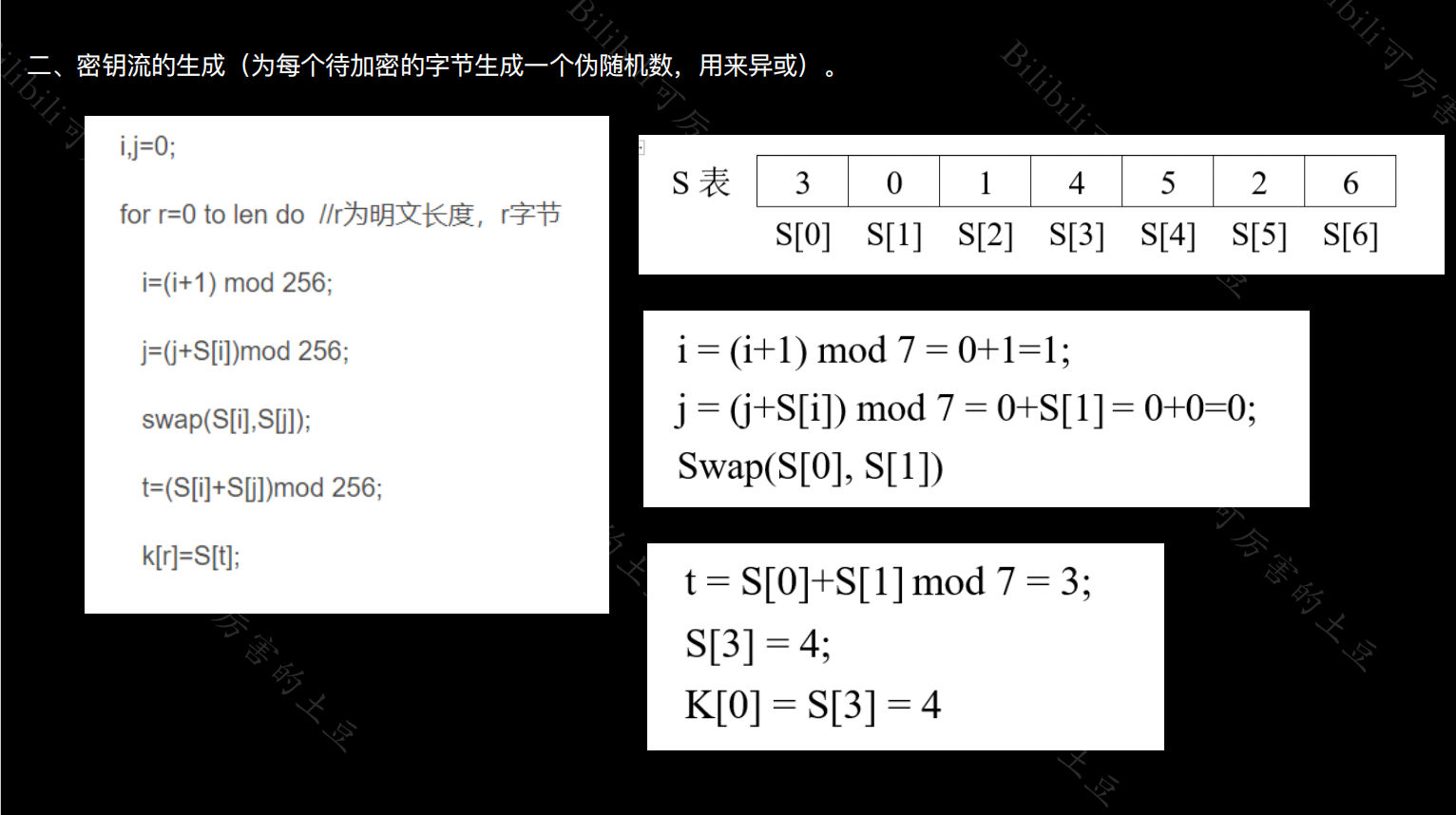
(2)伪随机生成密钥流
i := 0
j := 0
while GeneratingOutput:
i := (i + 1) mod 256
j := (j + S[i]) mod 256
swap values of S[i] and S[j]
K := S[(S[i] + S[j]) mod 256]
output K
endwhile
(3)加密解密
将上一步取出的K与明文当前字节做异或得到密文,再异或得到密文
二.魔改RC4
(待加)
三.实例
1.i春秋课附件题(不会花指令,没有反编译成功)
后面再做吧,记录一下
2.BUUCTF/[第五章 CTF之RE章]BabyAlgorithm(算法)

直接ida打开
tab键之后没有太多东西
找到main函数
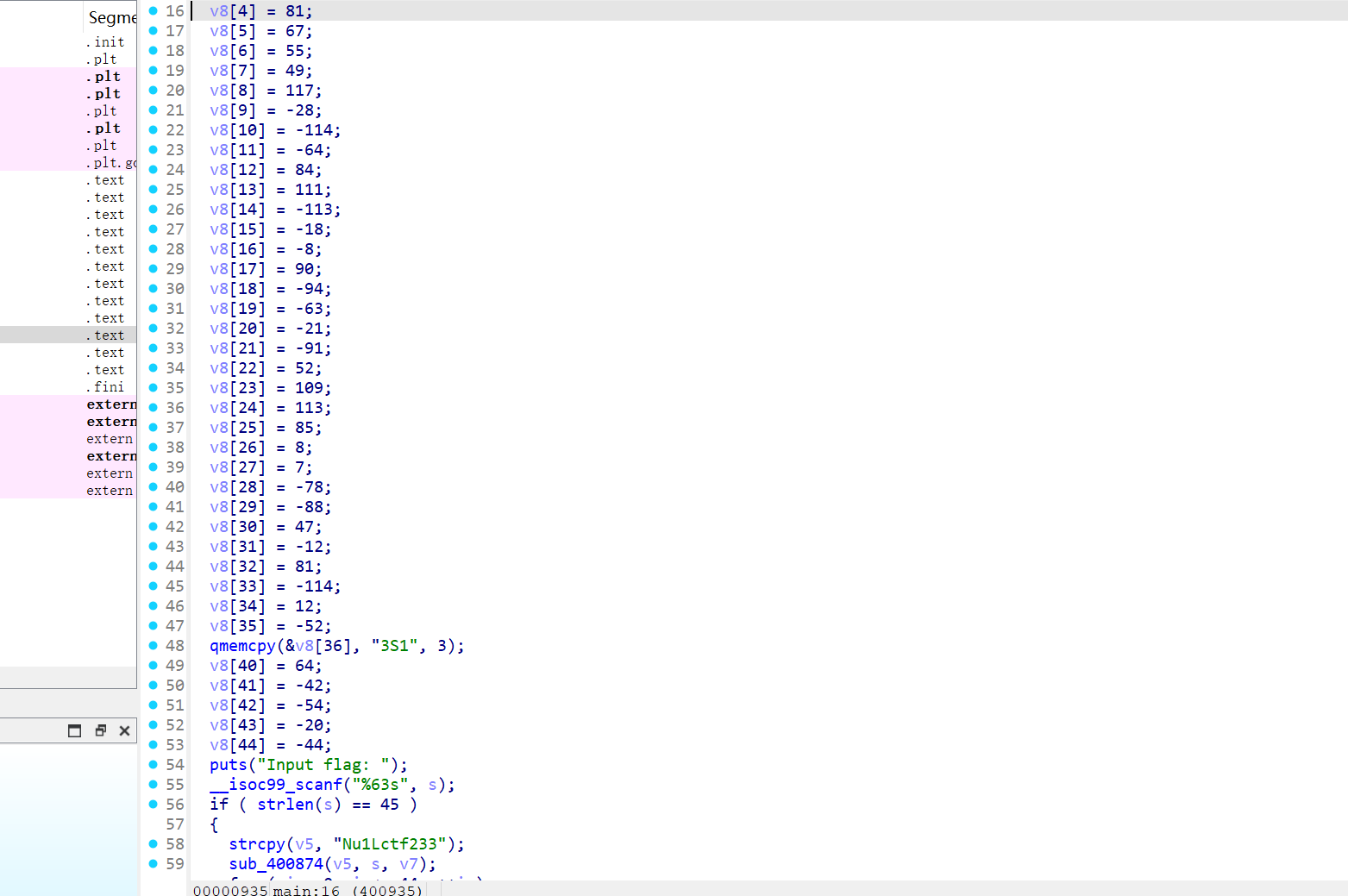
__int64 __fastcall main(int a1, char **a2, char **a3)
{
int i; // [rsp+Ch] [rbp-E4h]
char v5[16]; // [rsp+10h] [rbp-E0h] BYREF
char s[64]; // [rsp+20h] [rbp-D0h] BYREF
char v7[64]; // [rsp+60h] [rbp-90h] BYREF
char v8[72]; // [rsp+A0h] [rbp-50h] BYREF
unsigned __int64 v9; // [rsp+E8h] [rbp-8h]
v9 = __readfsqword(0x28u);
memset(v8, 0, 0x40uLL);
v8[0] = -58;
v8[1] = 33;
v8[2] = -54;
v8[3] = -65;
v8[4] = 81;
v8[5] = 67;
v8[6] = 55;
v8[7] = 49;
v8[8] = 117;
v8[9] = -28;
v8[10] = -114;
v8[11] = -64;
v8[12] = 84;
v8[13] = 111;
v8[14] = -113;
v8[15] = -18;
v8[16] = -8;
v8[17] = 90;
v8[18] = -94;
v8[19] = -63;
v8[20] = -21;
v8[21] = -91;
v8[22] = 52;
v8[23] = 109;
v8[24] = 113;
v8[25] = 85;
v8[26] = 8;
v8[27] = 7;
v8[28] = -78;
v8[29] = -88;
v8[30] = 47;
v8[31] = -12;
v8[32] = 81;
v8[33] = -114;
v8[34] = 12;
v8[35] = -52;
qmemcpy(&v8[36], "3S1", 3);
v8[40] = 64;
v8[41] = -42;
v8[42] = -54;
v8[43] = -20;
v8[44] = -44;
puts("Input flag: ");
__isoc99_scanf("%63s", s);
if ( strlen(s) == 45 )
{
strcpy(v5, "Nu1Lctf233");
sub_400874(v5, s, v7);
for ( i = 0; i <= 44; ++i )
{
if ( v7[i] != v8[i] )
{
puts("GG!");
return 0LL;
}
}
puts("Congratulations!");
return 0LL;
}
else
{
puts("GG!");
return 0LL;
}
}
看见Nu1Lctf233
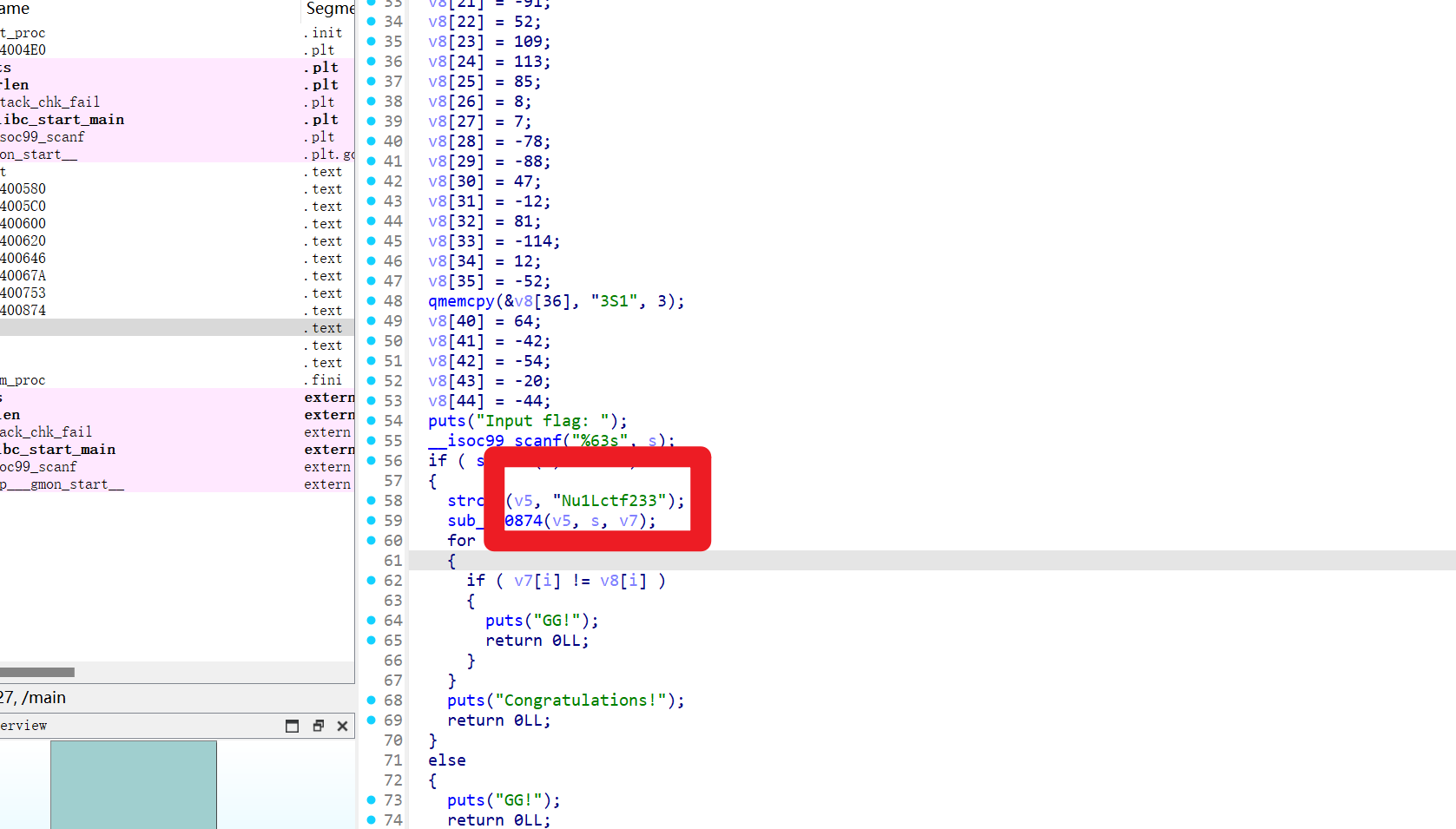
第一反应是一个密钥,但是是什么加密喃
点击函数看看
sub_400874
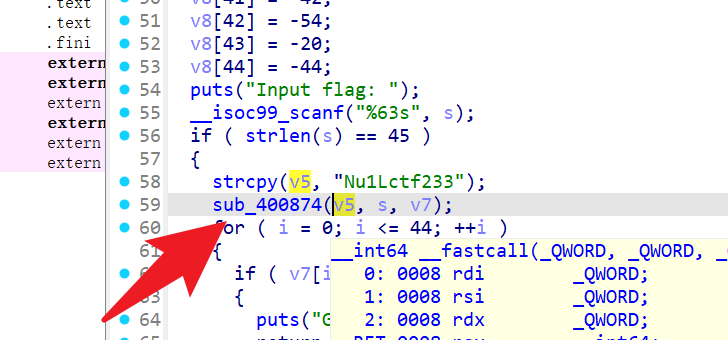
又是两个函数
sub_40067A(a1, v5);
sub_400753(v5, a2, a3);
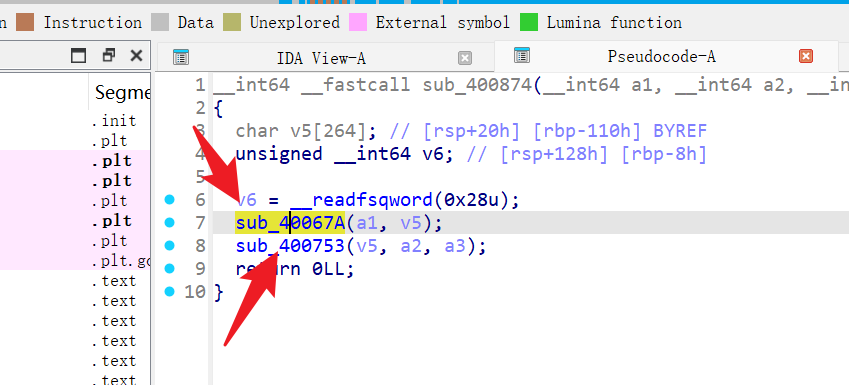
一个个点击进去看看
第一个
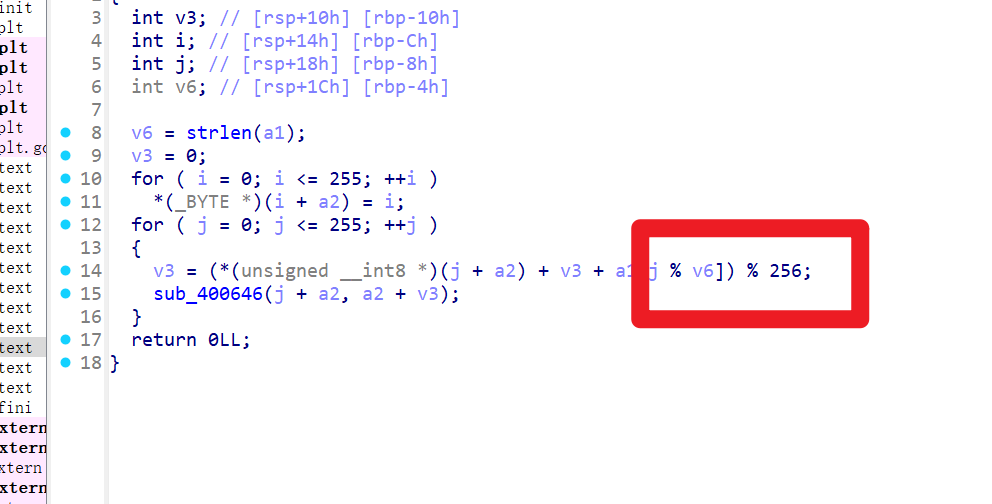
第二个
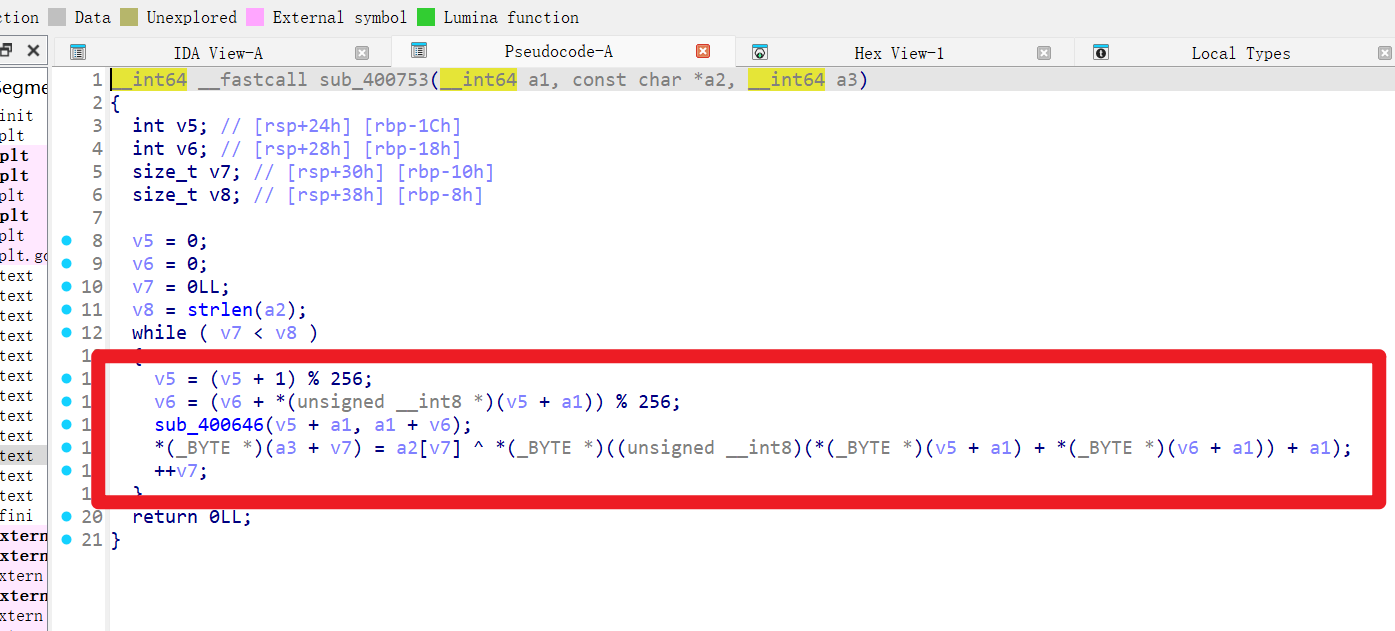
发现是RC4,并且没有魔改
知道密钥是Nu1Lctf233
现在提取密文
esc键返回到主函数
选中之后,shift+E提取数据(十六进制)
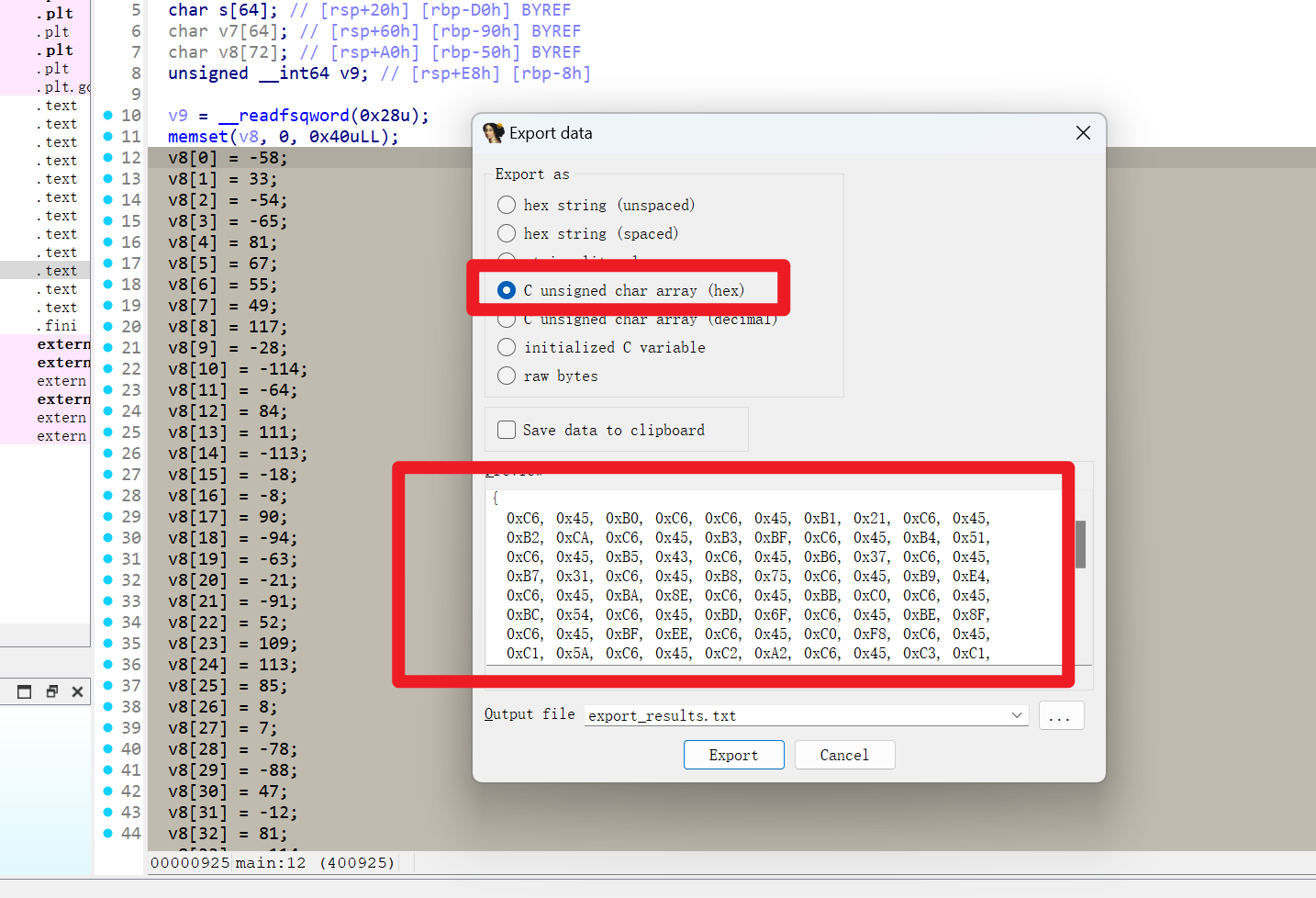
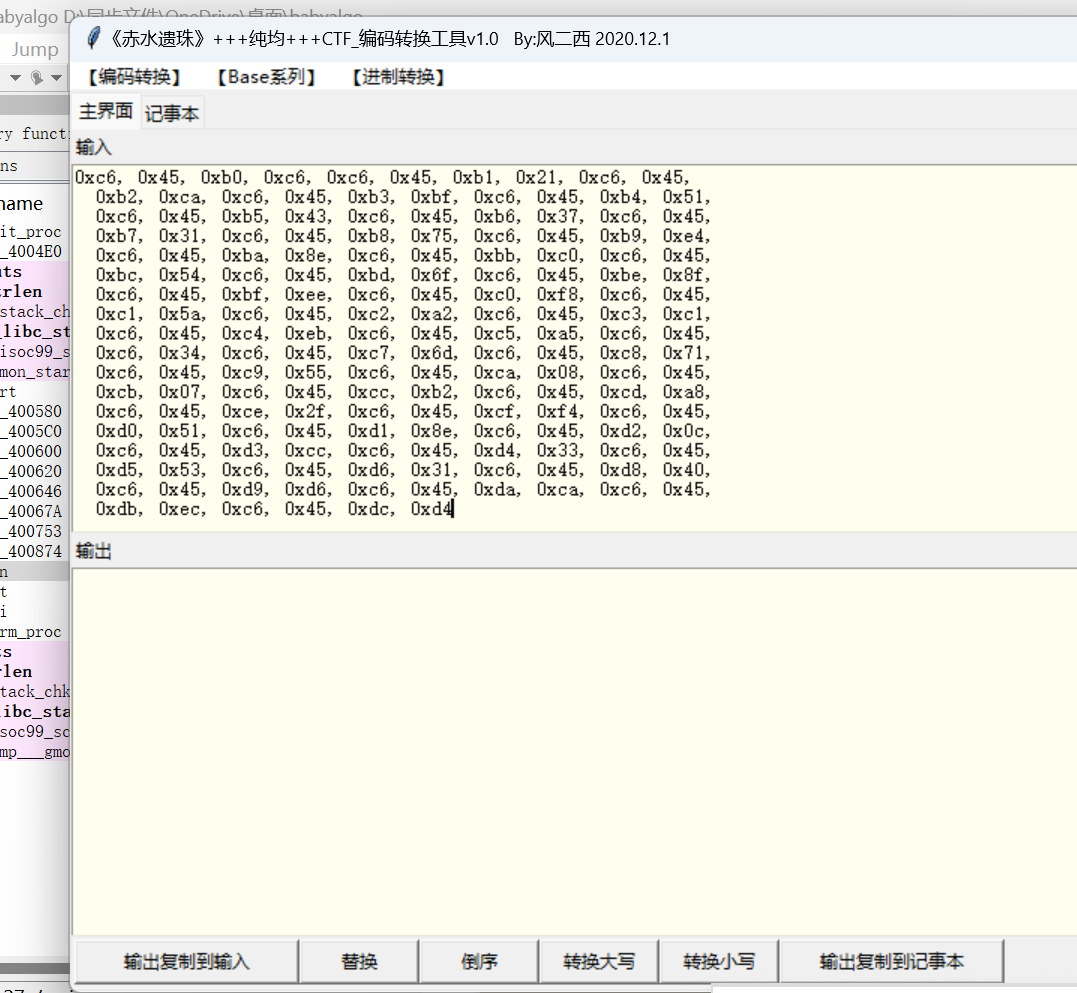
十六进制大写转换为十六进制小写
工具直接转
RC4解密
import base64
def rc4_main(key="init_key", message="init_message"): #密钥 #密文
print("RC4解密主函数调用成功")
print('\n')
s_box = rc4_init_sbox(key)
crypt = rc4_excrypt(message, s_box)
return crypt
def rc4_init_sbox(key):
s_box = list(range(256))
print("原来的 s 盒:%s" % s_box)
print('\n')
j = 0
for i in range(256):
j = (j + s_box[i] + ord(key[i % len(key)])) % 256
s_box[i], s_box[j] = s_box[j], s_box[i]
print("混乱后的 s 盒:%s" % s_box)
print('\n')
return s_box
def rc4_excrypt(plain, box):
print("调用解密程序成功。")
print('\n')
plain = base64.b64decode(plain.encode('utf-8'))
plain = bytes.decode(plain)
res = []
i = j = 0
for s in plain:
i = (i + 1) % 256
j = (j + box[i]) % 256
box[i], box[j] = box[j], box[i]
t = (box[i] + box[j]) % 256
k = box[t]
res.append(chr(ord(s) ^ k))
print("res用于解密字符串,解密后是:%res" % res)
print('\n')
cipher = "".join(res)
print("解密后的字符串是:%s" % cipher)
print('\n')
print("解密后的输出(没经过任何编码):")
print('\n')
return cipher
a = [0xc6, 0x21, 0xca, 0xbf, 0x51, 0x43, 0x37, 0x31, 0x75, 0xe4, 0x8e, 0xc0, 0x54, 0x6f, 0x8f, 0xee, 0xf8, 0x5a, 0xa2,
0xc1, 0xeb, 0xa5, 0x34, 0x6d, 0x71, 0x55, 0x8, 0x7, 0xb2, 0xa8, 0x2f, 0xf4, 0x51, 0x8e, 0xc, 0xcc, 0x33, 0x53,
0x31, 0x0, 0x40, 0xd6, 0xca, 0xec, 0xd4]
s = ""
for i in a:
s += chr(i)
s = str(base64.b64encode(s.encode('utf-8')), 'utf-8')
rc4_main("Nu1Lctf233", s)
"""
RC4解密主函数调用成功
原来的 s 盒:[0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24, 25, 26, 27, 28, 29, 30, 31, 32, 33, 34, 35, 36, 37, 38, 39, 40, 41, 42, 43, 44, 45, 46, 47, 48, 49, 50, 51, 52, 53, 54, 55, 56, 57, 58, 59, 60, 61, 62, 63, 64, 65, 66, 67, 68, 69, 70, 71, 72, 73, 74, 75, 76, 77, 78, 79, 80, 81, 82, 83, 84, 85, 86, 87, 88, 89, 90, 91, 92, 93, 94, 95, 96, 97, 98, 99, 100, 101, 102, 103, 104, 105, 106, 107, 108, 109, 110, 111, 112, 113, 114, 115, 116, 117, 118, 119, 120, 121, 122, 123, 124, 125, 126, 127, 128, 129, 130, 131, 132, 133, 134, 135, 136, 137, 138, 139, 140, 141, 142, 143, 144, 145, 146, 147, 148, 149, 150, 151, 152, 153, 154, 155, 156, 157, 158, 159, 160, 161, 162, 163, 164, 165, 166, 167, 168, 169, 170, 171, 172, 173, 174, 175, 176, 177, 178, 179, 180, 181, 182, 183, 184, 185, 186, 187, 188, 189, 190, 191, 192, 193, 194, 195, 196, 197, 198, 199, 200, 201, 202, 203, 204, 205, 206, 207, 208, 209, 210, 211, 212, 213, 214, 215, 216, 217, 218, 219, 220, 221, 222, 223, 224, 225, 226, 227, 228, 229, 230, 231, 232, 233, 234, 235, 236, 237, 238, 239, 240, 241, 242, 243, 244, 245, 246, 247, 248, 249, 250, 251, 252, 253, 254, 255]
混乱后的 s 盒:[78, 196, 247, 104, 9, 38, 8, 14, 146, 45, 154, 26, 100, 176, 33, 164, 11, 93, 162, 34, 74, 212, 27, 126, 251, 118, 128, 85, 50, 39, 79, 29, 248, 142, 136, 15, 90, 105, 230, 180, 47, 156, 140, 137, 54, 17, 56, 141, 37, 231, 205, 66, 135, 223, 120, 76, 95, 159, 153, 163, 207, 161, 178, 208, 155, 71, 106, 209, 188, 94, 133, 19, 89, 30, 198, 44, 82, 182, 75, 101, 43, 64, 170, 235, 150, 117, 65, 73, 240, 16, 109, 244, 129, 222, 12, 171, 13, 91, 195, 210, 229, 144, 192, 102, 41, 1, 148, 68, 72, 32, 87, 152, 97, 131, 143, 21, 174, 40, 239, 168, 57, 215, 197, 42, 186, 236, 77, 147, 121, 169, 252, 233, 187, 189, 175, 69, 232, 221, 10, 220, 4, 200, 202, 226, 213, 185, 3, 0, 173, 167, 138, 108, 88, 245, 238, 48, 255, 190, 127, 25, 86, 84, 194, 243, 114, 191, 99, 23, 250, 157, 119, 211, 145, 20, 53, 125, 24, 183, 35, 139, 160, 218, 5, 123, 225, 122, 166, 98, 113, 204, 216, 107, 158, 246, 63, 31, 179, 46, 92, 18, 28, 58, 111, 115, 241, 103, 203, 172, 62, 7, 116, 193, 134, 81, 199, 130, 206, 67, 228, 227, 237, 83, 51, 22, 181, 6, 55, 219, 201, 242, 132, 80, 149, 165, 214, 70, 184, 253, 112, 96, 36, 151, 110, 177, 60, 2, 234, 59, 52, 254, 217, 249, 124, 224, 61, 49]
调用解密程序成功。
res用于解密字符串,解密后是:['n', '1', 'b', 'o', 'o', 'k', '{', 'u', 's', '1', 'n', 'G', '_', 'f', '3', 'a', 't', 'u', 'r', '3', 's', '_', '7', 'o', '_', 'd', 'e', '7', 'e', 'r', 'm', '1', 'n', '3', '_', '4', 'l', 'g', '0', 'r', 'i', '7', 'h', 'm', '}']es
解密后的字符串是:n1book{us1nG_f3atur3s_7o_de7erm1n3_4lg0ri7hm}
解密后的输出(没经过任何编码):
"""
n1book{us1nG_f3atur3s_7o_de7erm1n3_4lg0ri7hm}
3.普通RC4题
直接拖进IDA,String找到密文密钥
CyberChef直接解,密钥或者输出类型调一下